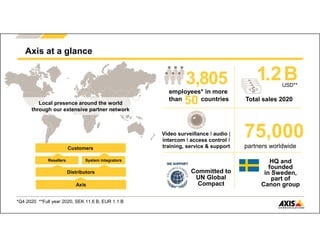
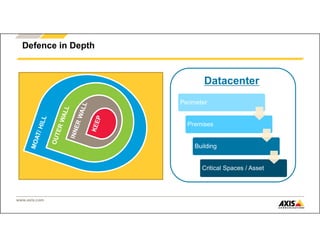
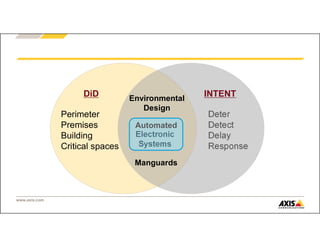
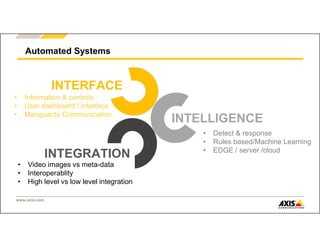
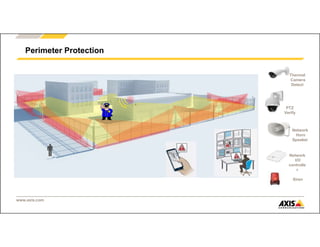
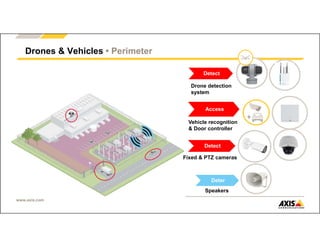
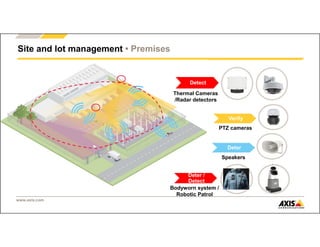
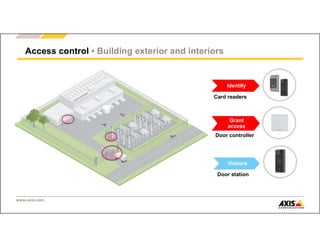
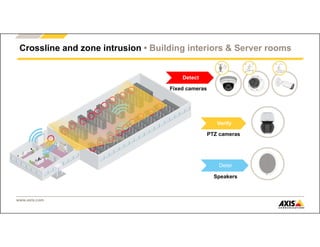
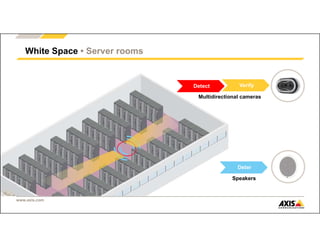
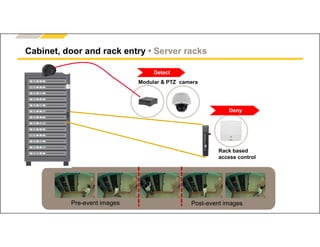
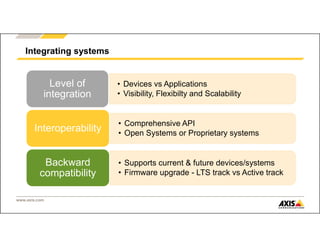
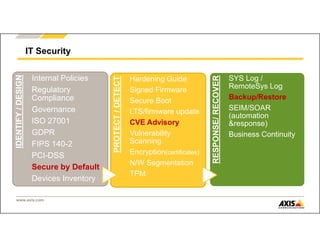
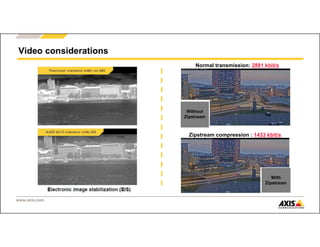
The document outlines Axis Communications' approach to enhancing security through automated systems in various environments. It emphasizes the importance of reducing response times and increasing effectiveness by integrating technology, along with providing a detailed overview of different security solutions like video surveillance, access control, and environmental design. Key considerations include system interoperability, regulatory compliance, environmental factors, and optimizing cabling for efficiency.