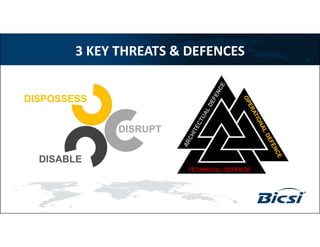
1) The document discusses securing datacenters against key threats like dispossessing, disabling, and disrupting access.
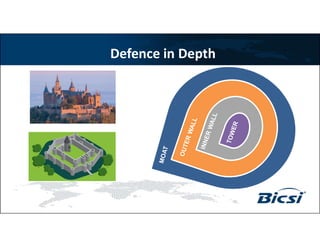
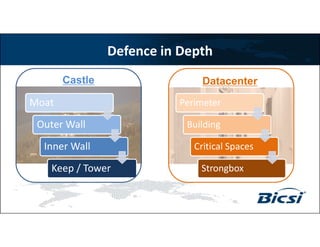
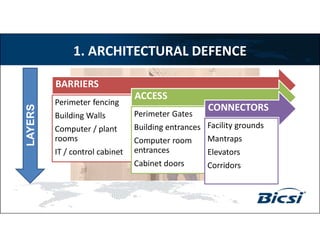
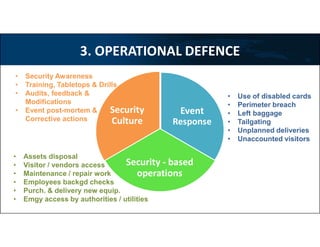
2) It recommends implementing defense in depth across multiple layers including the perimeter, building, critical spaces, and strongbox (server rack) layers using architectural barriers, access controls, intrusion detection technologies, and operational security practices.
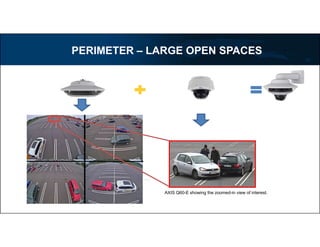
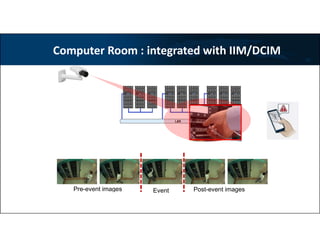
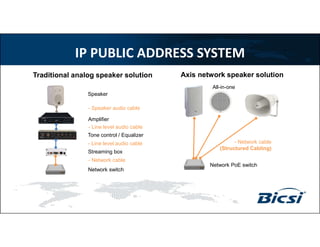
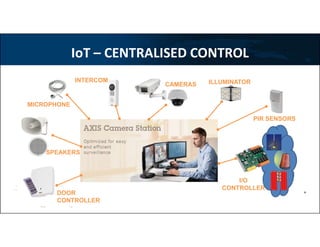
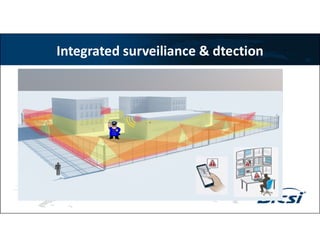
3) Technologies discussed include various camera types, access control systems, audio/video analytics, and an integrated physical security system controlled over an IP network.