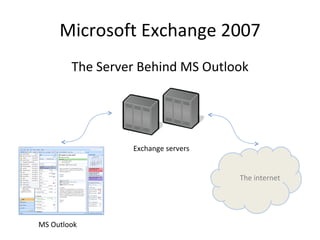
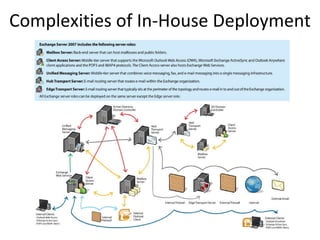
This document discusses the benefits of hosted Microsoft Exchange 2007 email and collaboration solutions over an on-premise solution. It highlights features like calendaring, contacts, tasks management and enhanced security. It also notes the growing market for hosted Exchange services and mentions benefits like no upfront costs, fixed monthly fees, 24/7 support and mobility through Blackberry and Windows integration.