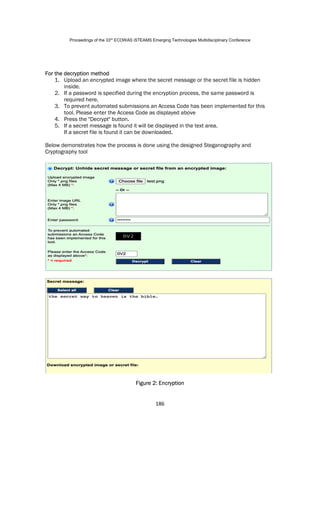
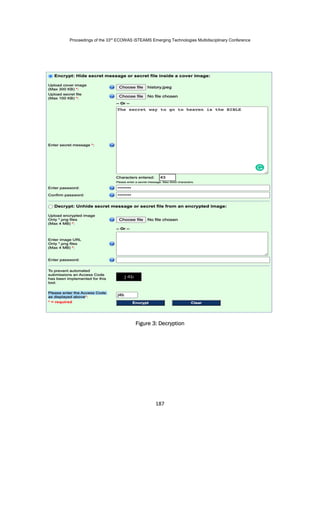
The document describes a method for encrypting plaintext into an image to send over a network securely. It involves encrypting the text using the Blowfish algorithm, hiding the encrypted text in the image using least significant bit steganography, and sending the encoded image to the recipient. The recipient can then decrypt the image to retrieve the hidden encrypted text and decrypt it to view the original plaintext. The document outlines the system architecture and steps for encryption and decryption of text in an image for secure transmission over a network.