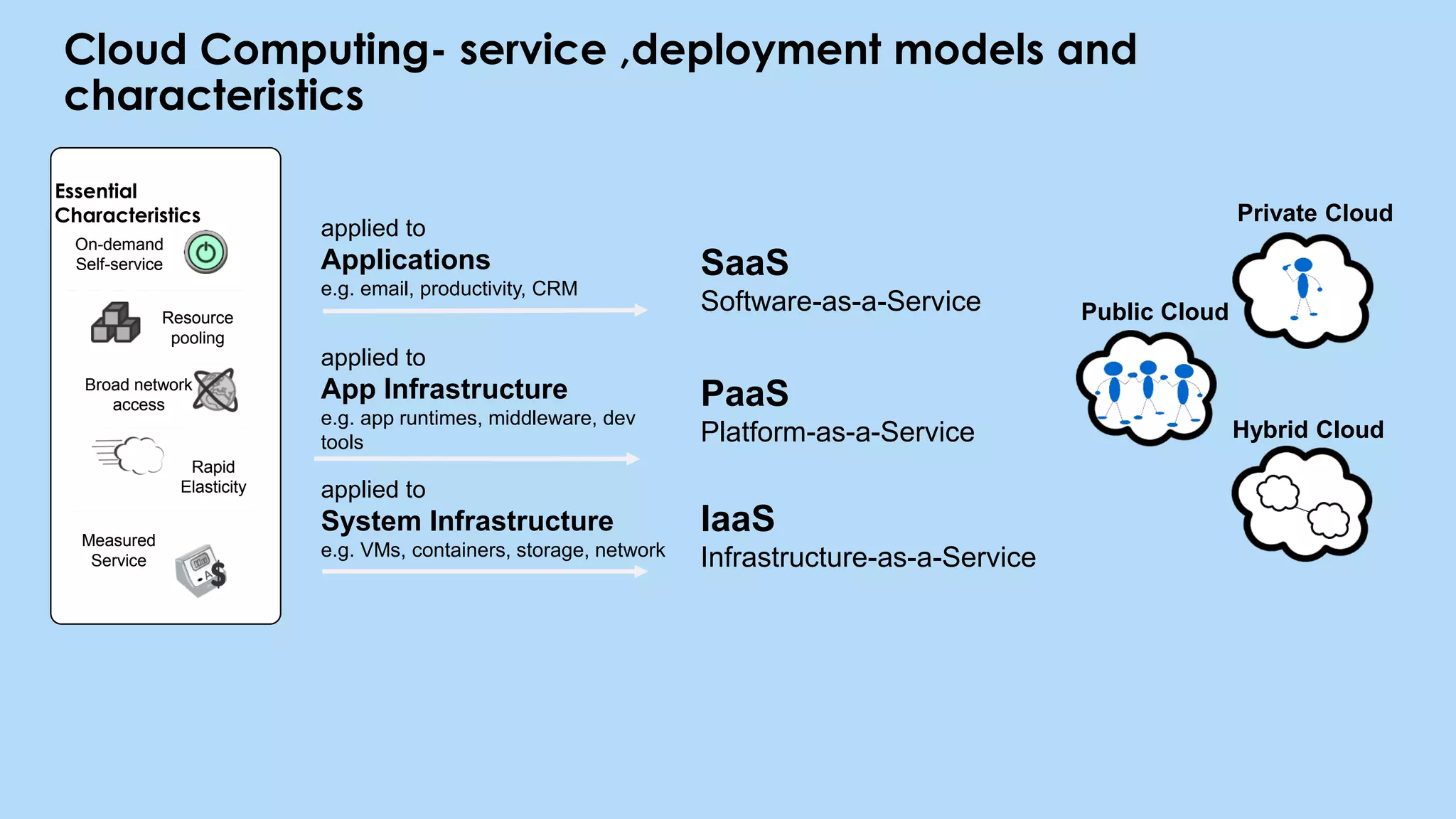
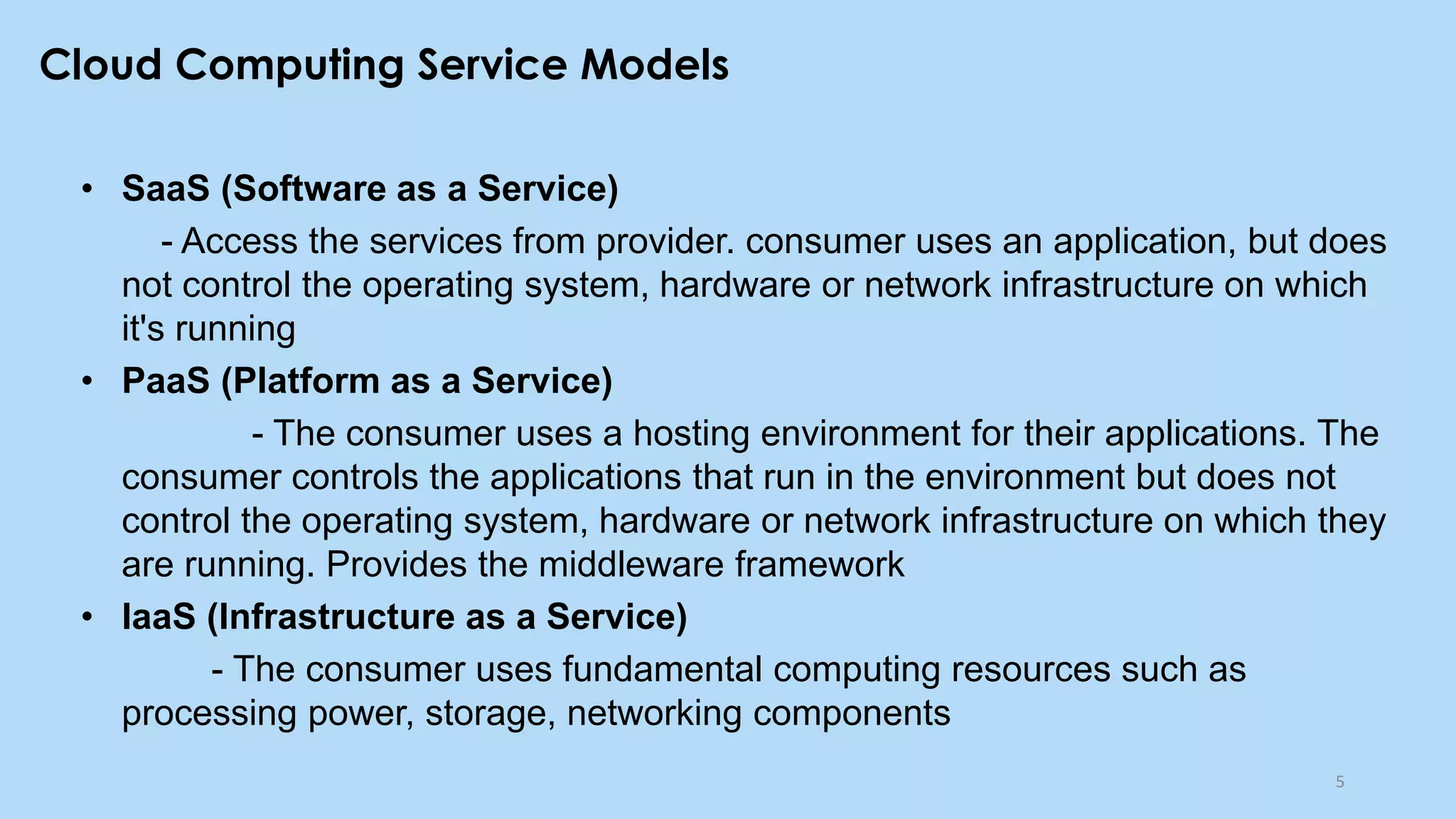
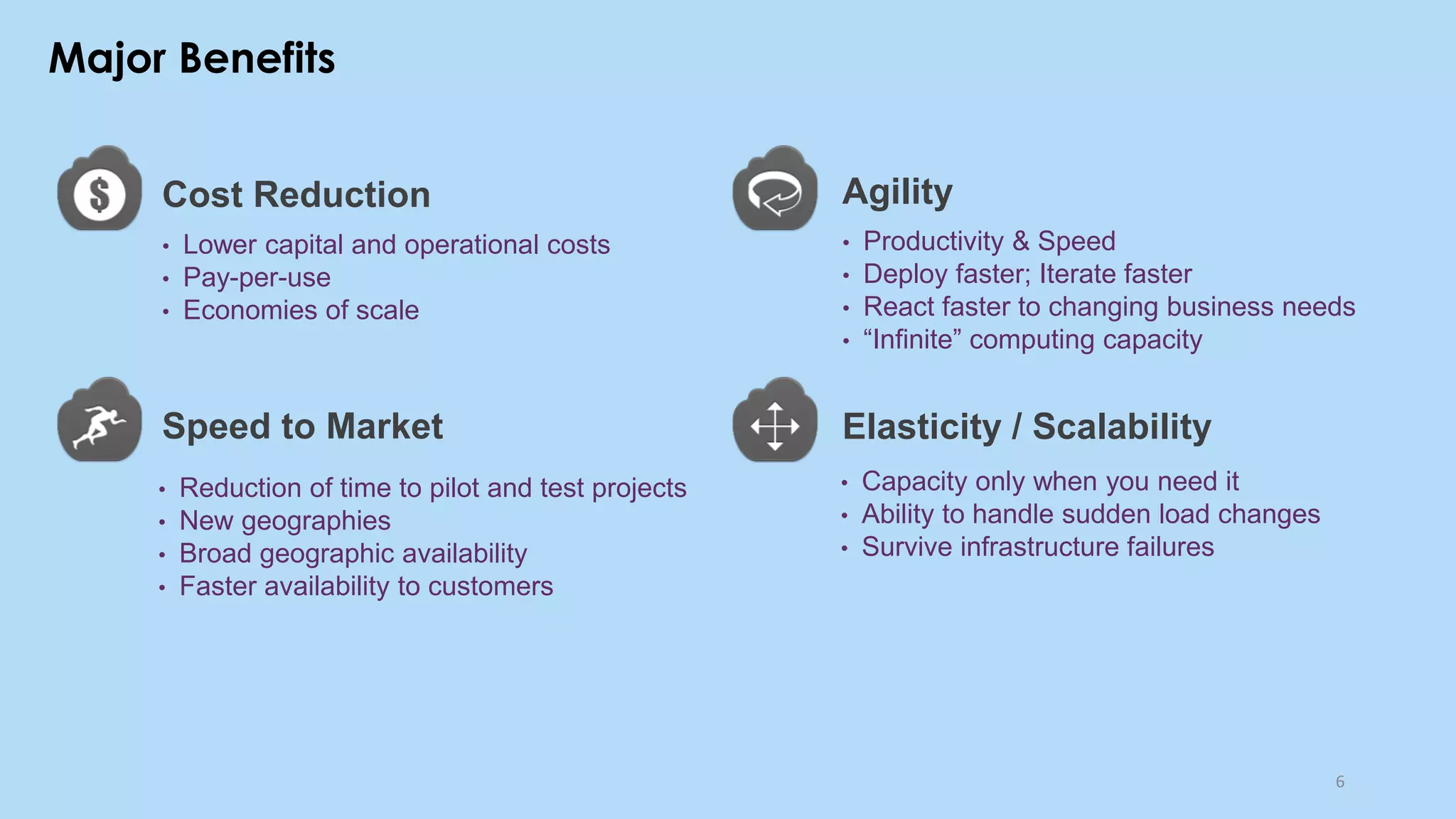
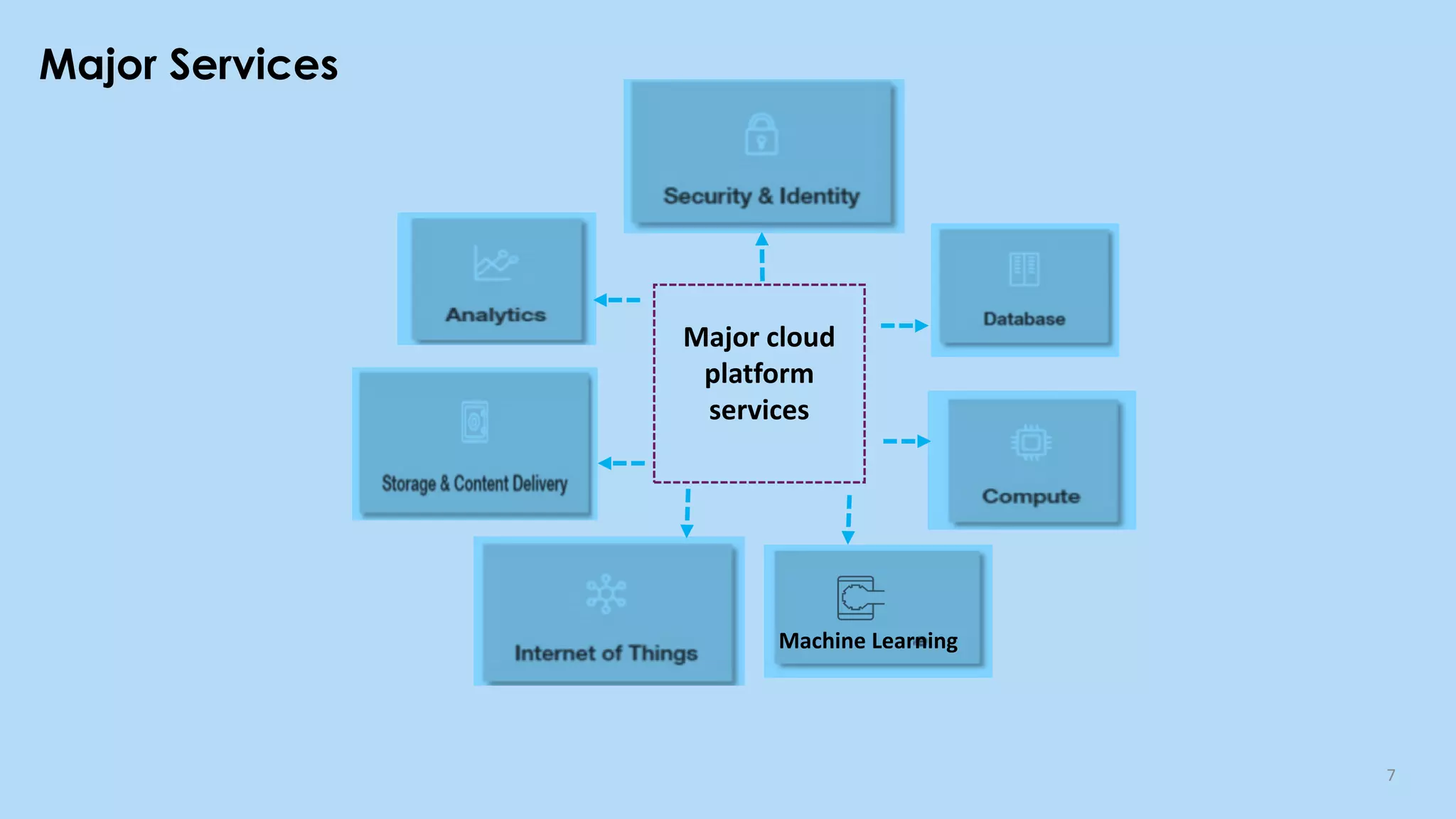
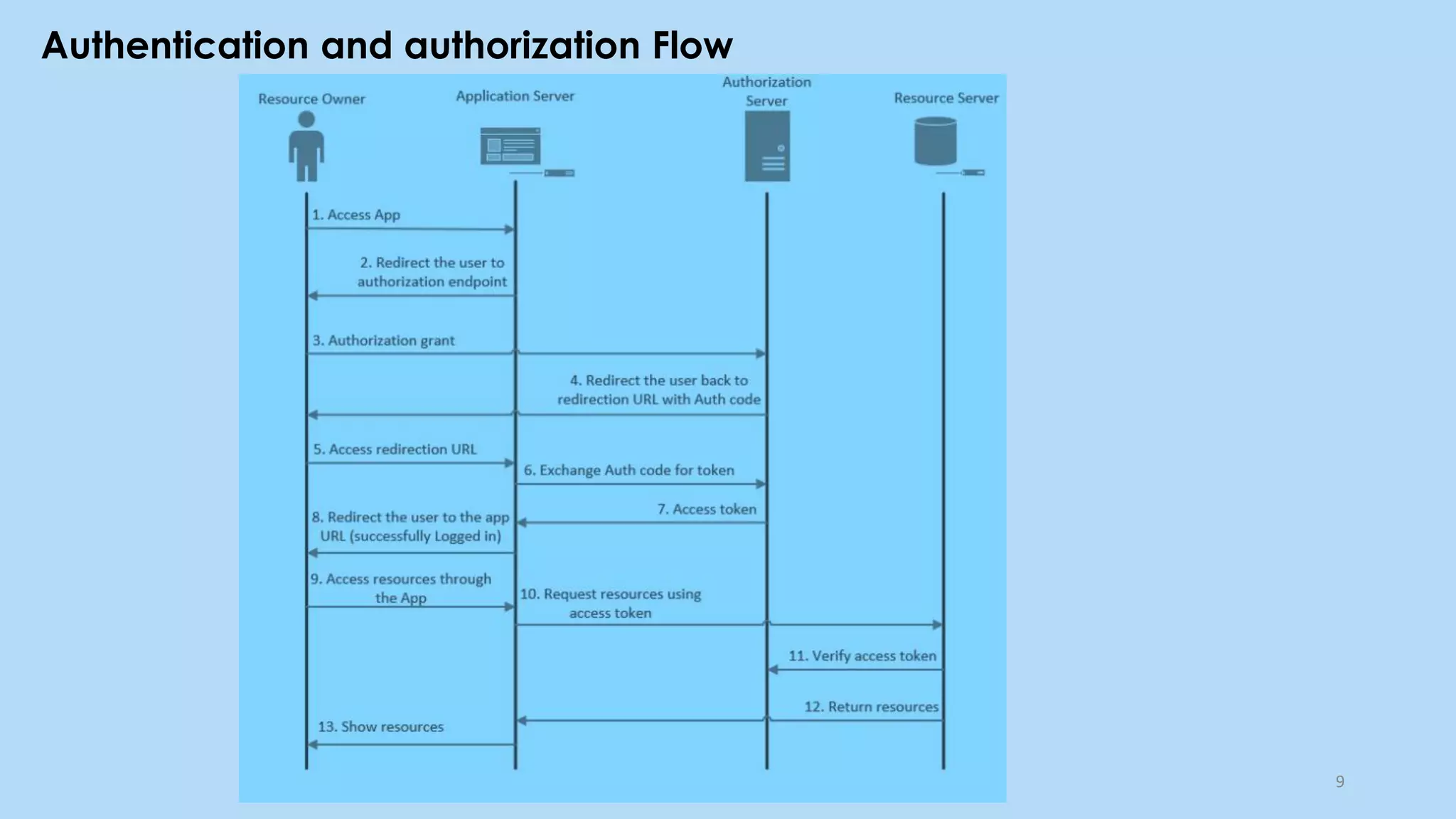
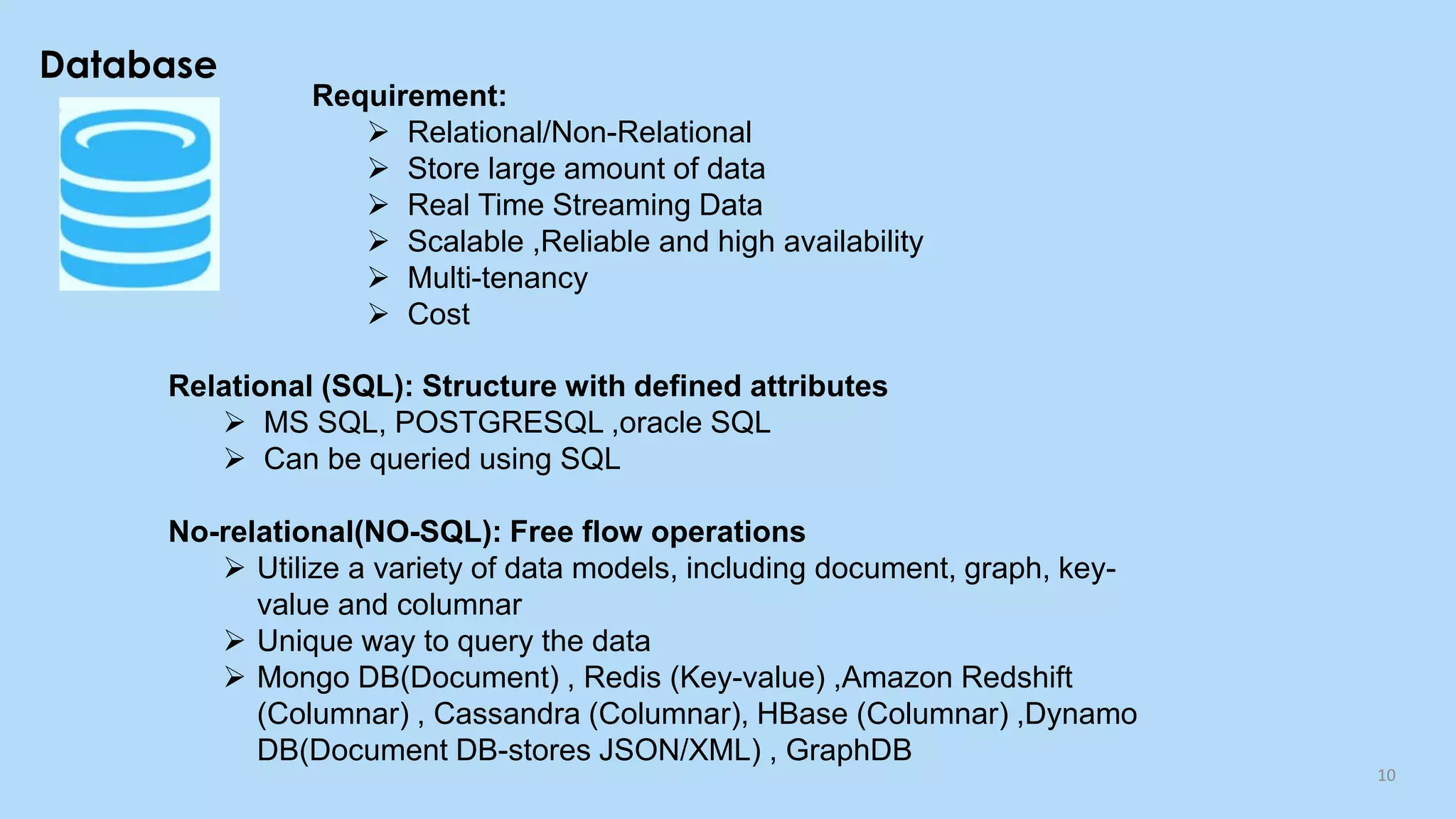
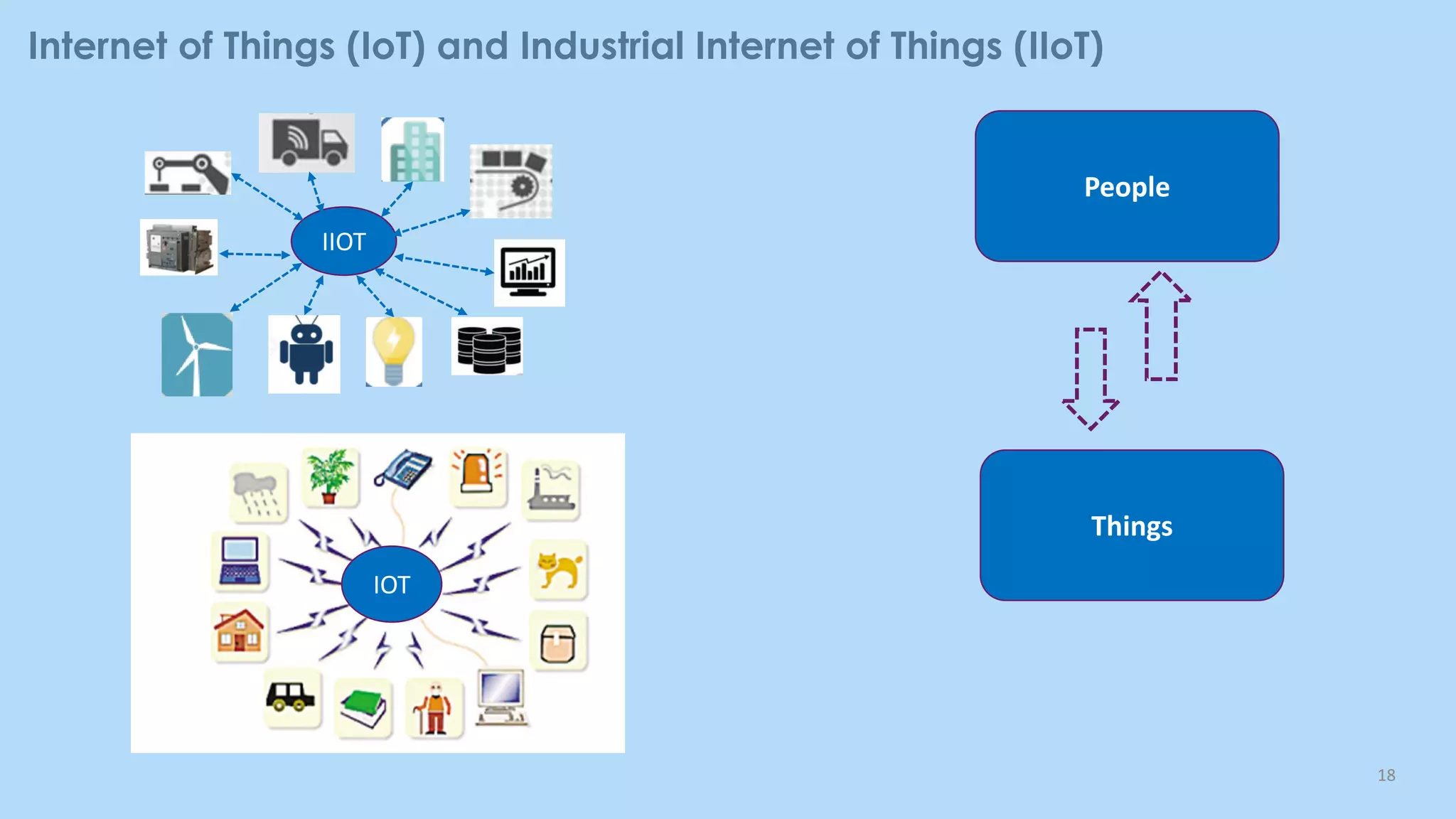
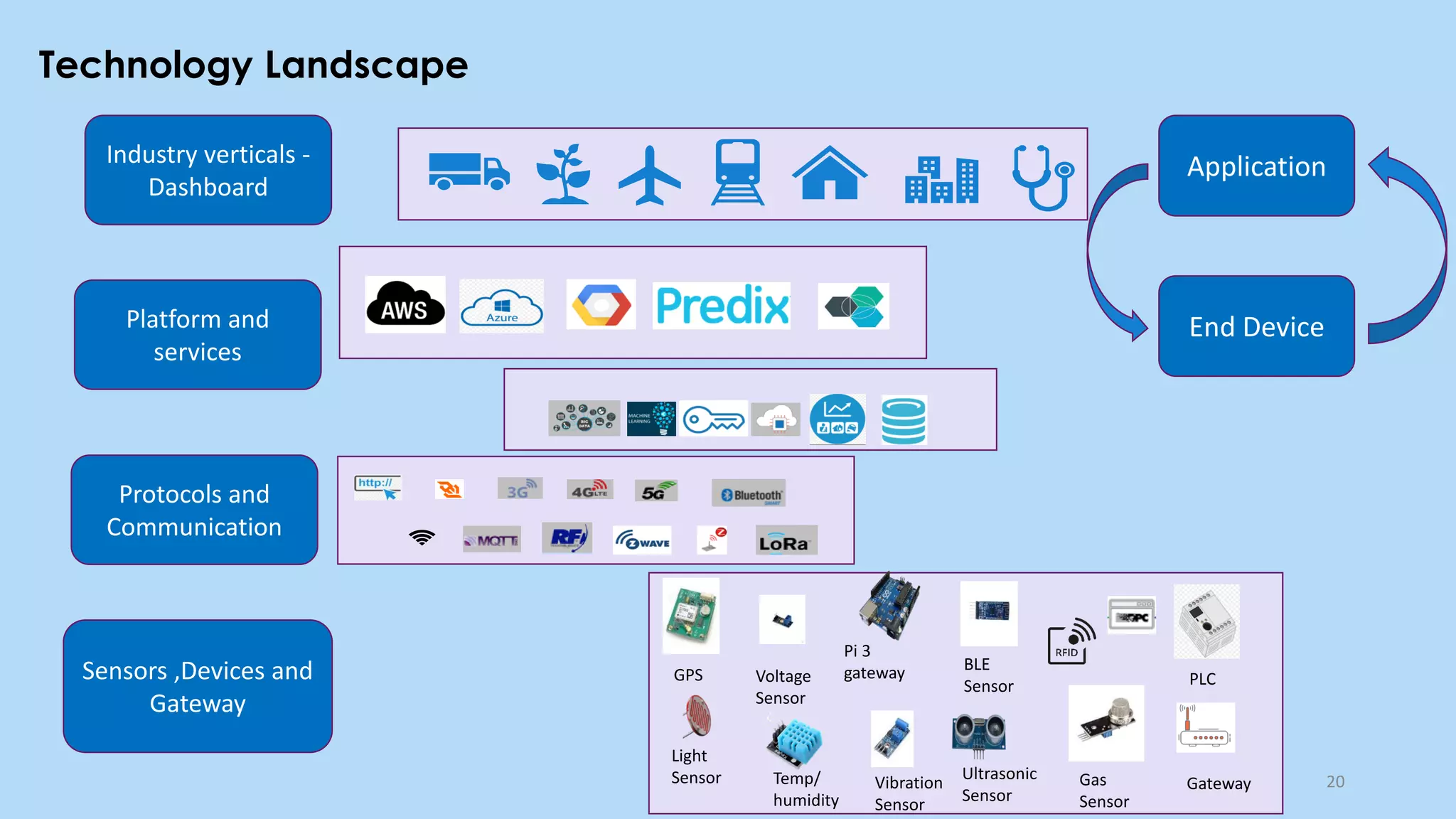
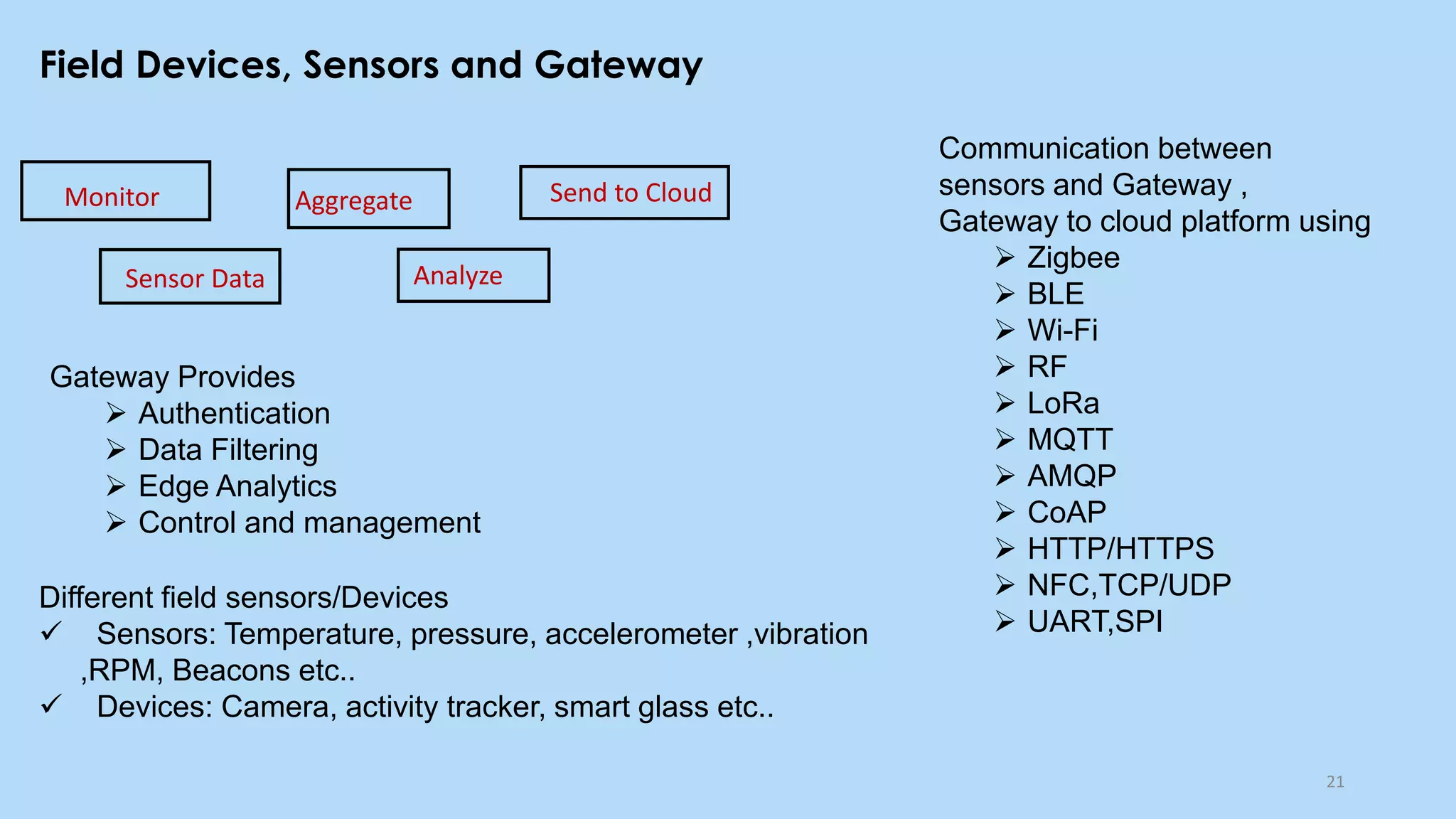
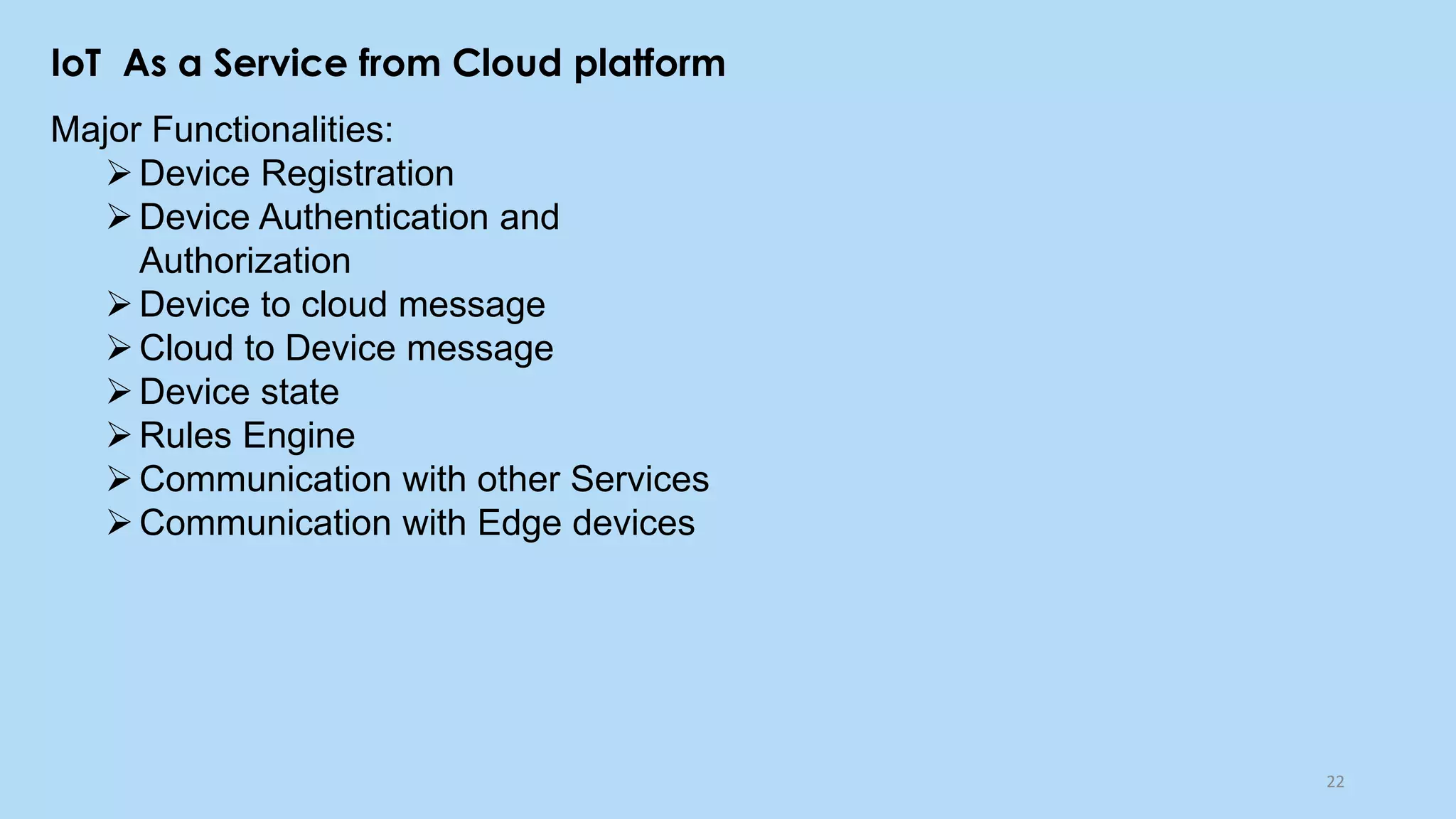
This document provides an overview of cloud computing and the Internet of Things (IoT). It defines cloud computing as the on-demand delivery of computing resources over the Internet. It describes the common cloud service models of SaaS, PaaS, and IaaS. It also discusses characteristics of cloud computing like resource pooling, elasticity, and measured service. The document then introduces IoT and describes components of an IoT system including sensors, gateways, communication protocols, cloud platforms, and applications. It provides examples of services from major cloud platforms and discusses tools for visualizing IoT data.