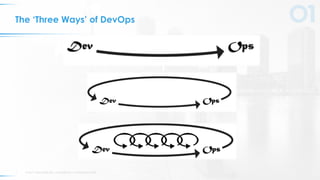
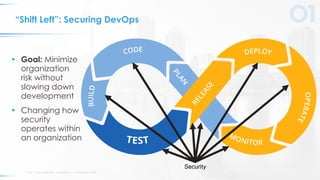
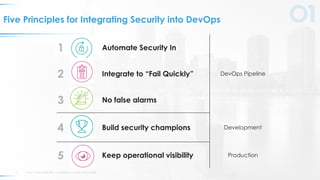
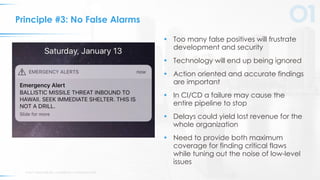
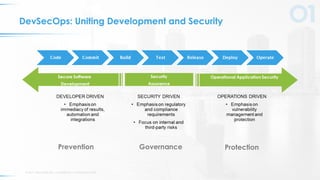
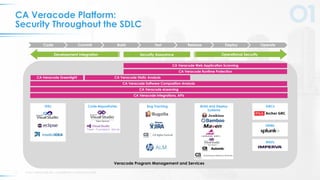
The document outlines five key principles for integrating security into DevOps, focusing on automation, quick failure integration, accurate alerts, building security champions, and maintaining operational visibility. It emphasizes a cultural shift in organizations towards high-velocity software development while addressing security challenges. Ultimately, the approach aims to minimize organizational risks without compromising development speed.