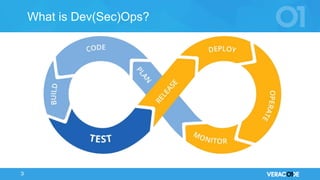
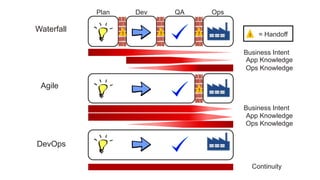
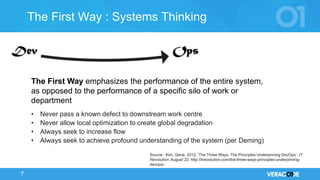
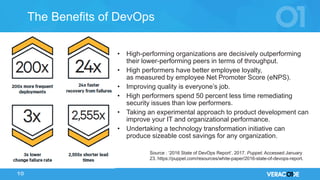
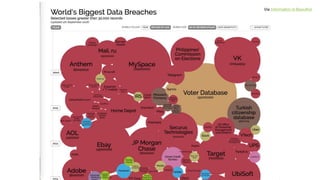
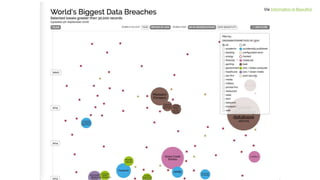
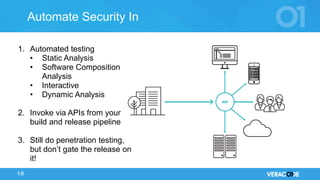
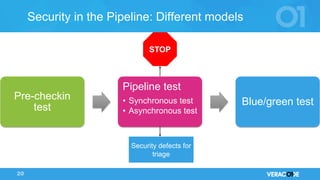
The document discusses the concept of DevOps, emphasizing collaboration between development and operations throughout the service lifecycle. It outlines three key principles of DevOps: systems thinking, amplifying feedback loops, and fostering a culture of continual experimentation and learning. Additionally, it highlights the benefits of implementing DevOps practices, particularly in enhancing security and organizational performance.