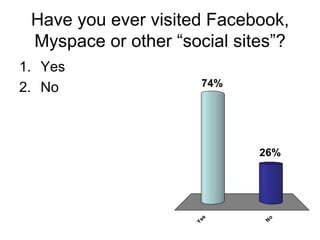
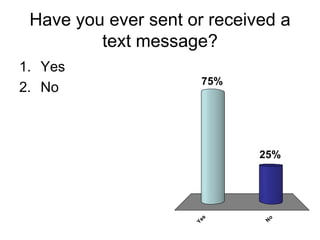
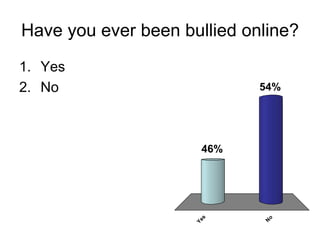
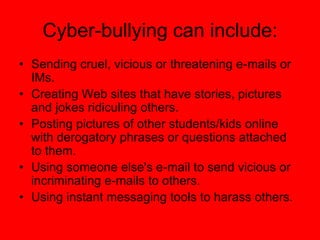
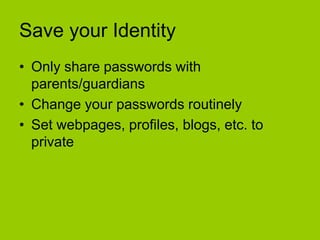
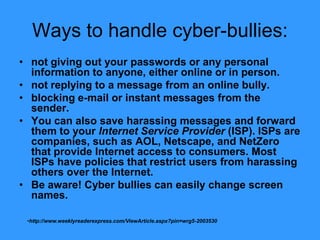
Electronic Safety document provides information and advice to students in grades 4-5 about staying safe online and using cell phones appropriately. It discusses common risks like cyberbullying, inappropriate content, and interacting with strangers. The document encourages students to avoid sharing private information, ignore bullies, and tell a trusted adult if they feel unsafe online or receive harmful messages. It emphasizes the importance of thinking before posting personal details or photos and getting permission before sharing other people's information.