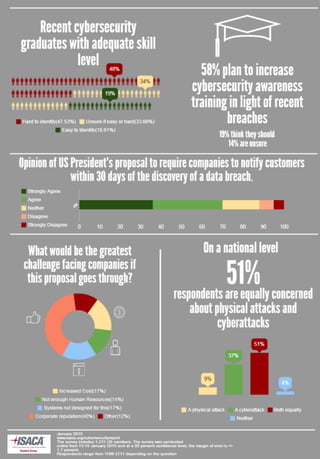
The document discusses the founding and purpose of the ISACA UW student chapter at the University of Washington. It was founded to raise awareness about the importance of information security and risk management. The chapter will provide learning opportunities for students through events with industry professionals and hands-on experience. The goal is to engage students in the field and attract a diverse workforce to address challenges in keeping networks secure.
























![27
Information Security & Risk Managment
Handbook 2016
Gotta sue ‘em all!!
By Divya Kothari
With Information Security becoming ever so vital with each passing day, it is pertinent to keep
yourself abreast of the latest security updates irrespective of your past expertise or existing
knowledge base. In fact you would be surprised by how different sciences can blend in with the field
of security. As a law school graduate, let me share how the realm of jurisprudence, despite being
connected with all walks of life, is especially significant in the world of information and cyber security.
Information Security ensures that within the enterprise, information is protected against
disclosure to unauthorized users (confidentiality), improper modification (integrity), and non‐access
when required (availability). And what we use to ensure this, takes the flavor of law. It may be in the
form of industry standards (eg. PCI DSS) or enforceable compliance (eg. GLBA) or a hybrid of the two
(eg. HIPAA). The fact remains that you need a formalized structure to regulate systems and processes,
which is where legal knowledge steps in.
Let’s take the example of Pokémon Go. Since its release in July 2016, this augmented reality
game has become a worldwide phenomenon. If you were a victim to falling down this rabbit hole, the
symptoms surely included – eyes glued to your phone, distracted walks, constant upward finger flicks
and screen tapping, frustration at not being able to catch that Diglett peeking out of the toilet, or even
accidentally discovering dead bodies! In a nutshell, “unlike the original Nintendo series and most
video games, Pokémon Go requires physical exploration…The combined effect is part bird-watching,
part geocaching, part trophy hunting, with a heavy dose of mid-1990s nostalgia.” And naturally
several law suits. At another extreme, Gerry Beyer, Professor of Law at Texas Tech University warns
that “death by Pokémon is coming…Pokémon users will have all sorts of accidents as they use the
program while walking, biking, driving, etc…”
With Niantic assigning private property as Pokestops and Gyms, there have been several class
action law suits claiming nuisance and a claim in the profit share amongst other things. Another
controversial aspect is embedded within their Terms of Service. “In order to opt out [of the arbitration
clause] users must send an email within 30 days of their agreement to the terms, with “Arbitration
Opt-out Notice” in the subject line. Failure to do so “…will be deemed to have knowingly and
intentionally waived your right to litigate…”
3
4
5
1
2
6
ISACA UW](https://image.slidesharecdn.com/27691f25-6800-481b-bd65-24b98016a84f-161109221136/85/ISACA-UW-Handbook-2016-27-320.jpg)









![References
4. Rubino, K., “Pokemon Go Could Kill You, Warns Law Professor,” in Above the Law, July 18,
2016. Retrieved from: http://above thelaw.com/2016/07/pokemon-go-could-kill-you-warns-law-
professor/?rf=1
5. RT Question more, August 17, 2016. Retrieved from: https://www.rt.com/usa/356204-
pokemon-go-away-homeowners-sue/
6. Ha-Redeye, O., “Preserving Your Legal Rights Against Pokemon Go,” in Slaw CA, July 17,
2016. Retrieved from: http://www.slaw.ca/2016/07/17/preserving-your-legal-rights-against-
pokemon-go/
7. Schlossberg J. & Gavejian J., “Next Stop for Pokemon Go: Regulation & Litigation?,” in
Jackson|Lewis, August 1, 2016. Retrieved from: http://www.jacksonlewis.com/publication/next-
stop-pok-mon-go-regulation-litigation
8. Ibidem
9. Gouriet v Union of Post Office Workers and Others [1977] CA
ISACA UW](https://image.slidesharecdn.com/27691f25-6800-481b-bd65-24b98016a84f-161109221136/85/ISACA-UW-Handbook-2016-38-320.jpg)