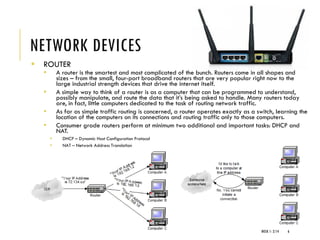
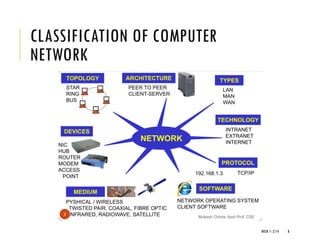
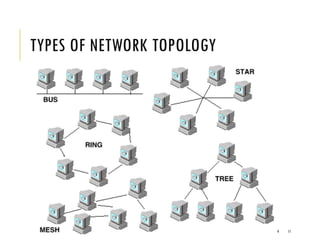
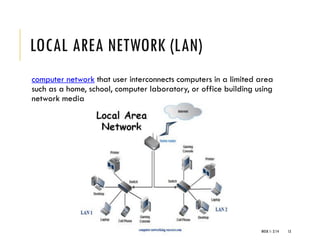
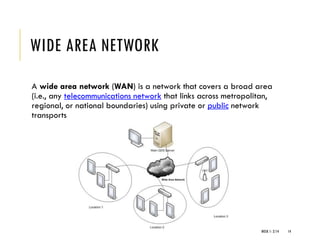
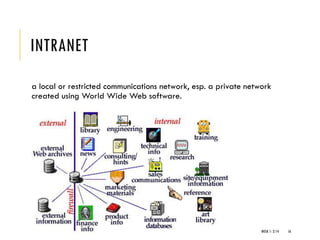
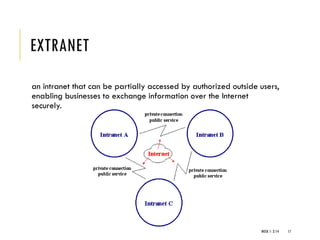
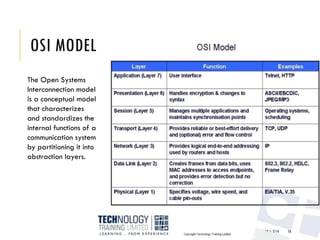
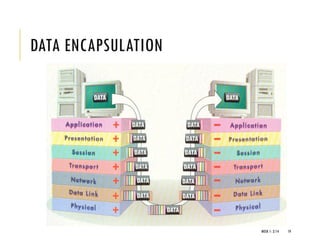
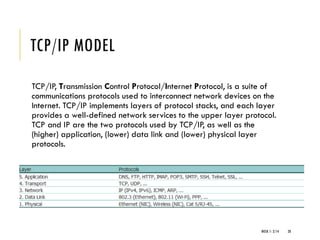
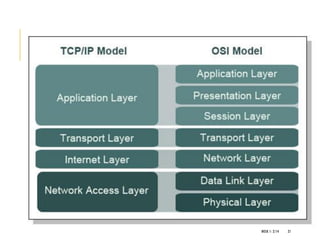
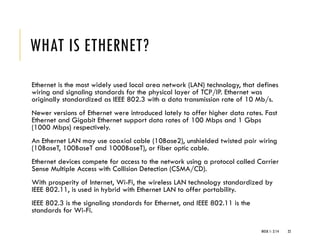
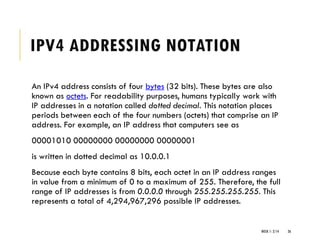
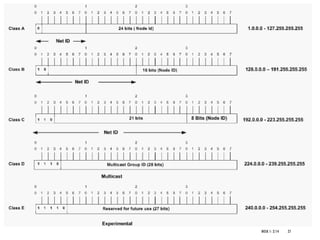
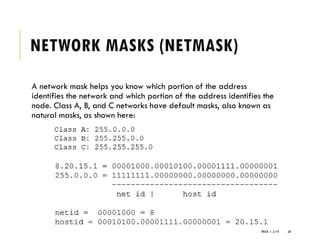
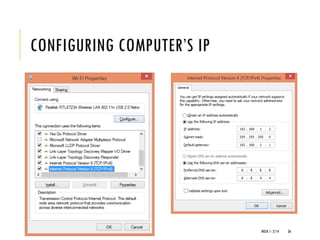
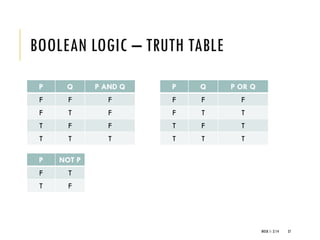
The document provides an introduction to data communication and computer networking, covering essential concepts such as network devices (hubs, switches, routers), network topologies, and types of networks (LAN, WAN, MAN). It explains IP addressing, including IPv4 and IPv6, subnetting, and the functionality of DHCP. Additionally, it highlights the importance of public and private IP addresses and the concept of loopback addressing.