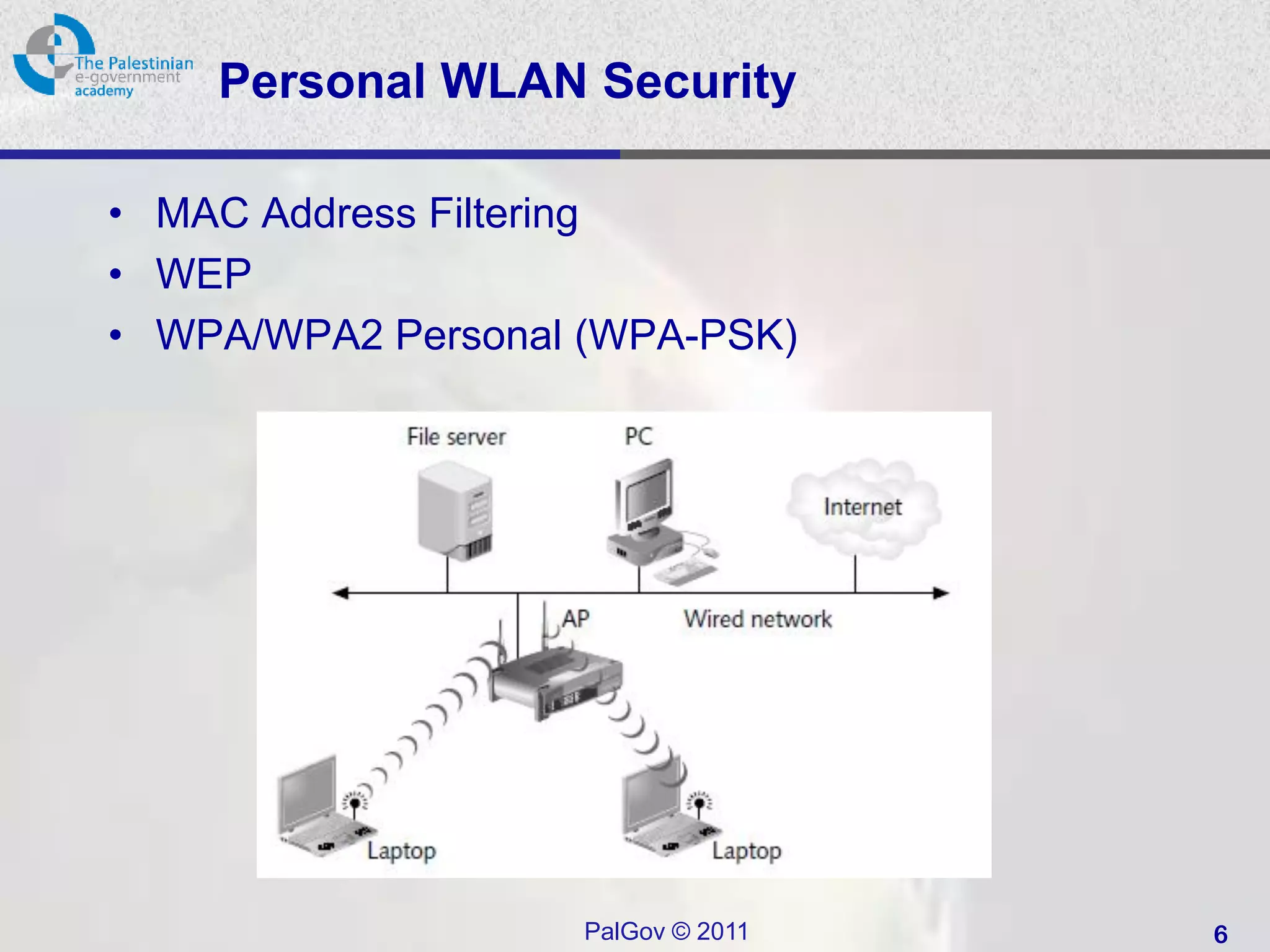
This document provides instructions for setting up wireless security using WPA2 Enterprise authentication with a FreeRADIUS server on Ubuntu. It describes installing and configuring FreeRADIUS, adding a test user, and testing the RADIUS server. It then explains configuring the FreeRADIUS server to accept the wireless access point as a client and restarting the service. Finally, it states that the access point needs to be configured to send authentication requests to the RADIUS server IP address and to use the test user credentials for client testing.