This document provides an overview of access control and database security. It discusses different access control models including discretionary access control, mandatory access control, role-based access control, and attribute-based access control. It also covers access control elements, functions, and examples of how access control is implemented in UNIX and Windows systems. The document then discusses database security topics like relational databases, SQL, database access controls, and statistical database security and inference problems. It concludes with sections on database encryption and homomorphic encryption.



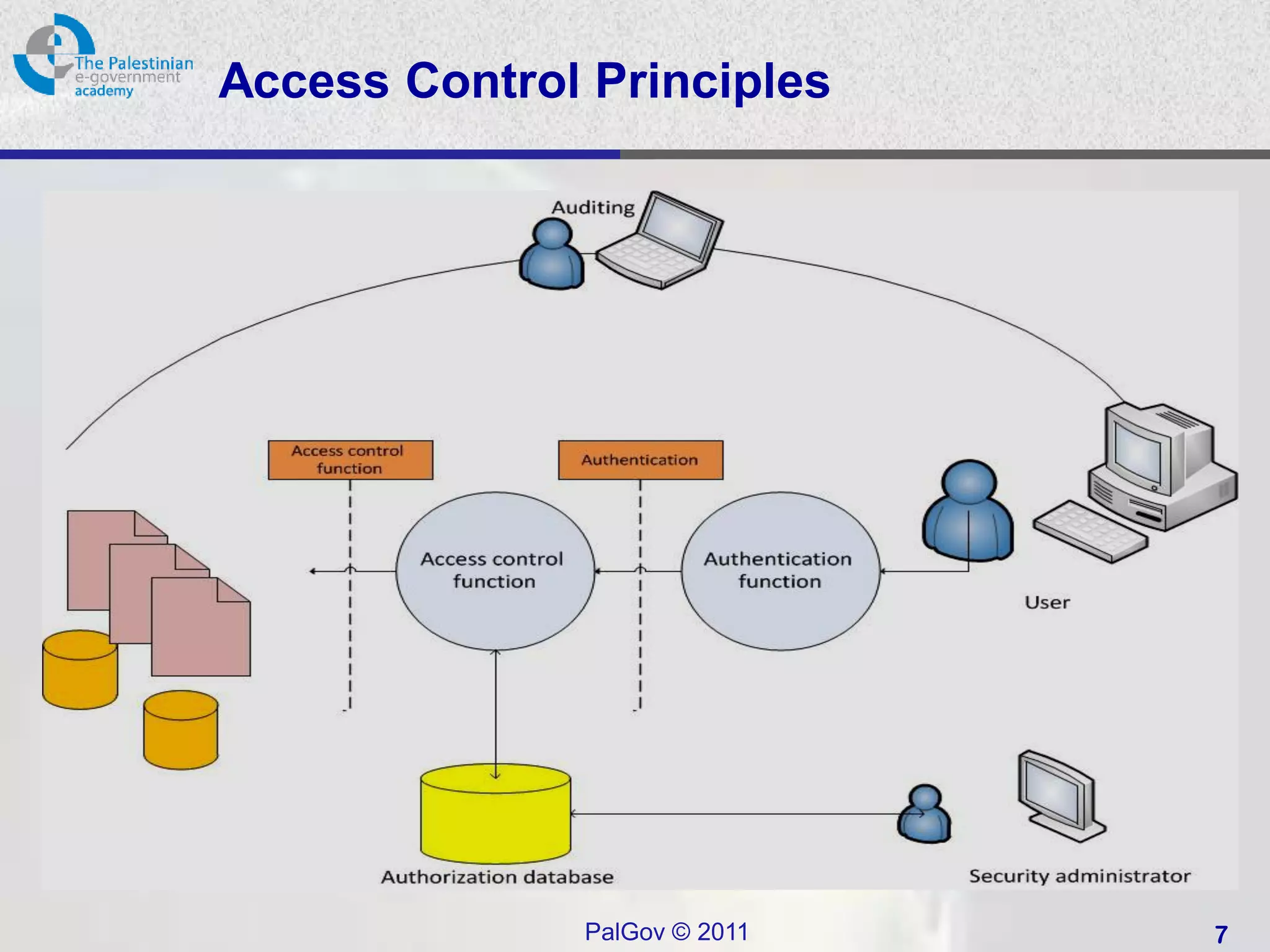
![Access Control
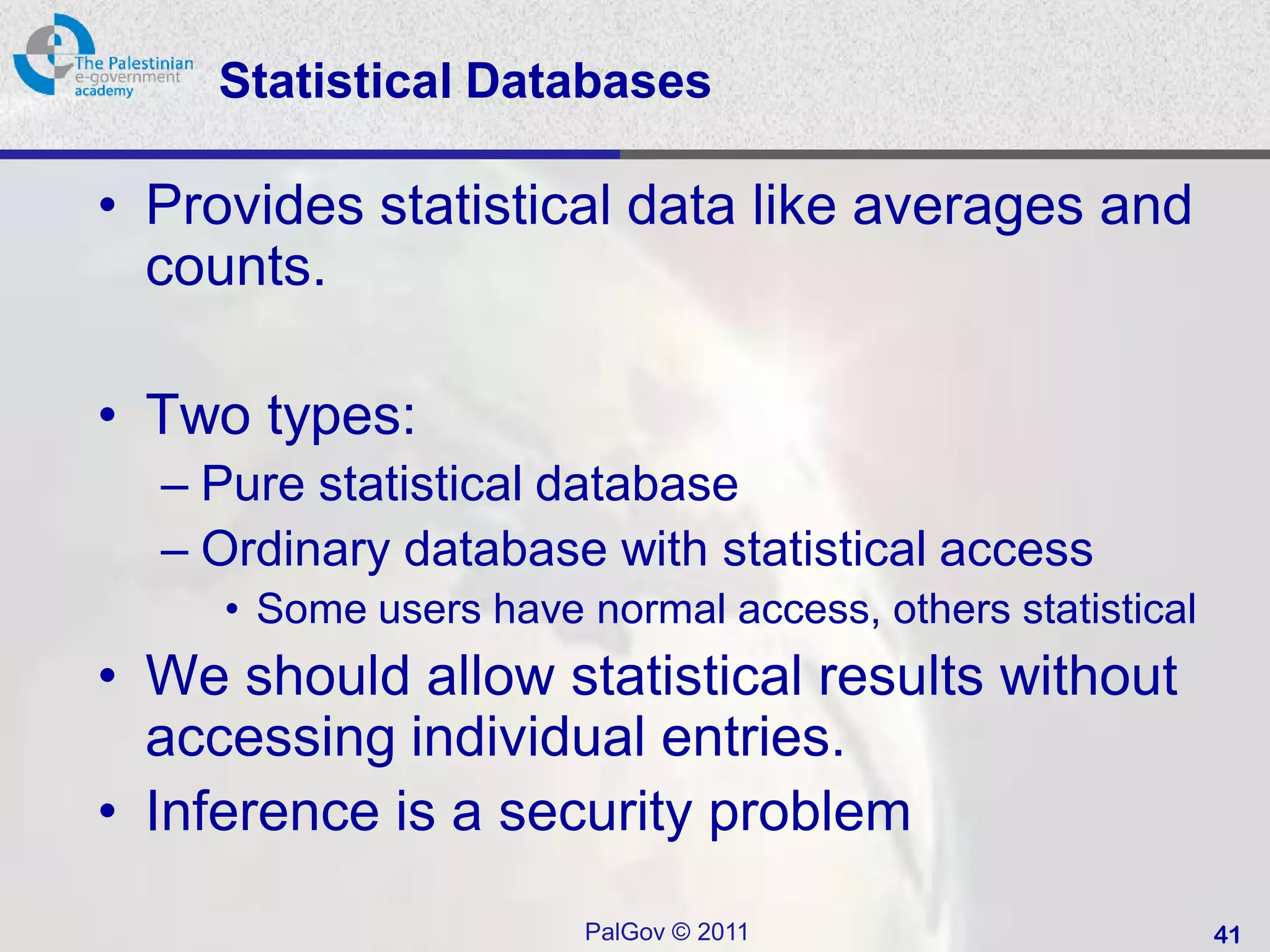
• “The prevention of unauthorized use of a
resource, including the prevention of use of
a resource in an unauthorized manner“ [1]
• Central element of computer security
• Systems have users and groups
– Authenticate to system
– Assigned access rights to certain resources on
system
– Logging and auditing is very important (why?)
1. Computer Security: Principles and Practice, by William Stallings and Lawrie Brown. Published by Pearson/Prentice Hall, © 2008.
ISBN: 0-13-600424-5.
PalGov © 2011 6](https://image.slidesharecdn.com/egovsecuritytutsession11-120312052600-phpapp02/75/E-gov-security_tut_session_11-6-2048.jpg)
![Different Access Control Policies
• Discretionary access control (DAC):
– an entity might have access rights that permit another
entity to access some resource (done by its own volition).
• Mandatory access control (MAC):
– may not enable another entity to access that resource.
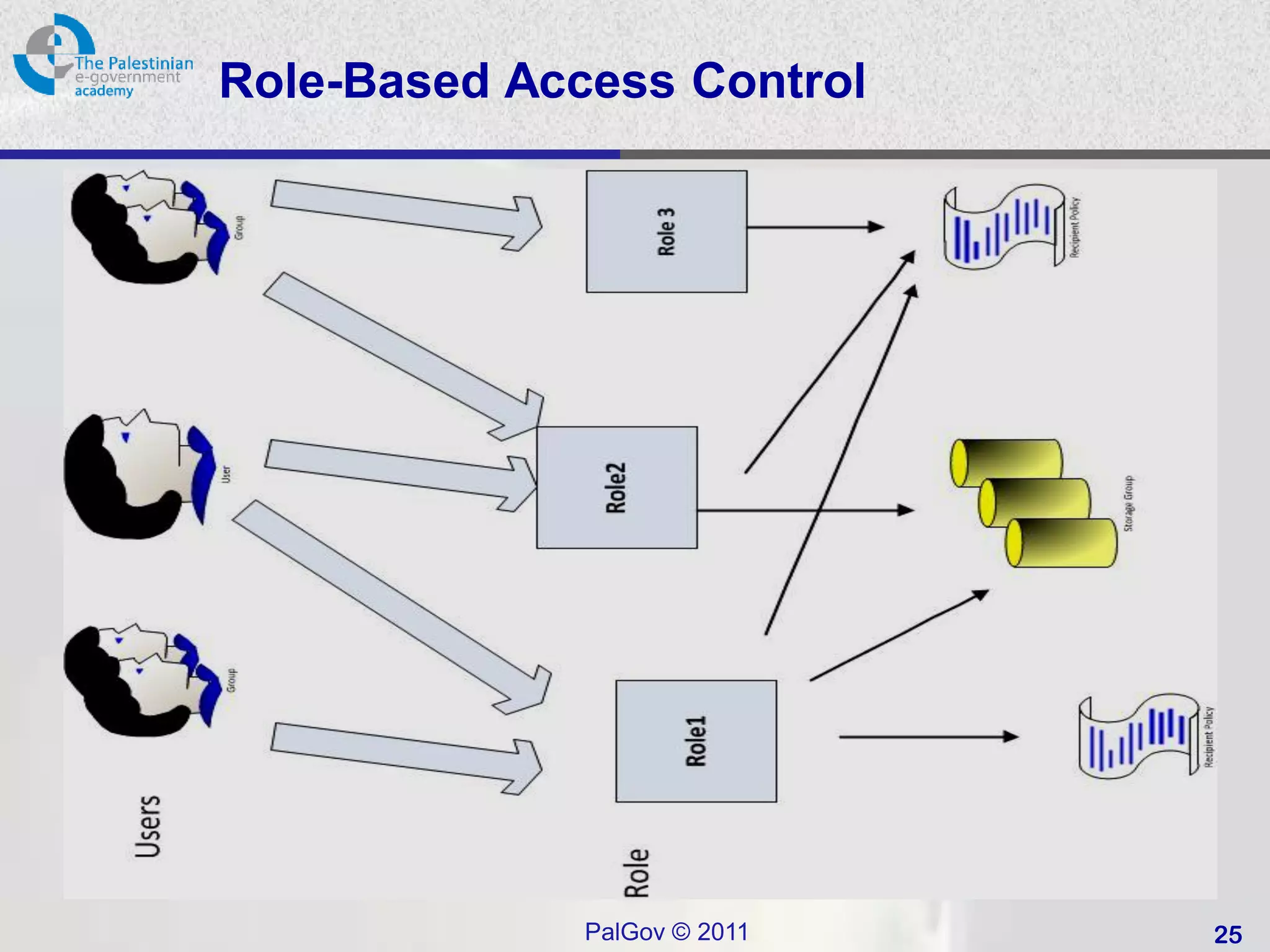
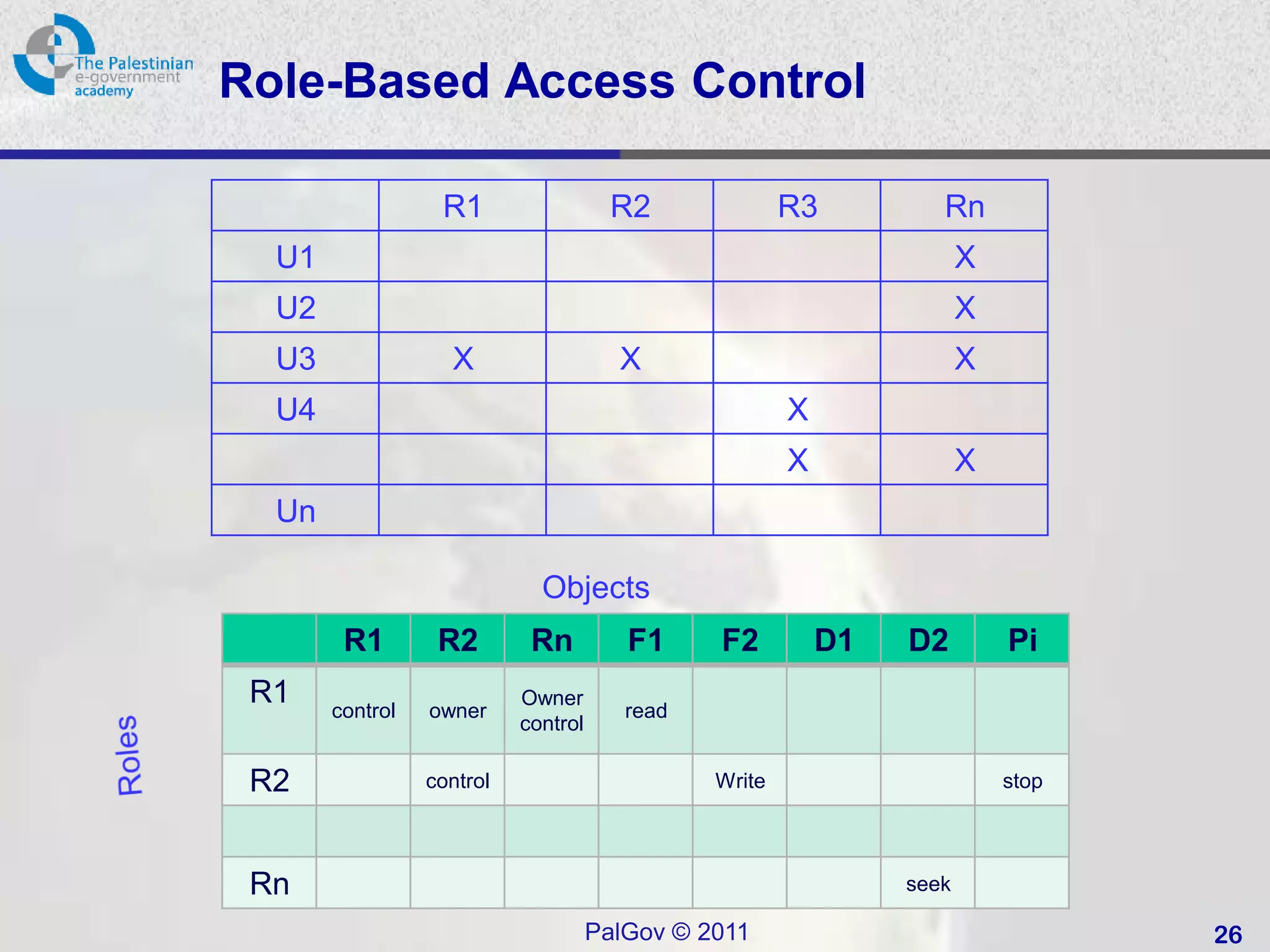
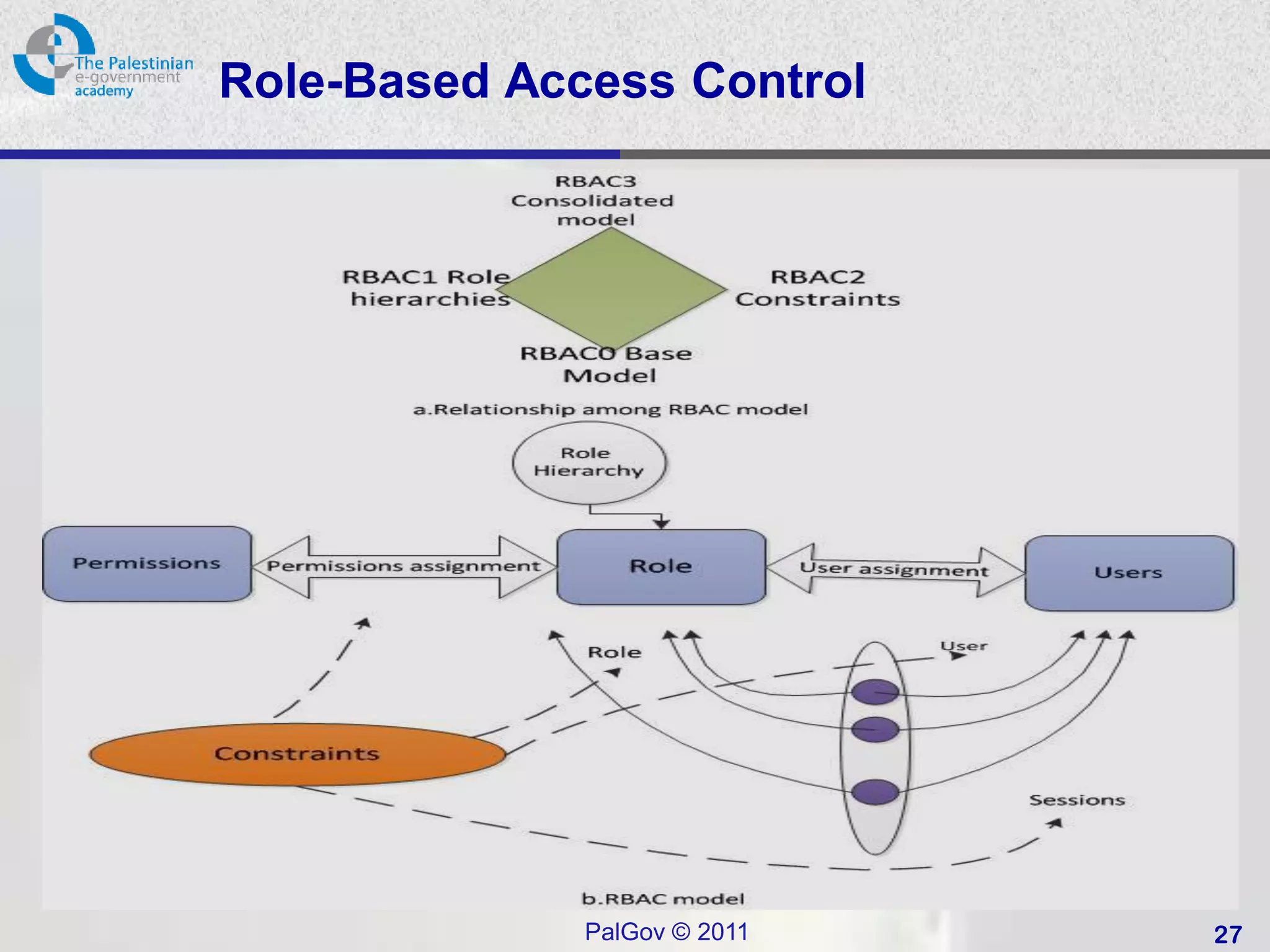
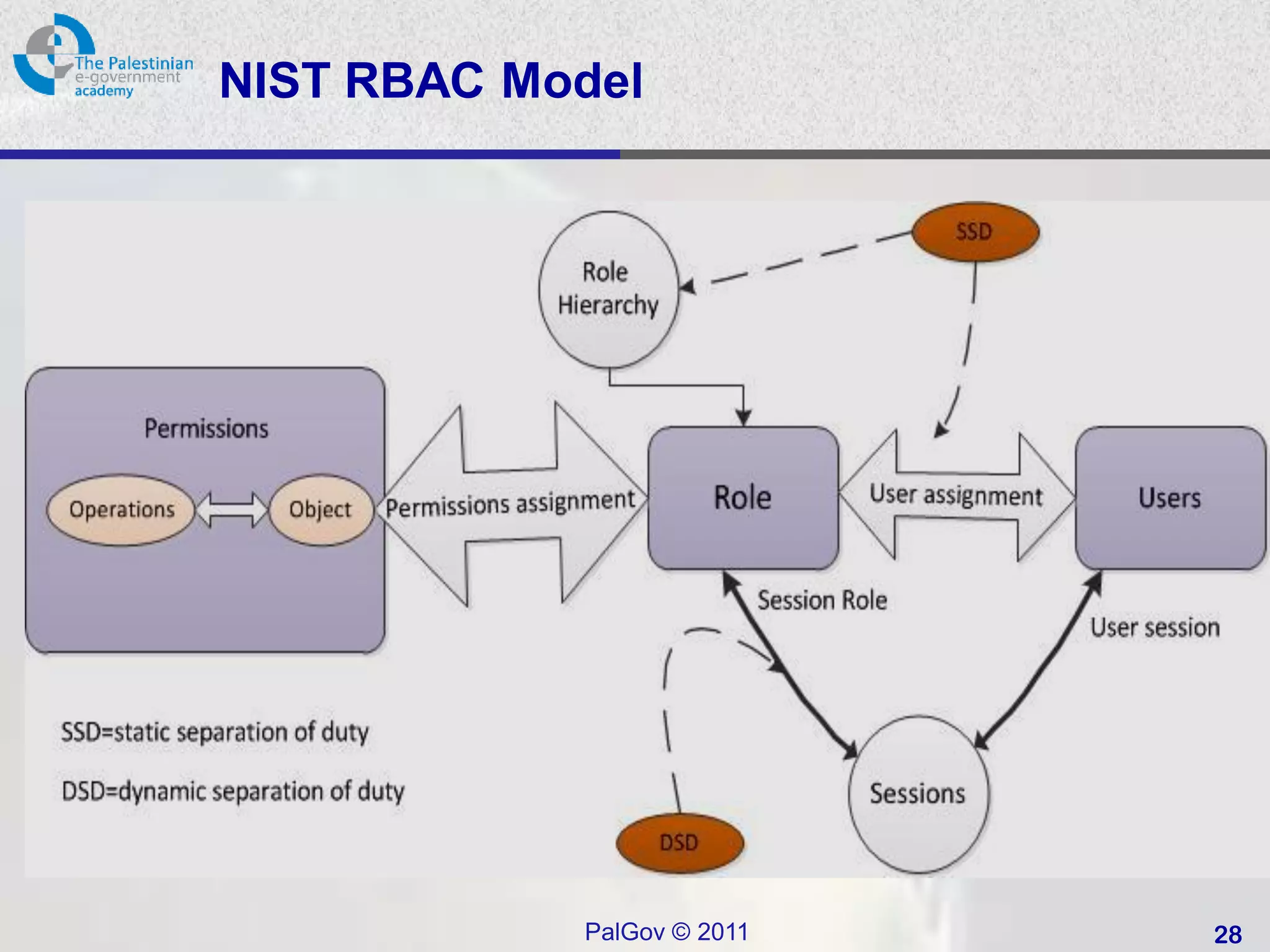
• Role-based access control (RBAC):
– based on the roles.
– ABAC: Administrative RBACK .
(See [2] The ARBAC97 model for role-based administration of roles for more details)
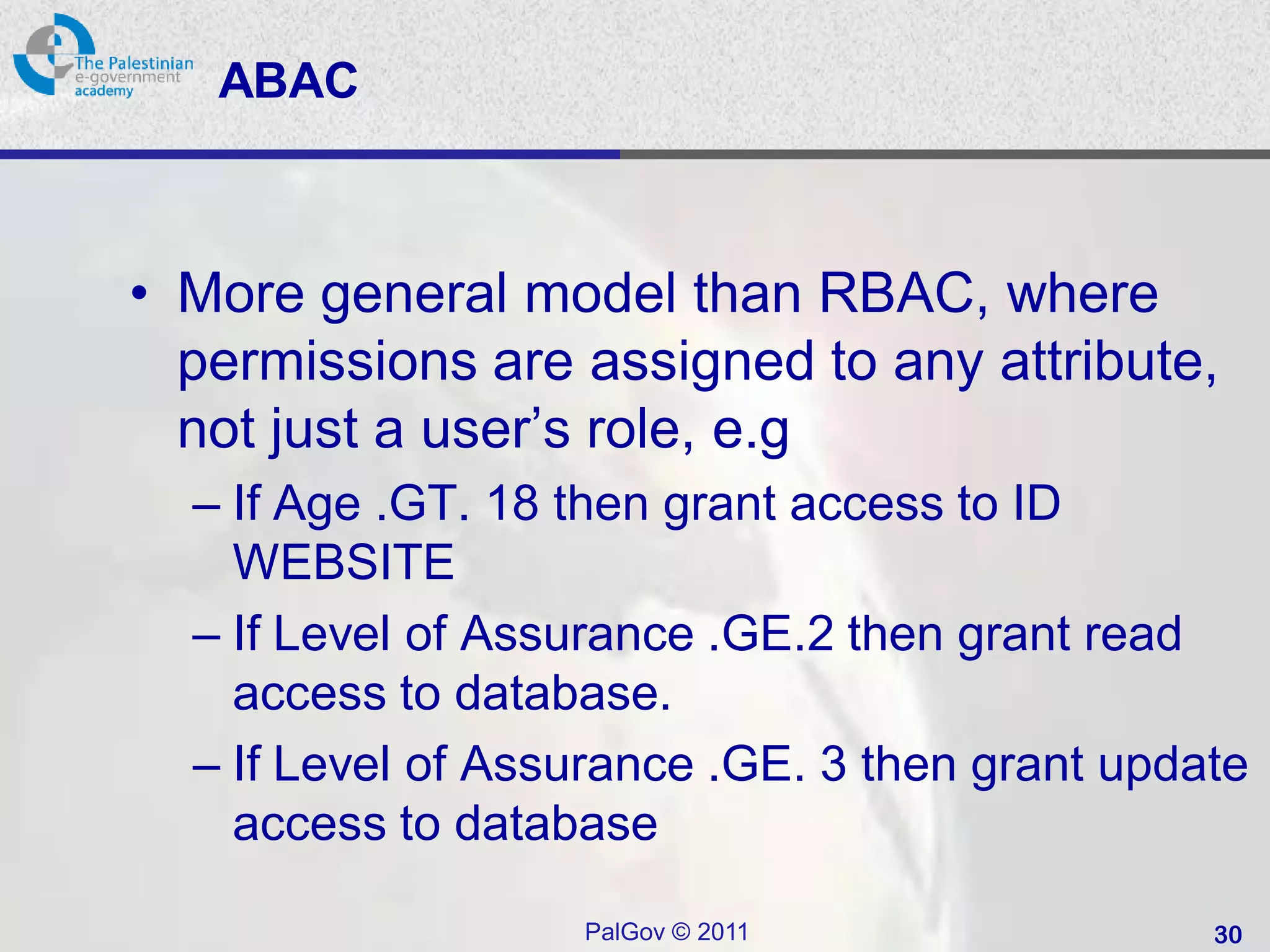
• Attribute Based Access Control (ABAC):
– Generalisation of RBAC to use any attributes
PalGov © 2011 8](https://image.slidesharecdn.com/egovsecuritytutsession11-120312052600-phpapp02/75/E-gov-security_tut_session_11-8-2048.jpg)



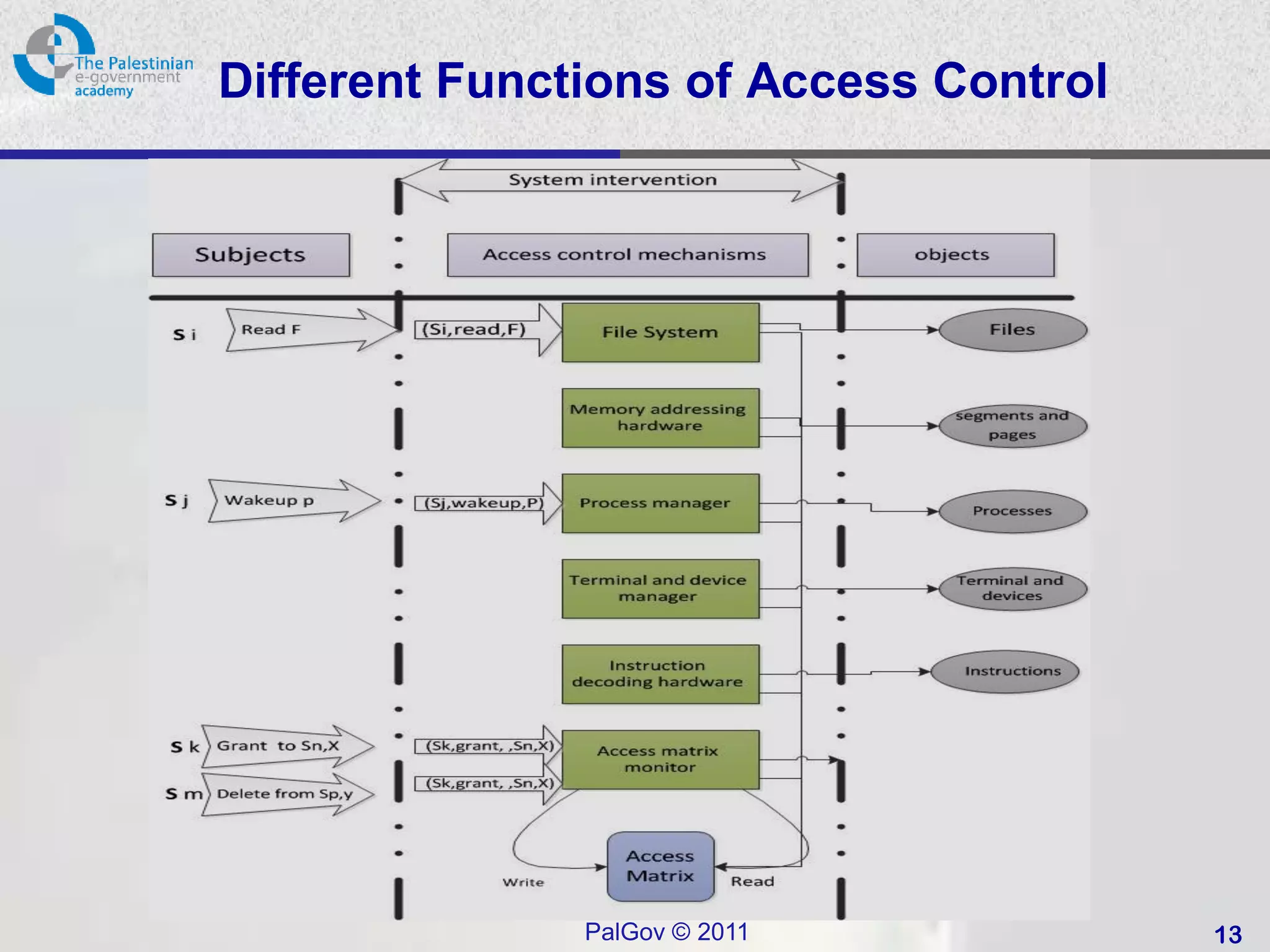
![Access Control Model
Access Control Model [1]
1. Computer Security: Principles and Practice, by William Stallings and Lawrie Brown. Published by Pearson/Prentice Hall, © 2008.
ISBN: 0-13-600424-5.
PalGov © 2011 12](https://image.slidesharecdn.com/egovsecuritytutsession11-120312052600-phpapp02/75/E-gov-security_tut_session_11-12-2048.jpg)


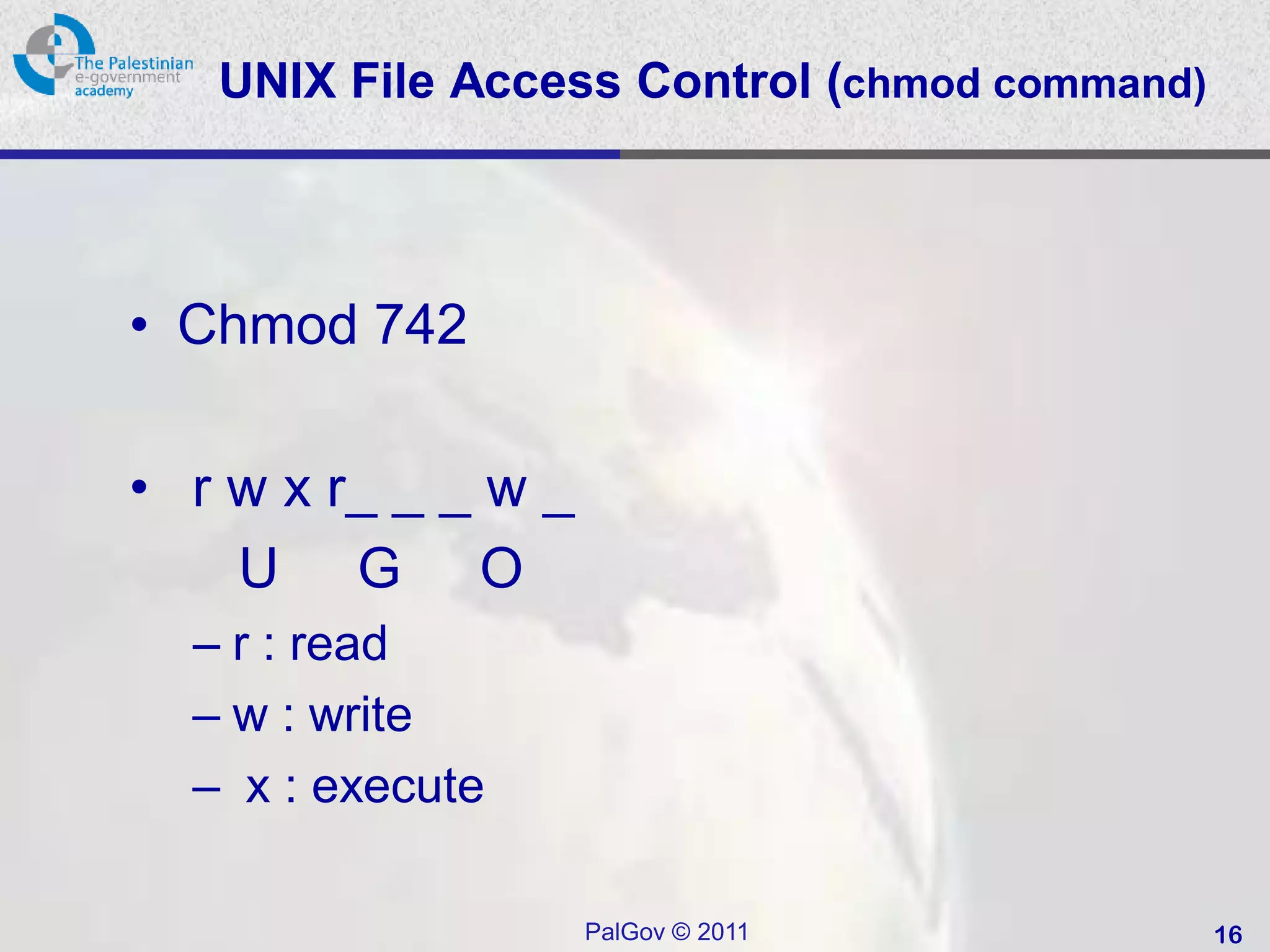






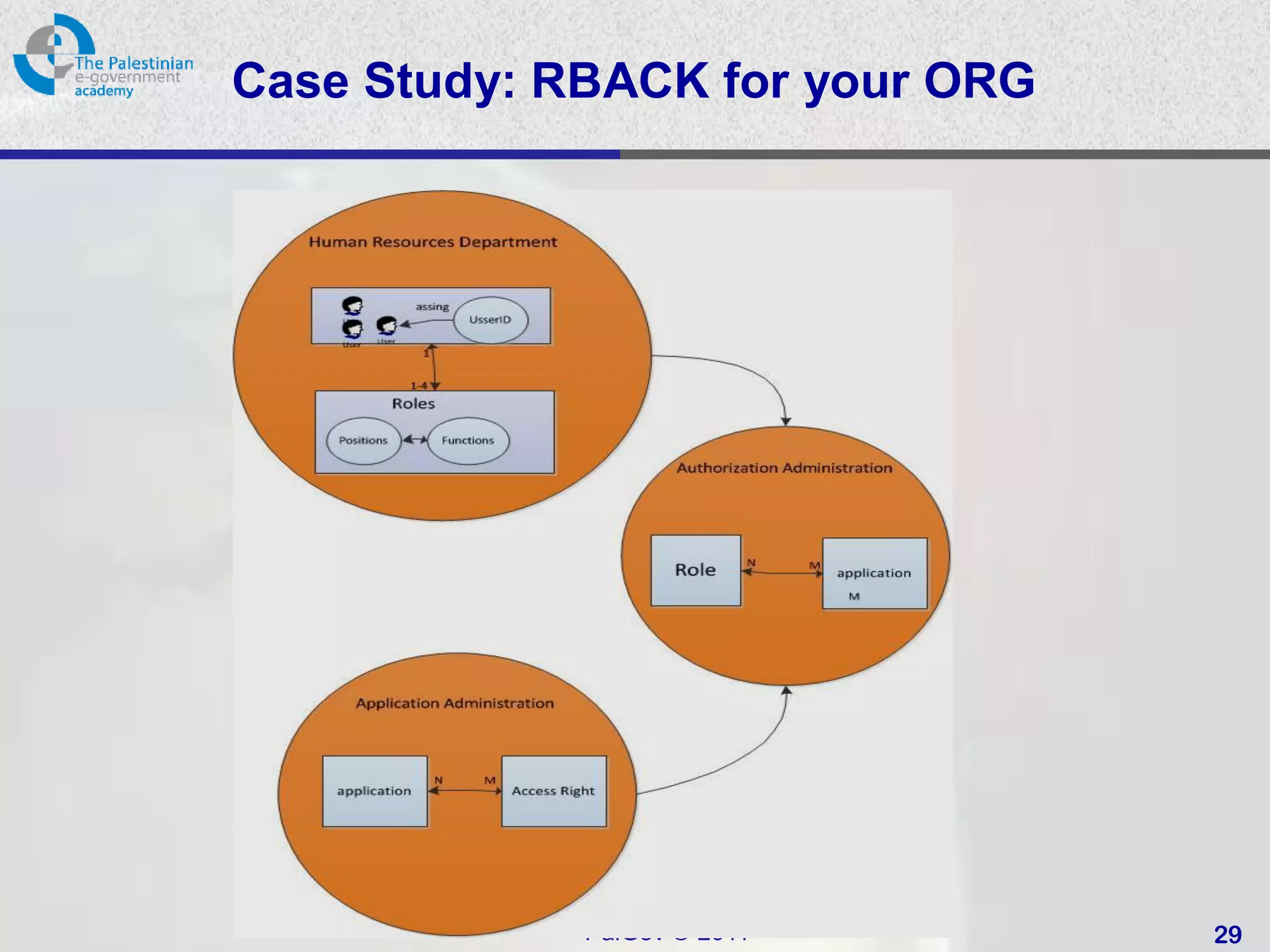

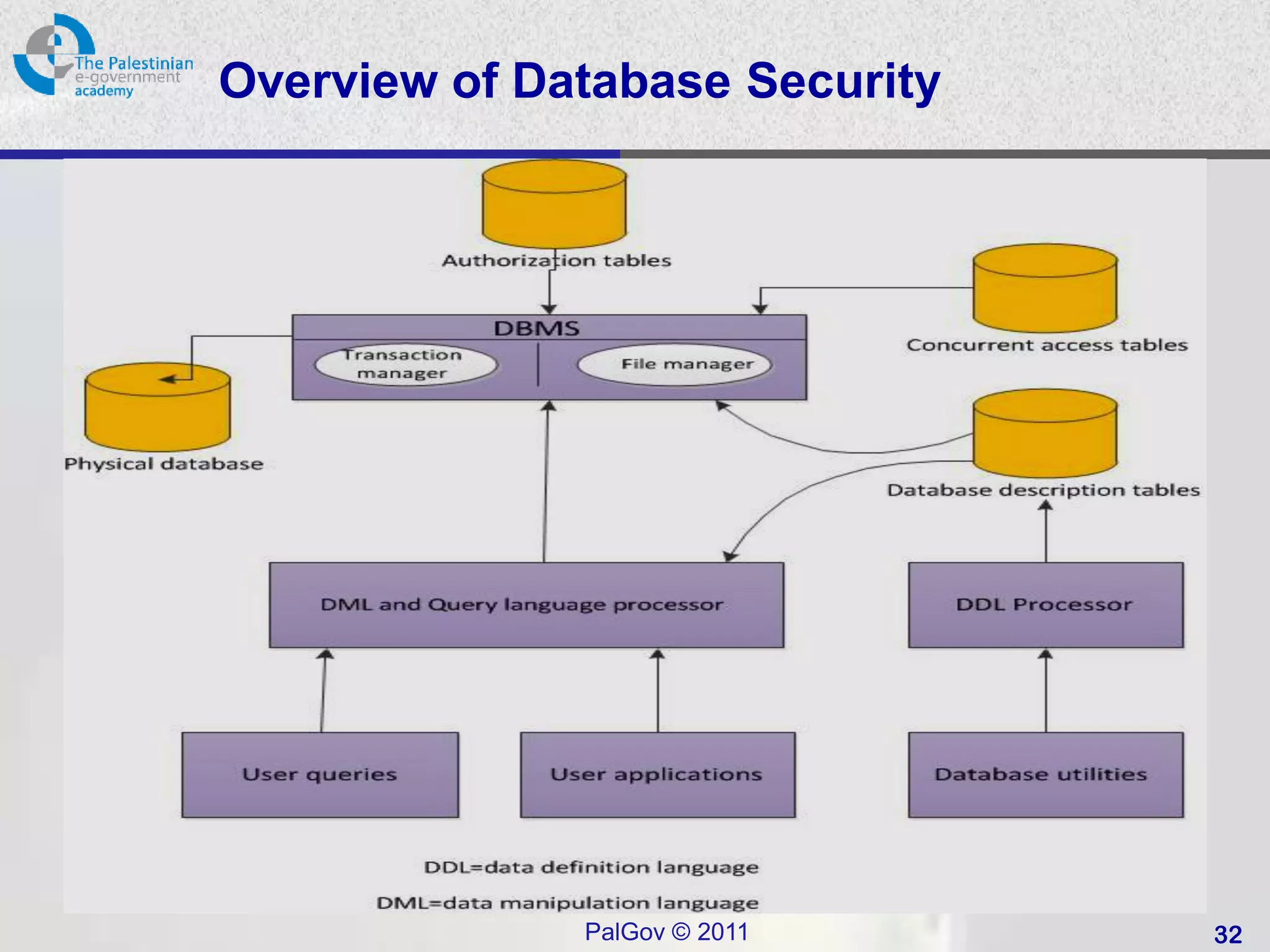
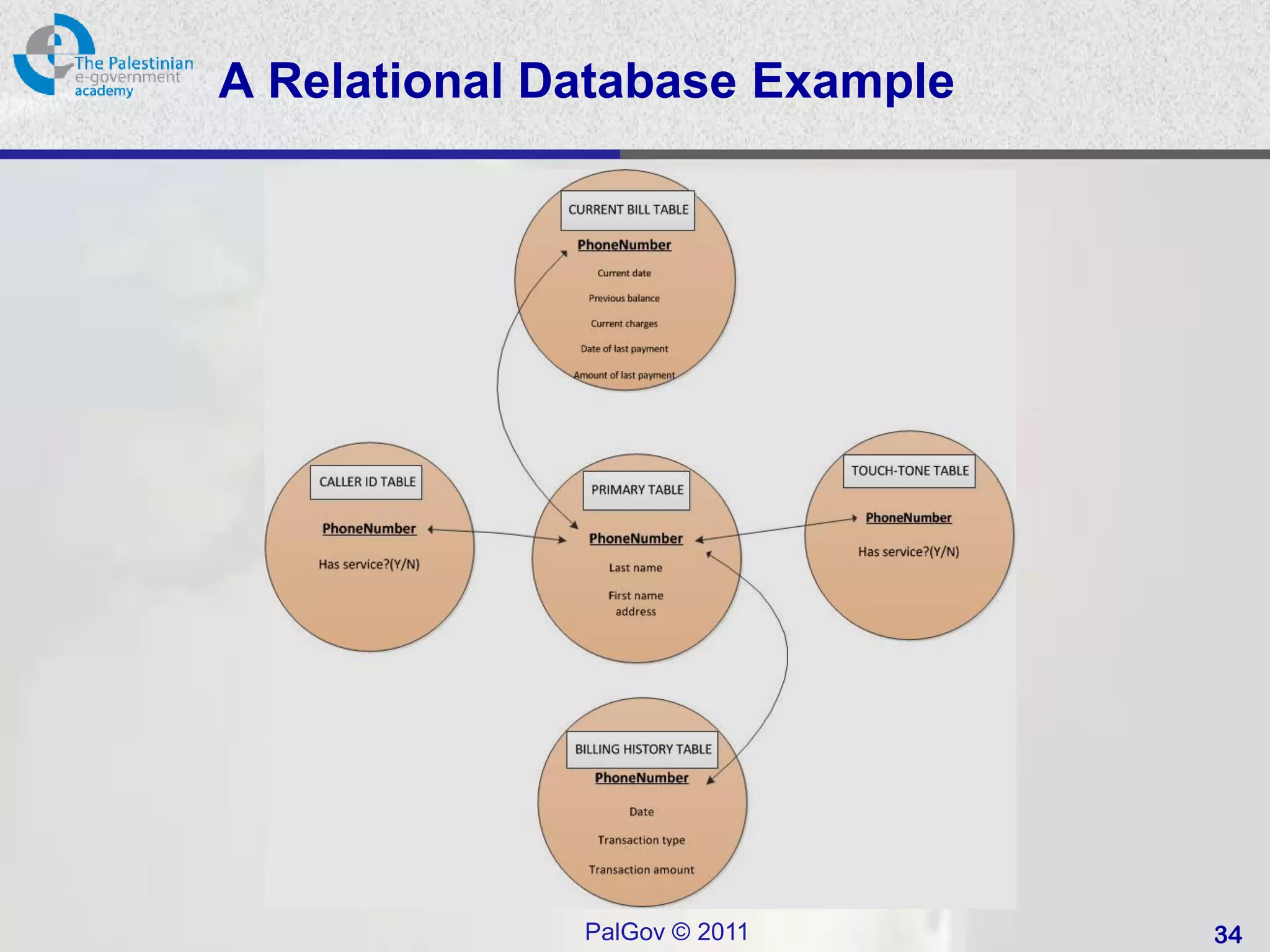
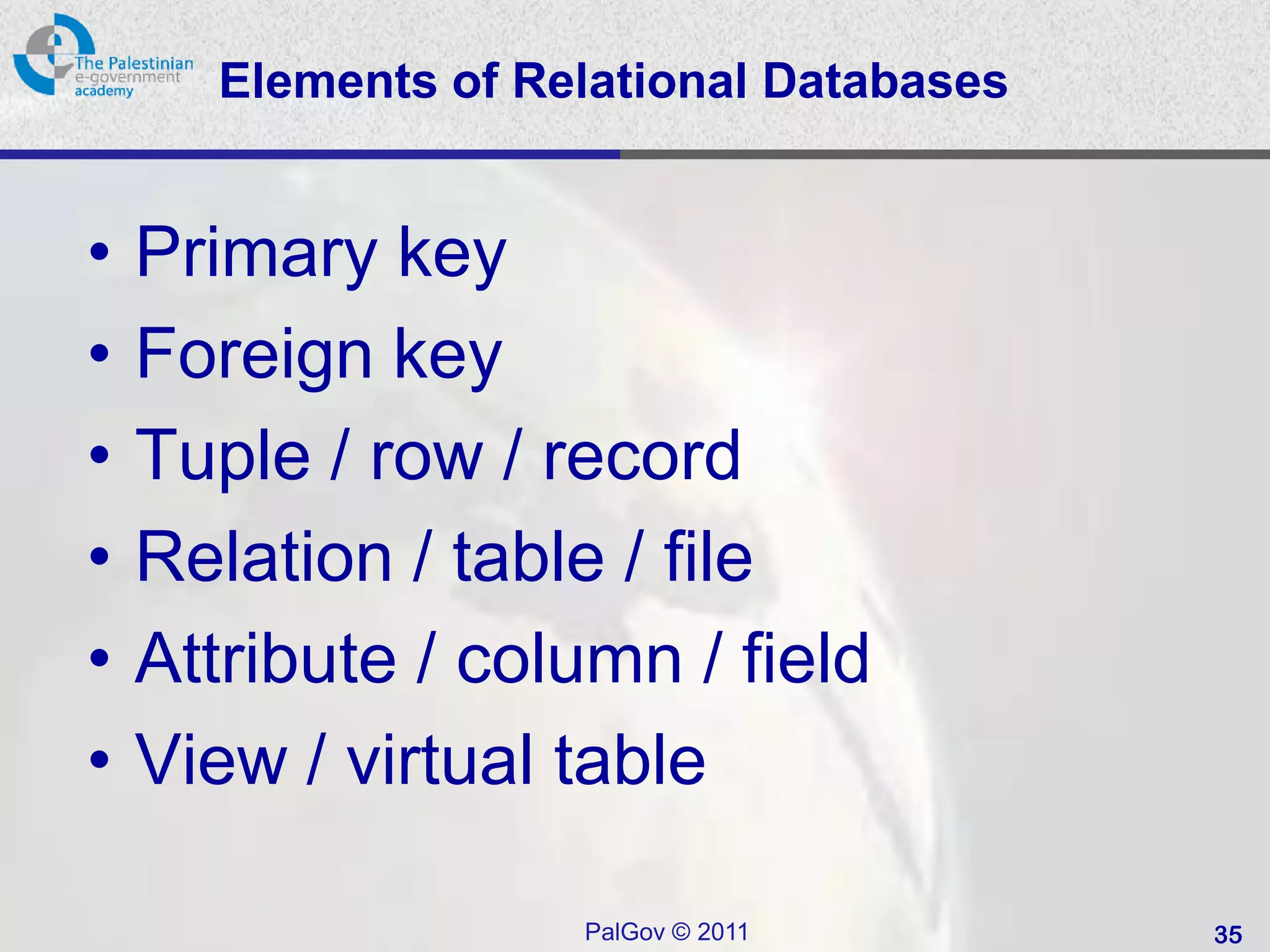
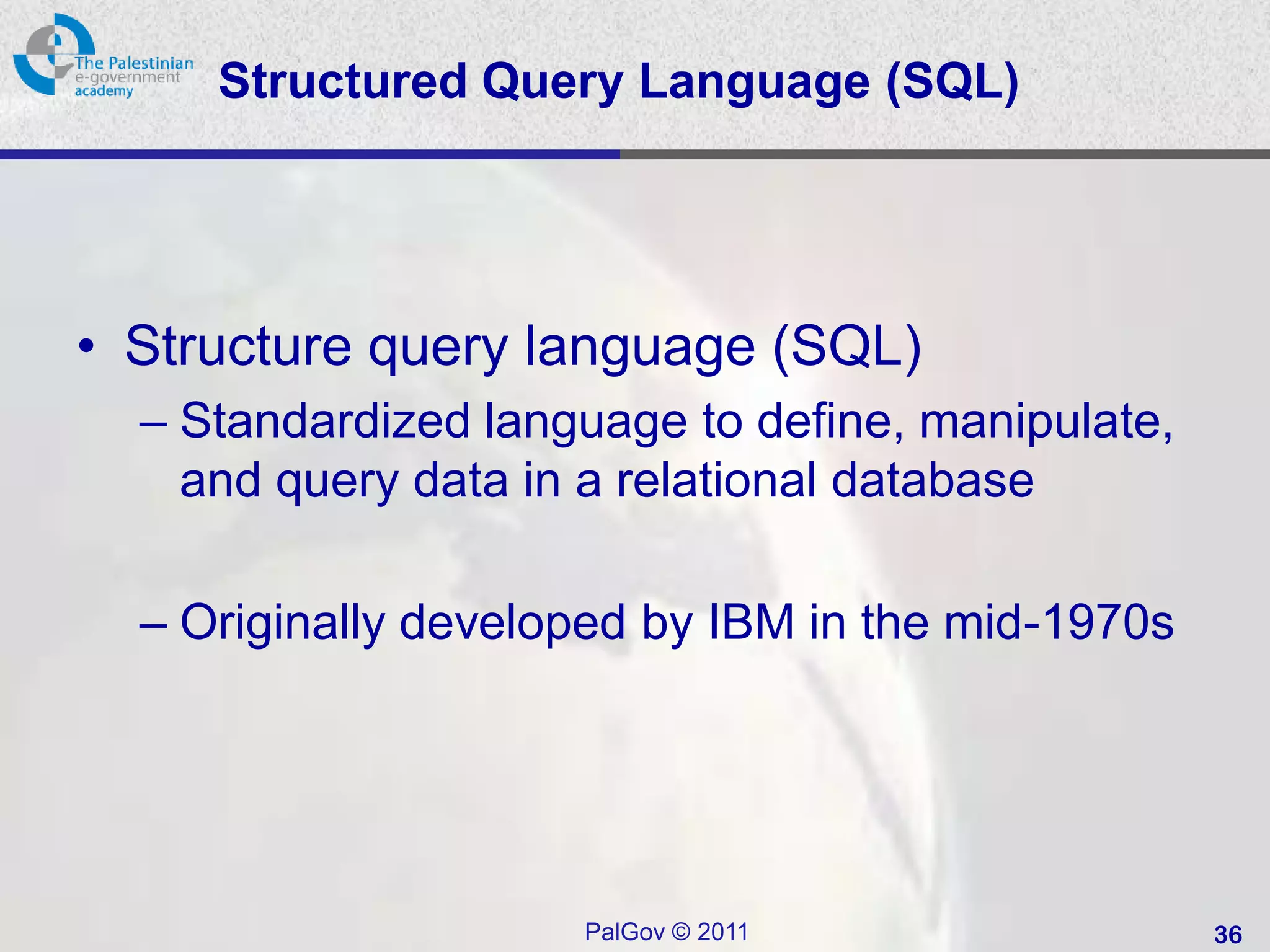

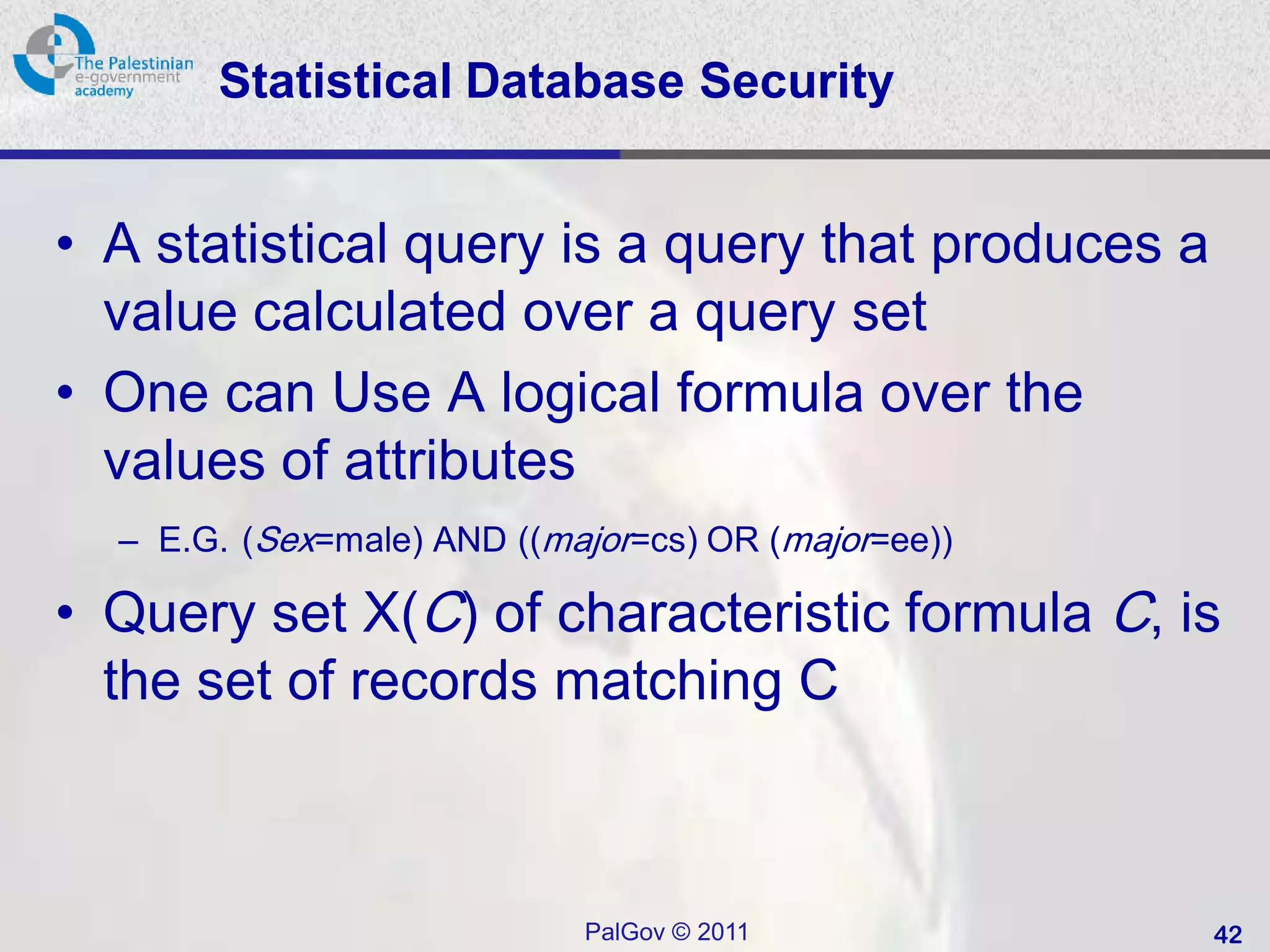
![SQL Access Controls
• Two commands:
– GRANT { privileges | role } [ON table] TO { user |
role | PUBLIC } [IDENTIFIED BY password]
[WITH GRANT OPTION]
• e.g. GRANT SELECT ON ANY TABLE TO ricflair
– REVOKE { privileges | role } [ON table] FROM {
user | role | PUBLIC }
• e.g. REVOKE SELECT ON ANY TABLE FROM ricflair
• Typical access rights are:
– SELECT, INSERT, UPDATE, DELETE,
REFERENCES
PalGov © 2011 38](https://image.slidesharecdn.com/egovsecuritytutsession11-120312052600-phpapp02/75/E-gov-security_tut_session_11-38-2048.jpg)

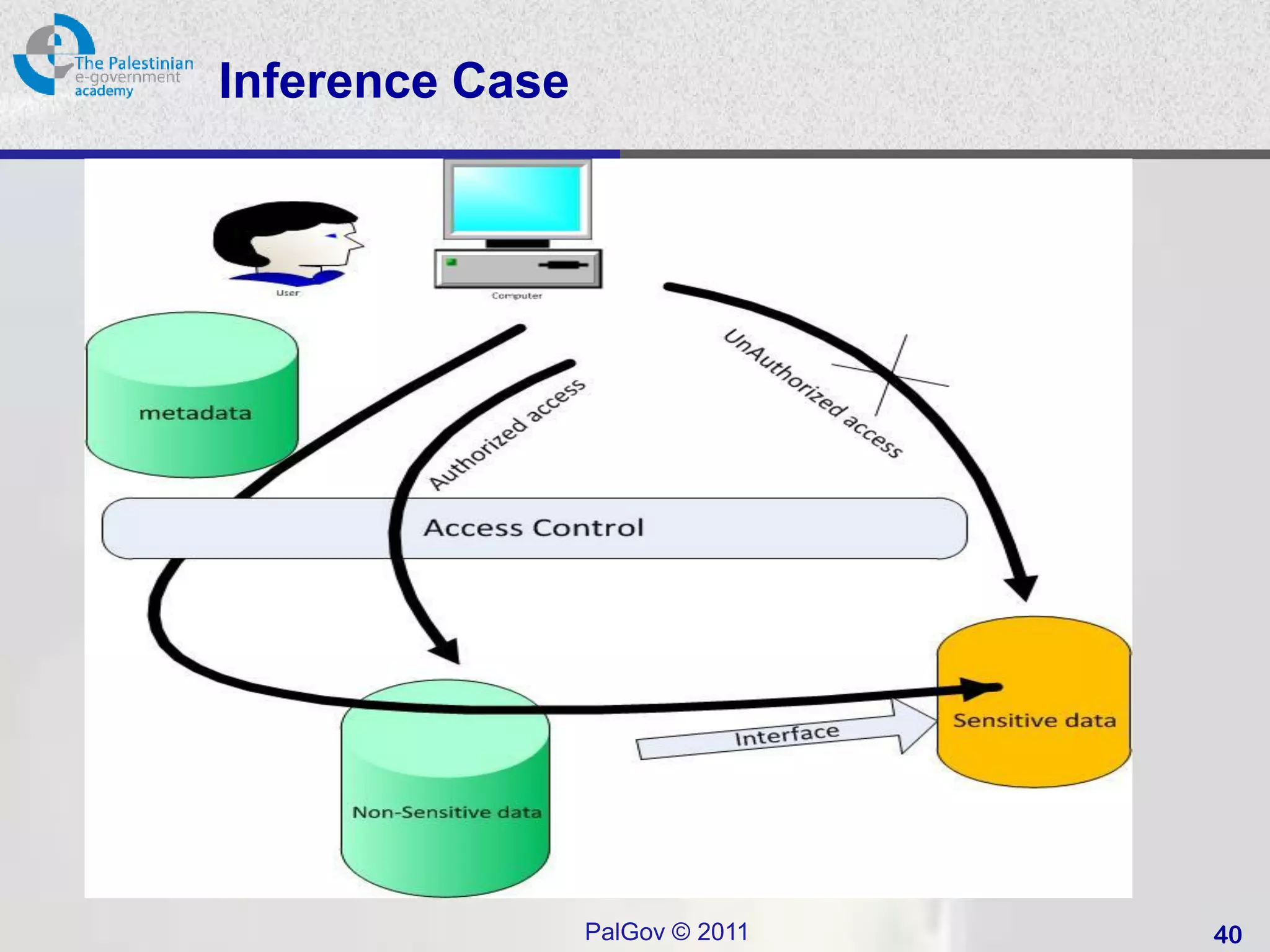
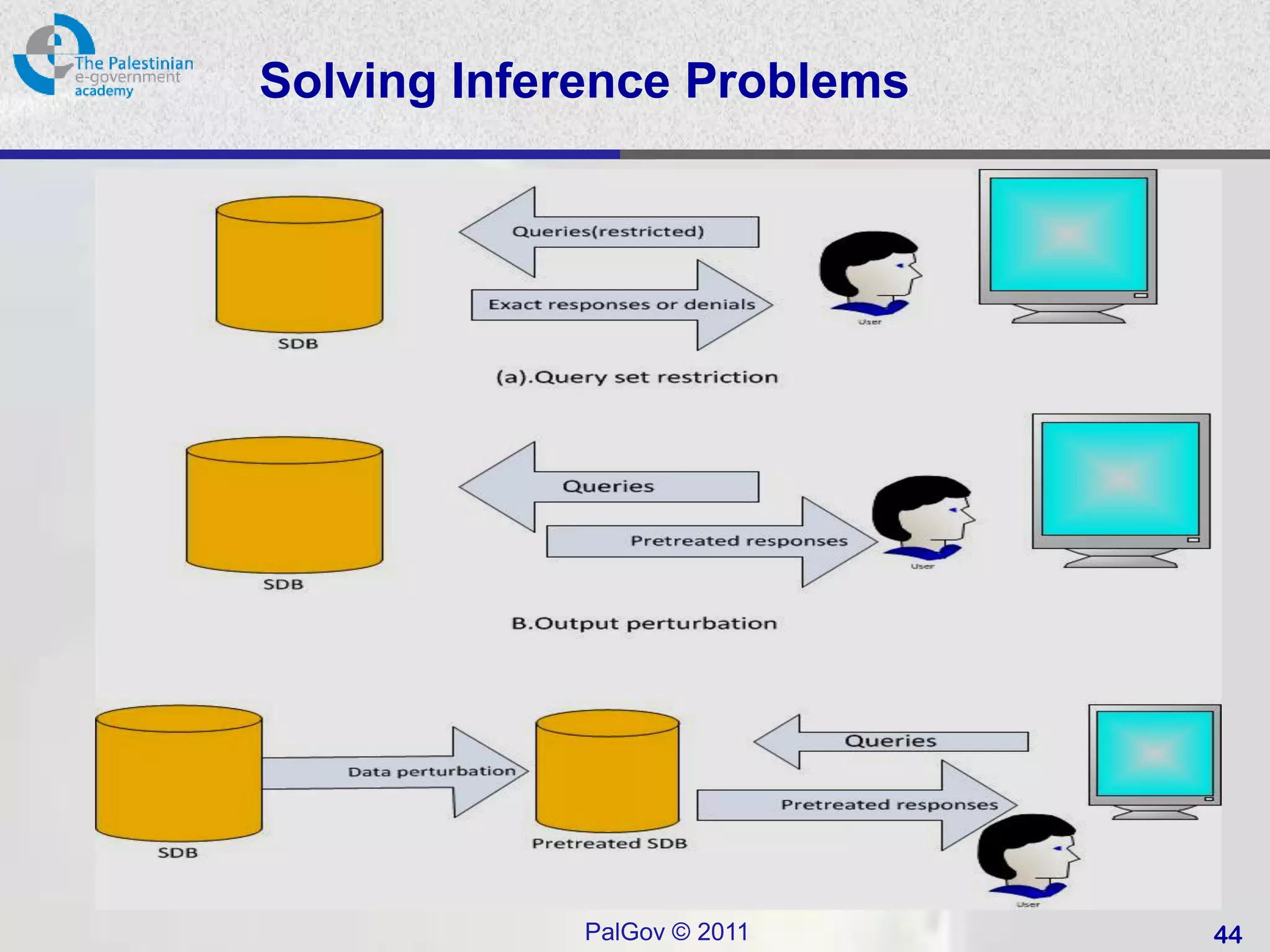
![Statistical Database Example [1]
1. Computer Security: Principles and Practice, by William Stallings and Lawrie Brown. Published by Pearson/Prentice Hall, © 2008.
ISBN: 0-13-600424-5.
PalGov © 2011 43](https://image.slidesharecdn.com/egovsecuritytutsession11-120312052600-phpapp02/75/E-gov-security_tut_session_11-43-2048.jpg)

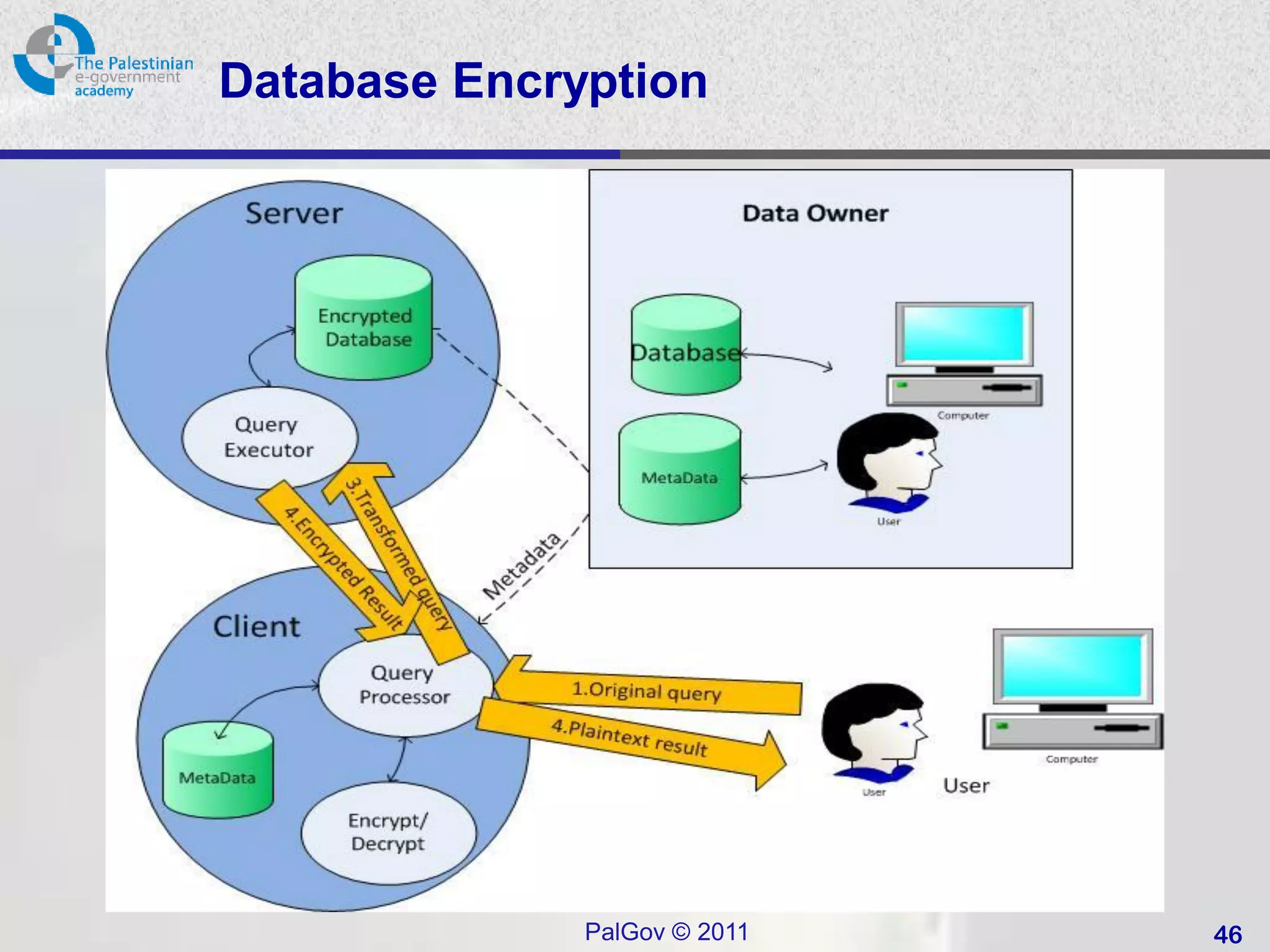
![Homomorphic Encryption (2)
• The correspondence between the
operations on unencrypted data and the
operations to be performed on encrypted
data is known as a homomorphism.
– "In principle," says Gentry, an IBM researcher,
"something like this could be used to secure
operations over the Internet.“ [2]
[2] (http://www.technologyreview.com/computing/37197/)
PalGov © 2011 48](https://image.slidesharecdn.com/egovsecuritytutsession11-120312052600-phpapp02/75/E-gov-security_tut_session_11-48-2048.jpg)