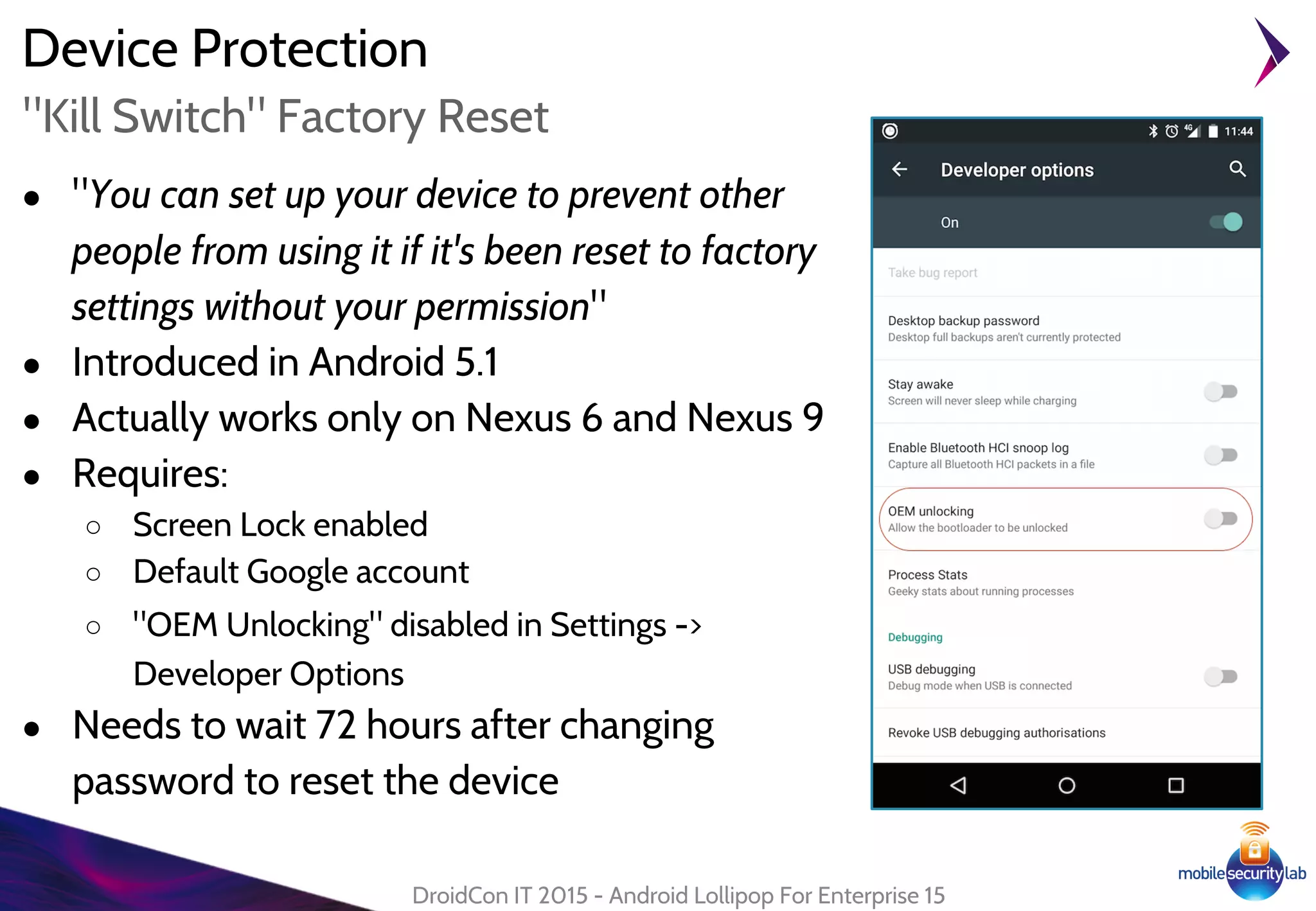
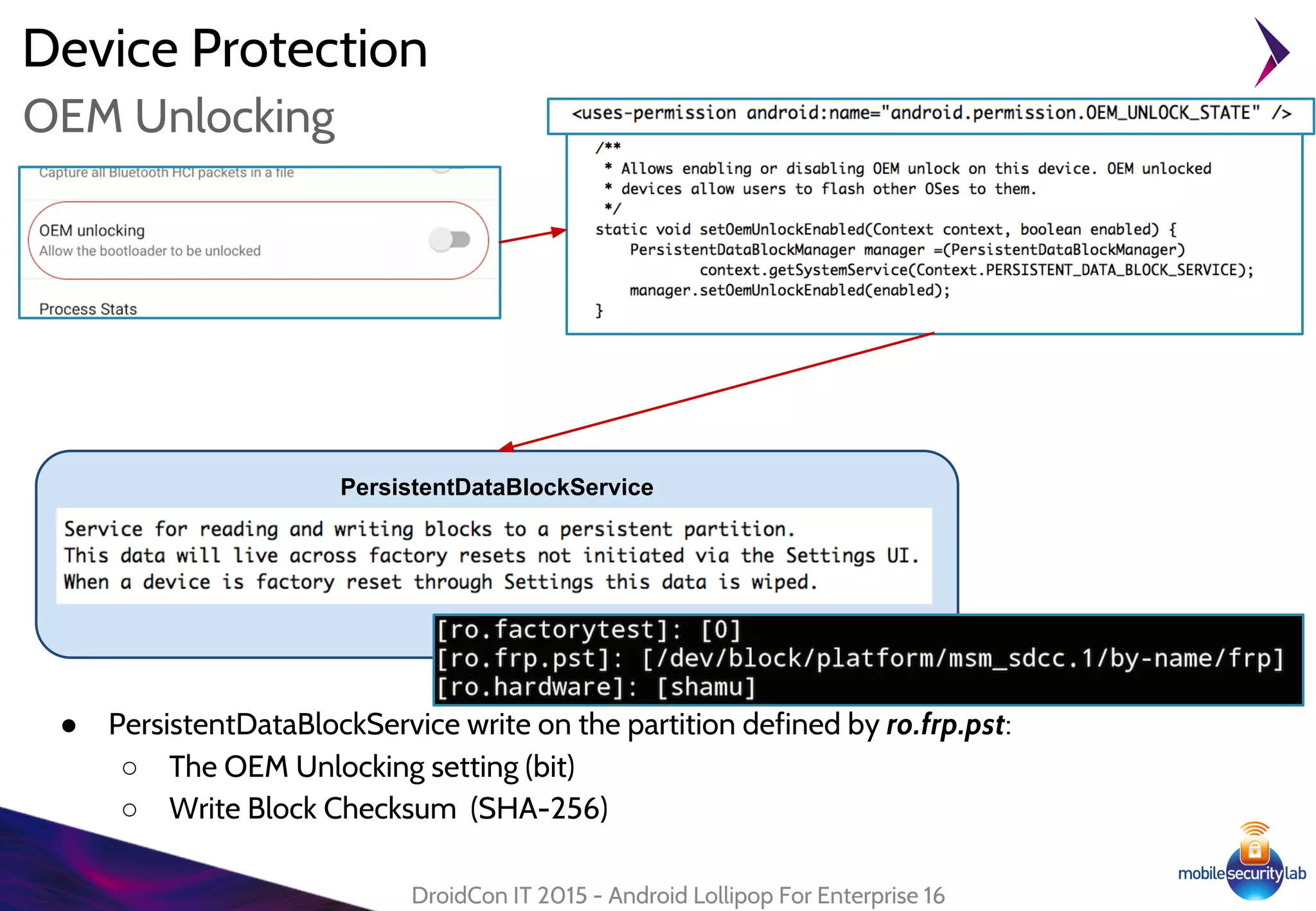
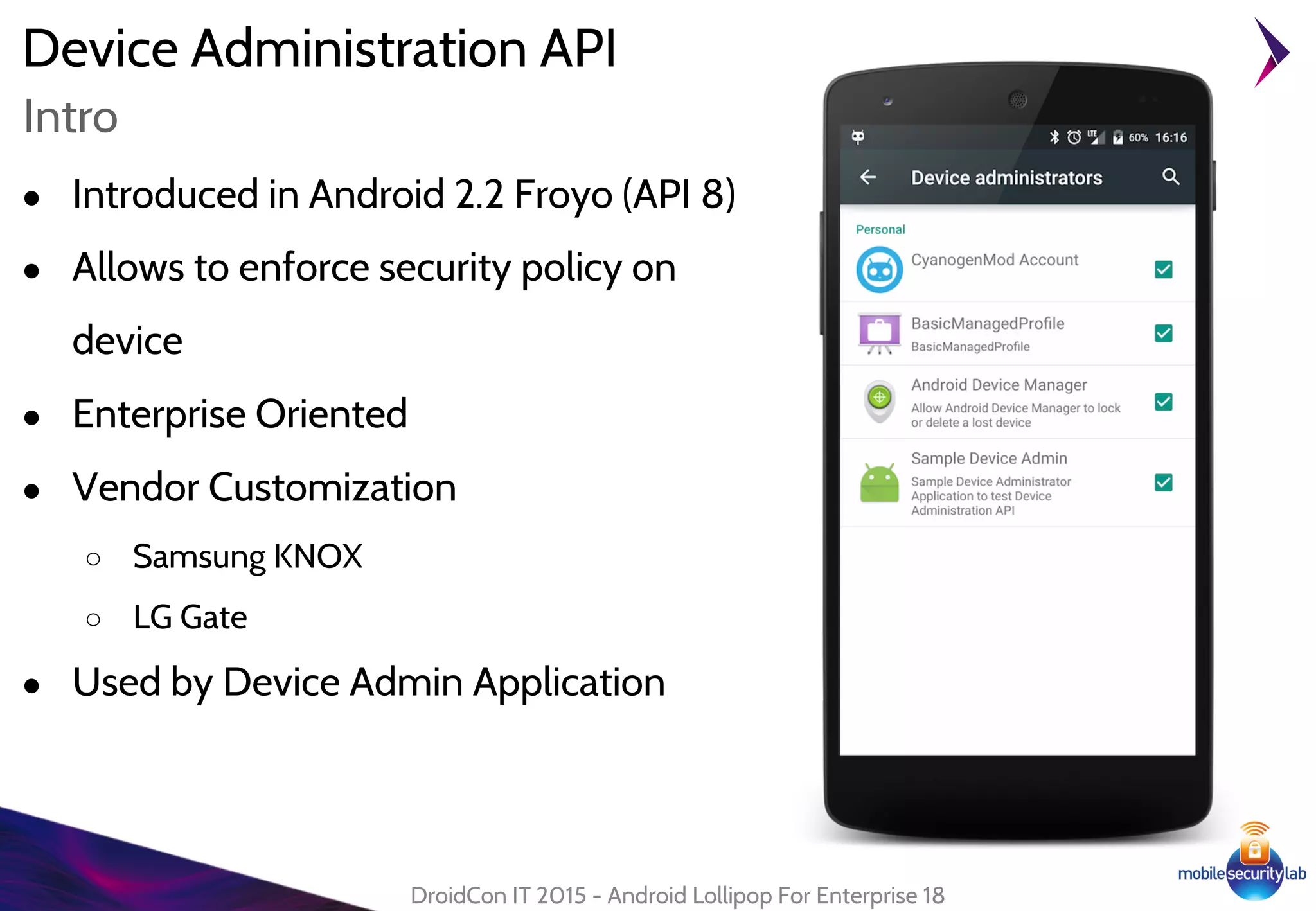
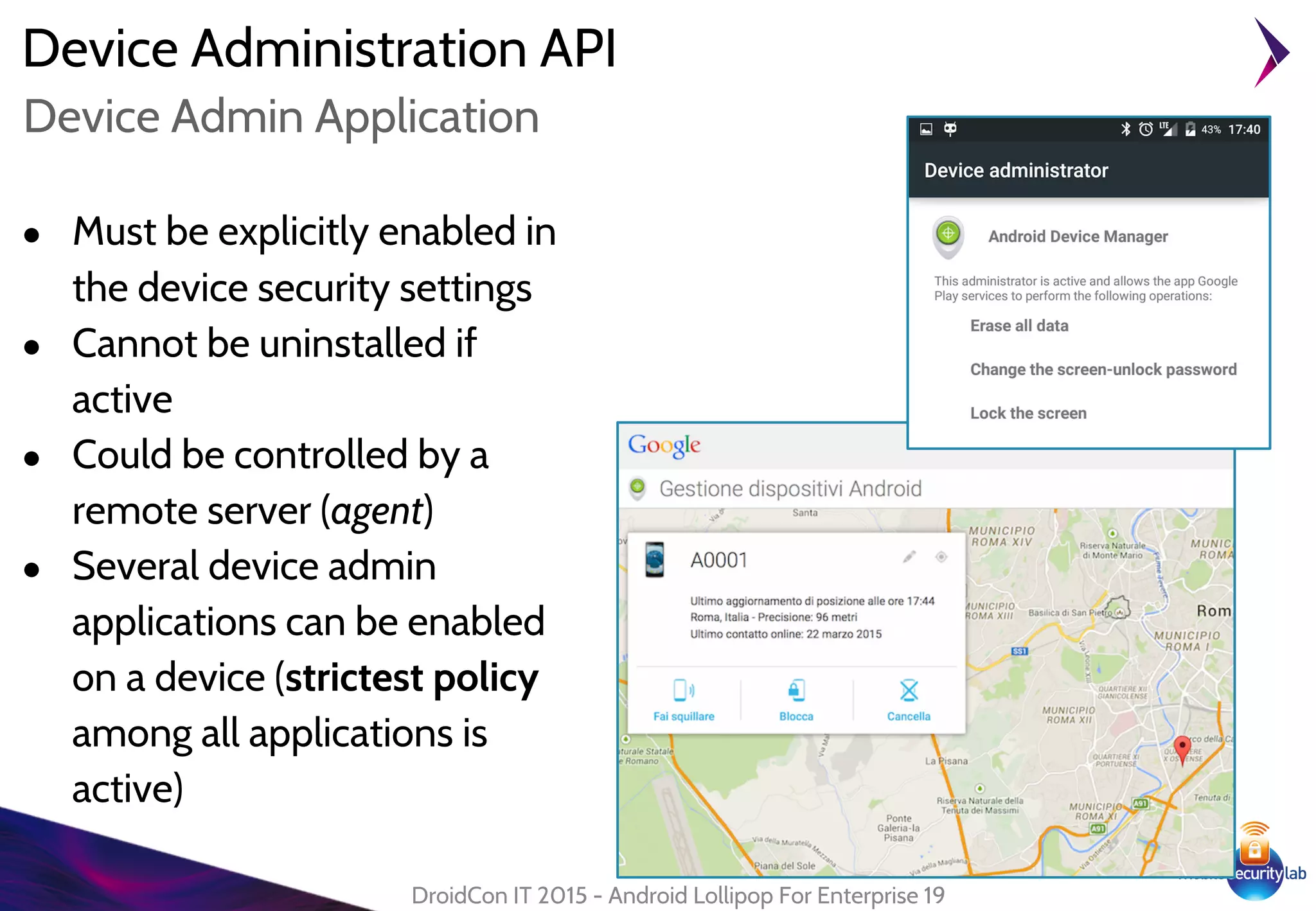
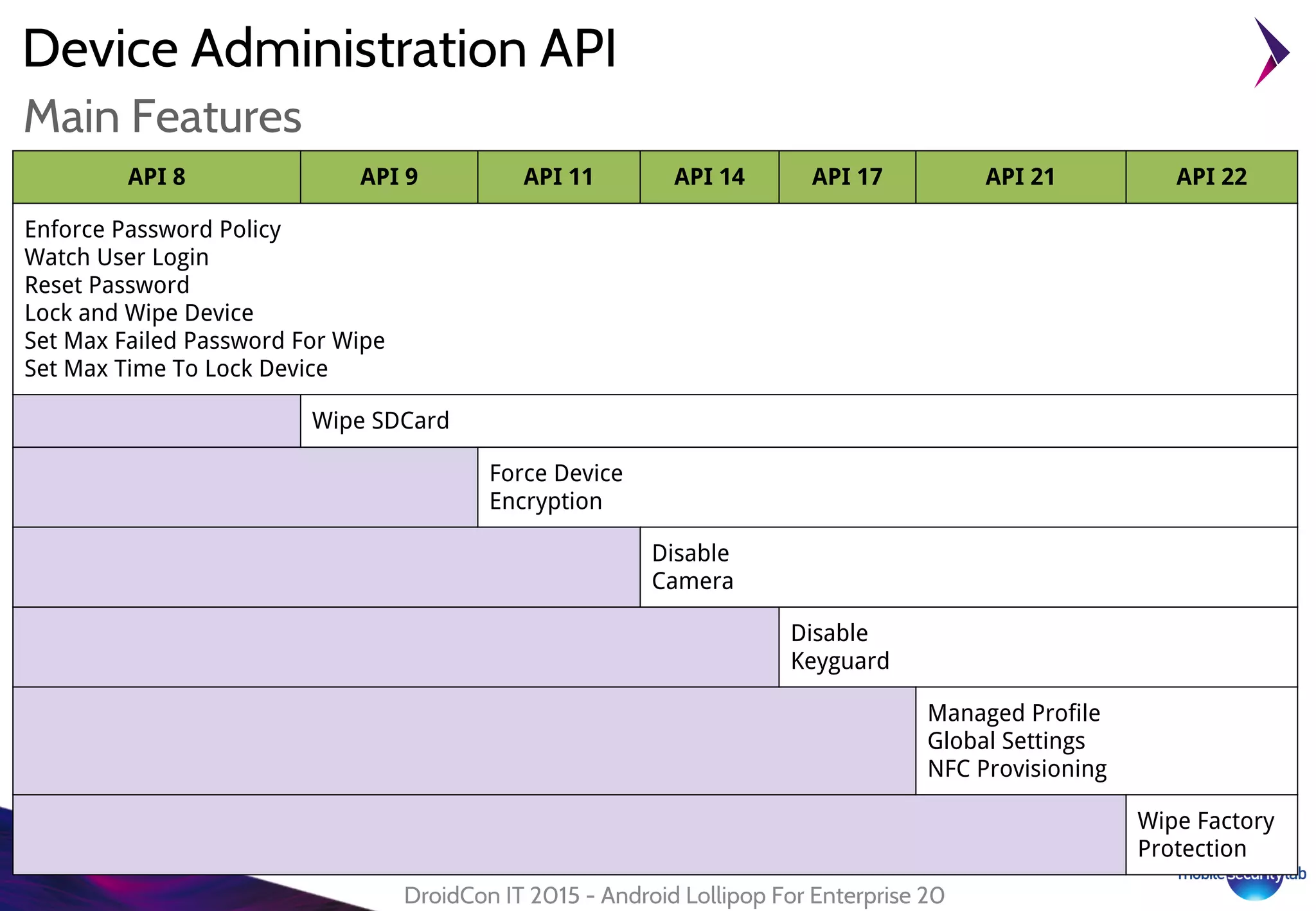
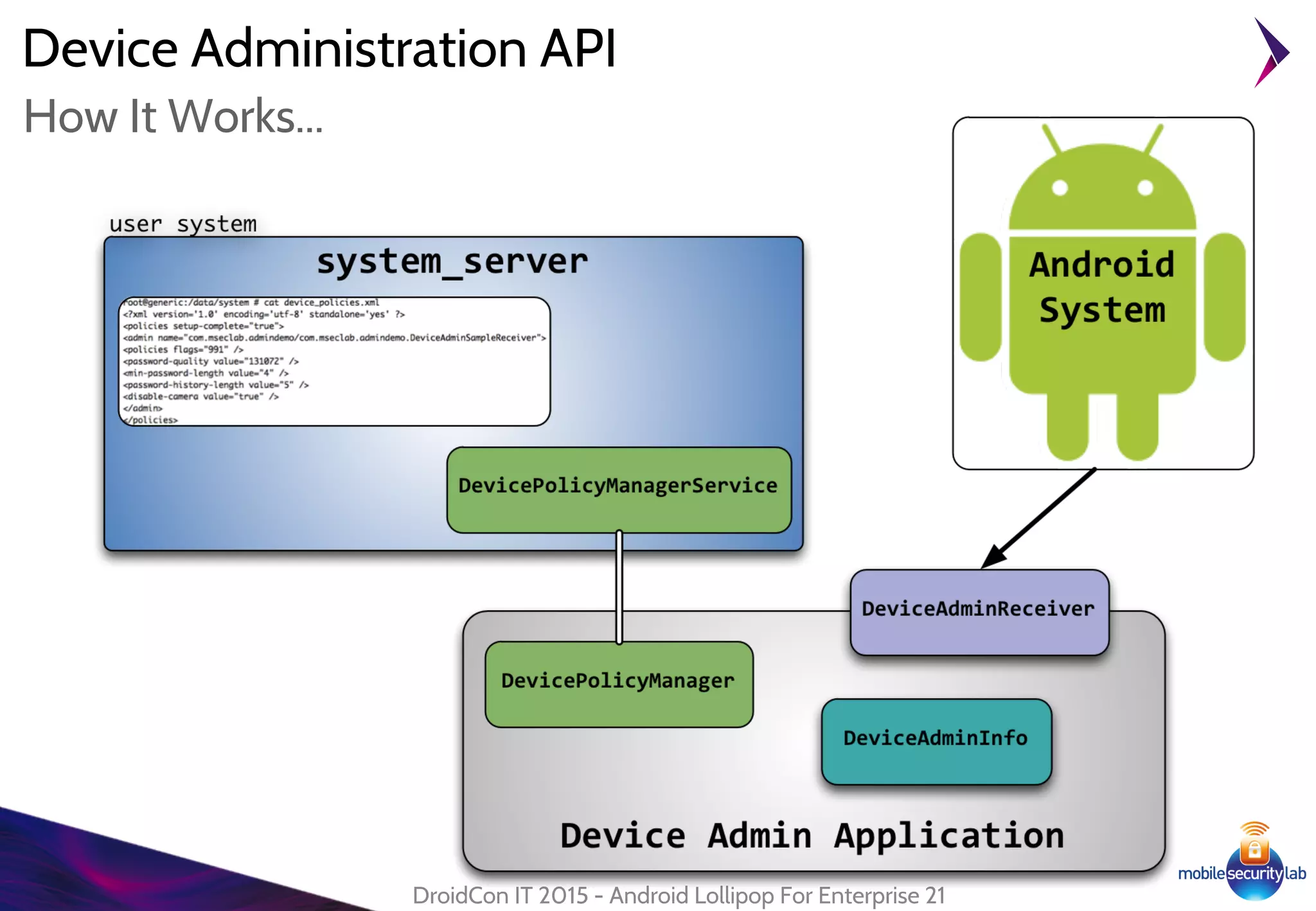
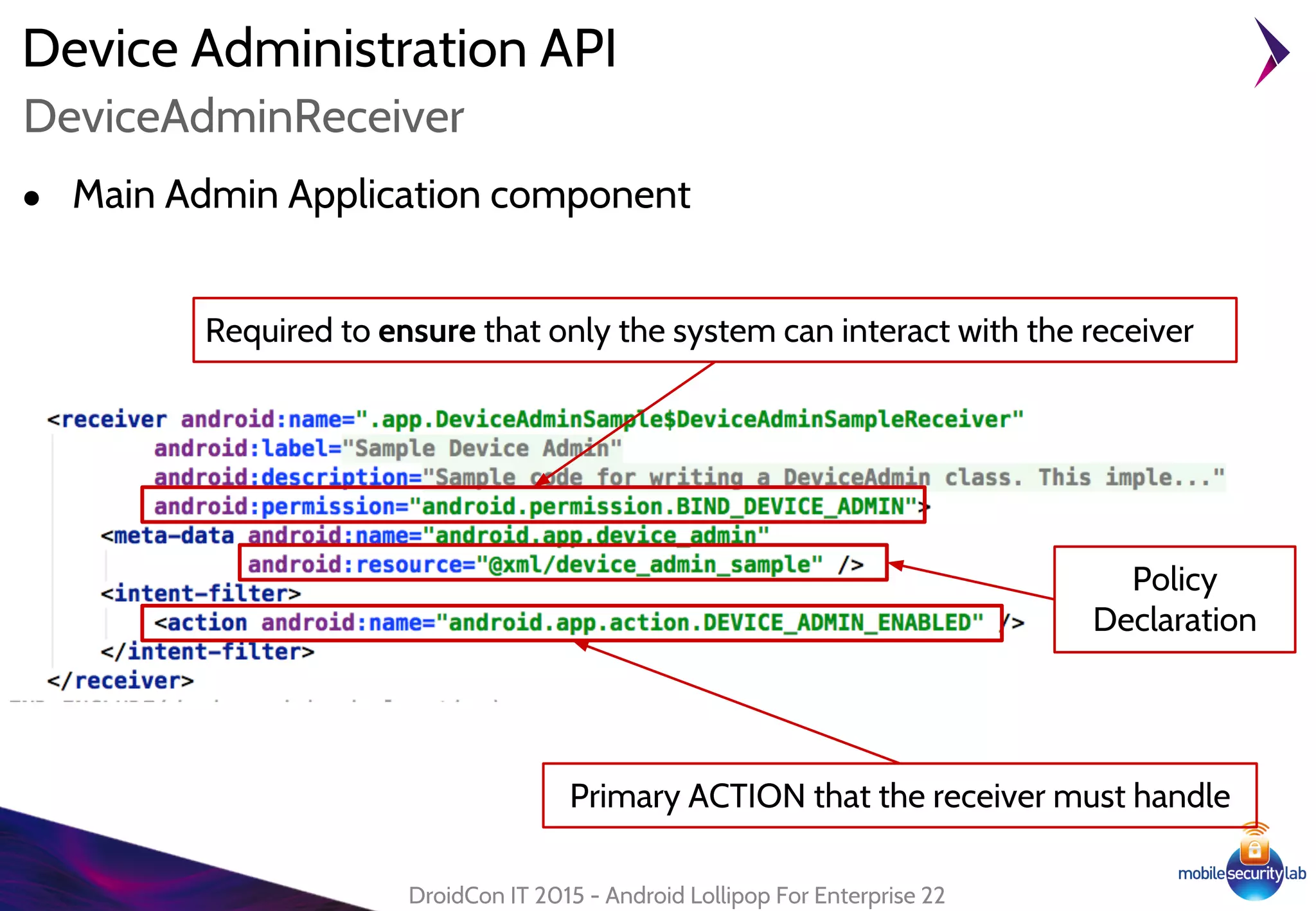
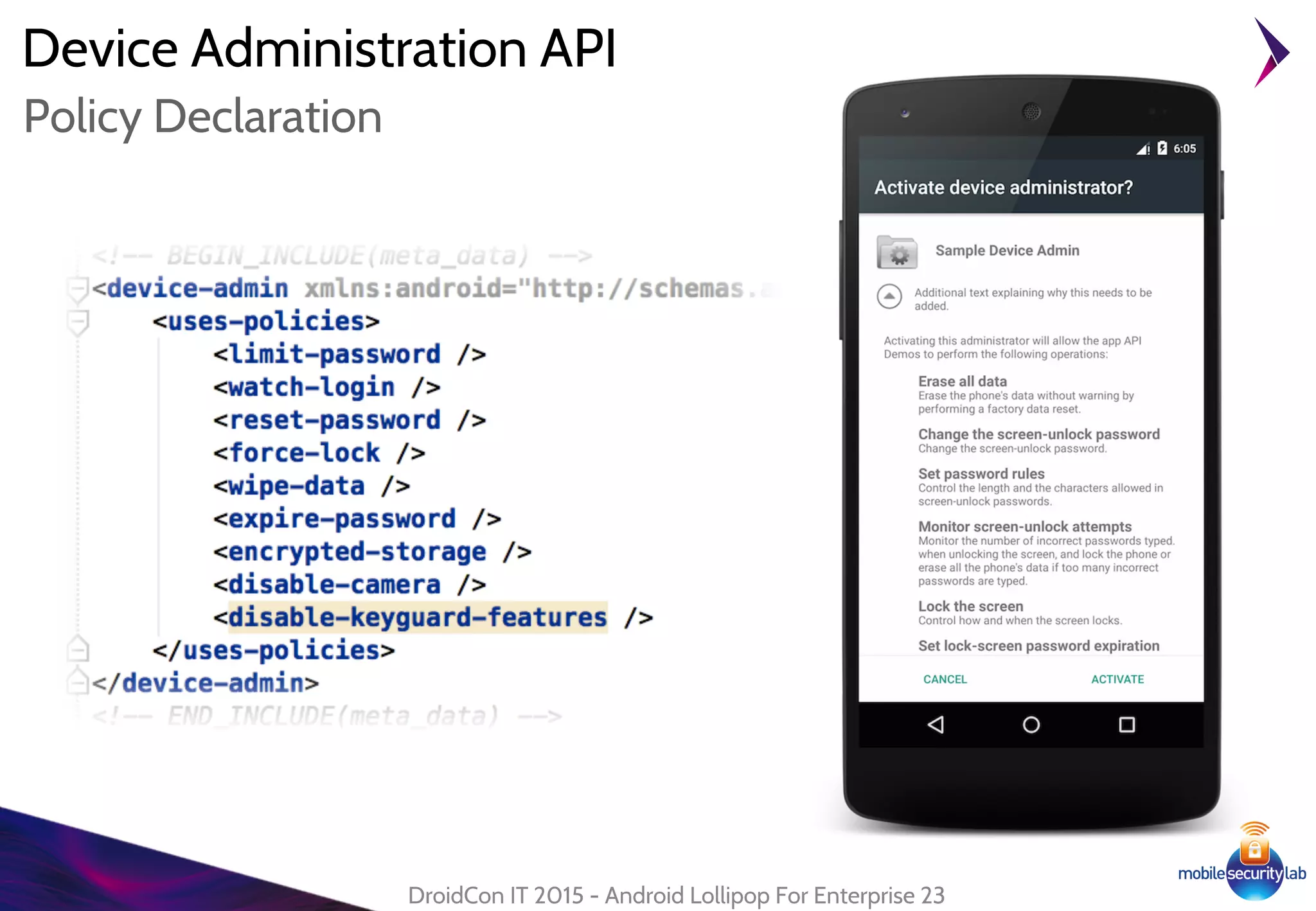
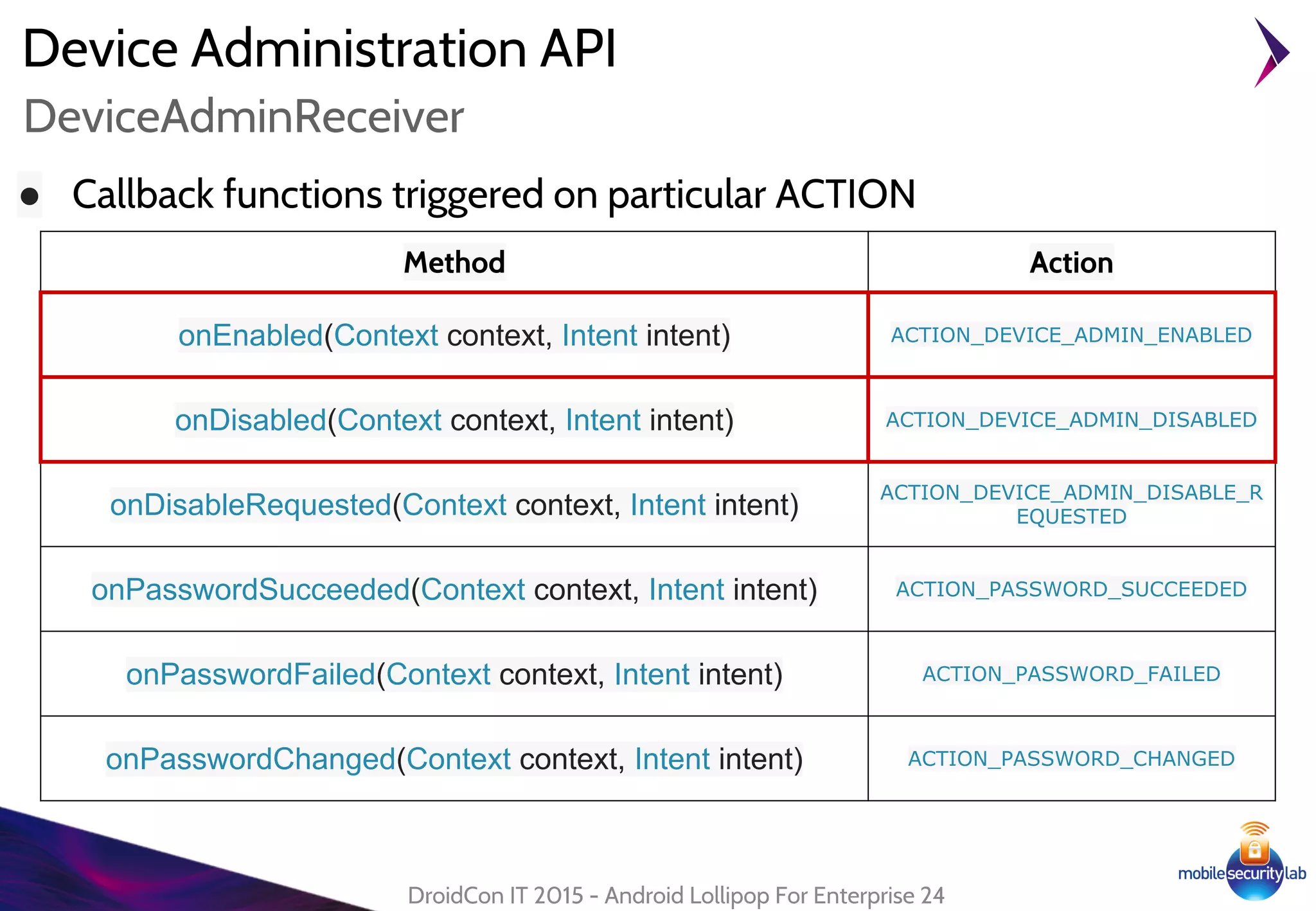
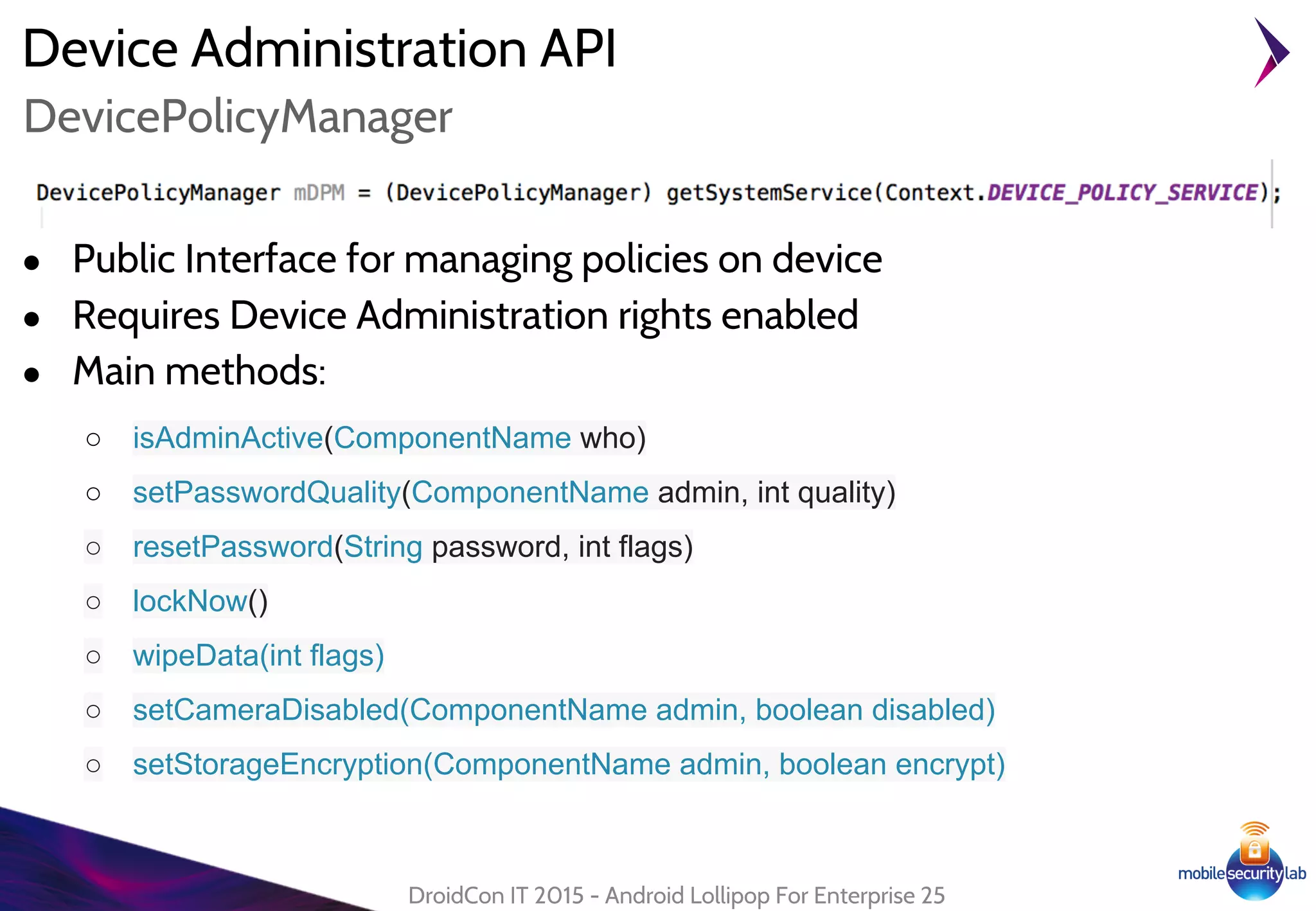
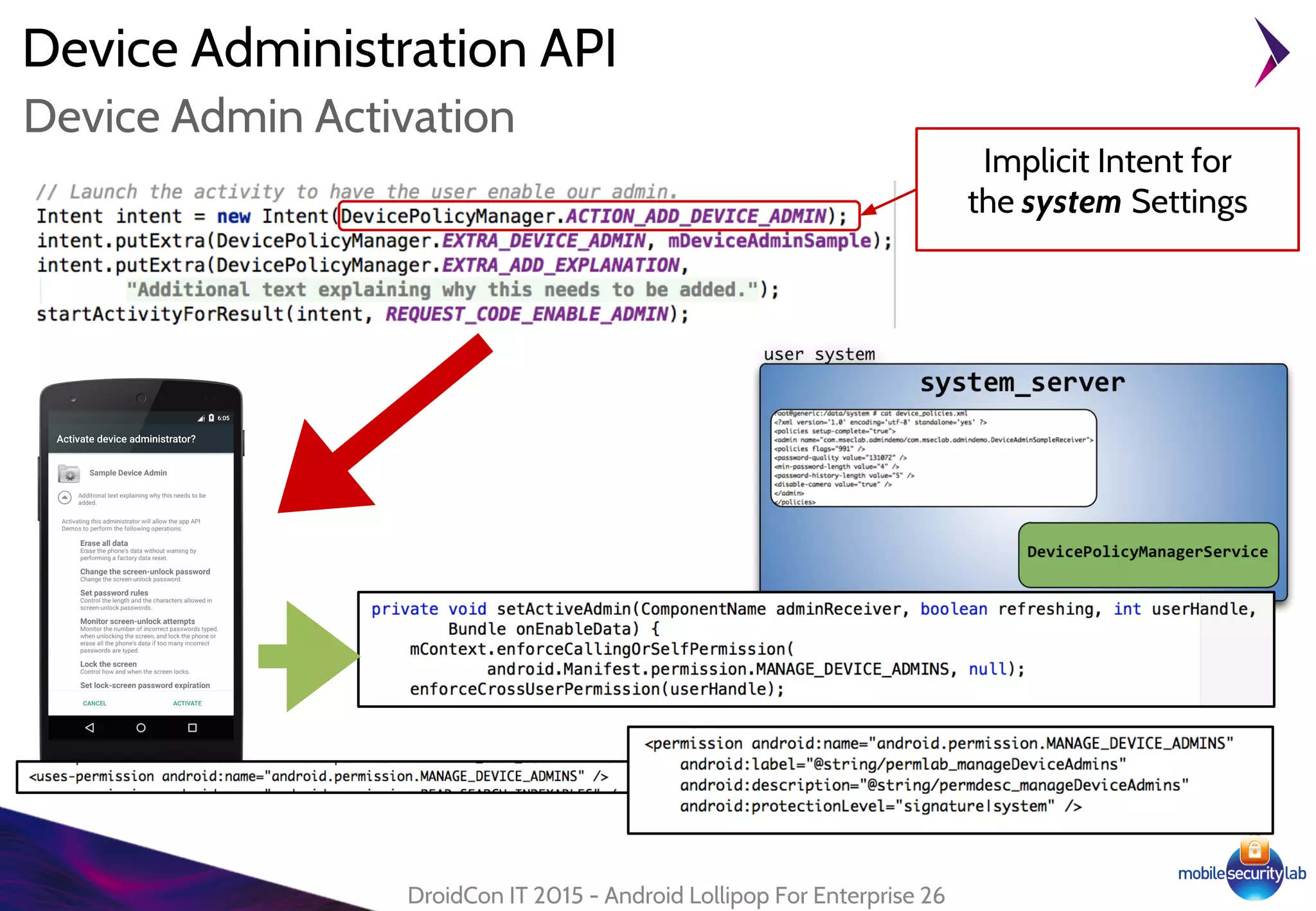
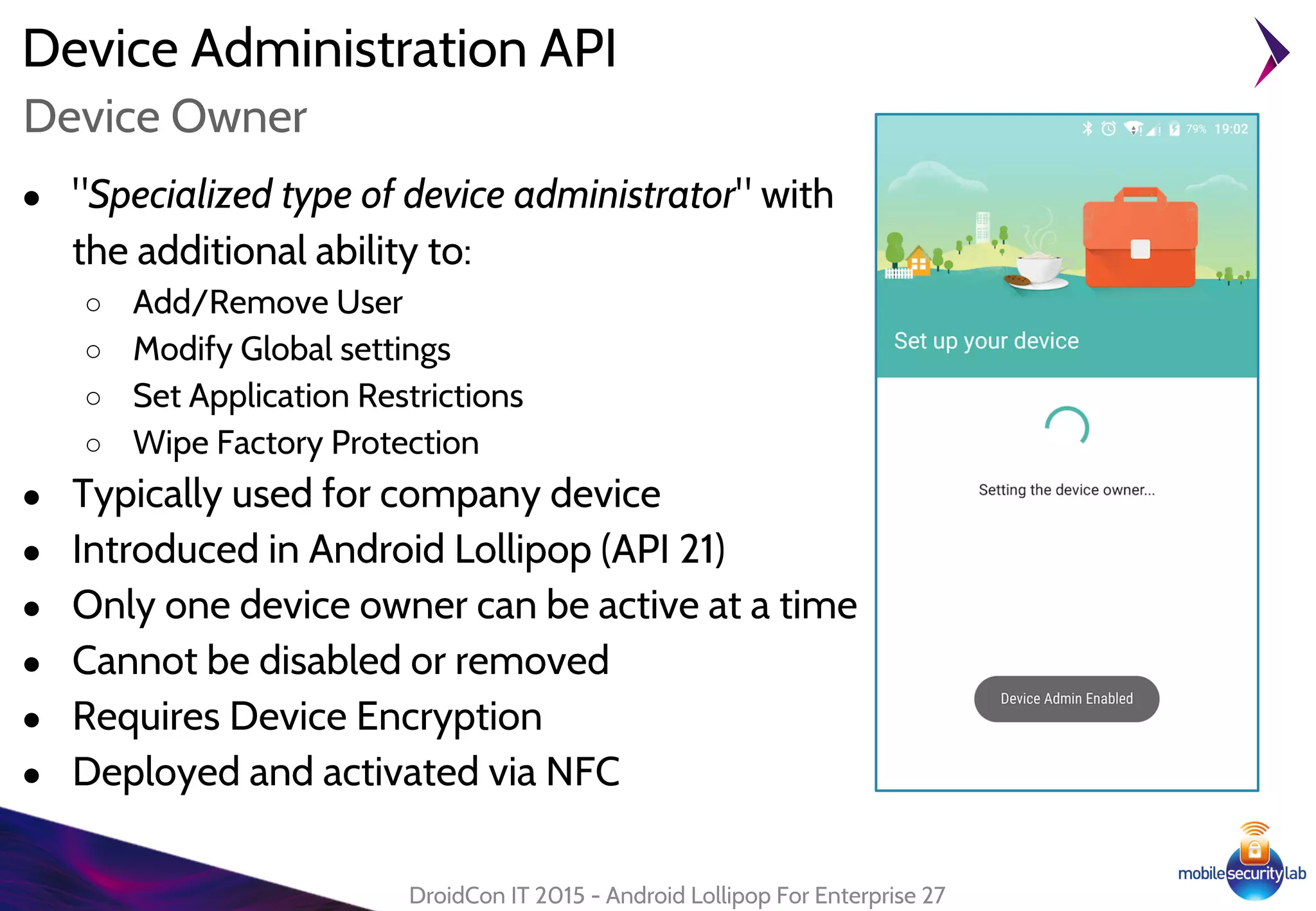
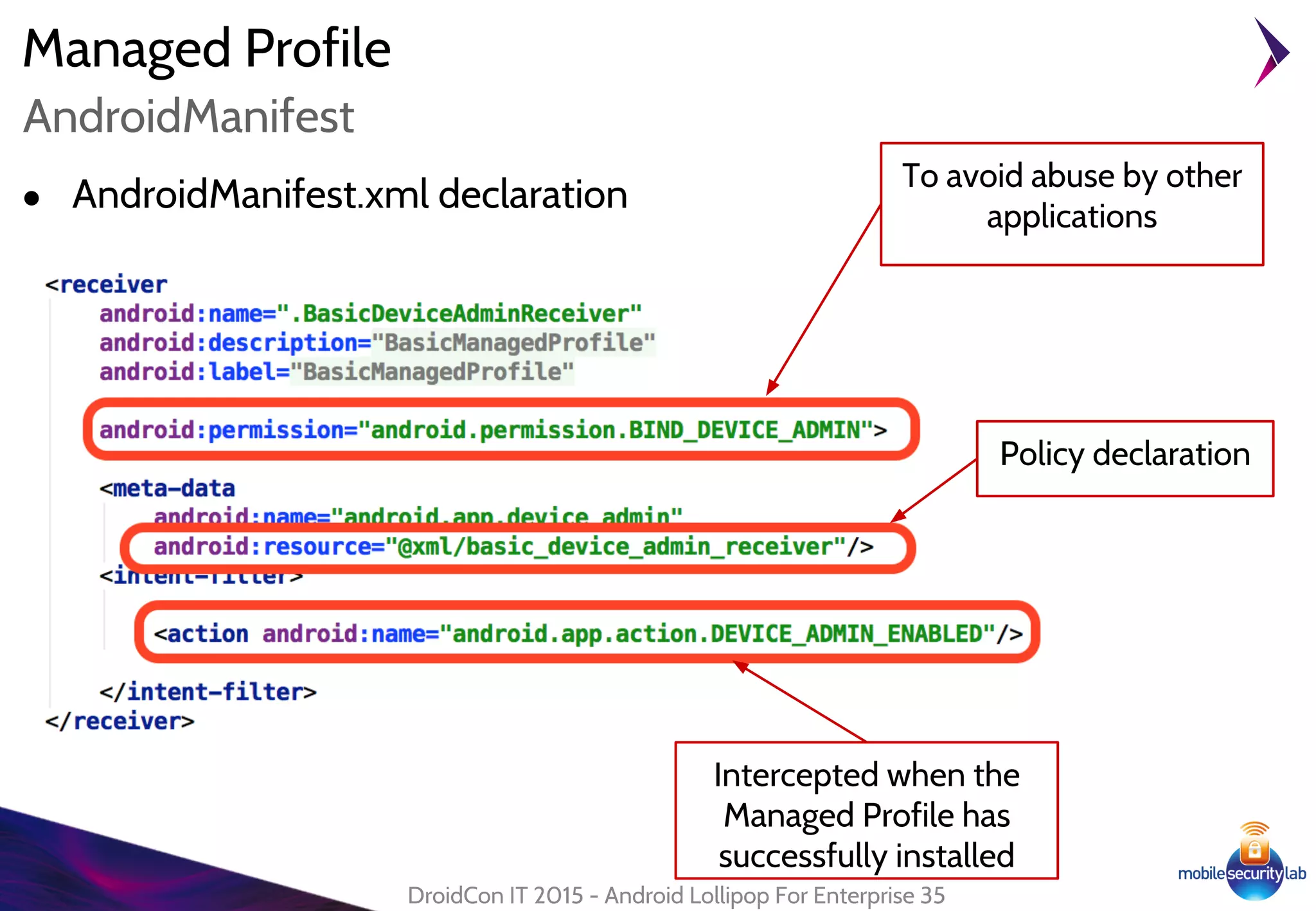
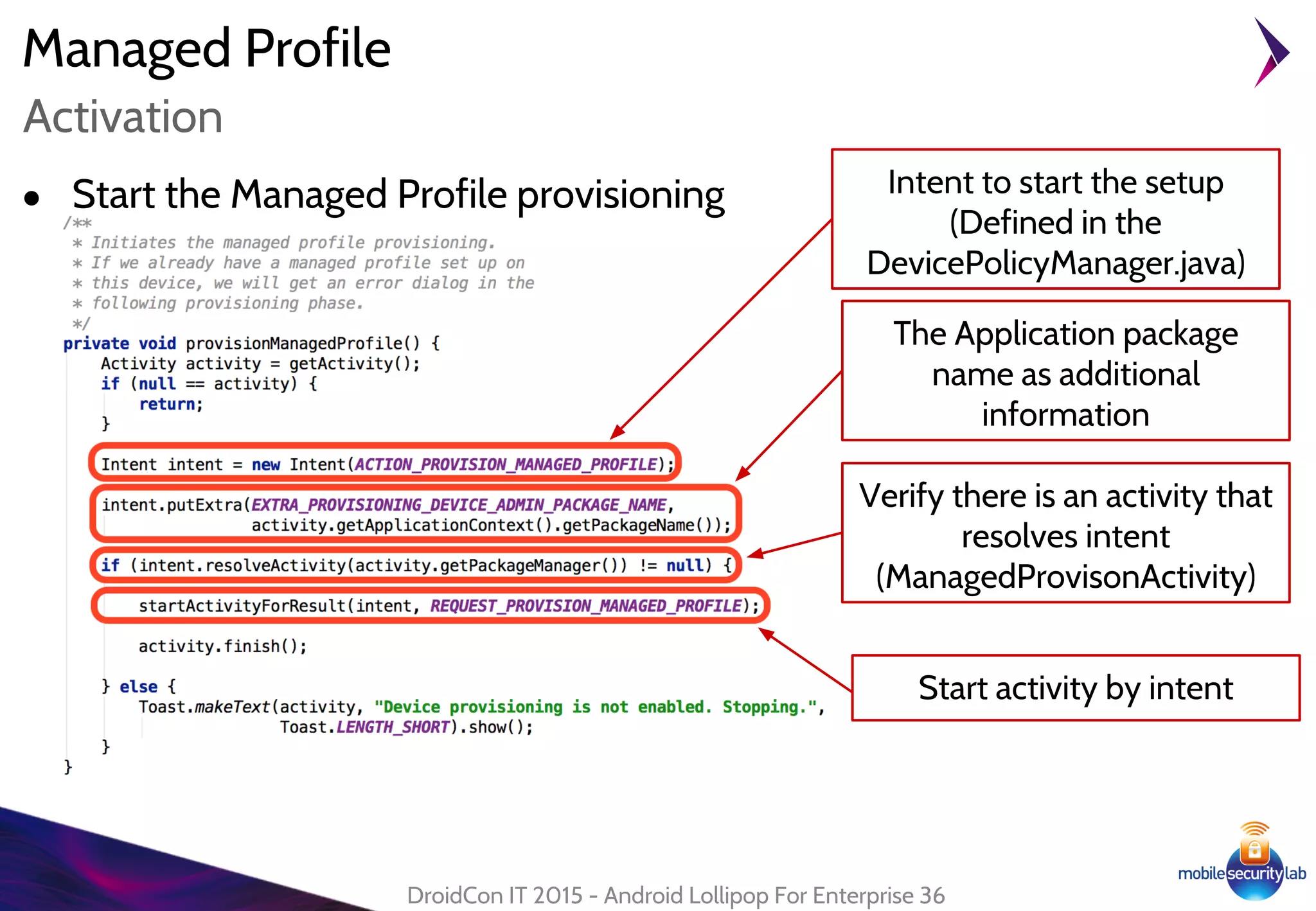
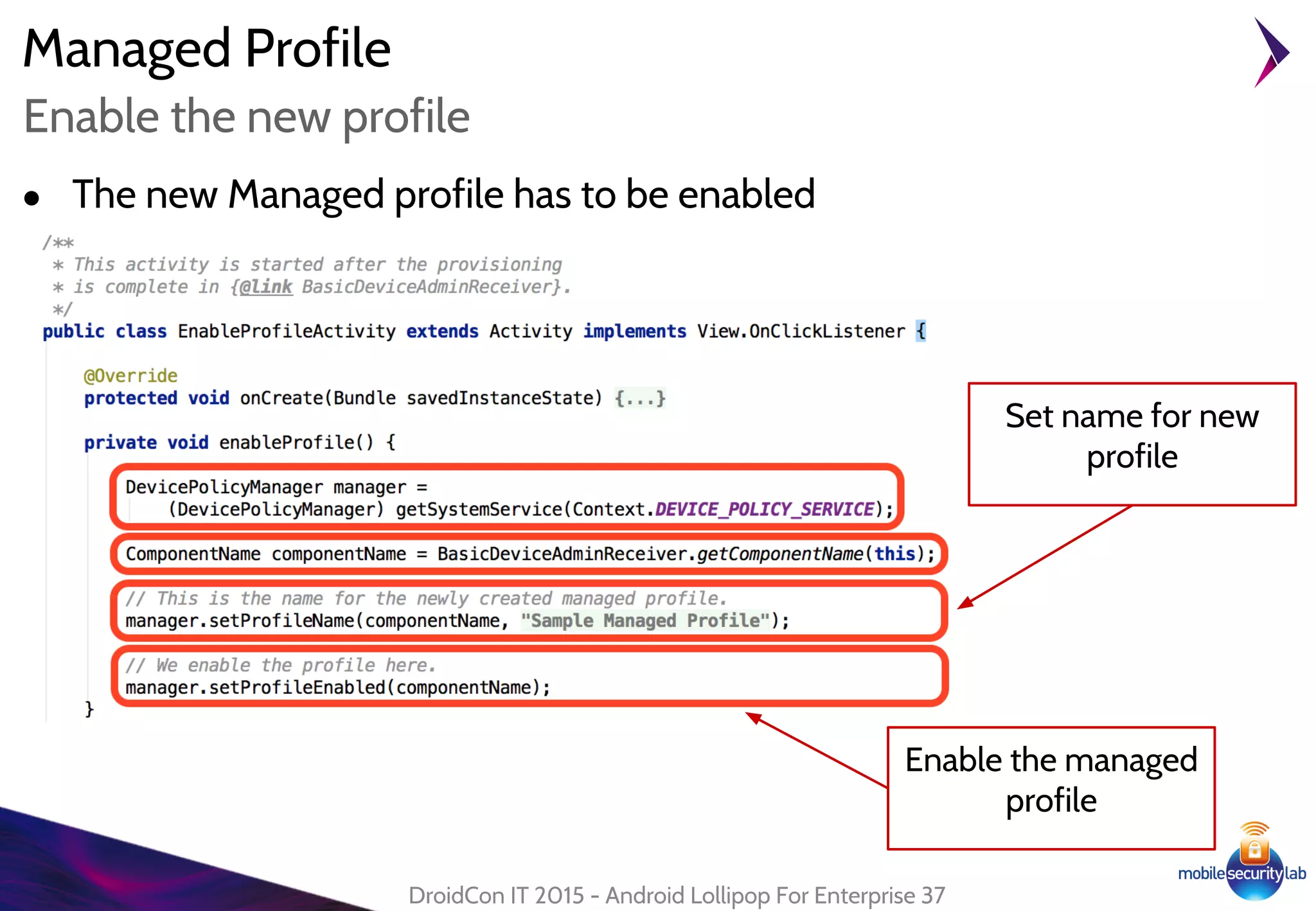
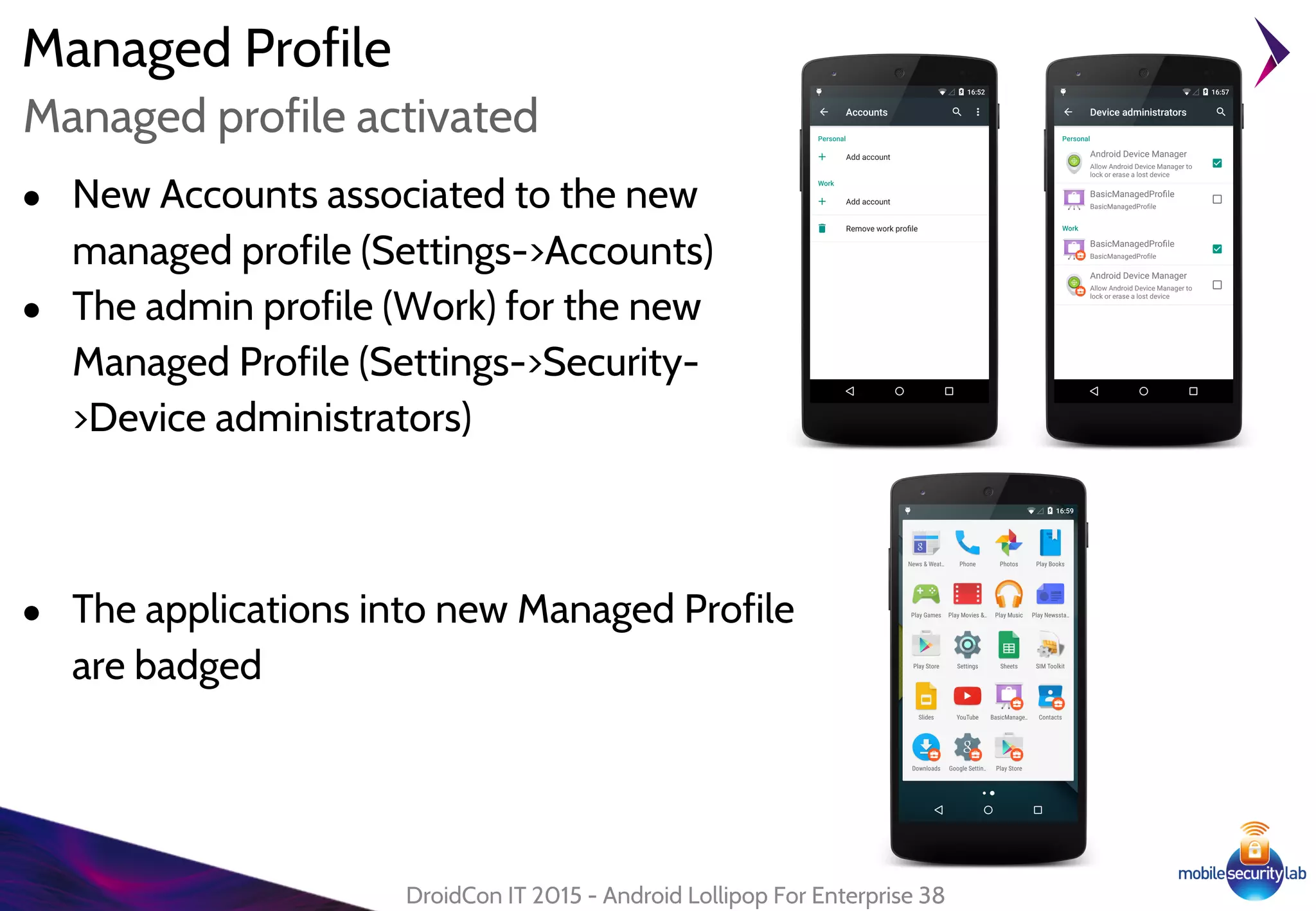
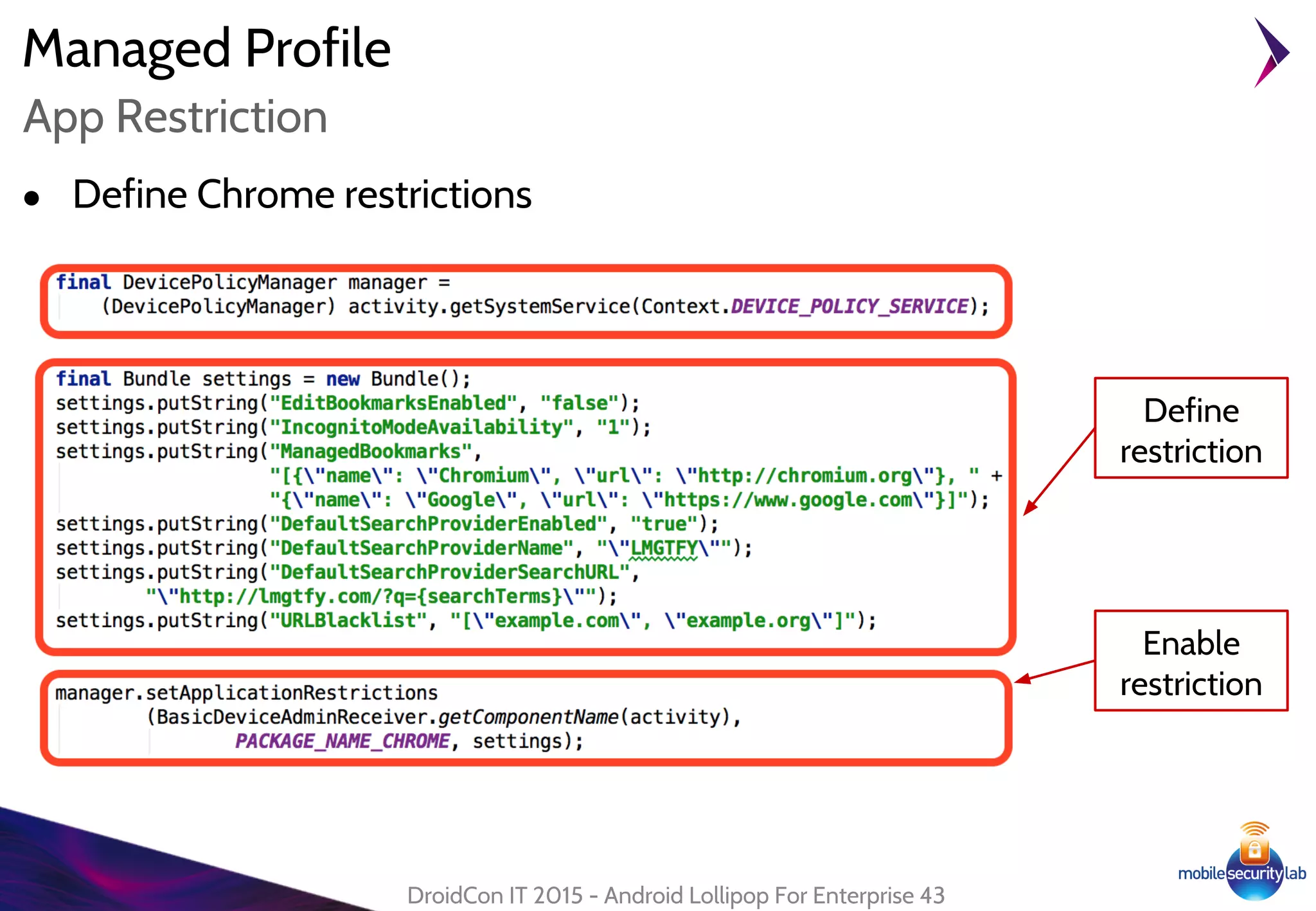
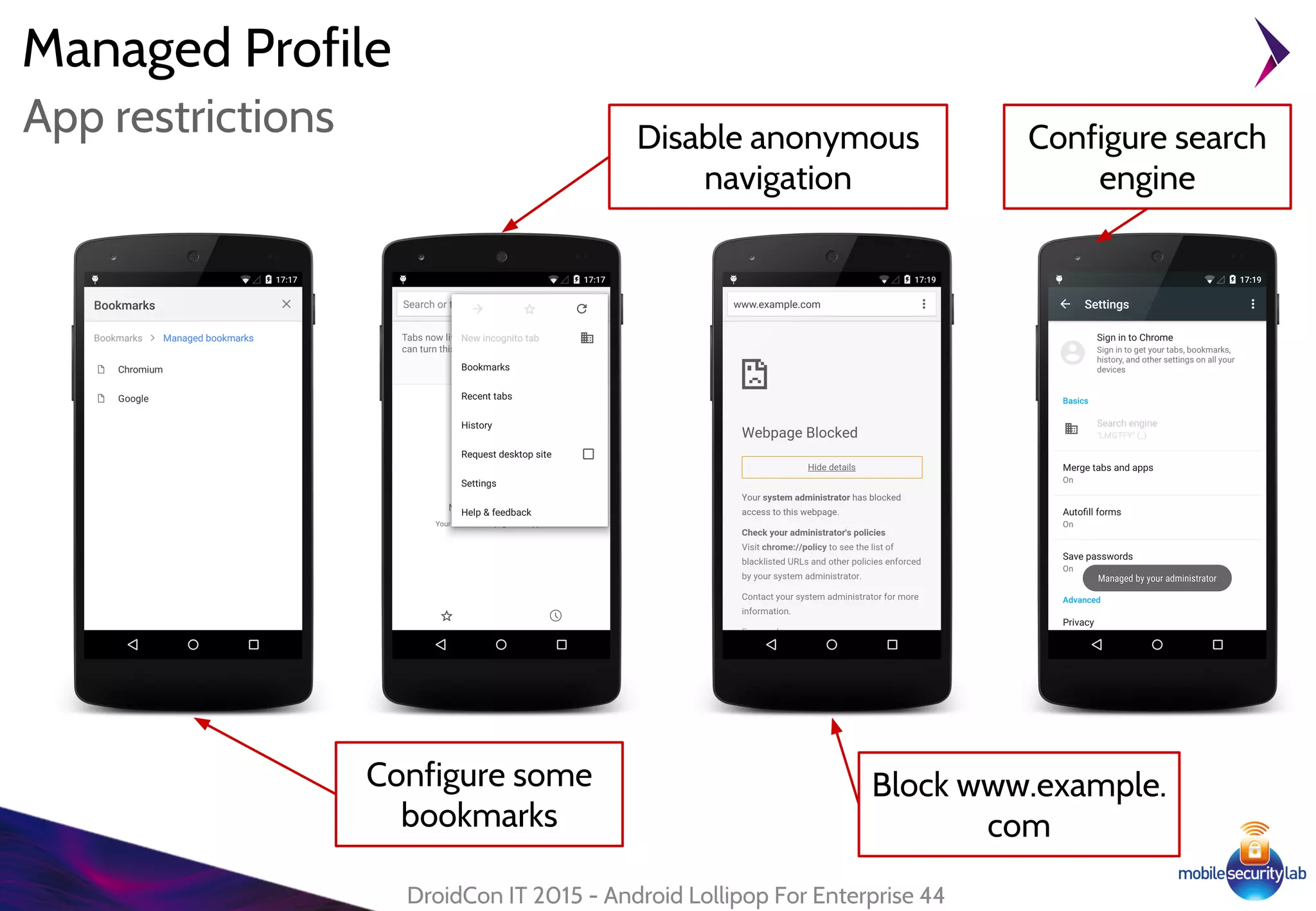
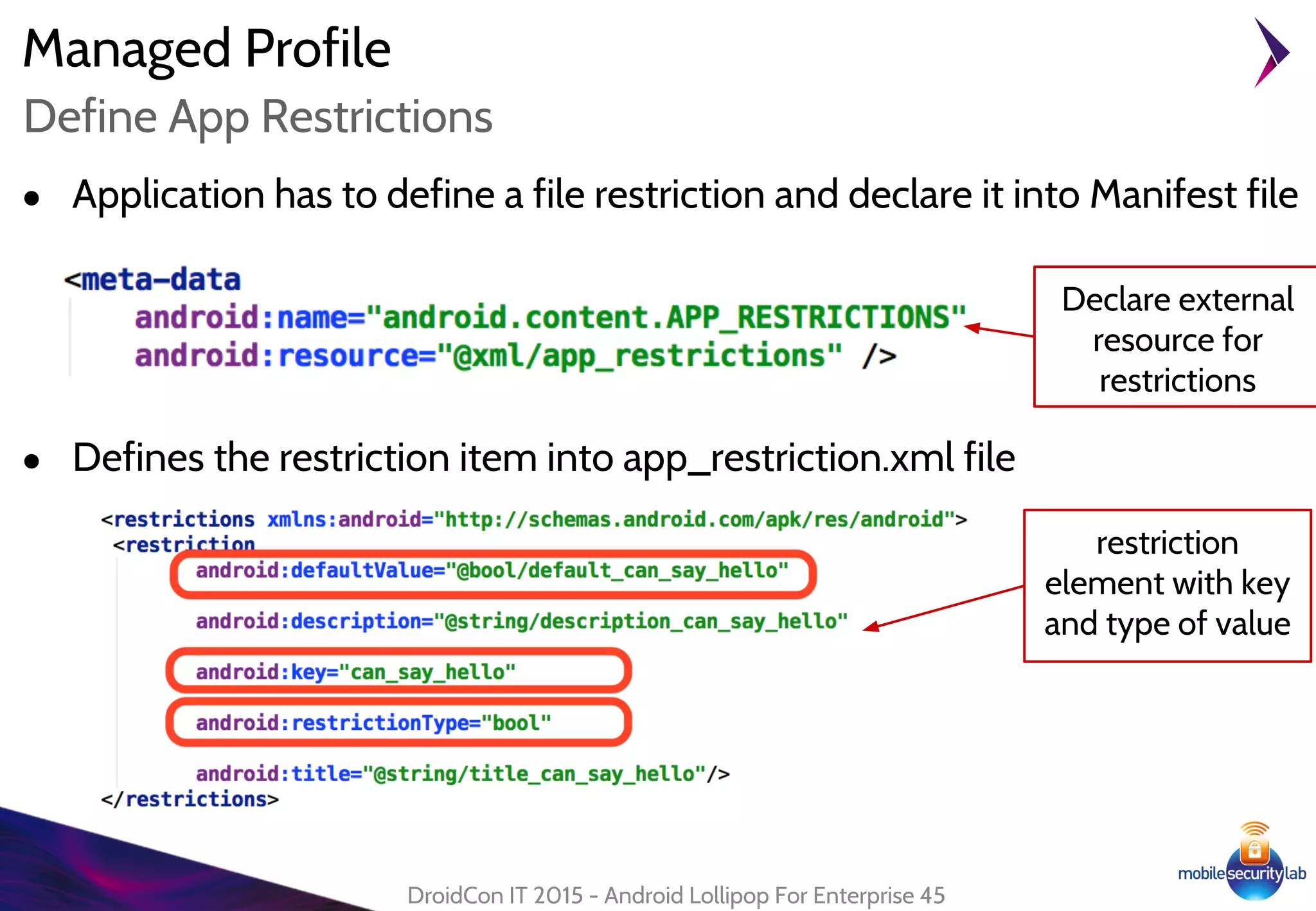
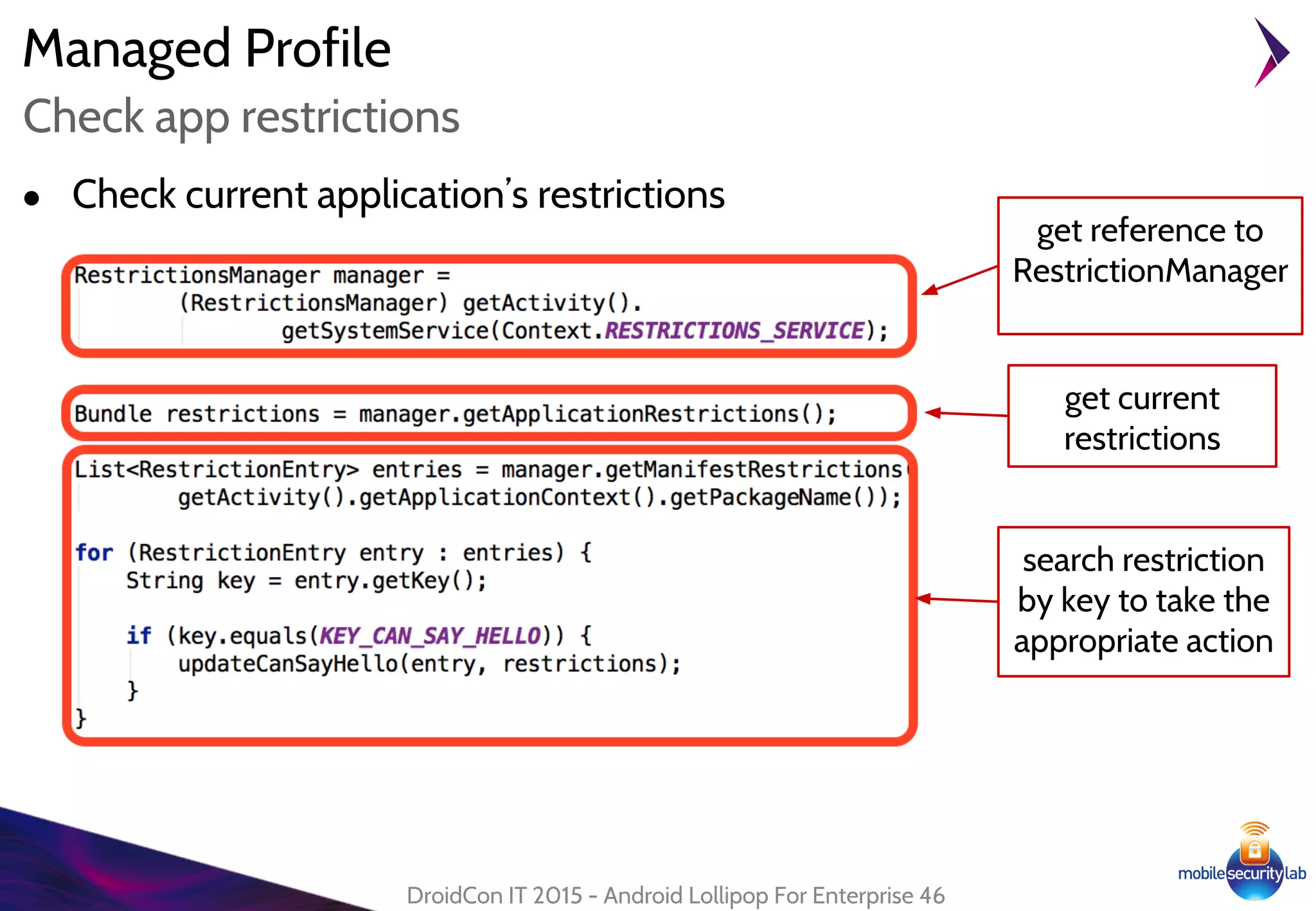
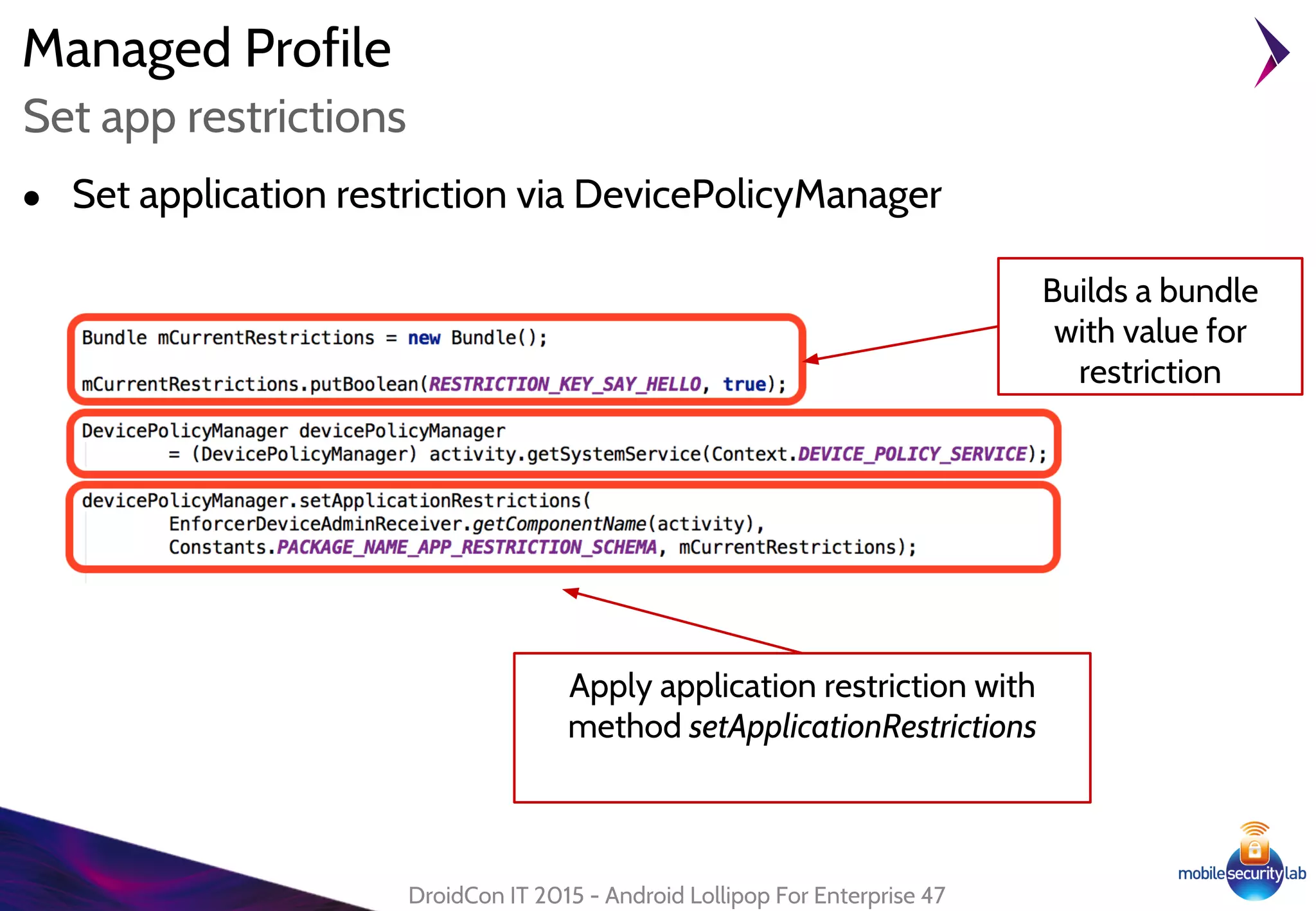
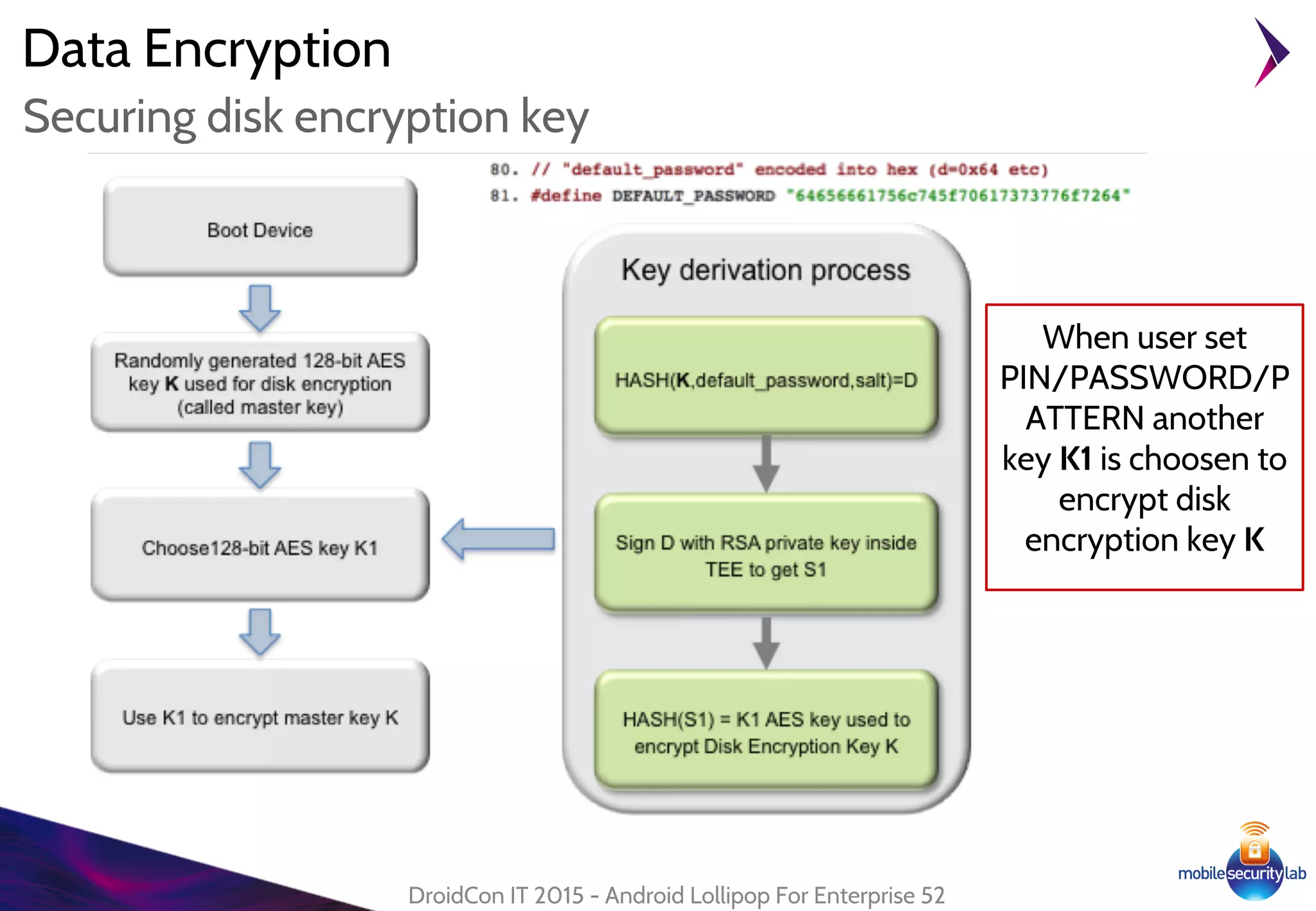
Android Lollipop introduced several new security features for enterprise mobile device management including enhanced SELinux policies, Smart Lock, Device Protection, the Device Administration API, and Managed Profiles. It also improved data encryption with faster encryption of only used blocks and support for encryption without password. These features help provide a more secure environment for enterprise mobility.






![Smart Lock
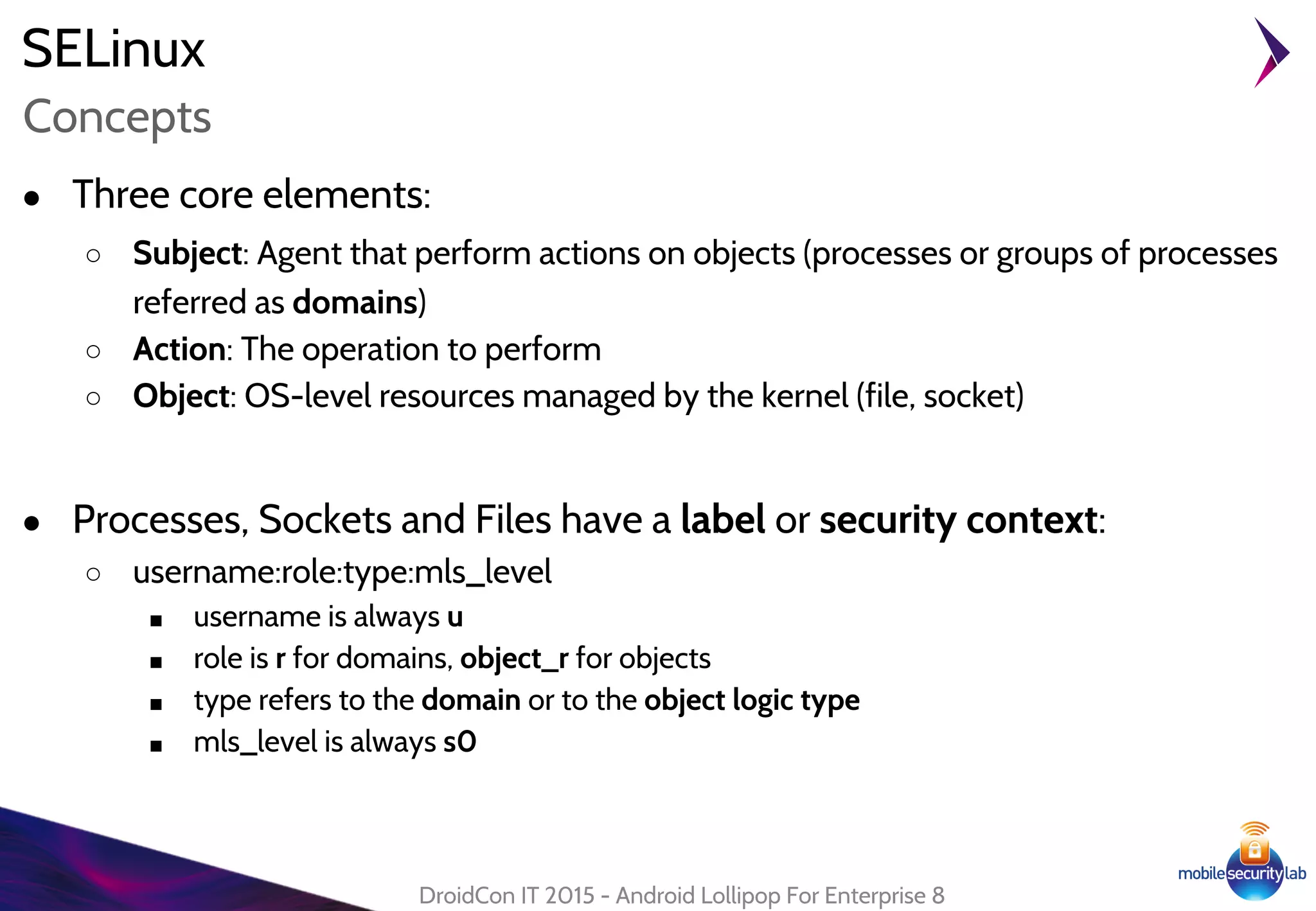
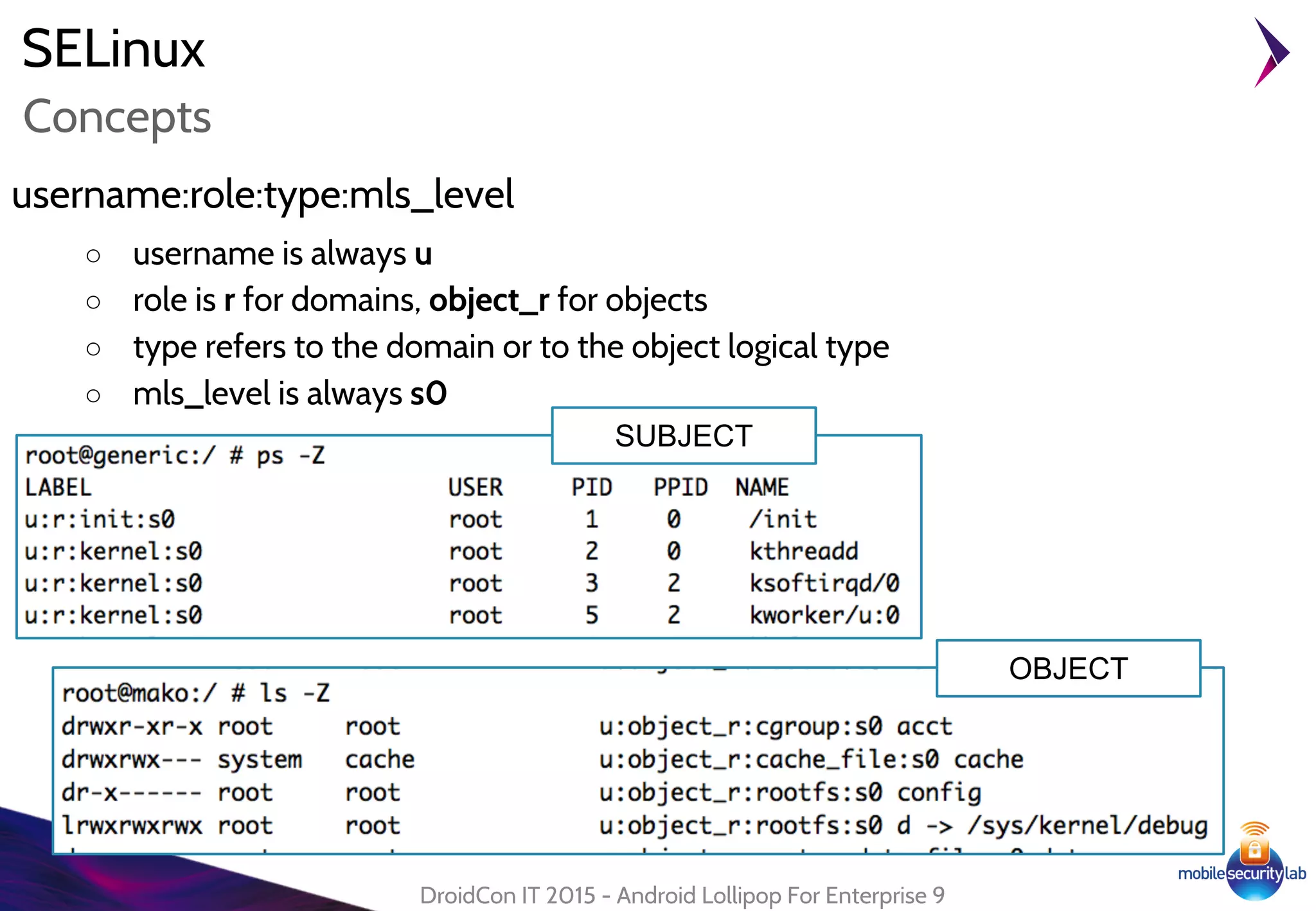
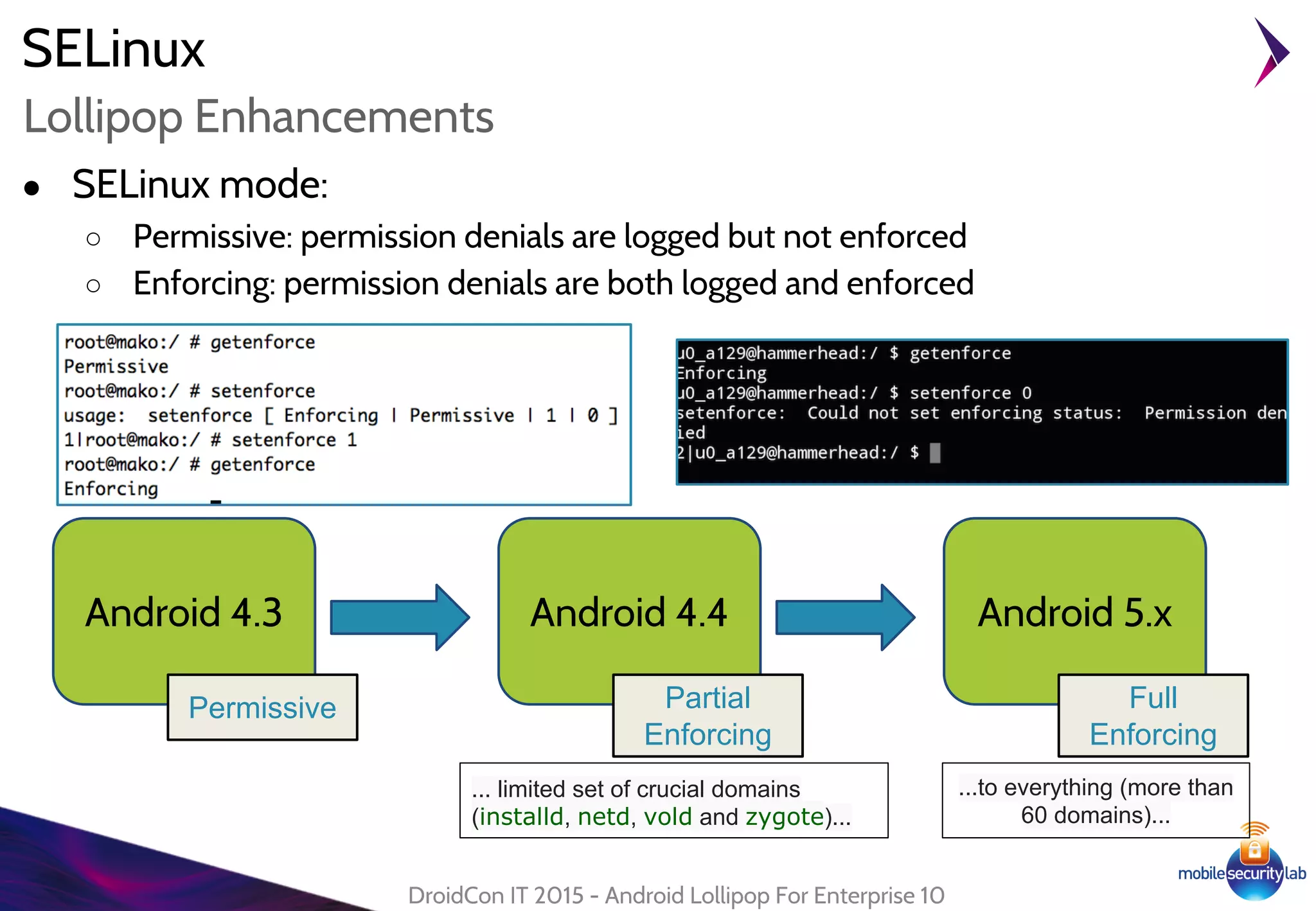
● Disable device lockscreen in "trusted condition"
● Based on Trust Agent:
○ "A service that notifies the system about whether it
believes the environment of the device to be trusted"
○ Requires signatureOrSystem permission
○ Can be disabled by Device Administrator
[KEYGUARD_DISABLE_TRUST_AGENTS]
DroidCon IT 2015 - Android Lollipop For Enterprise 12
Trust Agent
http://nelenkov.
blogspot.
it/2014/12/dissecting
-lollipops-smart-
lock.html
lollipop/frameworks/base/core/res/AndroidManifest.xml](https://image.slidesharecdn.com/droidcon-it-2015-androidlollipopforenterprise-slide-150413075634-conversion-gate01/75/Droidcon-it-2015-Android-Lollipop-for-Enterprise-12-2048.jpg)