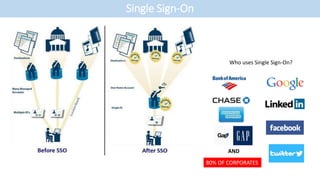
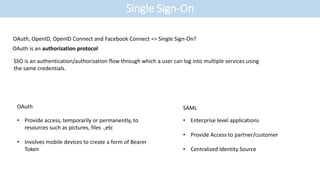
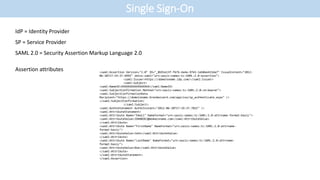
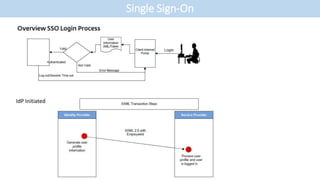
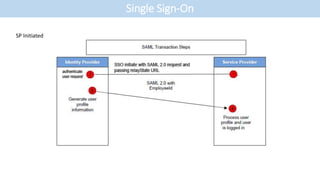
- The document discusses single sign-on (SSO) integration and implementation. It defines key terms like identity provider (IdP), service provider (SP), and Security Assertion Markup Language (SAML) 2.0.
- It outlines the typical steps to set up SSO between an IdP and SP, such as defining the user information to exchange and establishing an encrypted connection.
- SAML 2.0 is presented as the industry standard for SSO, with descriptions of its components like assertions and attributes that specify user details.