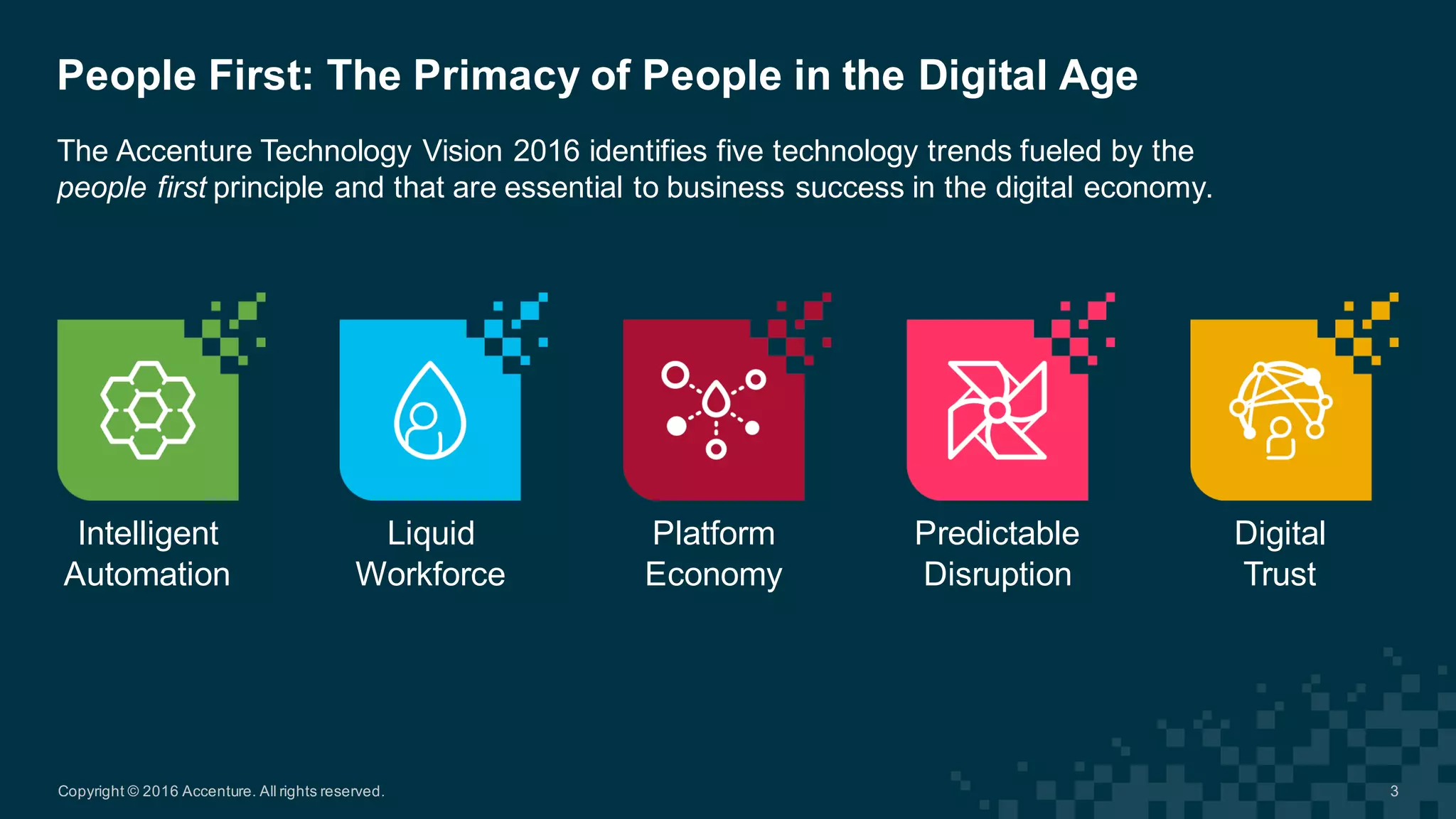
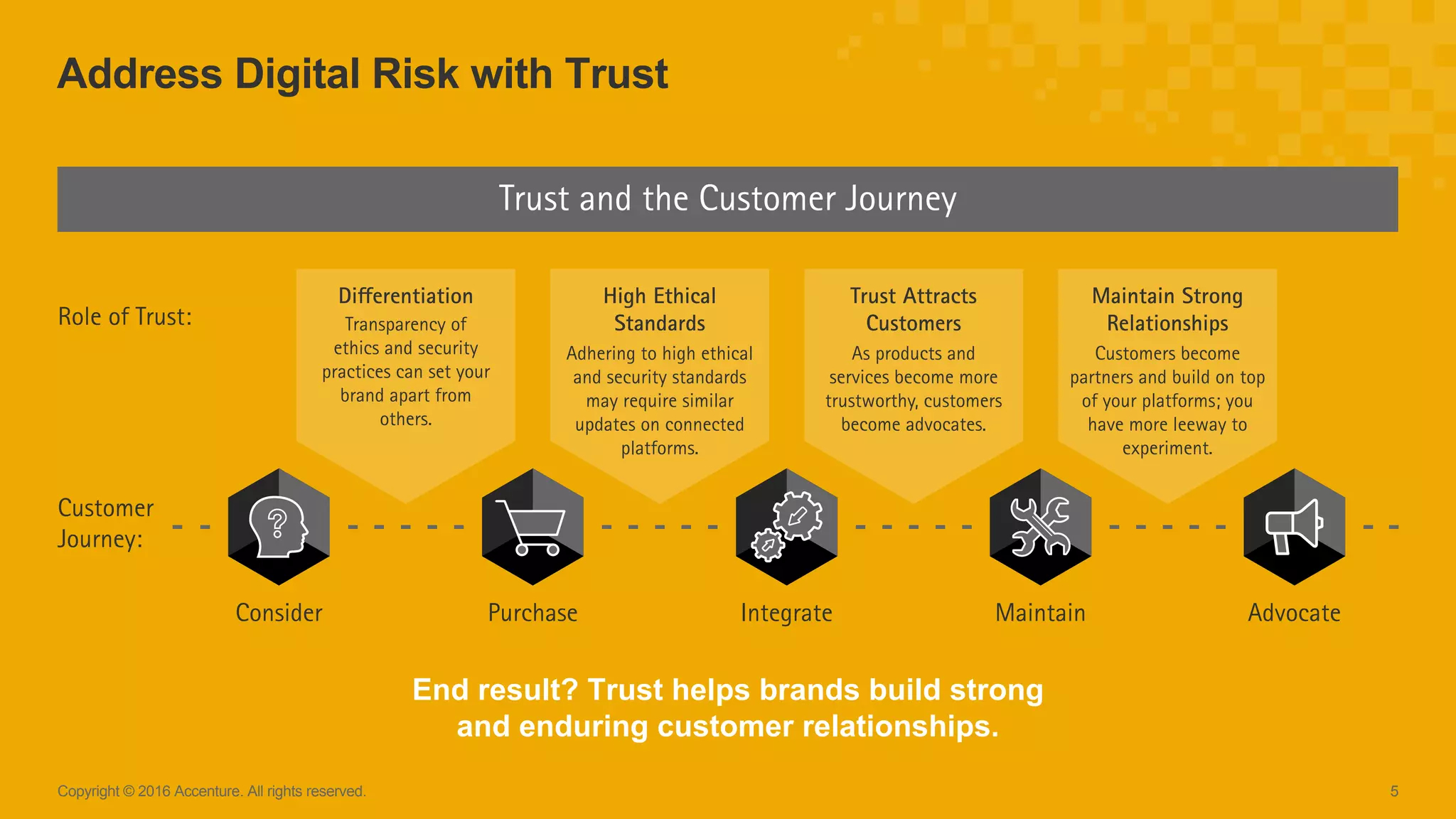
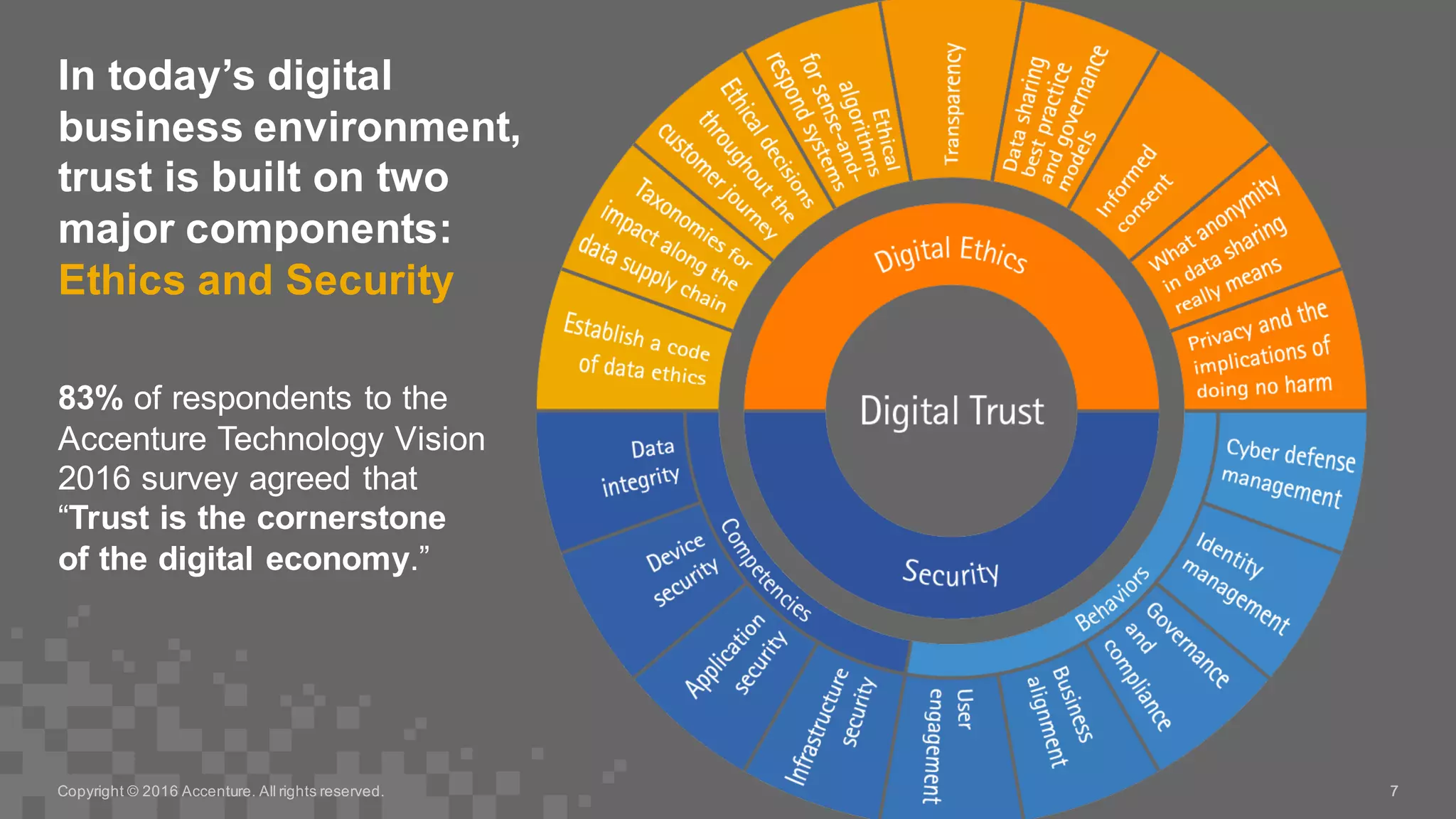
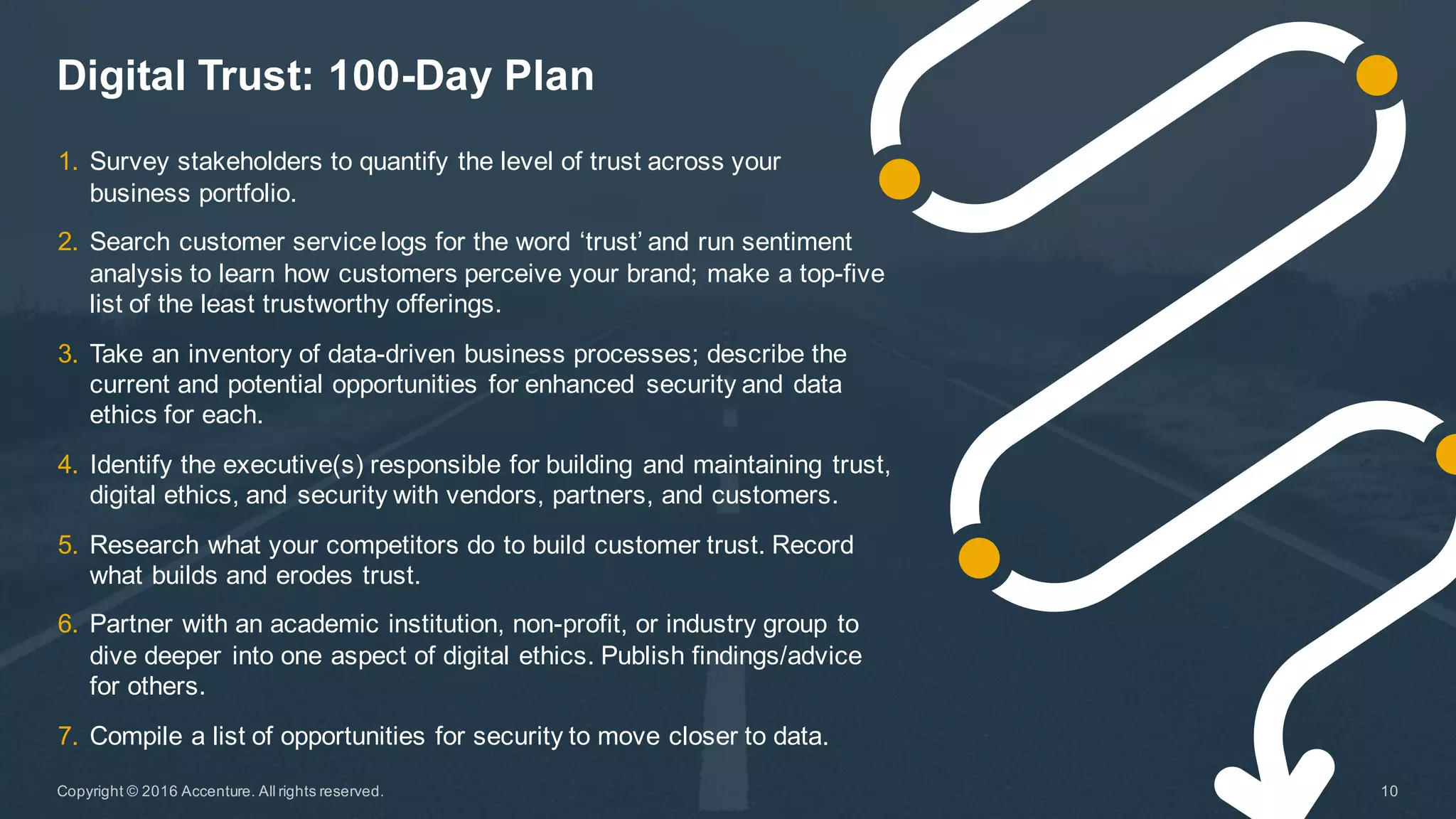
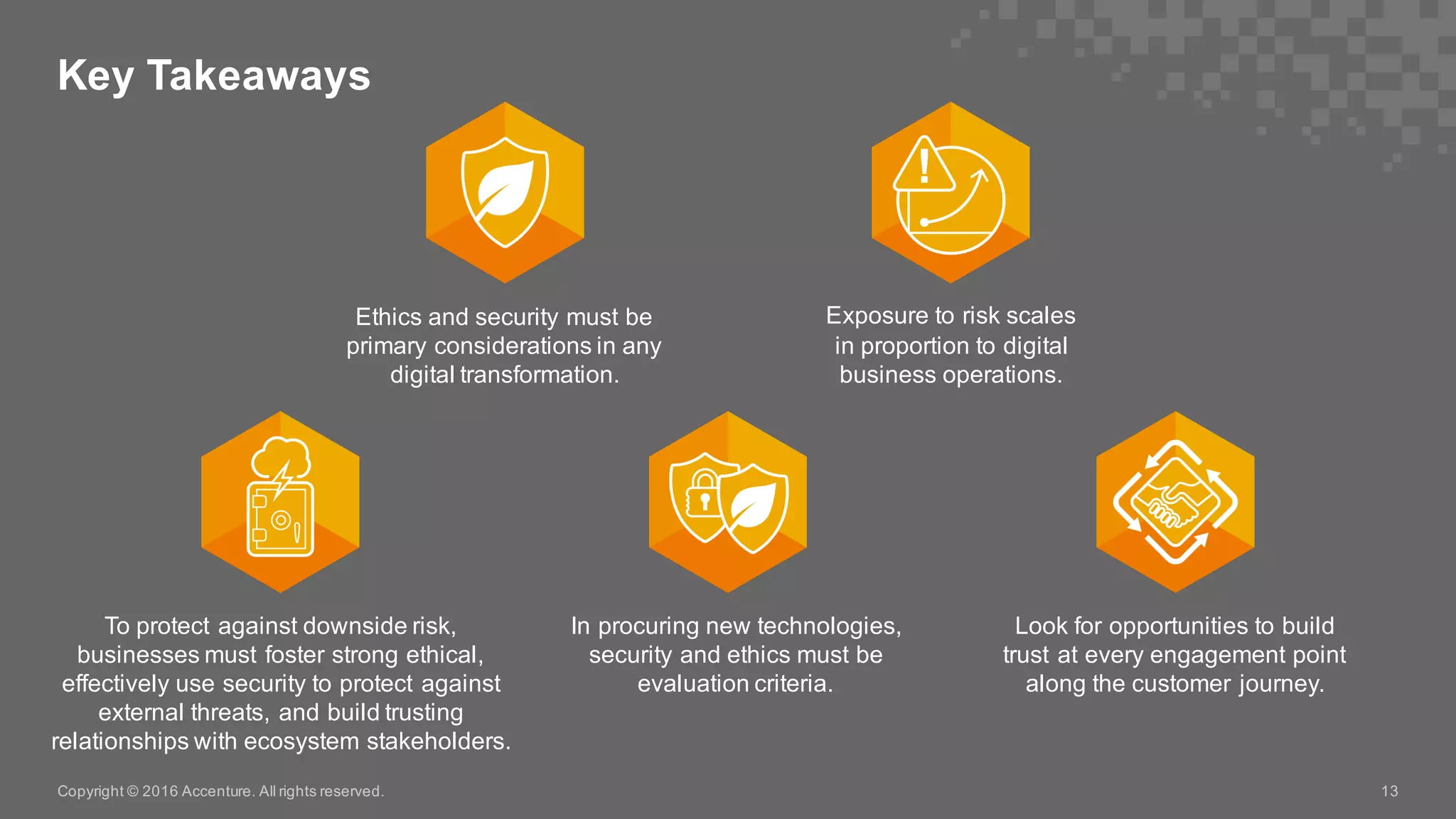
The Accenture Technology Vision 2016 emphasizes the importance of digital trust in the digital economy, highlighting that trust is essential for strong customer relationships and requires a balance of ethics and robust security. As businesses face increasing data-centric risks, implementing security measures that prioritize data protection and ethical practices is crucial for building trust with customers. The document outlines a 100-day and 365-day plan for companies to enhance trust, calling for dedicated roles such as Chief Trust Officer and integration of trust into business processes.