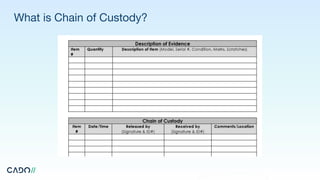
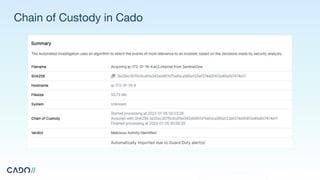
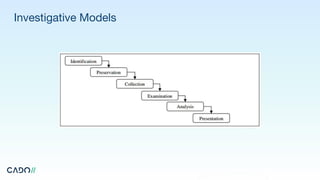
The document outlines the fundamentals of digital forensics and incident response, highlighting the importance of volatile and persistent data in investigations. It details the roles within an incident response team and emphasizes the need for preparedness, including communication plans and business continuity strategies. Additionally, it provides guidance on the investigation process, containment, remediation, and essential questions to consider during an incident.