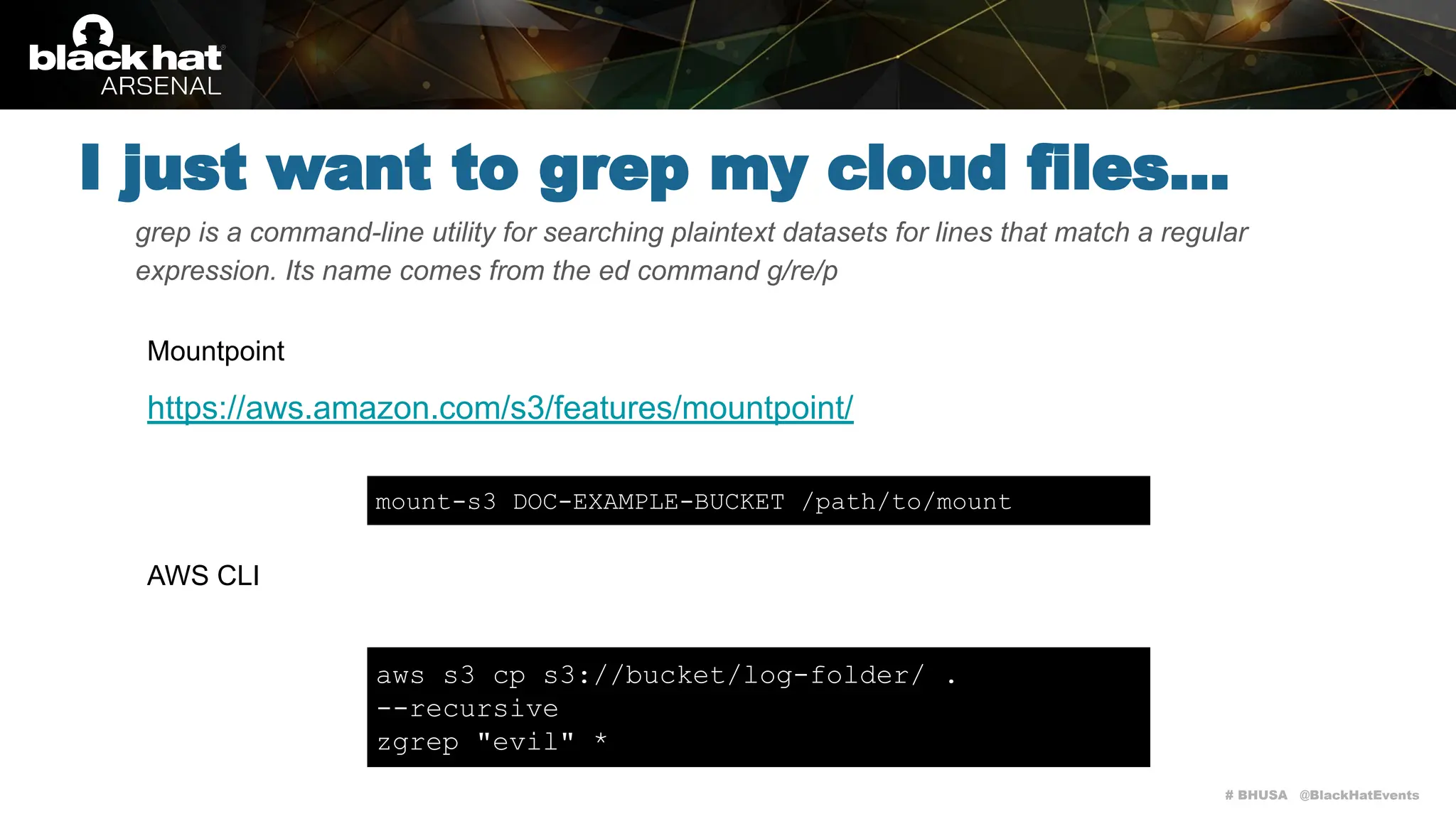
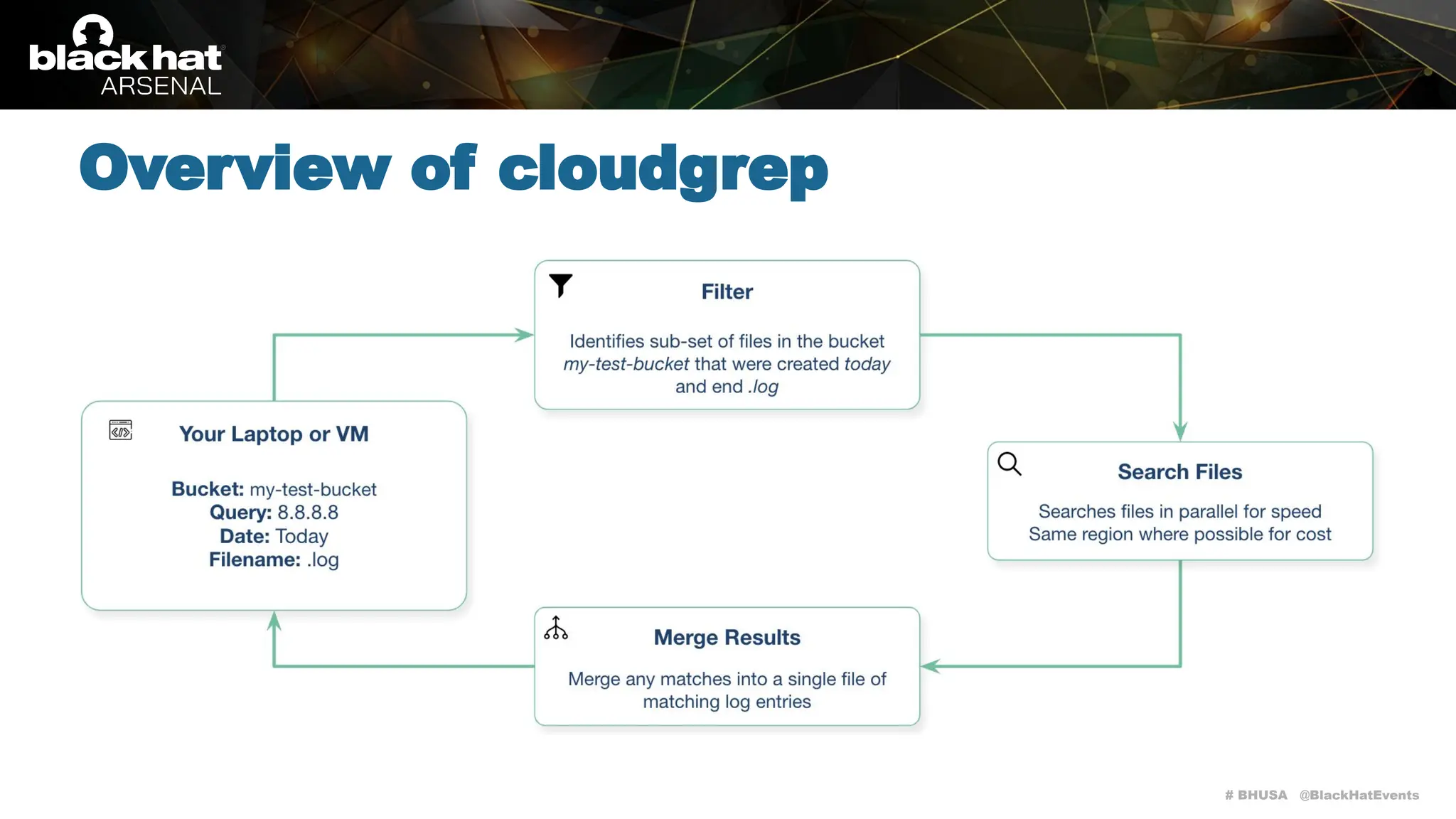
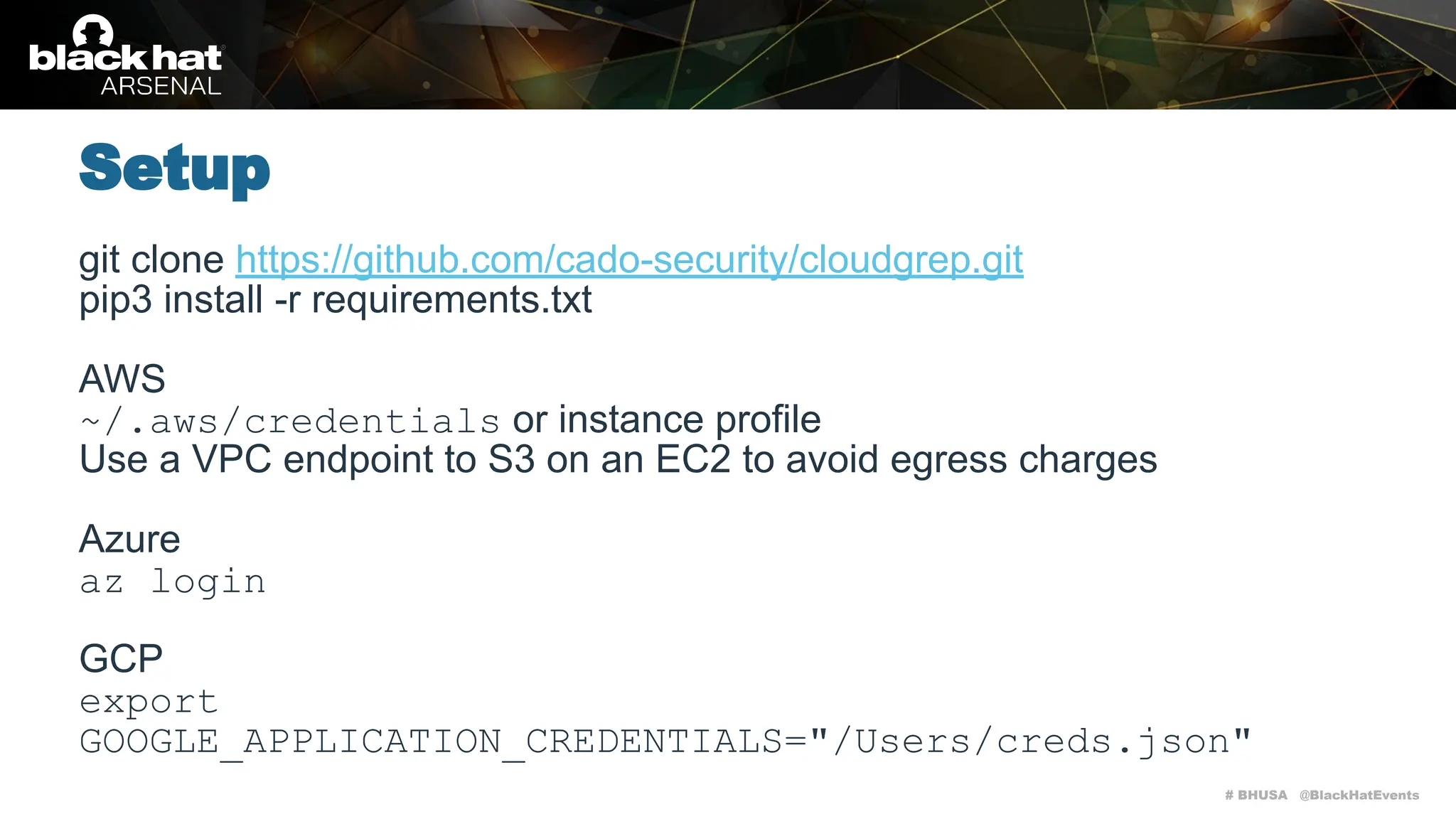
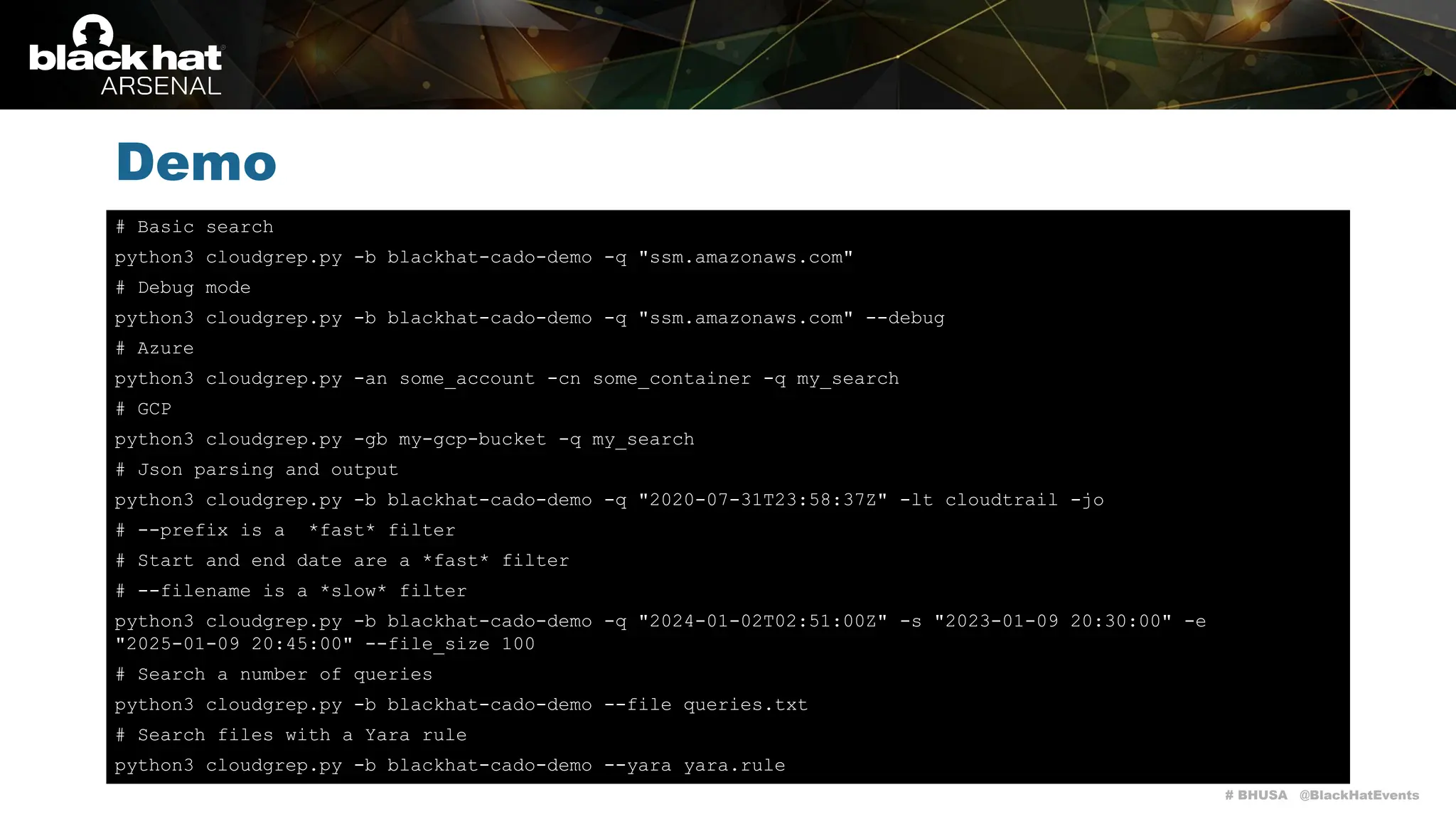
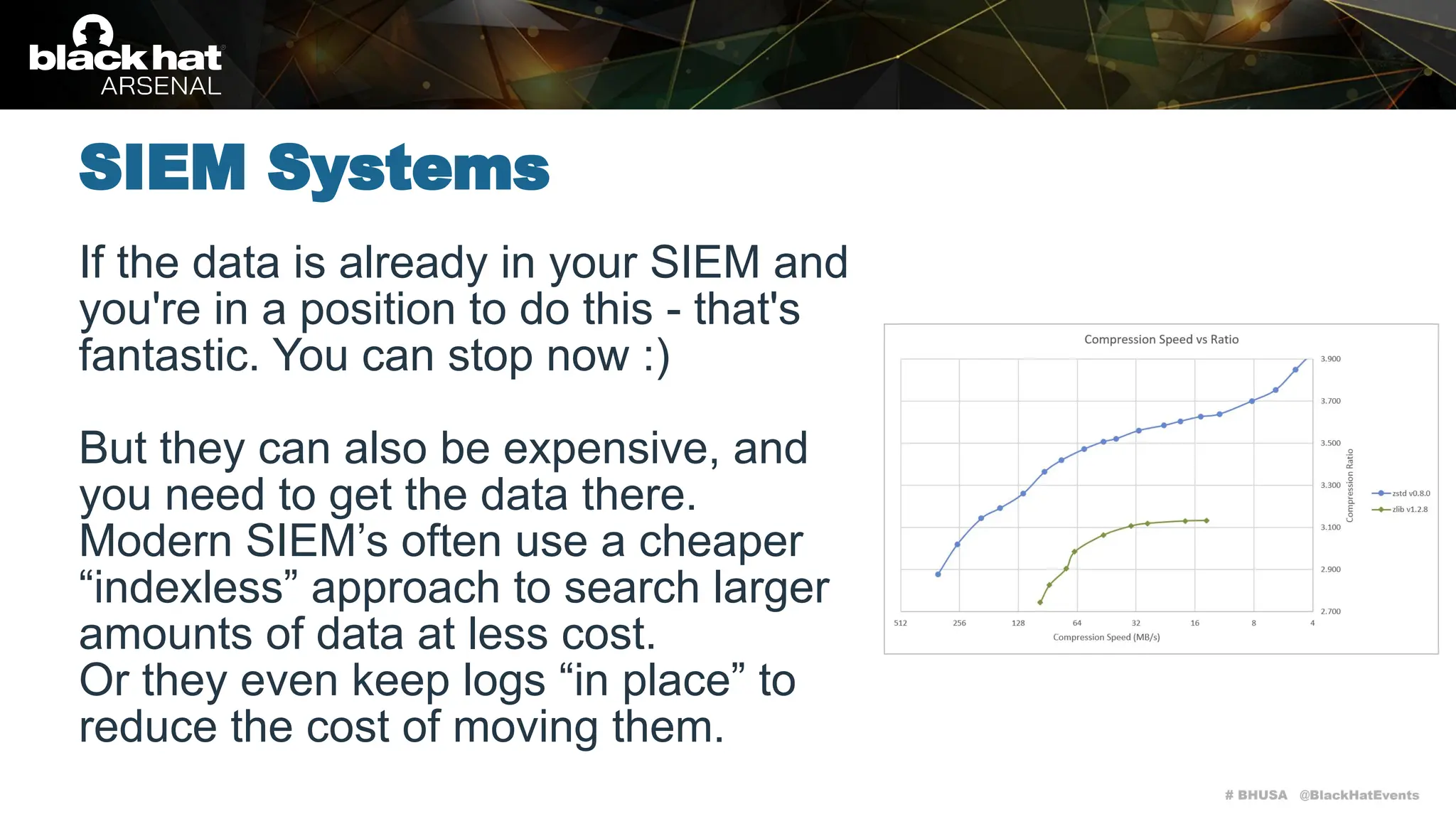
Cloudgrep is a command-line utility designed for searching cloud storage files without the need for indexing, supporting AWS, Azure, and GCP. It allows for fast parallel searches of plaintext, compressed, and binary files, and can run detection rules via regex or YARA. The document includes installation instructions, basic usage examples, and highlights contributions from the community.



![# BHUSA @BlackHatEvents
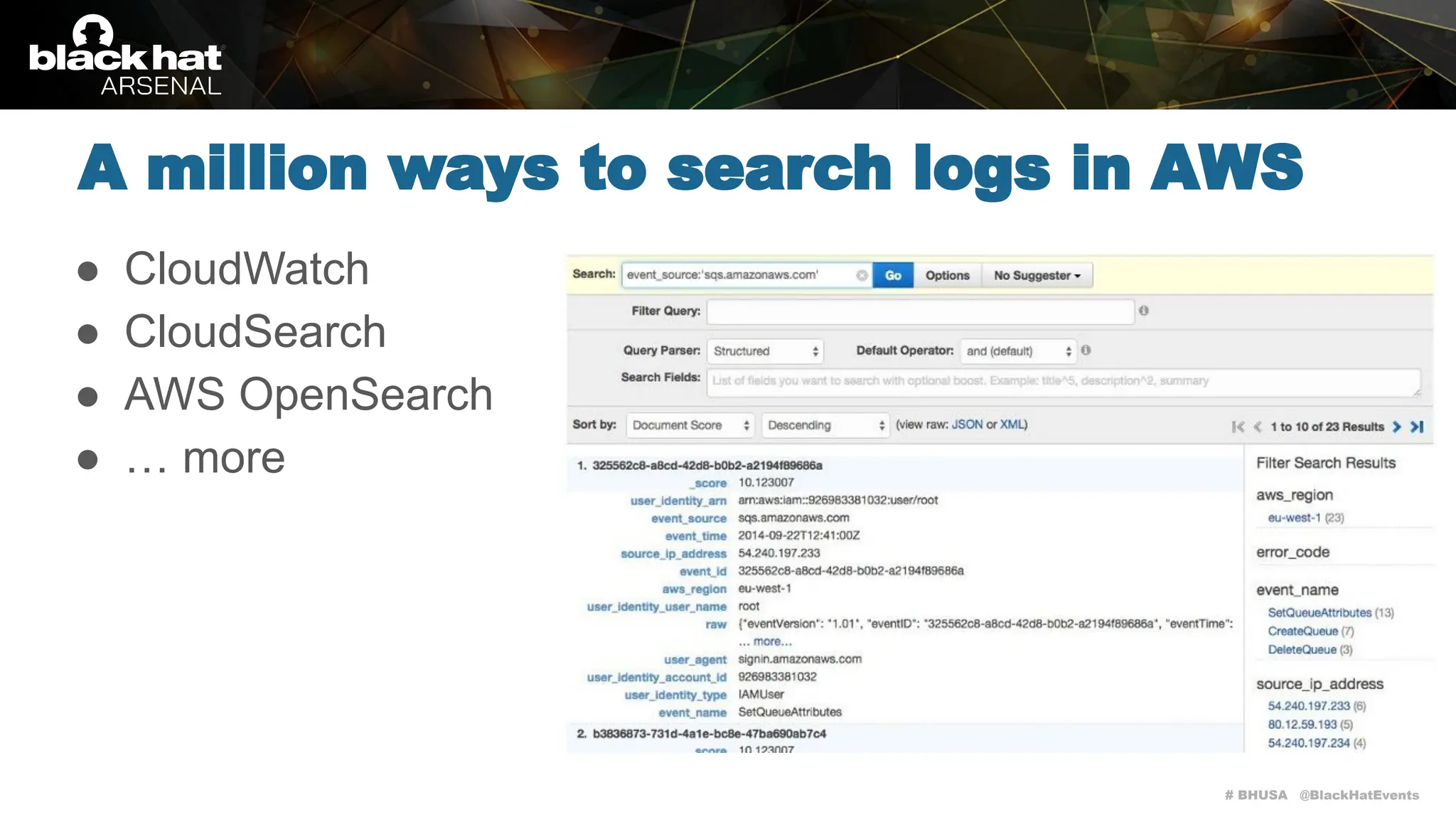
Athena for parsing and searching logs in
S3
CREATE EXTERNAL TABLE IF NOT EXISTS elb_logs_raw_native (
request_timestamp string,
request_ip string,
request_port int,
backend_ip string,
backend_port int, …)
ROW FORMAT SERDE 'org.apache.hadoop.hive.serde2.RegexSerDe'
WITH SERDEPROPERTIES (
'serialization.format' = '1','input.regex' = '([^ ]*) ... ([A-Za-z0-9.-]*)$' )
LOCATION 's3://athena-examples/elb/raw/';
SELECT * FROM elb_logs_raw_native WHERE elb_response_code = '200' LIMIT 100;
See also: Automated First-Response in AWS using Sigma and
Athena Invictus Incident Response Invictus Incident Response](https://image.slidesharecdn.com/cloudgrep-blackhataresenal-240811111702-8e986eb8/75/Cloudgrep-Blackhat-Aresenal-cloudgrep-searches-cloud-storage-7-2048.jpg)