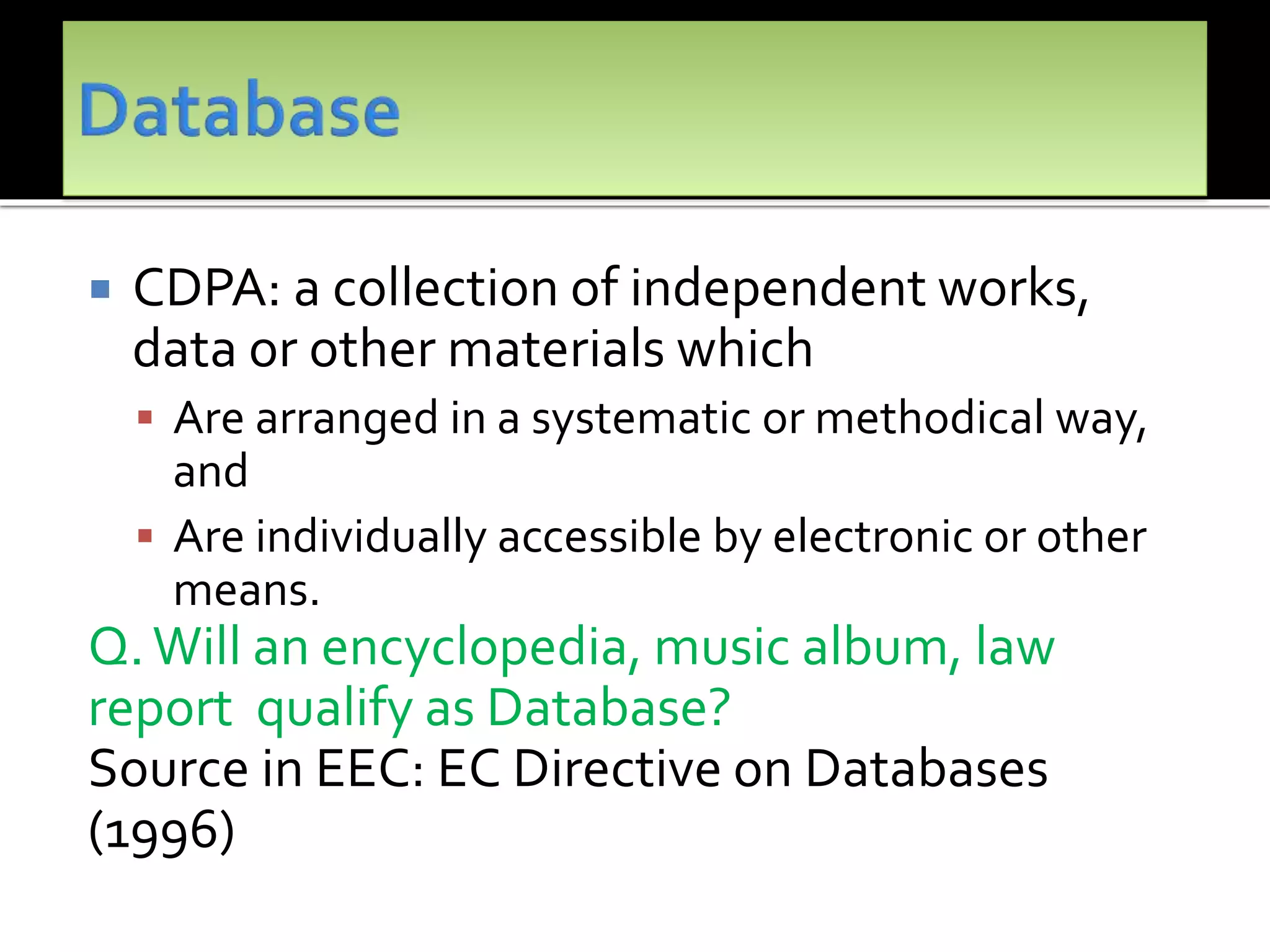
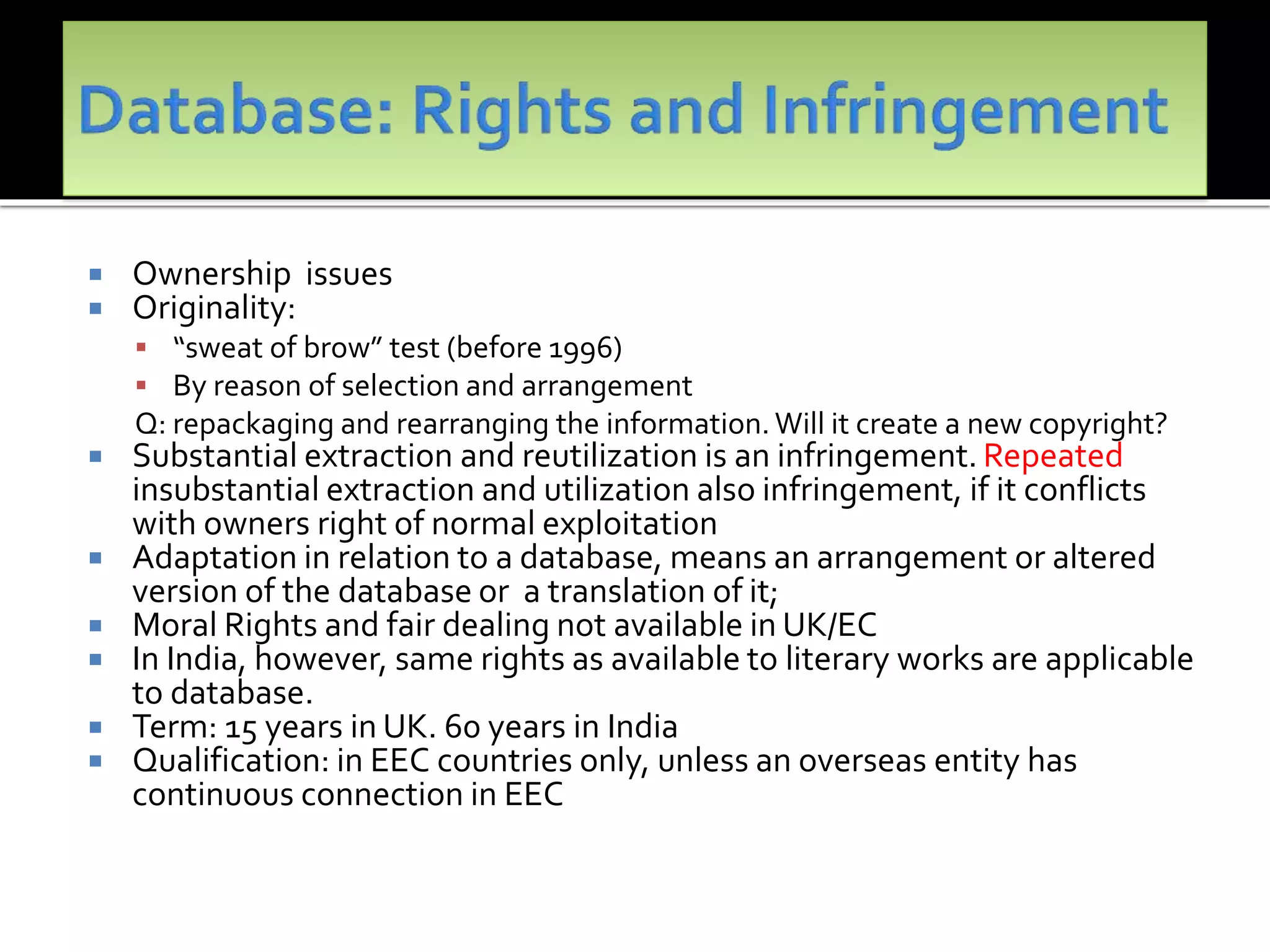
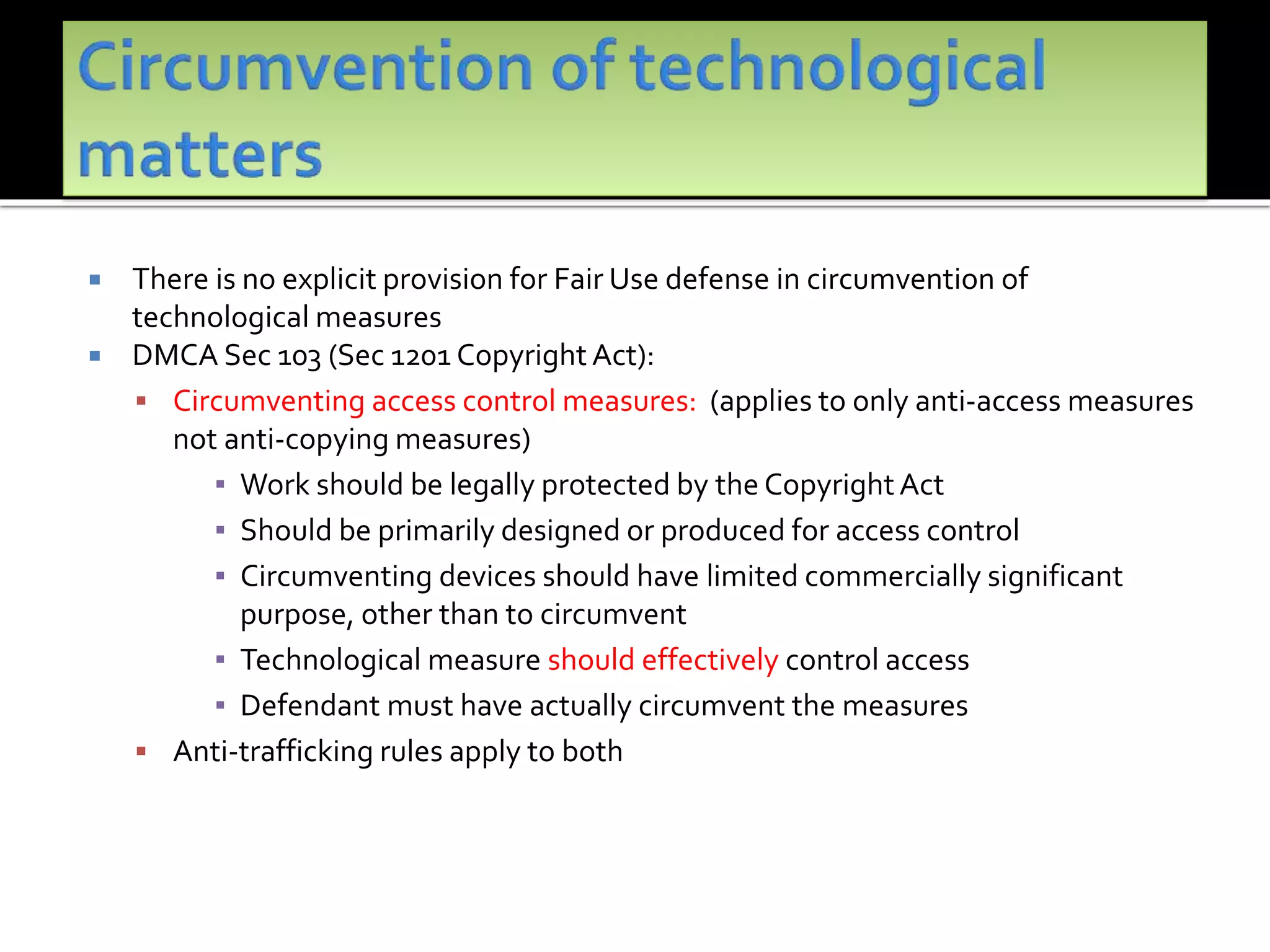
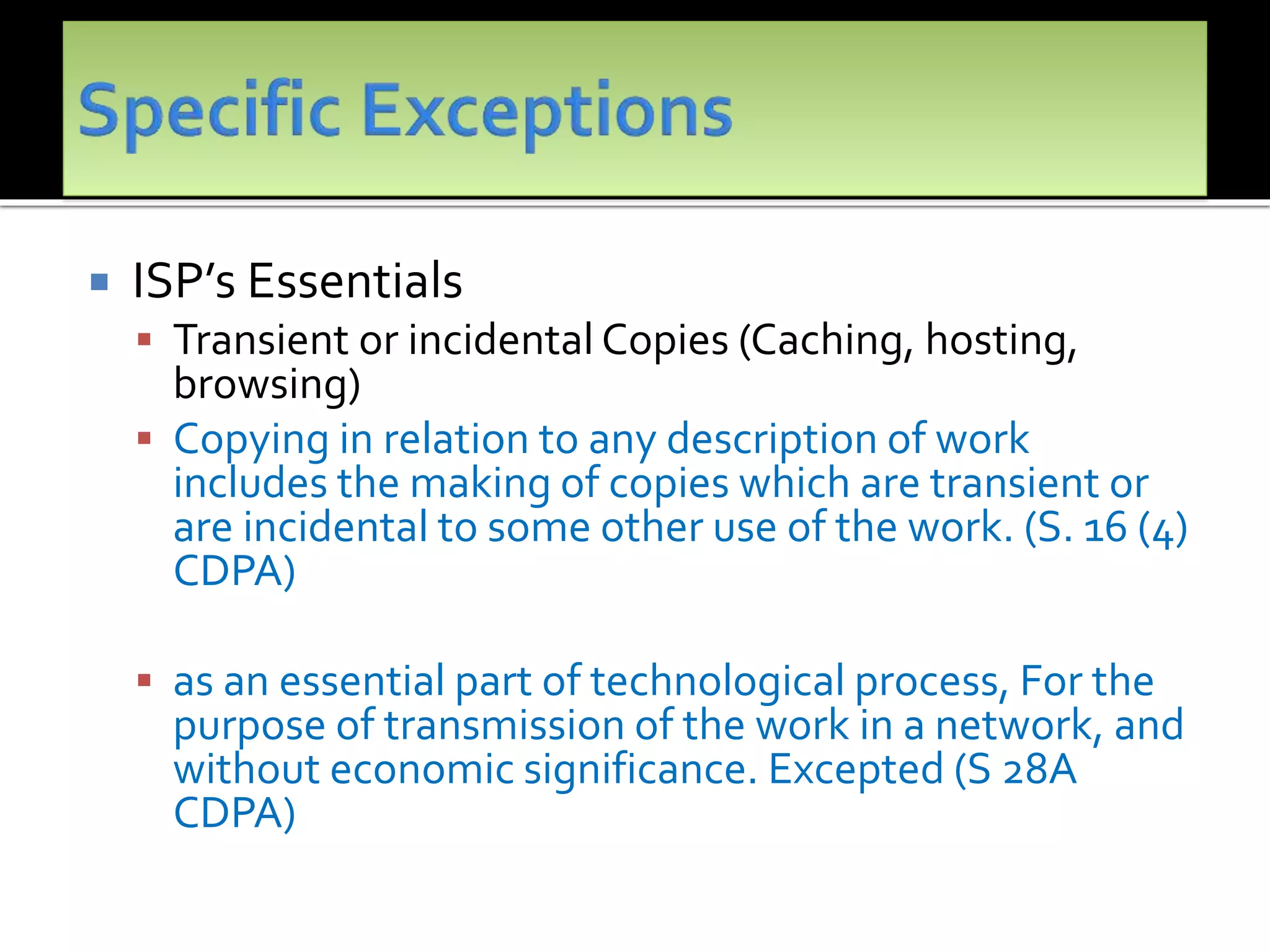
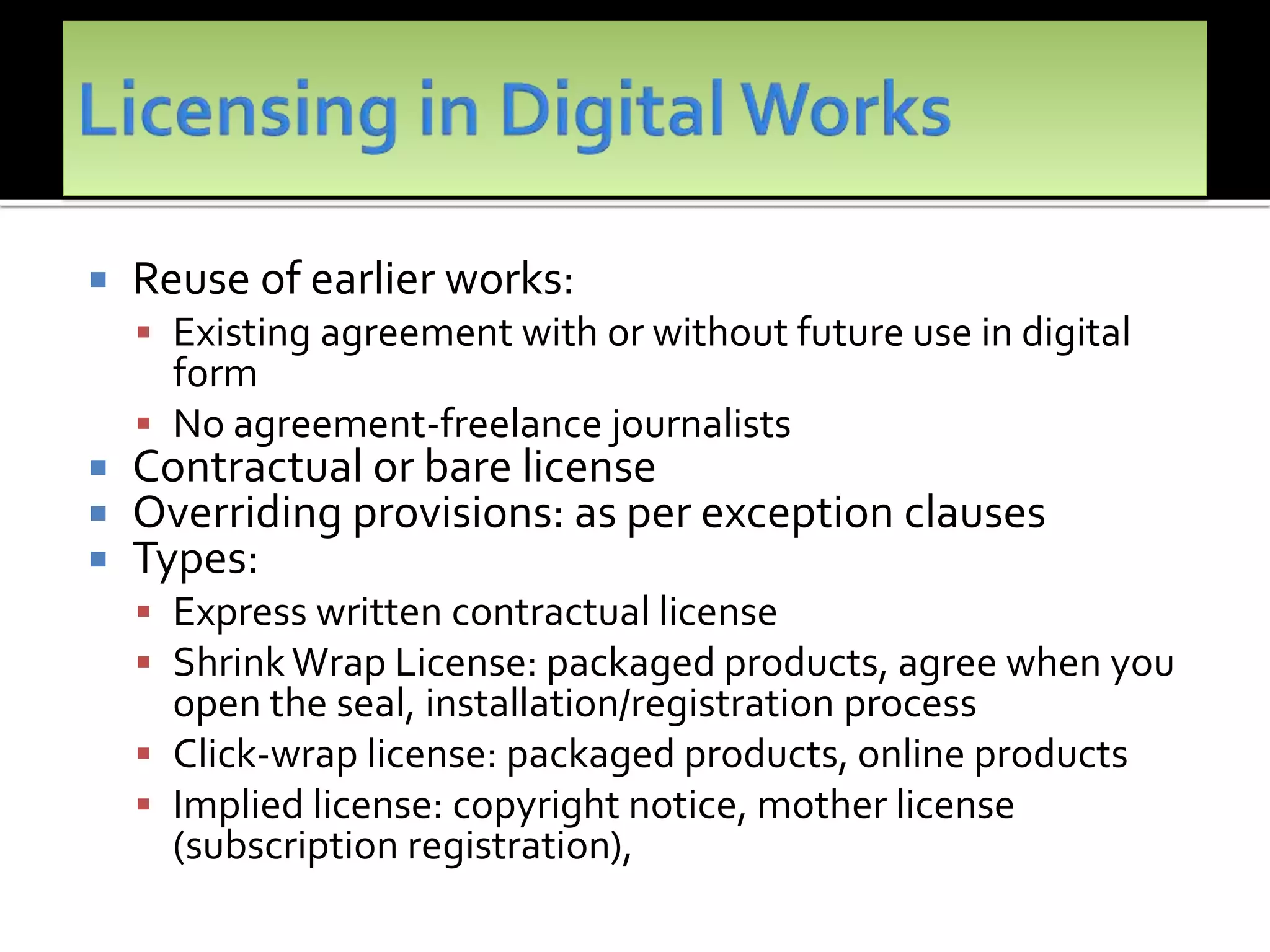
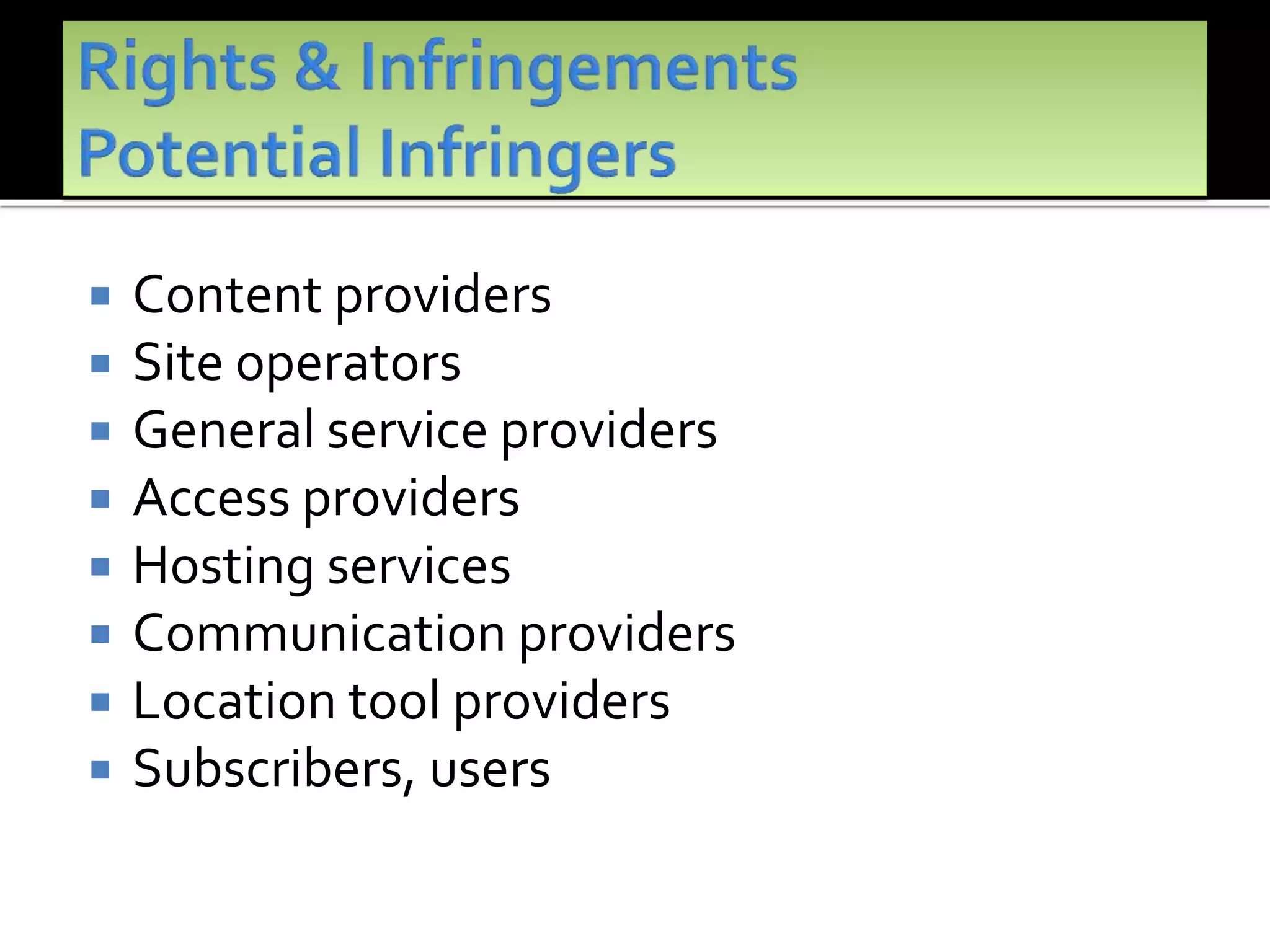
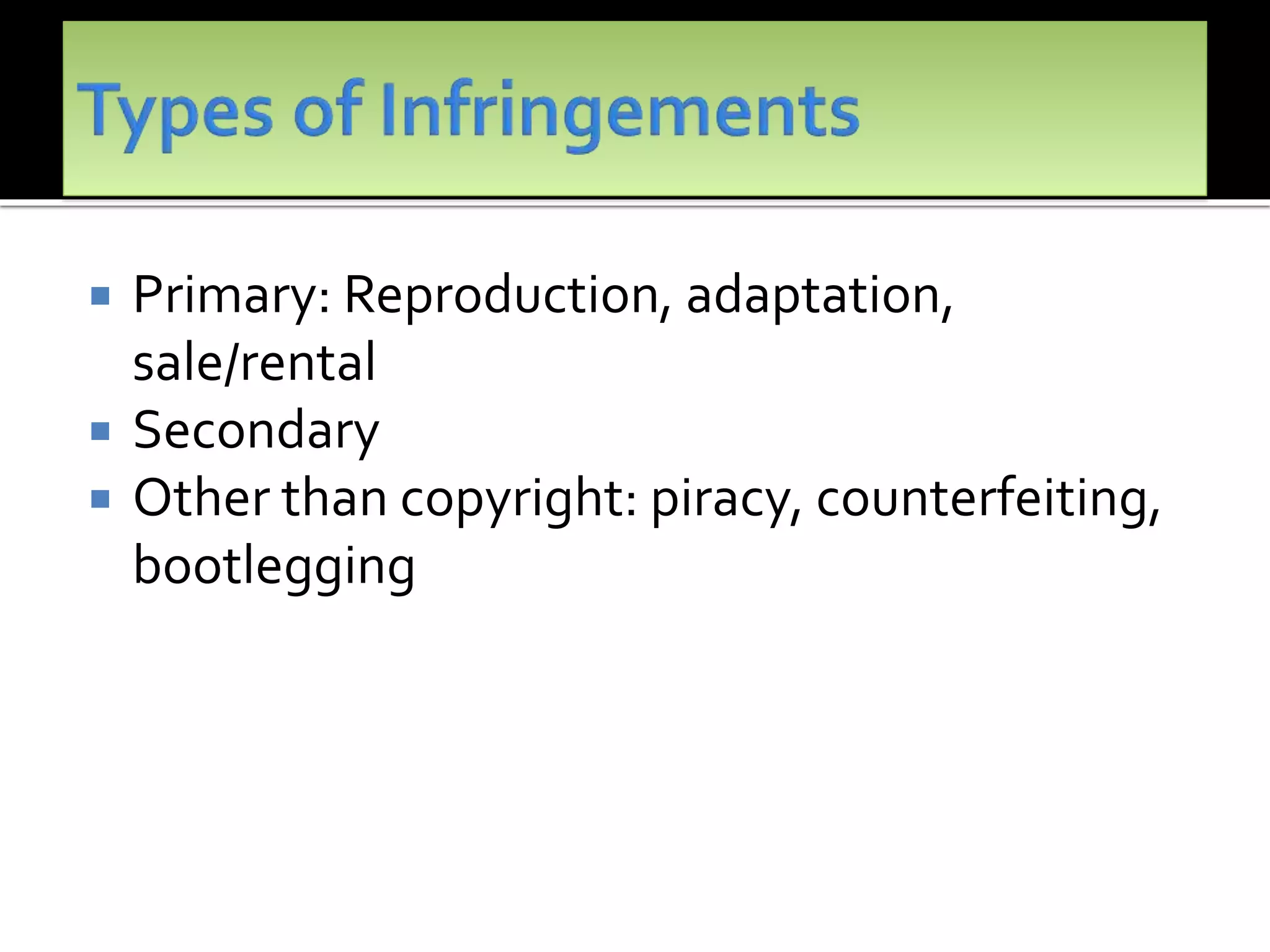
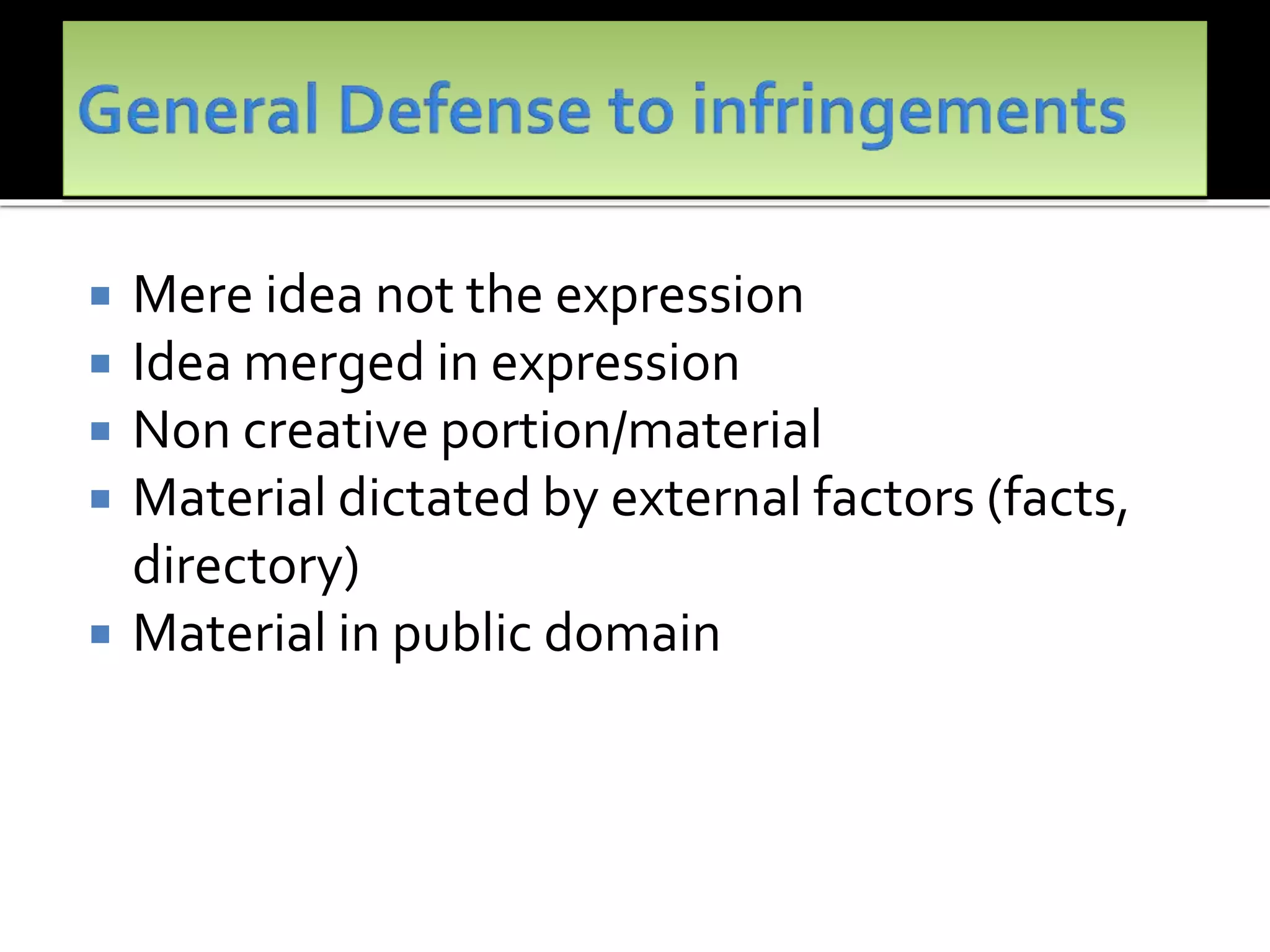
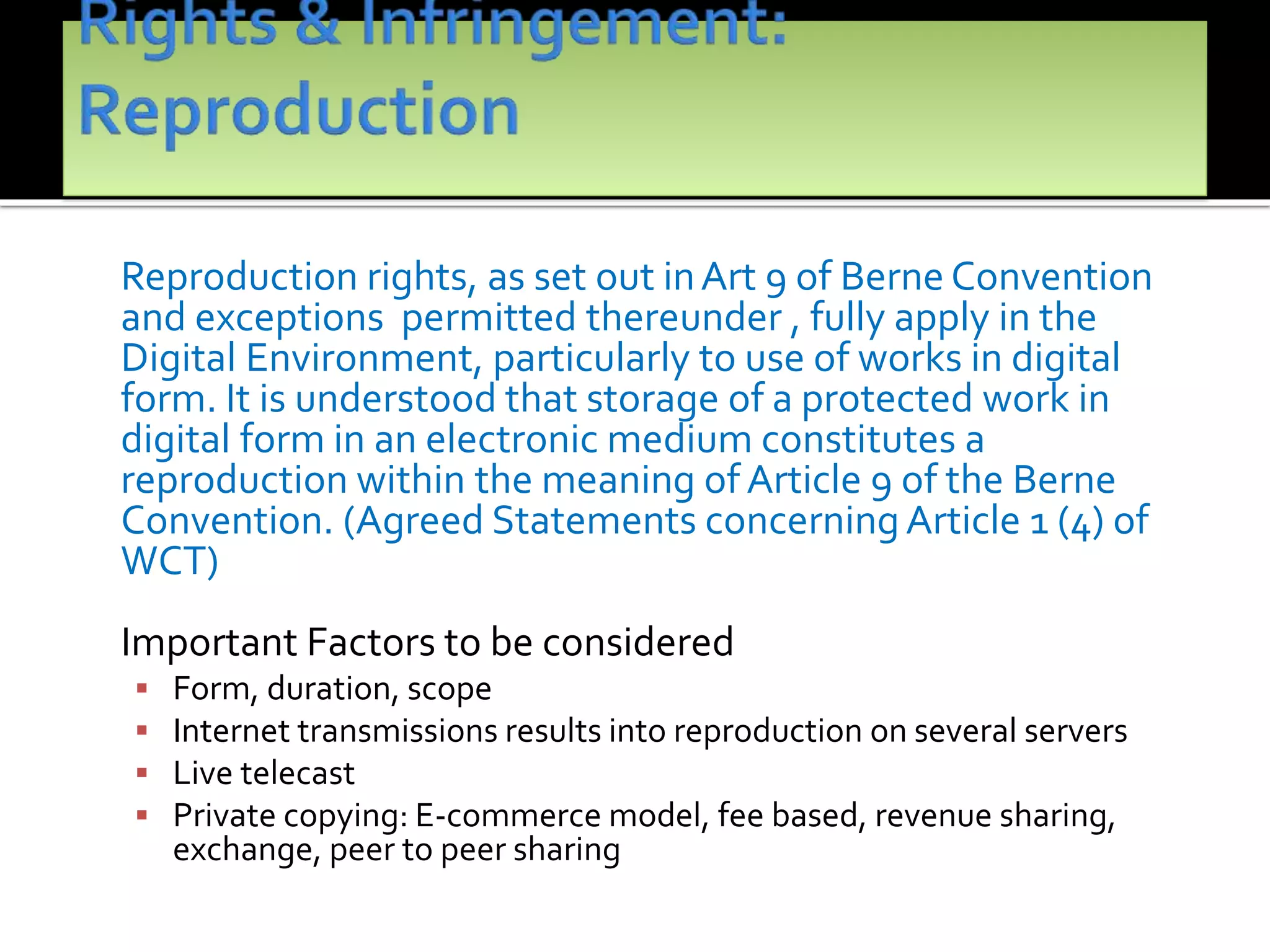
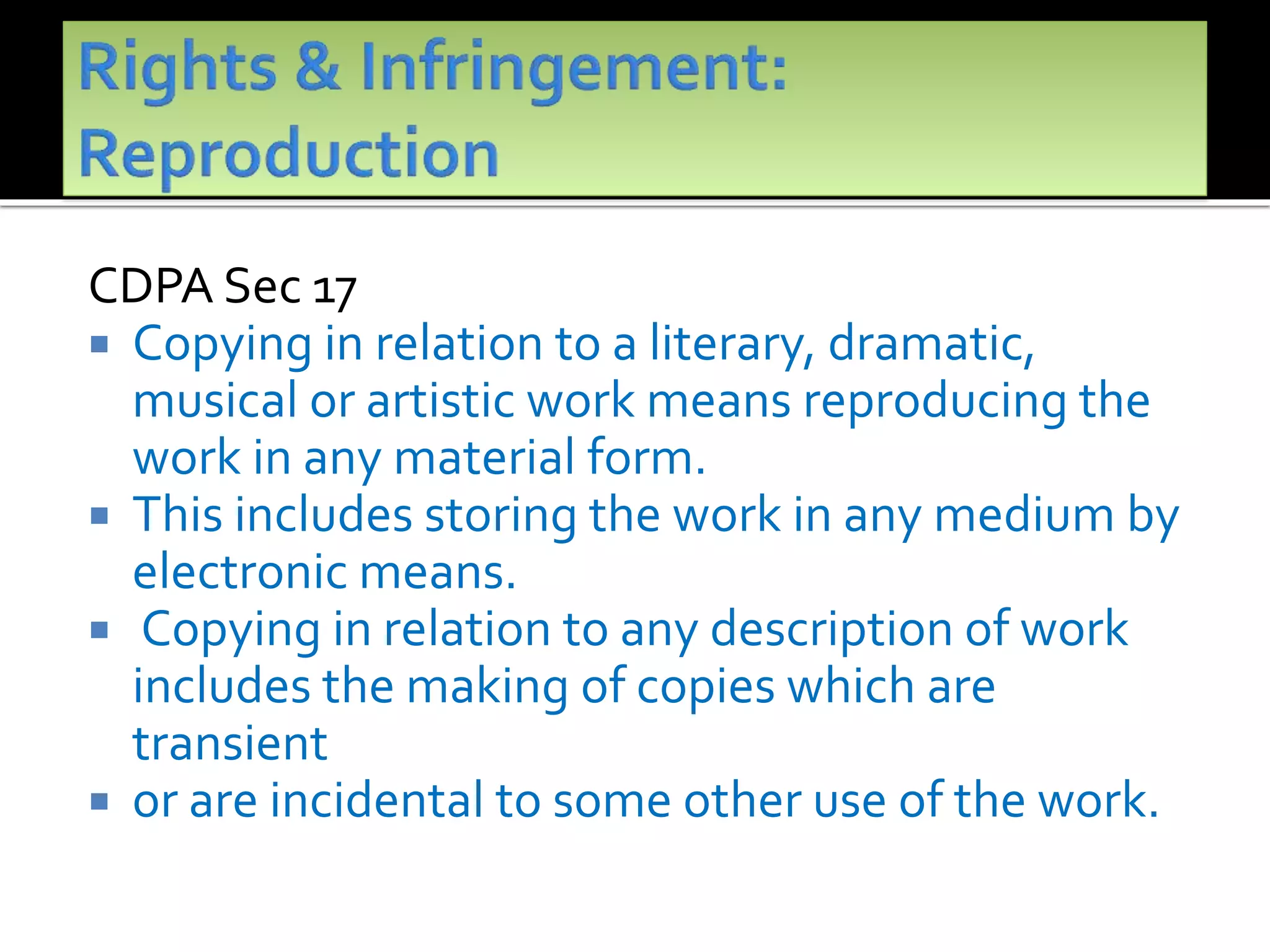
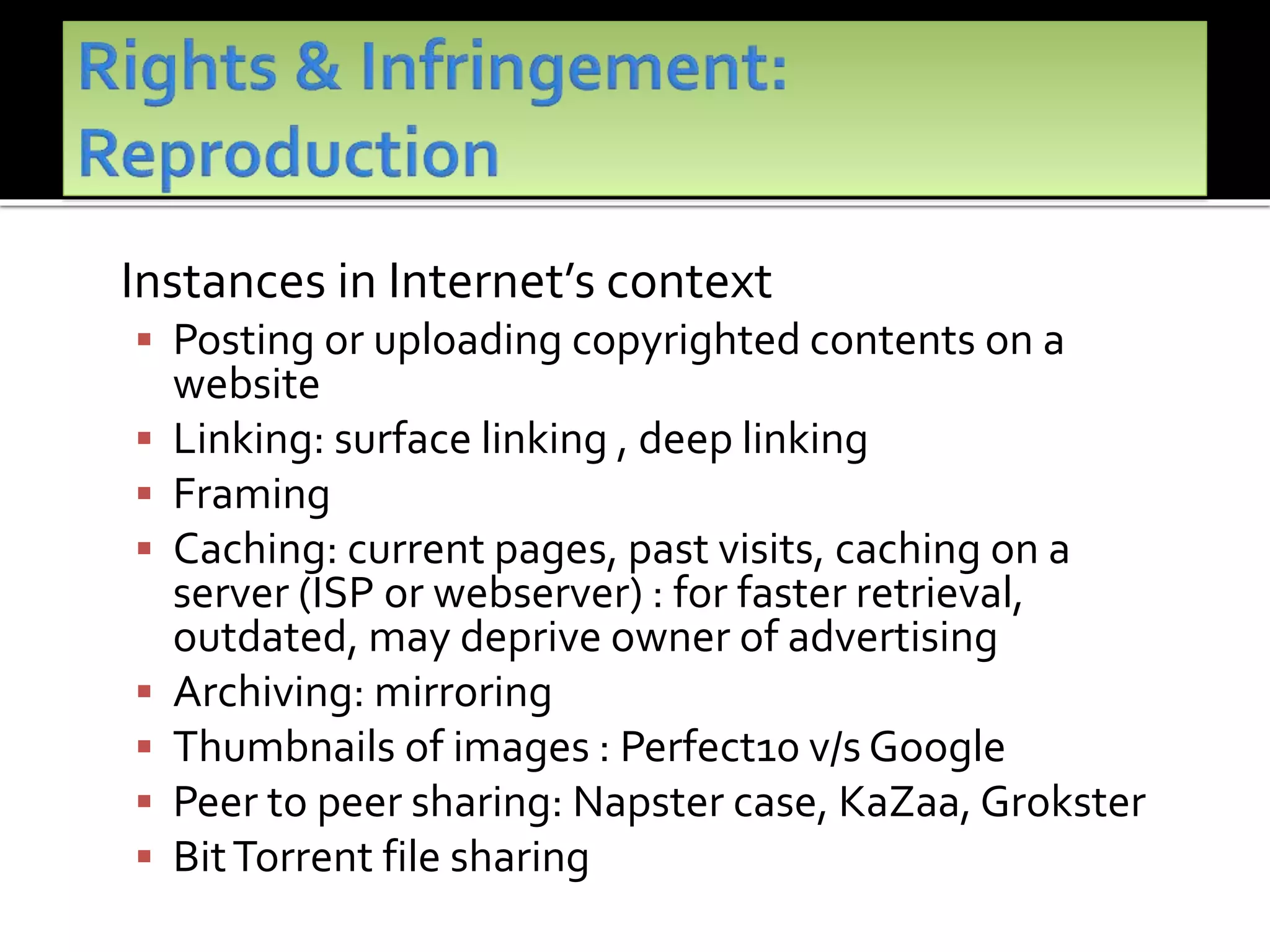
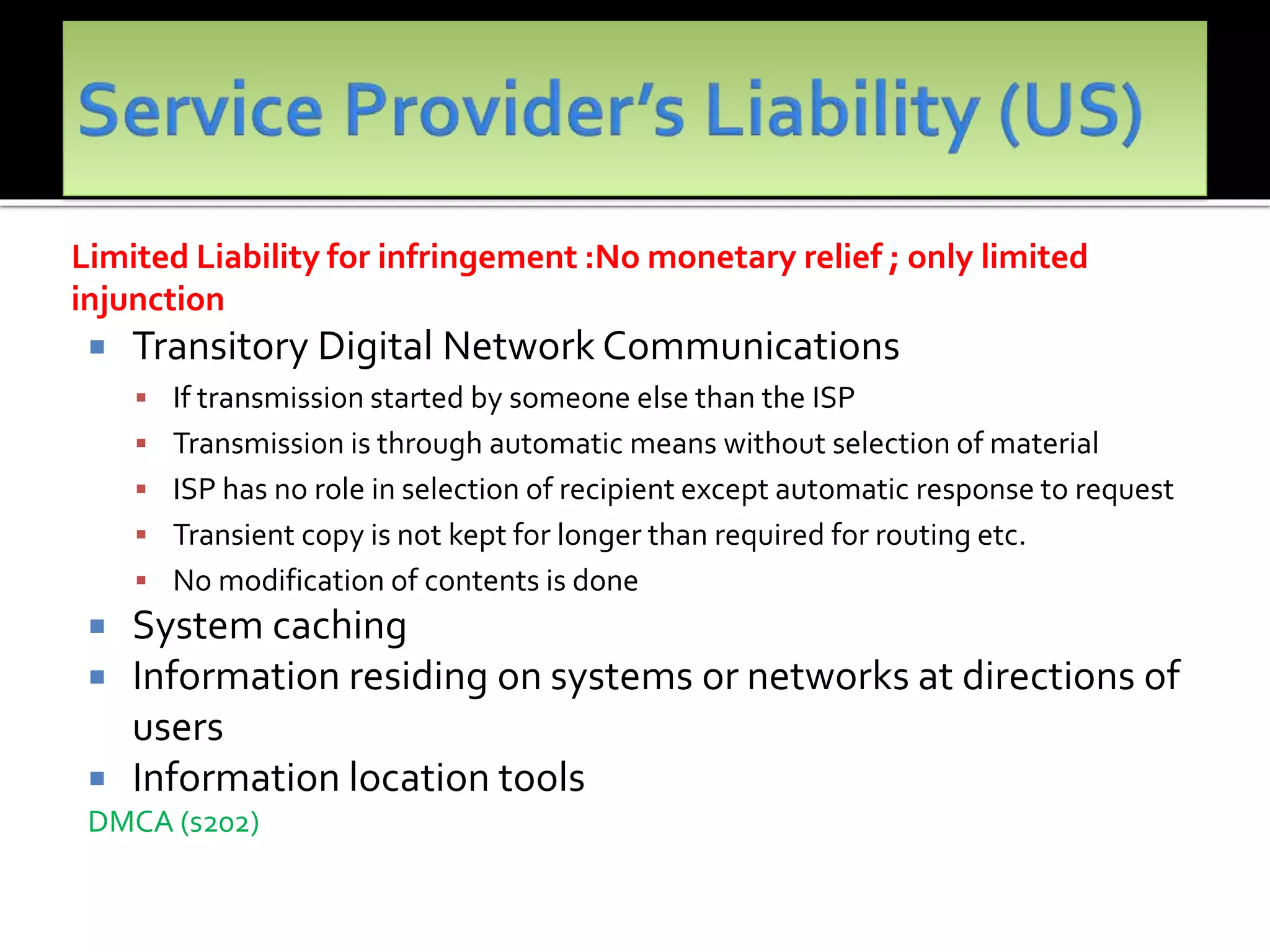
The document outlines the key topics to be covered in lectures on intellectual property rights (IPR) in the digital environment. The lectures will discuss 1) challenges posed by digital technologies to copyright, 2) complexities in applying copyright law digitally, 3) the extent to which existing copyright laws in India, UK and US have addressed these challenges, and 4) non-legislative solutions. It then provides an overview of relevant international treaties and domestic copyright laws. The rest of the document discusses in detail the impact of digital technologies on various aspects of copyright and analyses approaches taken in different jurisdictions.









![ ICA: Nothing expressly mentioned. Expression
IITA [Sec 4] Legal Recognition of Electronic Records:
Where any law provides that information or any other matter
shall be in writing or in the typewritten or printed form, then,
notwithstanding anything contained in such law, such
requirement shall be deemed to have been satisfied if such
information or matter is (a) rendered or made available in an
electronic form; and (b) accessible so as to be usable for a
subsequent reference
CDPA : Copyright does not subsist in a literary, dramatic or musical
work unless and until it is recorded, in writing or otherwise; …
US CA : in any tangible medium of expression, now known or later
developed, from which they can be perceived, reproduced, or
otherwise communicated, either directly or with the aid of a machine
or device](https://image.slidesharecdn.com/92ad348b-fcea-485b-b05f-145fcc5f2b2c-160414085005/75/Digital-Copyright-10-2048.jpg)












![IITA[Sec 67 C] Preservation and Retention of
information by intermediaries:
(1) Intermediary shall preserve and retain such
information as may be specified for such
duration and in such manner and format as the
Central Government may prescribe.
(2) Any intermediary who intentionally or
knowingly contravenes the provisions of sub
section (1) shall be punished with an
imprisonment for a term which may extend to
three years and shall also be liable to fine.](https://image.slidesharecdn.com/92ad348b-fcea-485b-b05f-145fcc5f2b2c-160414085005/75/Digital-Copyright-30-2048.jpg)