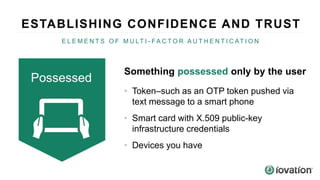
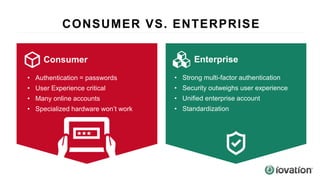
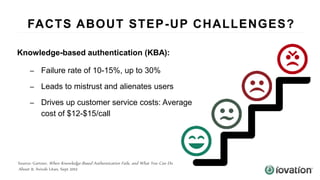
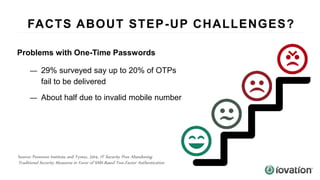
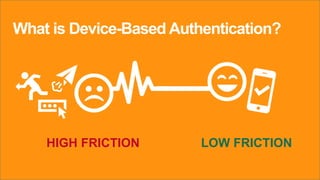
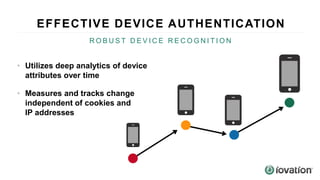
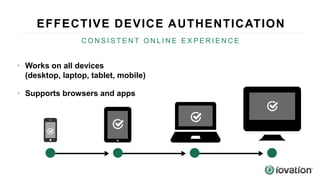
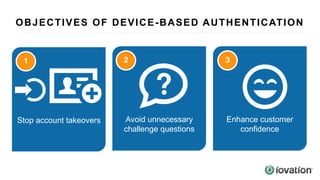
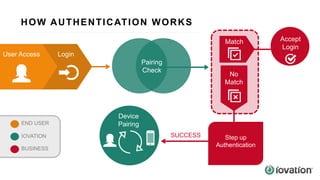
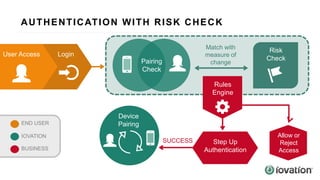
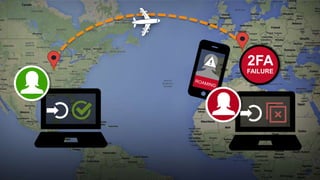
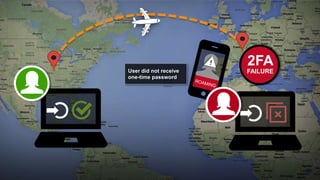
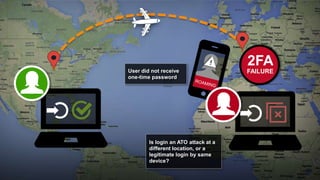
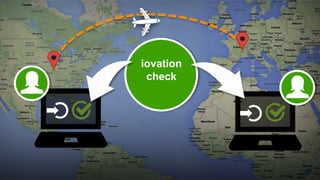
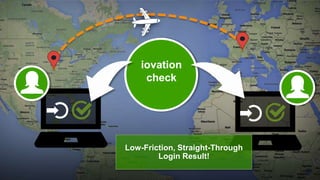
The document discusses the importance of device-based authentication as a low-friction solution to enhance security and user experience in both consumer and enterprise contexts. It highlights the limitations of traditional multi-factor authentication methods, such as knowledge-based authentication and one-time passwords, which can lead to user mistrust and increased costs. By pairing authorized devices with user accounts, device-based authentication aims to prevent account takeovers while providing a seamless login experience.