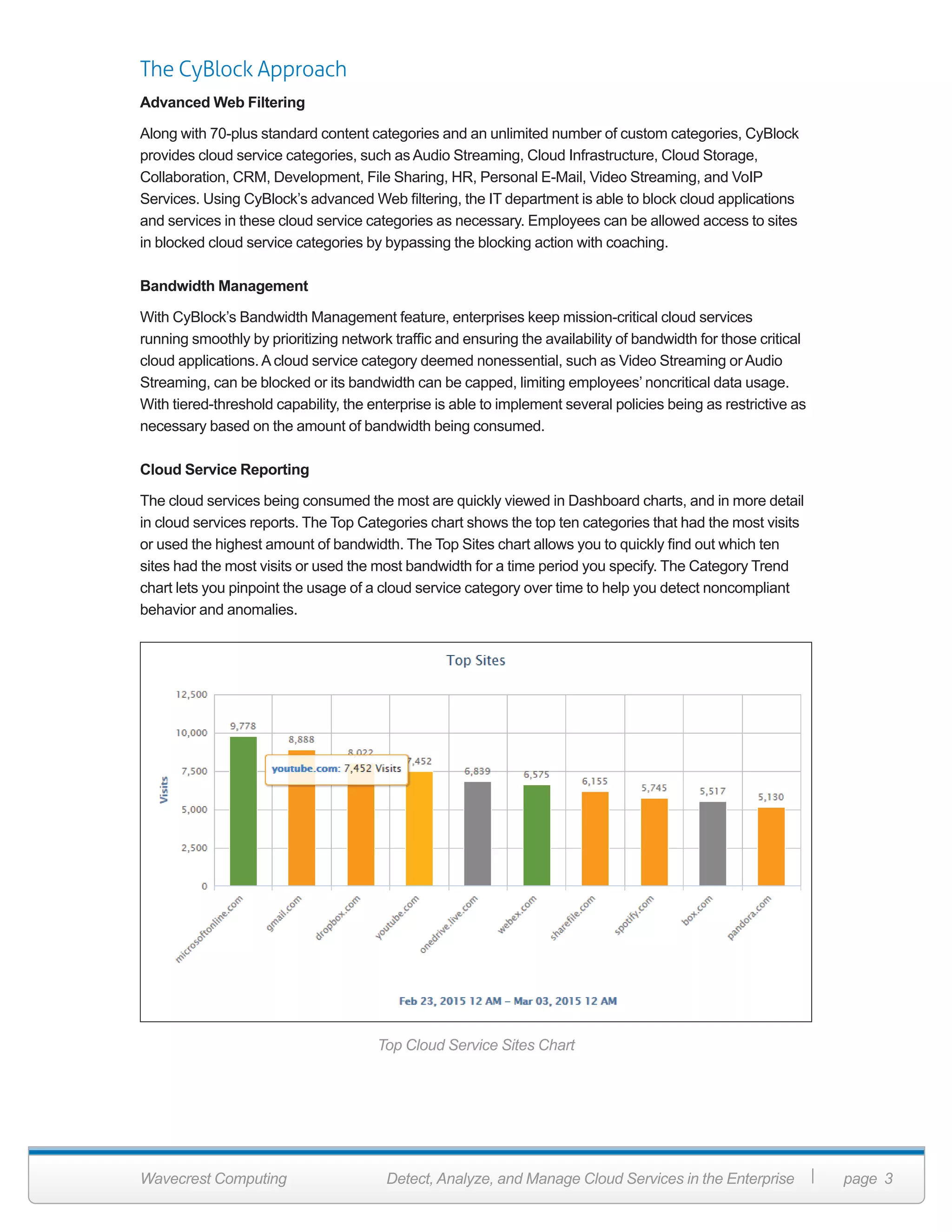
Wavecrest Computing's document outlines the importance of managing cloud services within enterprises as adoption grows, highlighting issues like shadow IT where employees deploy non-sanctioned applications. The Cyblock solution offers visibility, control, and security for cloud services usage by categorizing applications, enforcing policies, and providing detailed reporting capabilities. This enables organizations to mitigate risks, improve efficiency, and ensure compliance while securely adopting cloud technologies.