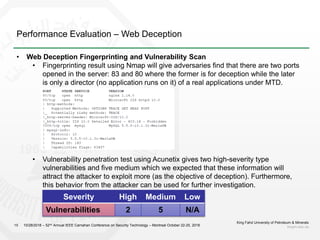
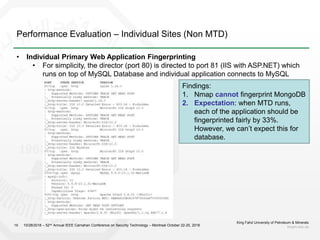
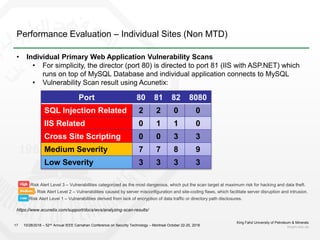
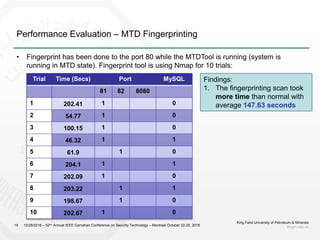
1) The document discusses challenges with static web application defenses and proposes combining web deception and moving target defense (MTD) techniques.
2) It outlines known web application risks and defense strategies like vulnerability scanning, secure development, and runtime protections. However, these are reactionary and do not provide long-term protection against adaptive attackers.
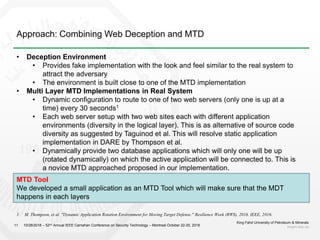
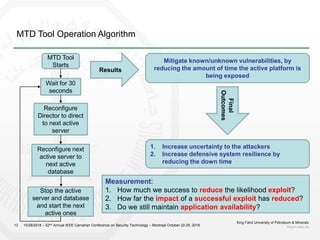
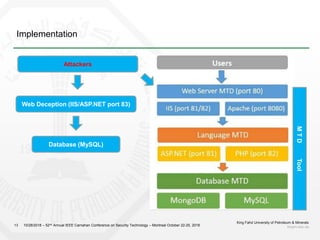
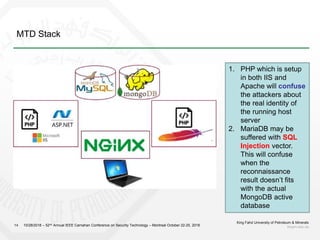
3) The proposal is to create a deception environment with fake implementations, along with implementing MTD at multiple layers (e.g. logical, storage, presentation) of the web application to increase complexity for attackers over time.






![References
King Fahd University of Petroleum & Minerals
kfupm.edu.sa21 10/28/2018 – 52nd Annual IEEE Carnahan Conference on Security Technology – Montreal October 22-25, 2018
[1] M. Taguinod, A. Doupe, Z. Zhao, and G. J. Ahn, “Toward a Moving Target Defense for Web Applications,”
Proc. - 2015 IEEE 16th Int. Conf. Inf. Reuse Integr. IRI 2015, pp. 510–517, 2015.
[2] A. Doupé, L. Cavedon, C. Kruegel, and G. Vigna, “Enemy of the State: A State-Aware Black-Box Vulnerability
Scanner.” 2012.
[3] A. Doupé, W. Cui, M. H. Jakubowski, M. Peinado, C. Kruegel, and G. Vigna, “deDacota: Toward Preventing
Server-side XSS via Automatic Code and Data Separation,” in Proceedings of the 2013 ACM SIGSAC Conference
on Computer & Communications Security, 2013, pp. 1205–1216.
[4] D. Evans, A. Nguyen-Tuong, and J. Knight, “Effectiveness of Moving Target Defenses,” in Moving Target
Defense: Creating Asymmetric Uncertainty for Cyber Threats, S. Jajodia, A. K. Ghosh, V. Swarup, C.Wang, and X.
S. Wang, Eds. New York, NY: Springer New York, 2011, pp. 29–48.
[5] C. De Faveri and A. Moreira, “A SPL Framework for Adaptive Deception-based Defense,” vol. 9, pp. 5542–
5551, 2018.
[6] V. E. Urias, W. M. S. Stout, and C. Loverro, “Computer network deception as a Moving Target Defense,” Proc. -
Int. Carnahan Conf. Secur. Technol., vol. 2015–Janua, 2016.
[7] X. Li and Y. Xue, “A survey on server-side approaches to securing web applications,” ACM Comput. Surv., vol.
46, no. 4, pp. 1–29, 2014.
[8] X. Han, N. Kheir, and D. Balzarotti, “Evaluation of Deception-Based Web Attacks Detection,” Proc. 2017
Work. Mov. Target Def. - MTD ’17, pp. 65–73, 2017.
[9] S. Jajodia, A. Ghosh, V. Swarup, C. Wamg, and X. Wang, Moving Target Defense. Springer, 2011.
[10] J. H. Jafarian, E. Al-Shaer, and Q. Duan. "Openflow random host mutation: transparent moving target defense
using software defined networking." Proceedings of the first workshop on Hot topics in software defined networks.
ACM, 2012.](https://image.slidesharecdn.com/deceptiontowardsmtd-181028181016/85/Deception-towards-Moving-Target-Defense-21-320.jpg)
![References
King Fahd University of Petroleum & Minerals
kfupm.edu.sa22 10/28/2018 – 52nd Annual IEEE Carnahan Conference on Security Technology – Montreal October 22-25, 2018
[11] D. Evans, A. Nguyen-Tuong, and J. Knight, Effectiveness of Moving Target Defenses. Springer, 2011, pp. 29–
48.
[12] R. Zhuang1, S. Zhang1, S. A. DeLoach1, X. Ou1, and A. Singhal2,“Simulation-based Approaches to Studying
Effectiveness of Moving-Target Network Defense,” in National Symposium on Moving Target Research, June
2012.
[13] M. Almeshekah, M. Atallah, and E. Spafford, “The case of using negative (deceiving) information in data
protection,” Proc. 2014 CERIAS '14 Proceedings of the 15th Annual Information Security Symposium, Article no.
45, 2014.
[14] M. Thompson, et al. "Dynamic Application Rotation Environment for Moving Target Defense." Resilience
Week (RWS), 2016. IEEE, 2016.](https://image.slidesharecdn.com/deceptiontowardsmtd-181028181016/85/Deception-towards-Moving-Target-Defense-22-320.jpg)
