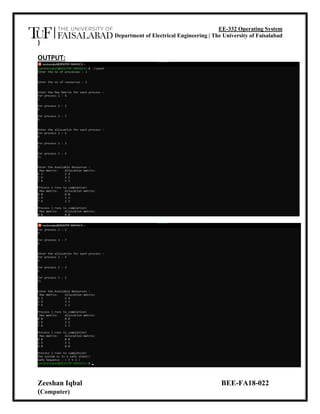
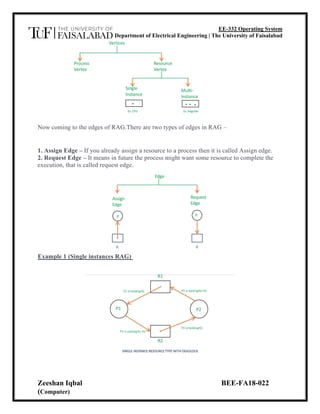
The document describes an experiment to simulate an algorithm for deadlock prevention in an operating system. It defines deadlock as when processes are blocked because each holds a resource needed by another. It explains resource allocation graphs (RAGs) that represent processes, resources, and their relationships. The algorithm aims to prevent deadlock by ordering resources and only allowing requests in increasing order to avoid cycles in the RAG. The program simulates this approach by tracking available resources, allocation, and need matrices to determine a safe process execution order or report an unsafe state.
![EE-332 Operating System
Department of Electrical Engineering | The University of Faisalabad
Zeeshan Iqbal BEE-FA18-022
(Computer)
Example 2 (Multi-instances RAG) –
Algorithm for Deadlock prevention:
• Start the program
• Attacking Mutex condition: never grant exclusive access. But this may not be possible
for several resources.
• Attacking preemption: not something you want to do.
• Attacking hold and wait condition: make a process hold at the most 1 resource
• At a time. Make all the requests at the beginning. Nothing policy. If you feel, retry.
• Attacking circular wait: Order all the resources. Make sure that the requests are issued
in the Correct order so that there are no cycles present in the resource graph. Resources
numbered 1 ... n.
• Resources can be requested only in increasing
• Order. i.e. you cannot request a resource whose no is less than any you may be holding.
• Stop the program
PROGRAM: (SIMULATE ALGORITHM FOR DEADLOCK PREVENTION)
#include <stdio.h>
#include <stdlib.h>
int main()
{
int Max[10][10], need[10][10], alloc[10][10], avail[10], completed[10], safeSequence[10];
int p, r, i, j, process, count;
count = 0;
printf("Enter the no of processes : ");
scanf("%d", &p);
for(i = 0; i< p; i++)
completed[i] = 0;](https://image.slidesharecdn.com/lab11-210227054856/85/Deadlock-Prevention-in-Operating-System-3-320.jpg)
![EE-332 Operating System
Department of Electrical Engineering | The University of Faisalabad
Zeeshan Iqbal BEE-FA18-022
(Computer)
printf("nnEnter the no of resources : ");
scanf("%d", &r);
printf("nnEnter the Max Matrix for each process : ");
for(i = 0; i < p; i++)
{
printf("nFor process %d : ", i + 1);
for(j = 0; j < r; j++)
scanf("%d", &Max[i][j]);
}
printf("nnEnter the allocation for each process : ");
for(i = 0; i < p; i++)
{
printf("nFor process %d : ",i + 1);
for(j = 0; j < r; j++)
scanf("%d", &alloc[i][j]);
}
printf("nnEnter the Available Resources : ");
for(i = 0; i < r; i++)
scanf("%d", &avail[i]);
for(i = 0; i < p; i++)
for(j = 0; j < r; j++)
need[i][j] = Max[i][j] - alloc[i][j];
do
{
printf("n Max matrix:tAllocation matrix:n");
for(i = 0; i < p; i++)
{
for( j = 0; j < r; j++)
printf("%d ", Max[i][j]);
printf("tt");
for( j = 0; j < r; j++)
printf("%d ", alloc[i][j]);
printf("n");
}
process = -1;](https://image.slidesharecdn.com/lab11-210227054856/85/Deadlock-Prevention-in-Operating-System-4-320.jpg)
![EE-332 Operating System
Department of Electrical Engineering | The University of Faisalabad
Zeeshan Iqbal BEE-FA18-022
(Computer)
for(i = 0; i < p; i++)
{
if(completed[i] == 0)//if not completed
{
process = i ;
for(j = 0; j < r; j++)
{
if(avail[j] < need[i][j])
{
process = -1;
break;
}
}
}
if(process != -1)
break;
}
if(process != -1)
{
printf("nProcess %d runs to completion!", process + 1);
safeSequence[count] = process + 1;
count++;
for(j = 0; j < r; j++)
{
avail[j] += alloc[process][j];
alloc[process][j] = 0;
Max[process][j] = 0;
completed[process] = 1;
}
}
}
while(count != p && process != -1);
if(count == p)
{
printf("nThe system is in a safe state!!n");
printf("Safe Sequence : < ");
for( i = 0; i < p; i++)
printf("%d ", safeSequence[i]);
printf(">n");
}
else
printf("nThe system is in an unsafe state!!");](https://image.slidesharecdn.com/lab11-210227054856/85/Deadlock-Prevention-in-Operating-System-5-320.jpg)