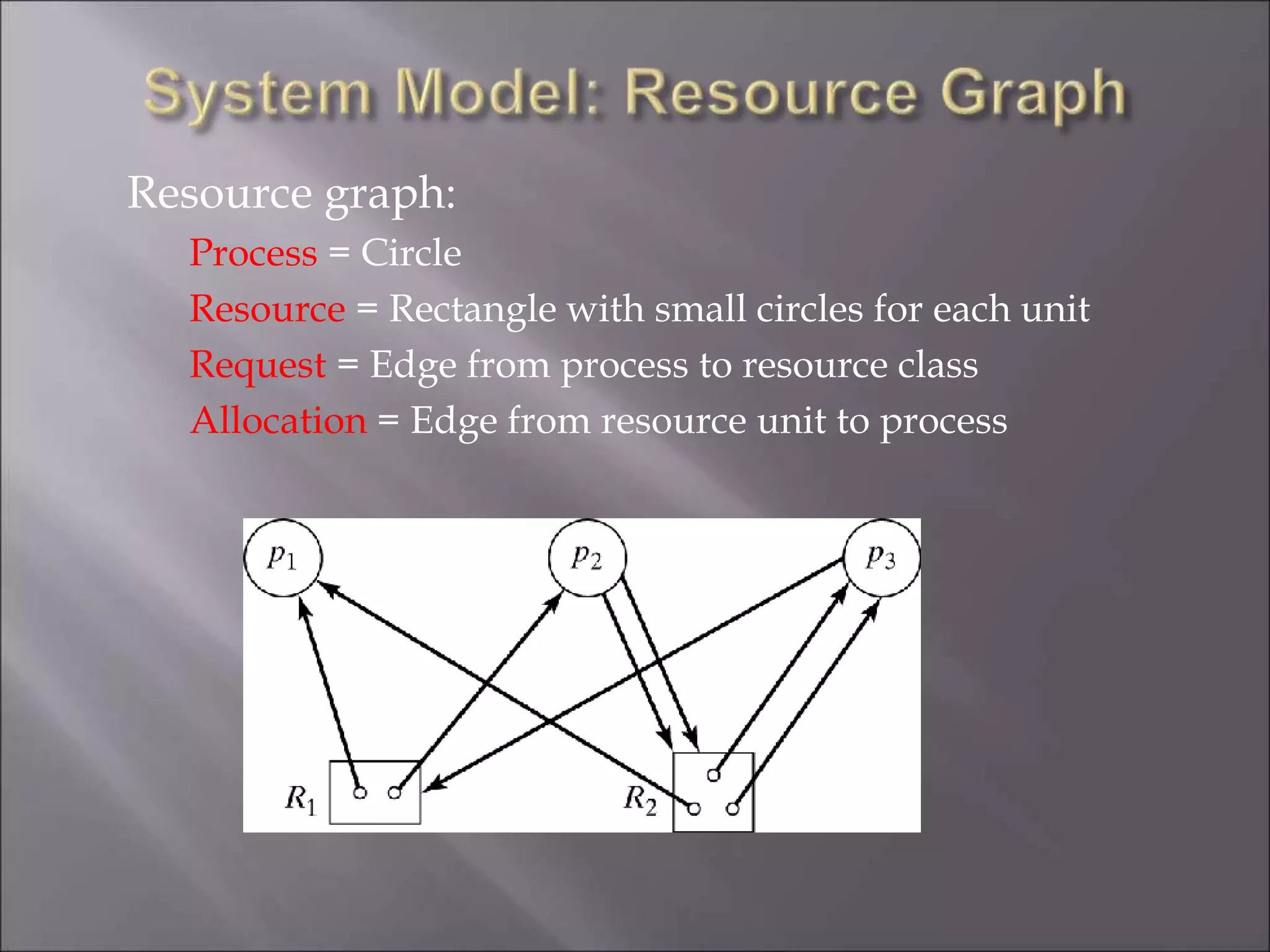
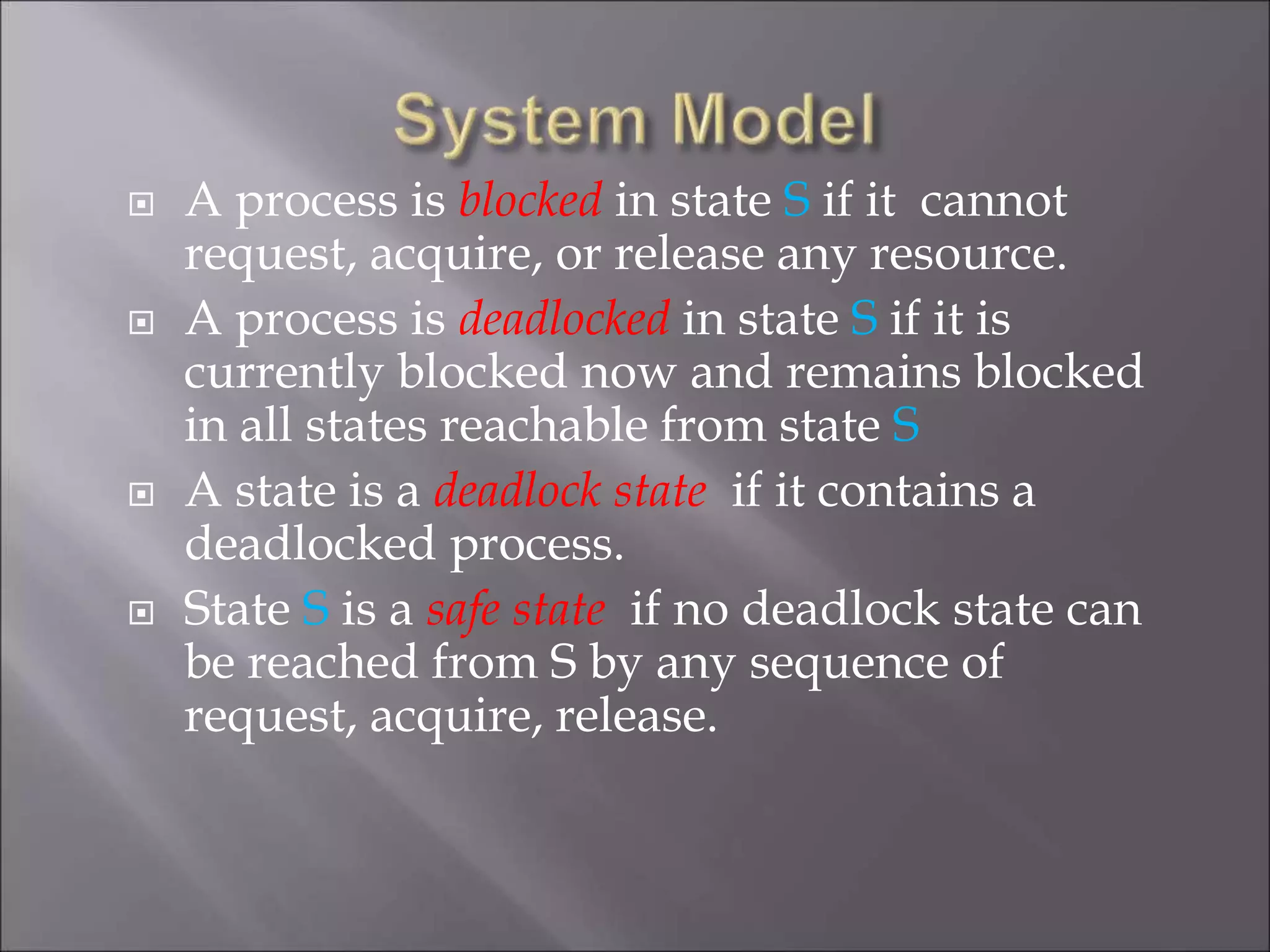
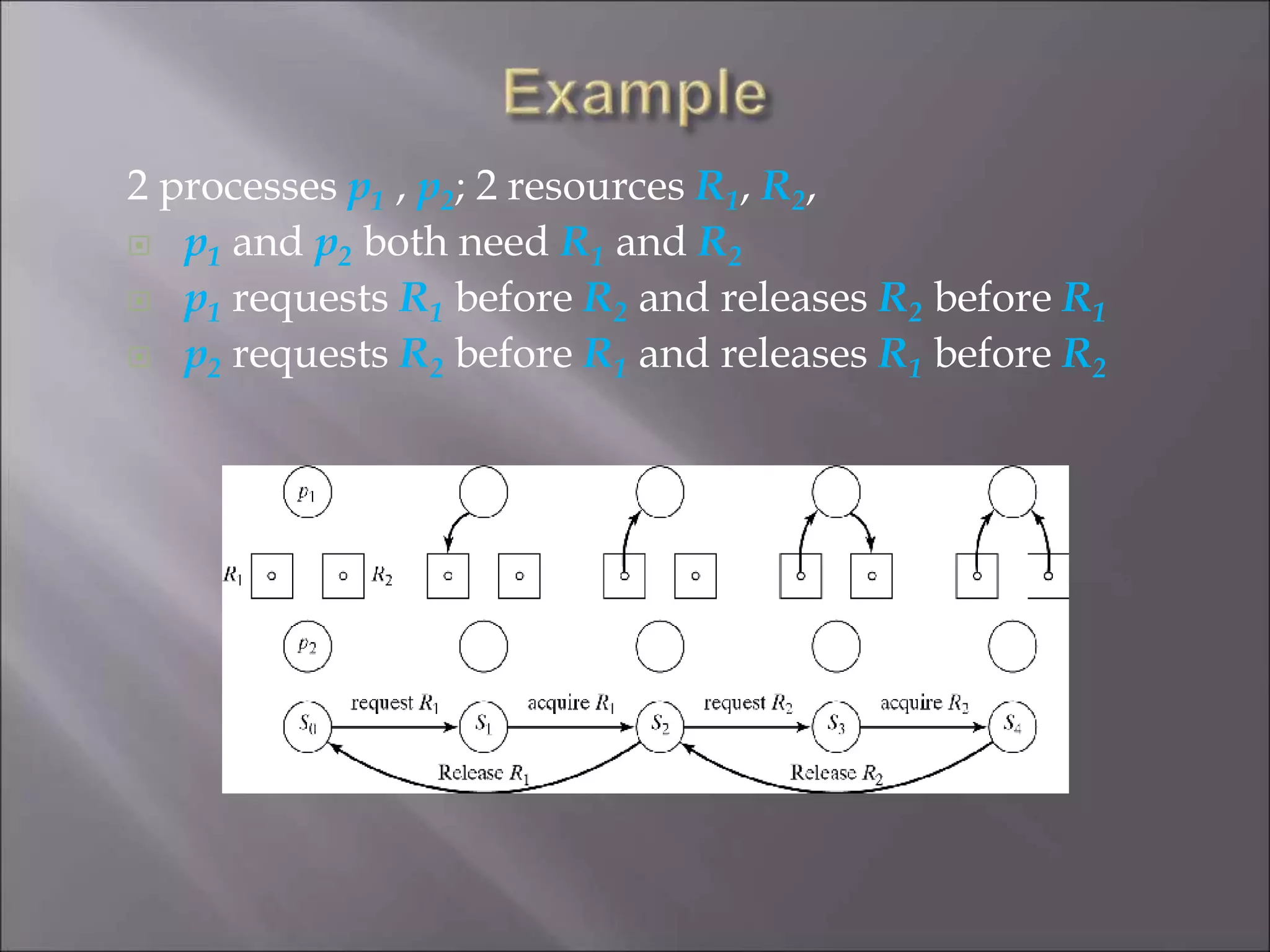
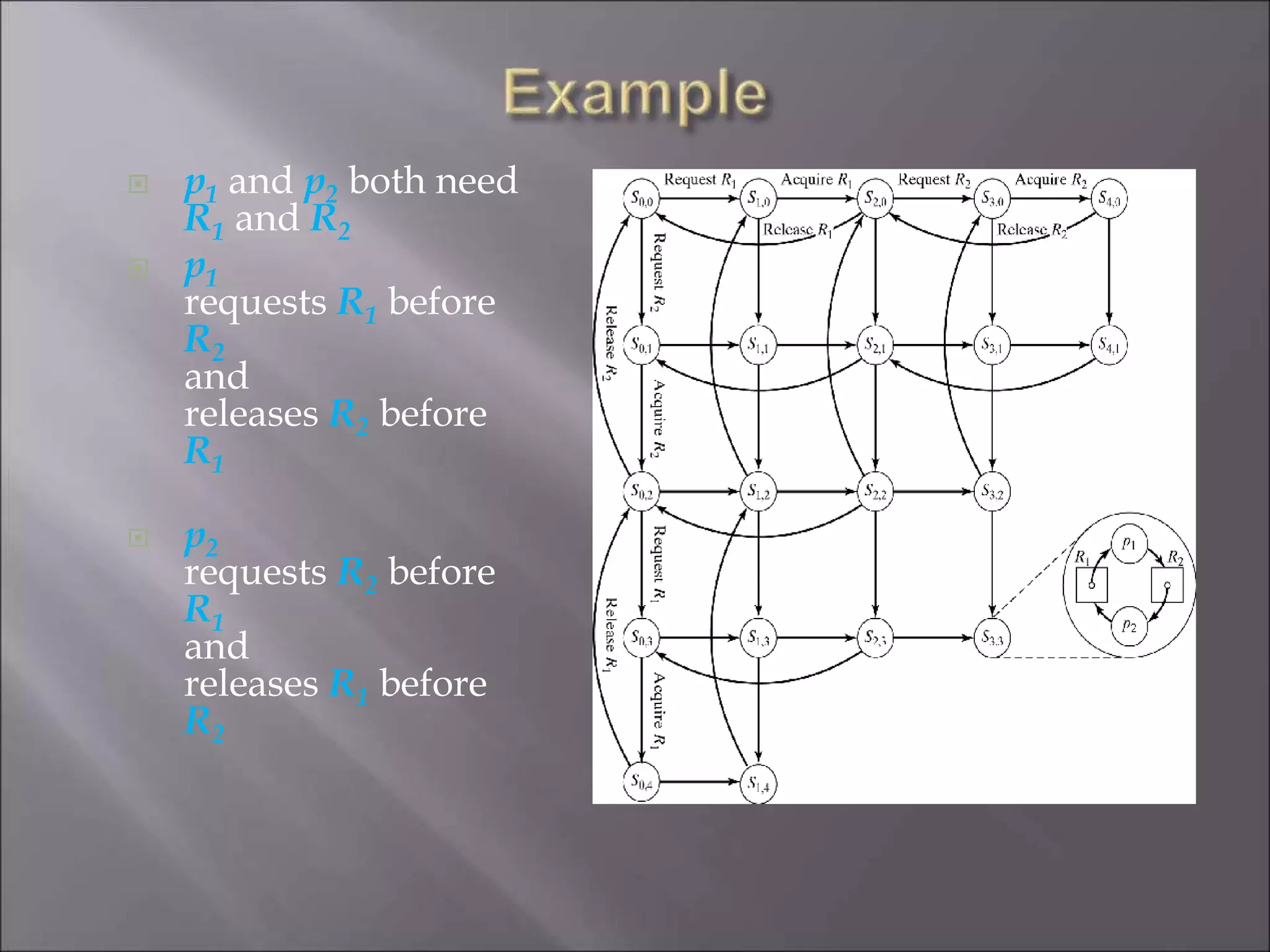
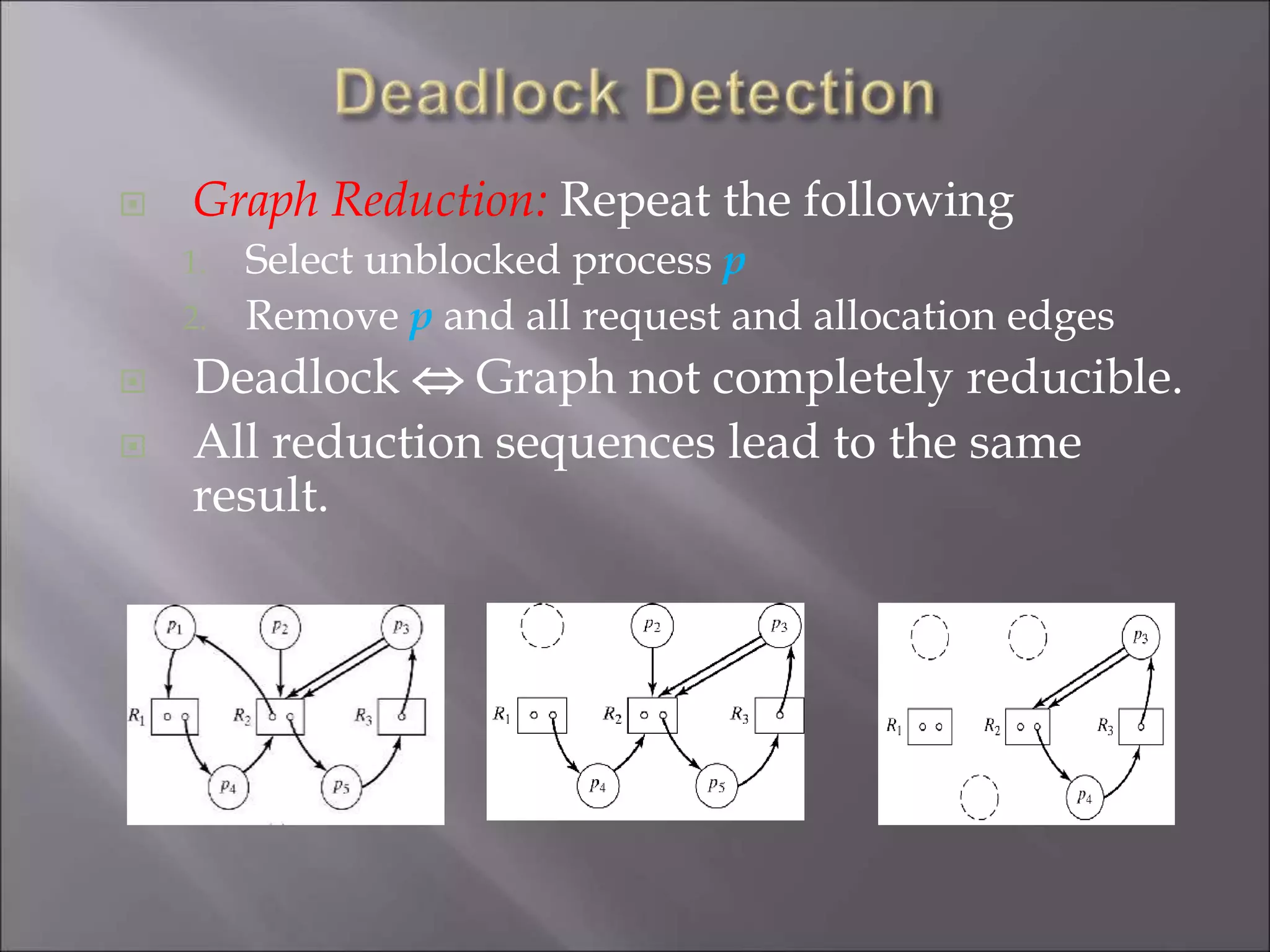
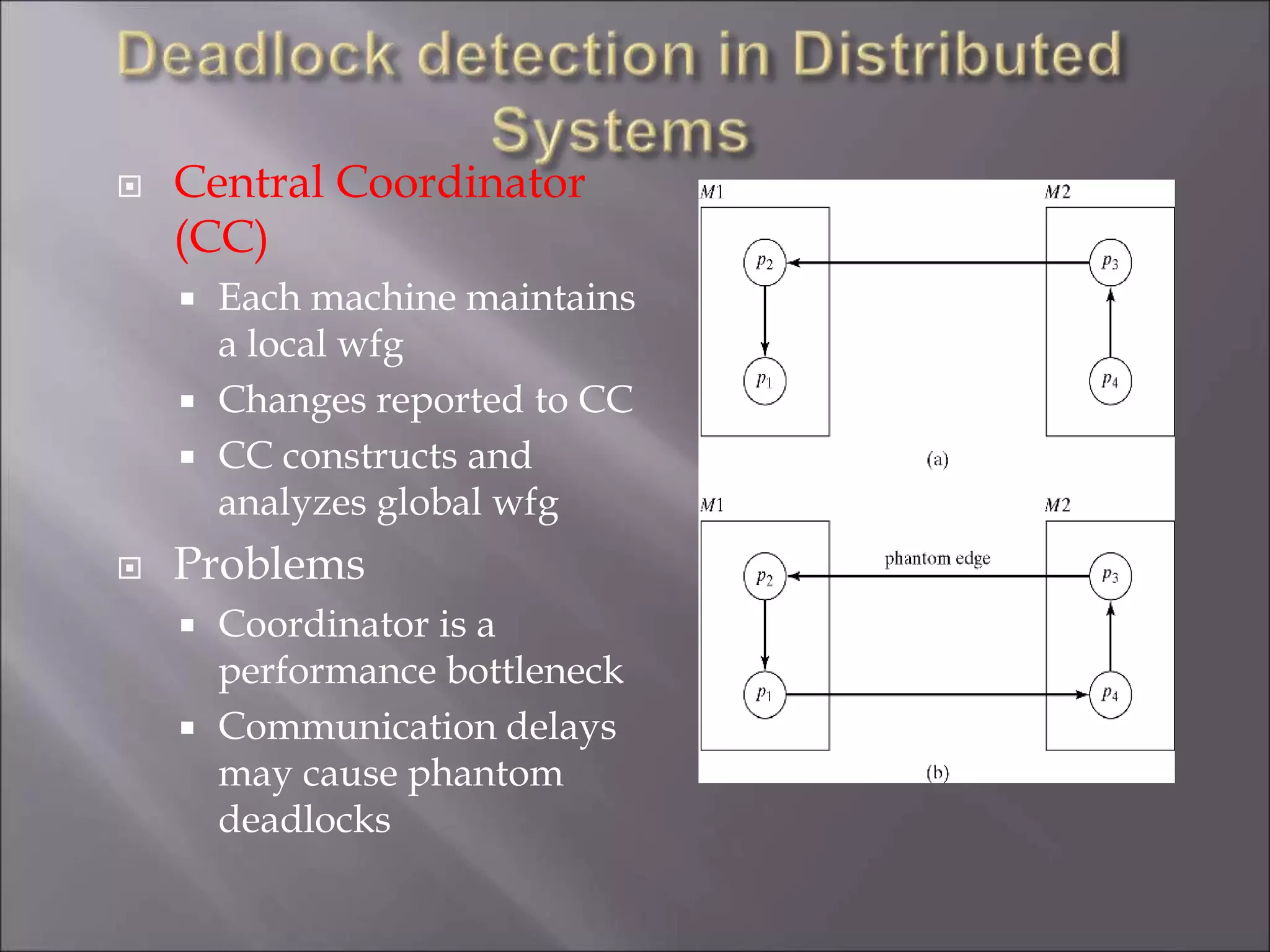
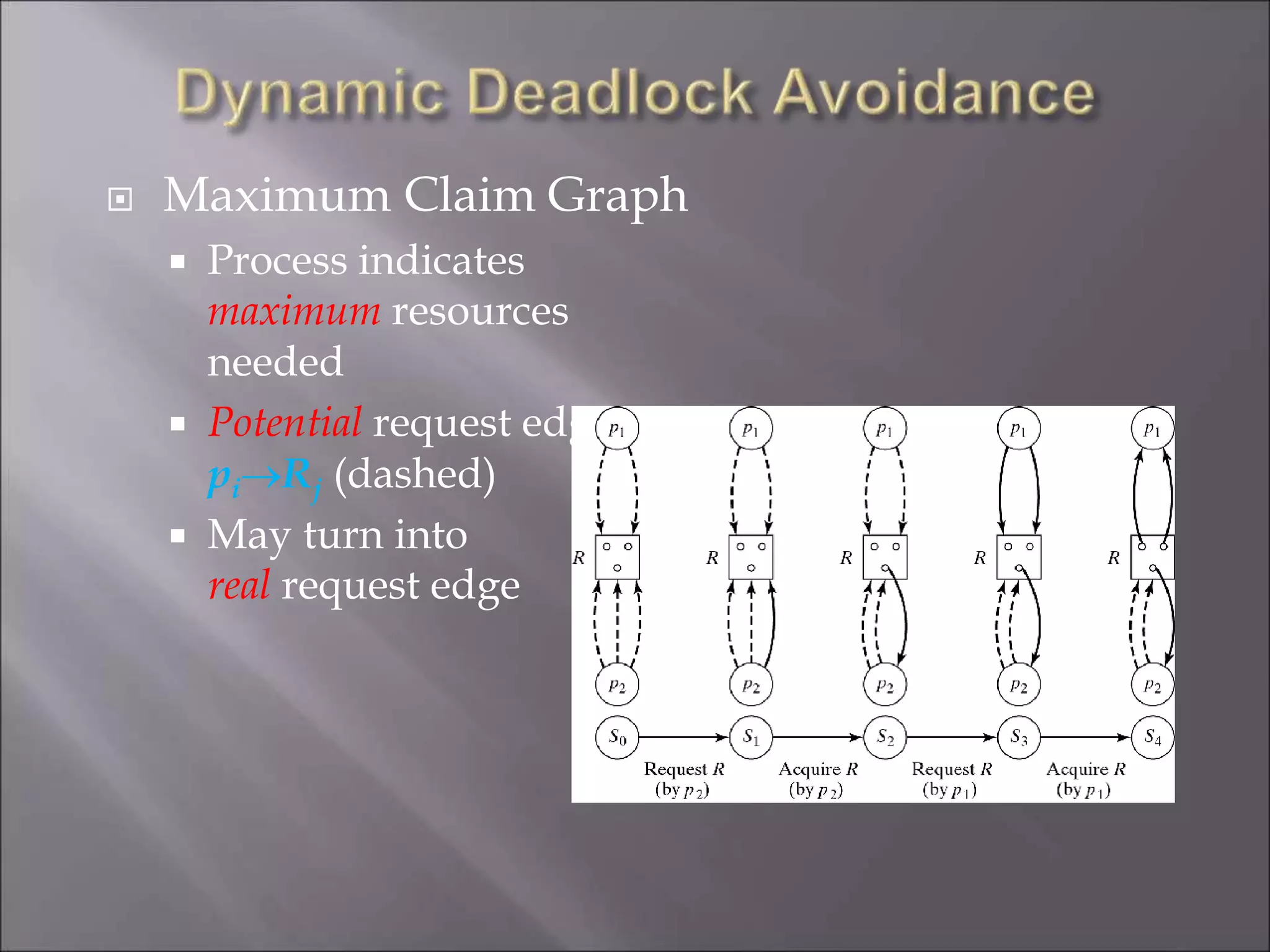
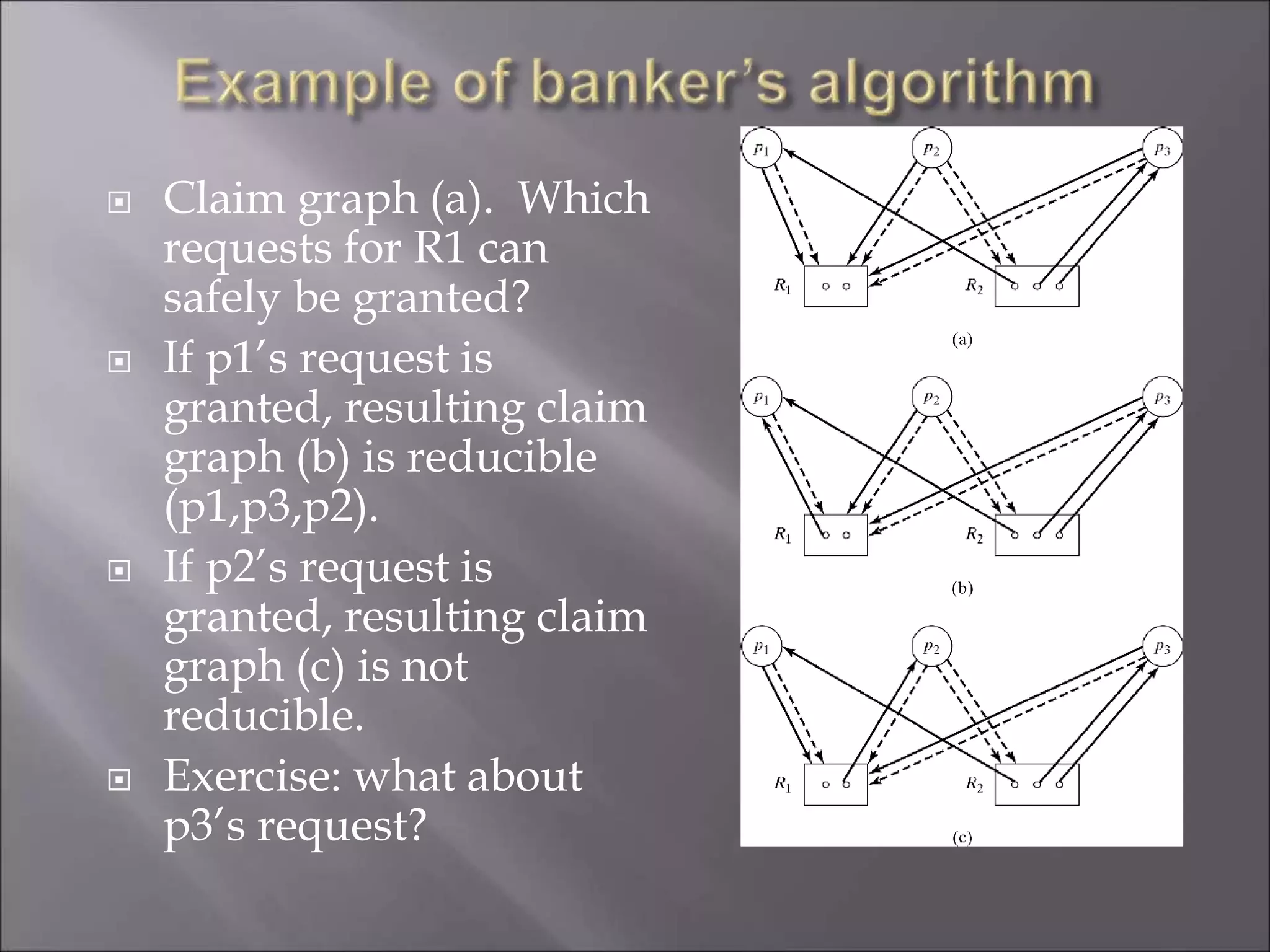
The document discusses deadlocks in computing systems. It defines deadlocks and related concepts like livelock and starvation. It presents various approaches to deal with deadlocks including detection and recovery, avoidance through runtime checks, and prevention by restricting resource requests. Graph-based algorithms are described for detecting and preventing deadlocks by analyzing resource allocation graphs. The Banker's algorithm is introduced as a static prevention method. Finally, it discusses ways to eliminate the conditions required for deadlocks, like mutual exclusion, hold-and-wait, and circular wait.