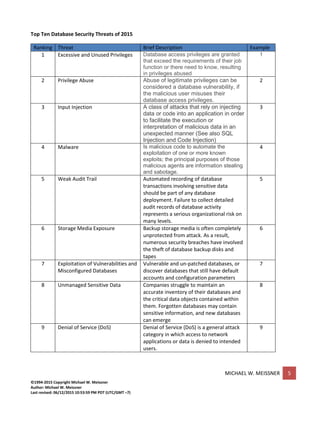
The document discusses database security threats and provides details about the top 10 threats in 2015 as identified by Imperva. It includes examples for each threat type and mitigation strategies. The top threats are: 1) Excessive and unused privileges 2) Privilege abuse 3) Input injection 4) Malware 5) Weak audit trail 6) Storage media exposure 7) Exploitation of vulnerabilities and misconfigured databases 8) Unmanaged sensitive data 9) Denial of service 10) Limited security expertise. The editor Michael Meissner is also introduced with his background and experience in cyber security.