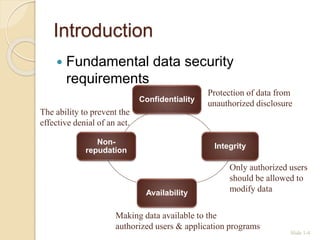
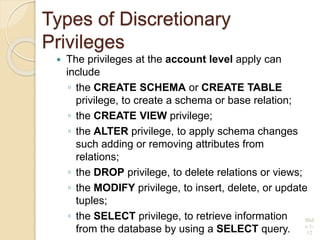
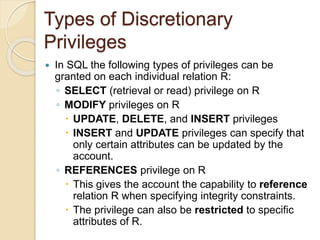
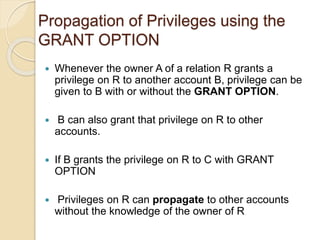
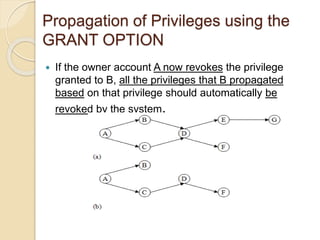
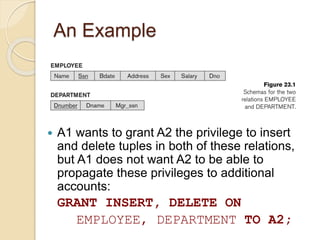
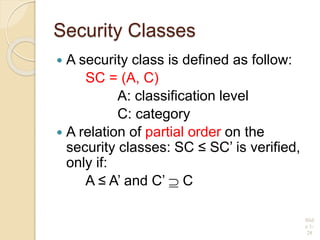
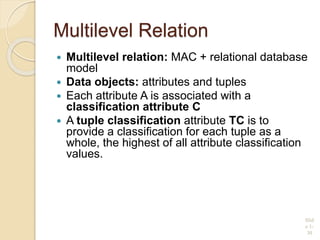
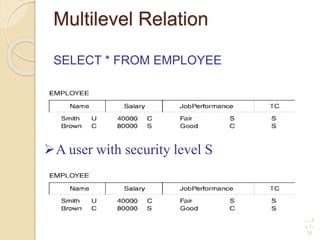
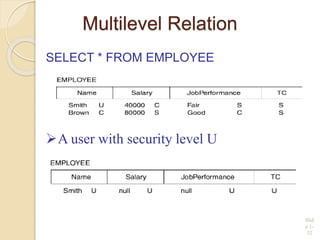
This document discusses database security and various techniques used to protect databases. It covers four main countermeasures: access control, inference control, flow control, and encryption. Access control includes discretionary access control (DAC) using privileges and mandatory access control (MAC) using security levels. DAC is enforced through granting and revoking SQL privileges at both the account and relation levels. MAC enforces the simple security and star properties based on subject and object security classes. The document also discusses data encryption techniques like DES and AES, as well as symmetric and public key encryption algorithms. The database administrator plays a key role in managing security and assigning privileges.