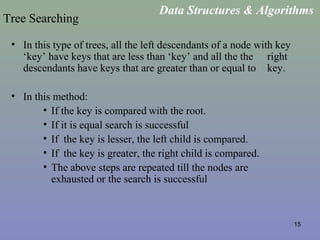
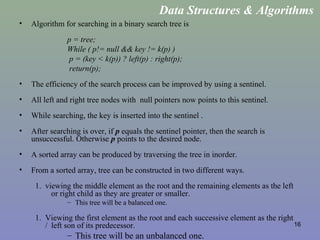
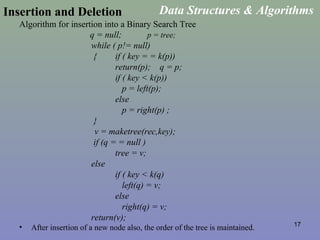
This document provides an overview of different searching techniques including sequential search, binary search, tree searching using binary search trees, hashing techniques, and general search trees. It defines key search terminology and summarizes algorithms for common search operations like search, insertion and deletion in various data structures that support efficient searching like binary search trees, B-trees, and hash tables. Examples are provided to illustrate search techniques and how they work.


![3
Searching
• Searching is a technique where the memory is scanned for the required
data
• Easiest way to search from a table is to perform a sequential search,
– i.e. a search through all the elements in the table or list.
• This can be done by :
For (int i = 0; i<n; i++)
If (x == a[i] )
break;
Data Structures & Algorithms](https://image.slidesharecdn.com/session8-180119052138/85/Data-Structures-8-3-320.jpg)




![9
l = 1 ; u = n; done = ‘f’
while ((l<=u) && (done=='f'))
{ m=(l+u)/2;
if (k>f[m])
l=m+1;
if (k<f[m])
u=m-1;
if (k==f[m])
{ i=m;
done='t';
}
}
if (done=='f')
printf("n KEY %d IS NOT FOUND IN THE FILE",k);
else
printf("n KEY %d IS FOUND IN POSITION %d",k,i);
Data Structures & AlgorithmsAlgorithm for Binary Search
• Binary search gives a complexity of O(log n) .
• This is much faster than the linear search](https://image.slidesharecdn.com/session8-180119052138/85/Data-Structures-8-9-320.jpg)


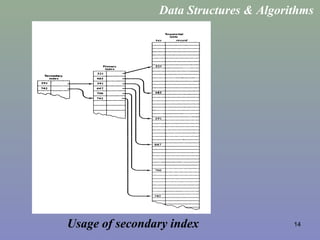


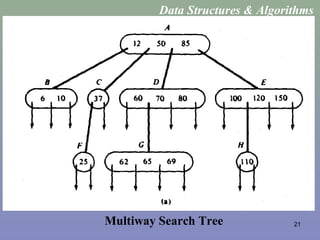
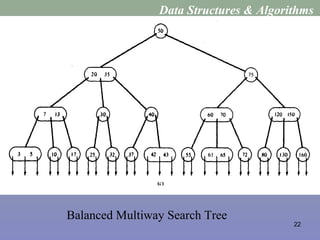
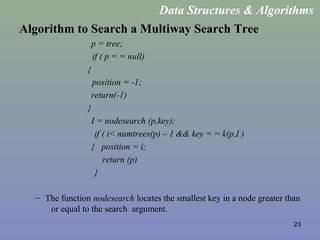


![27
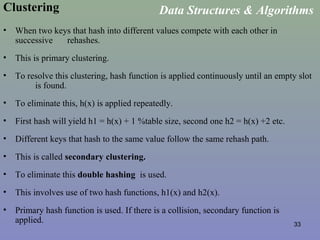
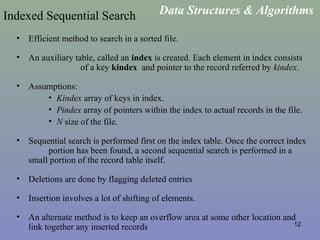
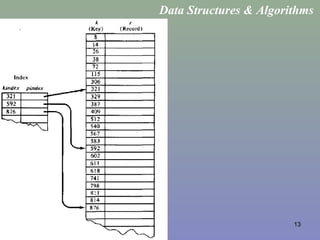
Hash Tables / Direct Access Tables
• A collection of n elements with unique keys, are stored in a direct access
table T[m].
• The hash function is f(x) = x.
• For a key k, if we access T[k]
• if it contains an element, return it
• if it doesn’t then return a null.
• Thus the complexity of this will be O(1).
• The keys should be unique
• The range of the keys should be bounded.
Data Structures & Algorithms](https://image.slidesharecdn.com/session8-180119052138/85/Data-Structures-8-27-320.jpg)