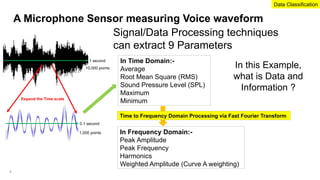
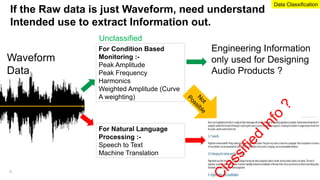
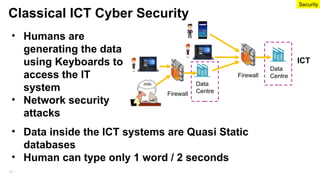
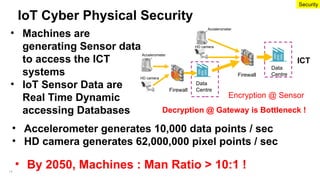
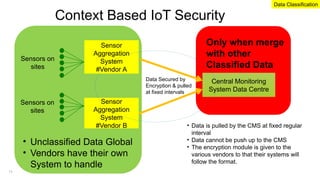
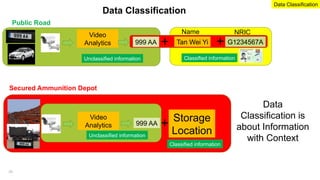
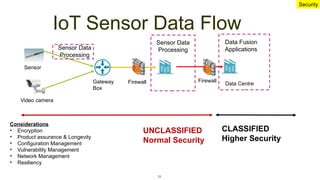
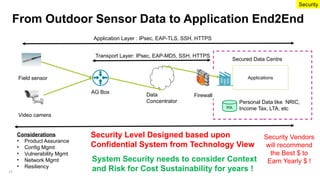
The document emphasizes the critical importance of securing classified information to protect national security and maintain public confidence in the Singapore government. It discusses data classification frameworks, distinguishing between structured and unstructured data, and highlights the need for controlled access to sensitive data through methods like unidirectional gateways and tiered security levels. Ultimately, it advocates for a risk-based security approach that balances security, costs, and functionalities by categorizing information into different tiers based on sensitivity.