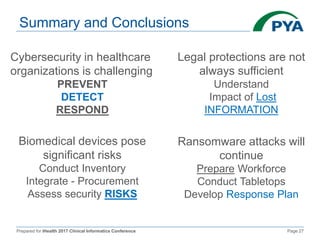
The document presents a comprehensive overview of cybersecurity challenges within healthcare organizations, highlighting the frequency of cyber attacks, particularly ransomware, and the insufficient preparedness of these organizations. It discusses legal considerations, especially the limitations of HIPAA in protecting non-PHI information and the need for robust security measures, user awareness, and institutional preparedness. Recommendations include developing layered defense strategies, ensuring timely updates of security protocols, and fostering a culture of awareness among staff to enhance overall cybersecurity resilience.





![Prepared for iHealth 2017 Clinical Informatics Conference Page 6
An Underlying Lack of Preparedness for a
New World Filled with Threats (cont.)
Challenges include (cont.):
Insufficient staffing of information security (IS) departments
Insufficient training, preparedness, and expertise of those
assigned to manage cybersecurity and data security in PCOs
A lack of data security strategic planning and execution of
strategic plans
A rapidly surging threat that is exposing more hospitals, medical
groups, and health systems to ransomware and other malware
and hacking
[M. Hagland, With The Ransomware Crisis, The Landscape of Data Security Shifts in Healthcare, Healthcare Informatics Special Report
Ransomeware Crisis, Jun. 2016, http://www.healthcare-informatics.com/]](https://image.slidesharecdn.com/dataandnetworksecurity-whatyouneedtoknowkocb-170511145832/85/Data-and-Network-Security-What-You-Need-to-Know-7-320.jpg)




![Prepared for iHealth 2017 Clinical Informatics Conference Page 12
HIPAA Security Rule (cont.)
Physical safeguards include:
Physical measures, policies, and procedures to safeguard the
CE or BA's electronic information systems
Facility access controls, workstation security, and device and
media controls
Technical safeguards include:
Access controls, audit controls, integrity, person or entity
authentication, and transmission security
[Examining Oversight of the Privacy & Security of Health Data Collected by Entities Not Regulated by HIPAA. U.S. Department of Health
and Human Services, https://www.healthit.gov/sites/default/files/non-covered_entities_report_june_17_2016.pdf]](https://image.slidesharecdn.com/dataandnetworksecurity-whatyouneedtoknowkocb-170511145832/85/Data-and-Network-Security-What-You-Need-to-Know-13-320.jpg)
![Prepared for iHealth 2017 Clinical Informatics Conference Page 13
HIPAA Security Rule (cont.)
Requires implementation of security measures that can
help prevent the introduction of malware, like
ransomware, including:
Implementing a security management process
Implementing procedures to guard against and detect malicious
software
Training users on malicious software protection
Implementing access controls
[FACT SHEET: Ransomware and HIPAA, http://www.hhs.gov/sites/default/files/RansomwareFactSheet.pdf]](https://image.slidesharecdn.com/dataandnetworksecurity-whatyouneedtoknowkocb-170511145832/85/Data-and-Network-Security-What-You-Need-to-Know-14-320.jpg)

![Prepared for iHealth 2017 Clinical Informatics Conference Page 15
HIPAA Security Rule (cont.)
Robust security incident procedures include:
Eradicating the instances of ransomware and mitigating or
remediating vulnerabilities that permitted the ransomware attack
and propagation
Recovering from the ransomware attack by restoring data lost
during the attack and returning to "business as usual" operations
Conducting post-incident activities, and incorporating any
lessons learned into the overall security management process of
the entity to improve incident response effectiveness for the
future of security incidents
[FACT SHEET: Ransomware and HIPAA, http://www.hhs.gov/sites/default/files/RansomwareFactSheet.pdf]](https://image.slidesharecdn.com/dataandnetworksecurity-whatyouneedtoknowkocb-170511145832/85/Data-and-Network-Security-What-You-Need-to-Know-16-320.jpg)
![Prepared for iHealth 2017 Clinical Informatics Conference Page 17
HIPAA Security Rule (cont.)
Is there a low probability that the PHI has been
compromised?
Four factor test:
1. The nature and extent of the PHI involved, including the
types of identifiers and the likelihood of re-identification
2. The unauthorized person who used the PHI or to whom the
disclosure was made
3. Whether the PHI was actually acquired or viewed
4. The extent to which the risk to the PHI has been mitigated
There should be a thorough and accurate evaluation of
all the evidence
[FACT SHEET: Ransomware and HIPAA, http://www.hhs.gov/sites/default/files/RansomwareFactSheet.pdf]](https://image.slidesharecdn.com/dataandnetworksecurity-whatyouneedtoknowkocb-170511145832/85/Data-and-Network-Security-What-You-Need-to-Know-18-320.jpg)