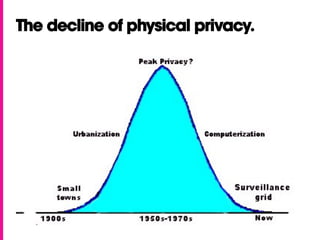
The document discusses the emergence and components of the "darknet", which refers to technologies that allow for anonymous use of the internet by avoiding personal identification. It outlines various darknet technologies like Tor, VPNs, encryption tools, cryptocurrencies and secure hardware. It also discusses how the darknet is used for both legal and illegal purposes, and why some people choose to use it given declining personal privacy elsewhere. Finally, it explores how darknet capabilities may continue to evolve and how adoption of such technologies could help defend critical institutions and democratic processes by enabling secure and anonymous communications.