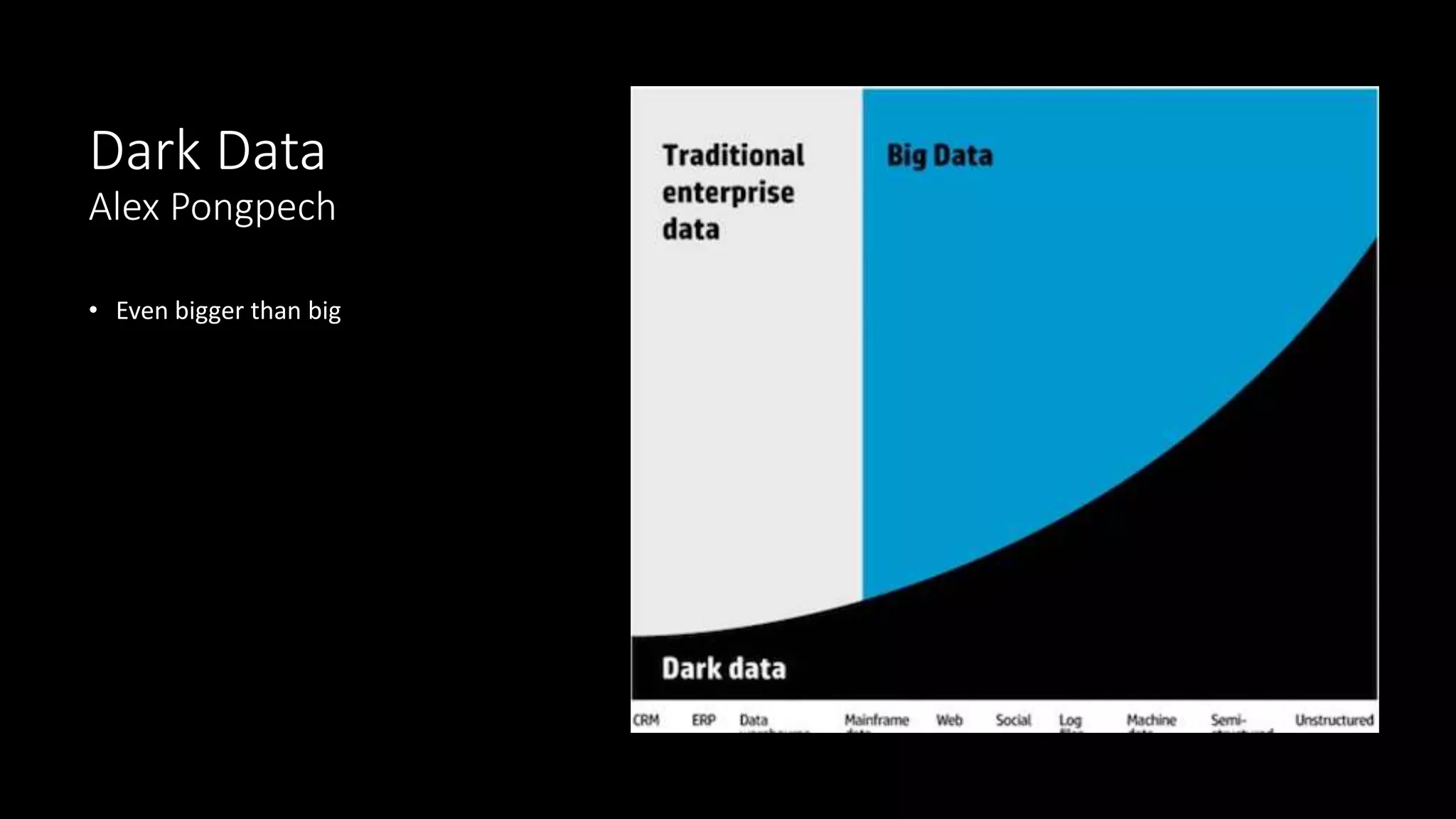
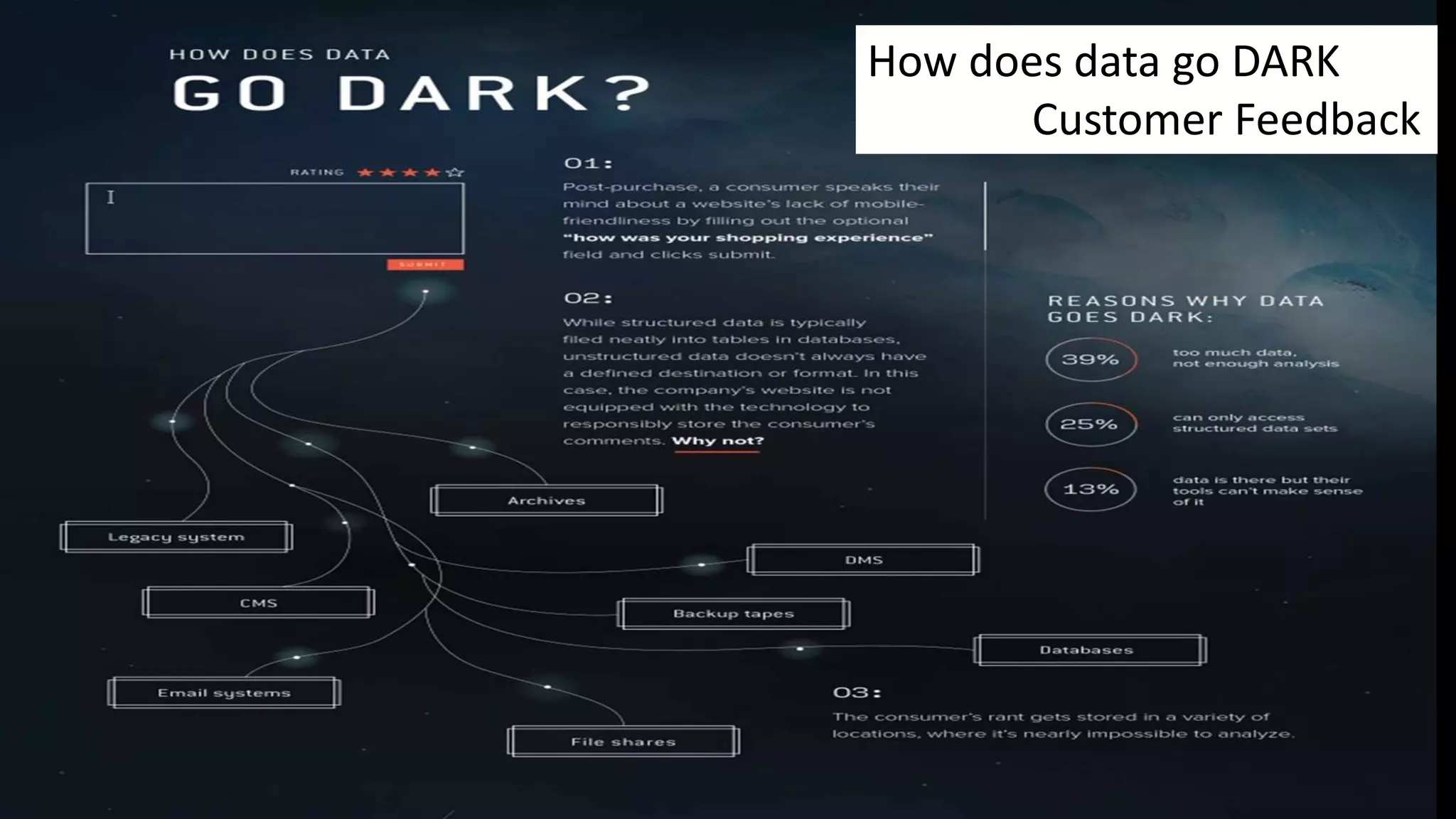
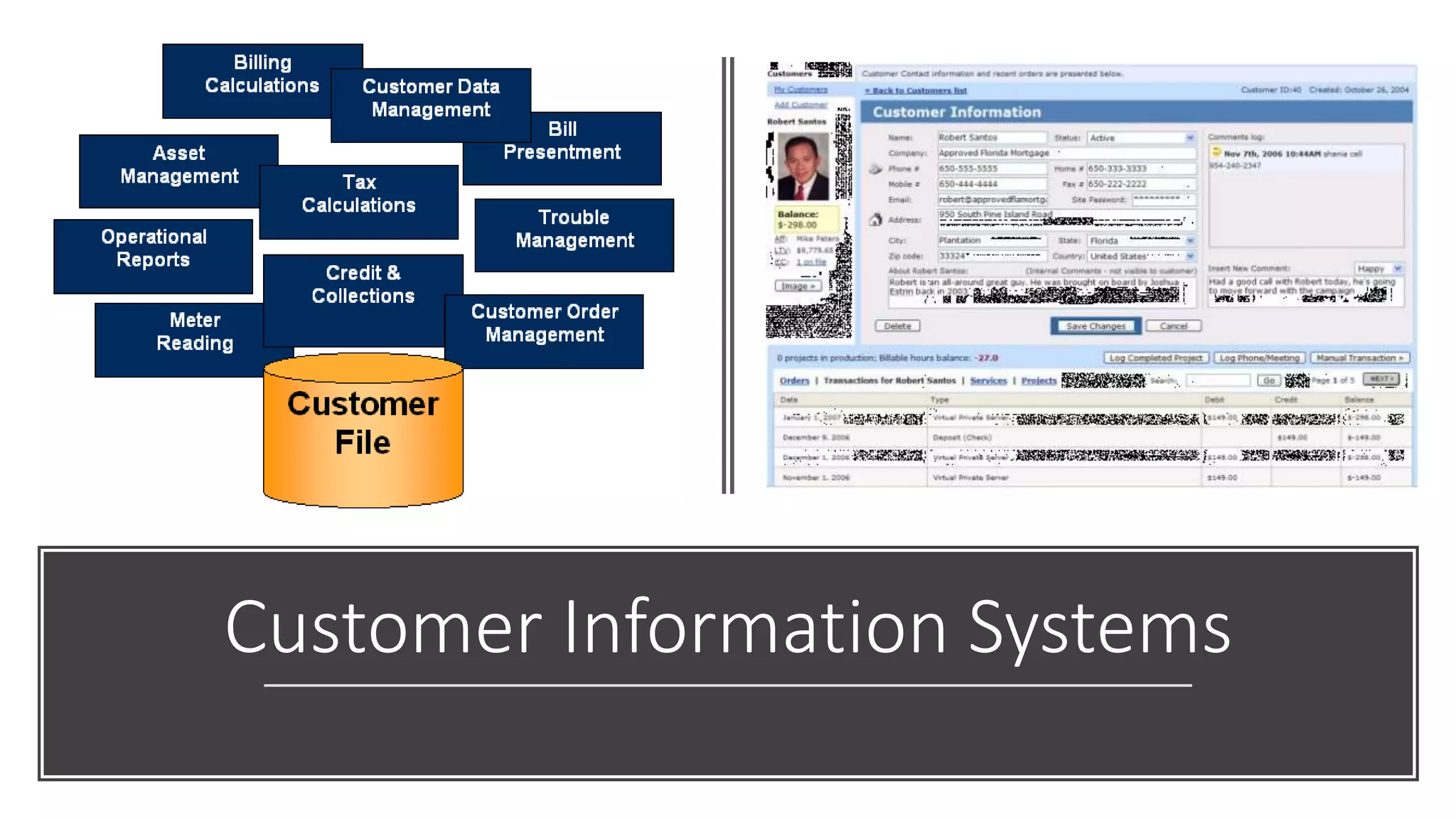
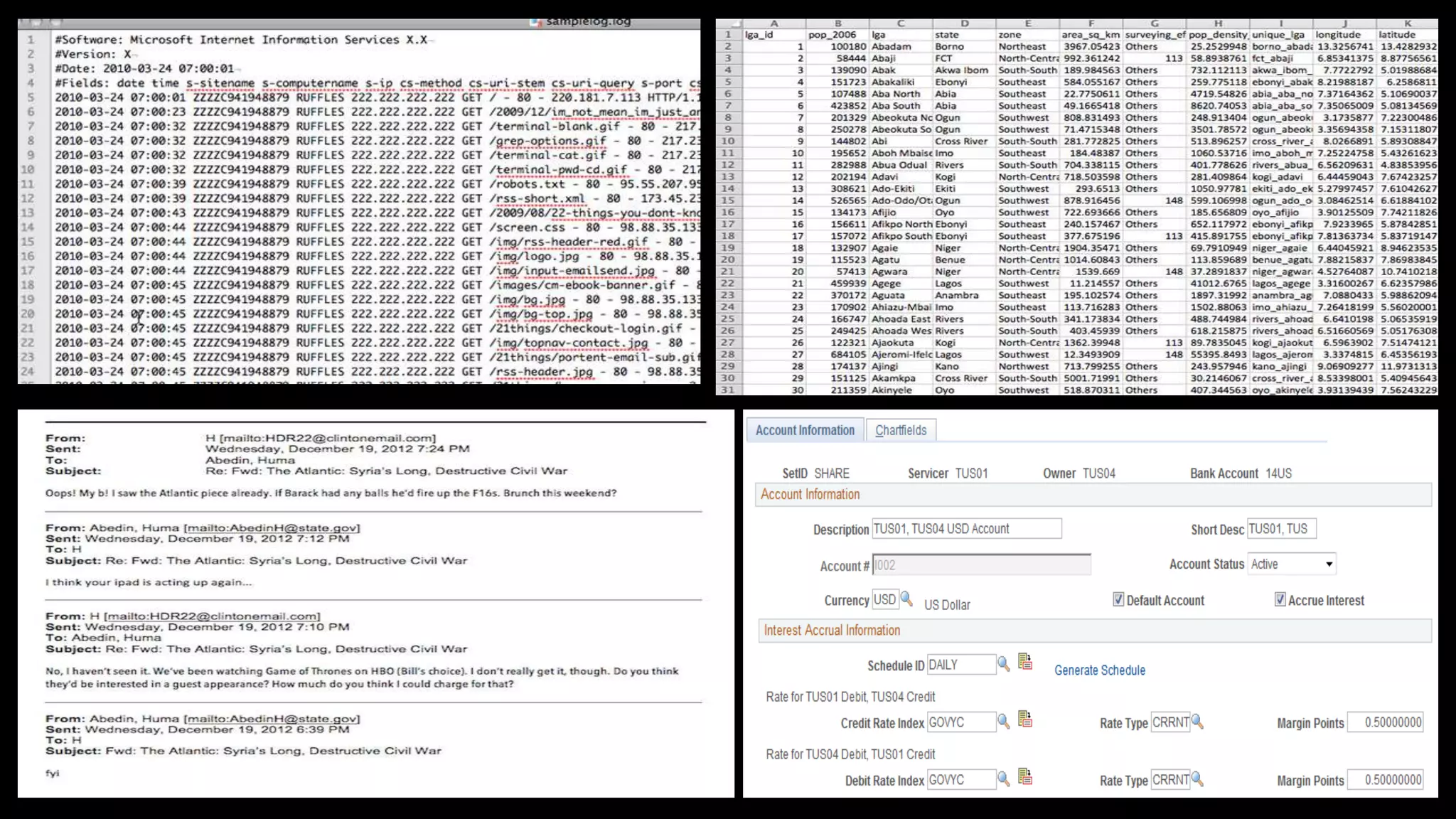
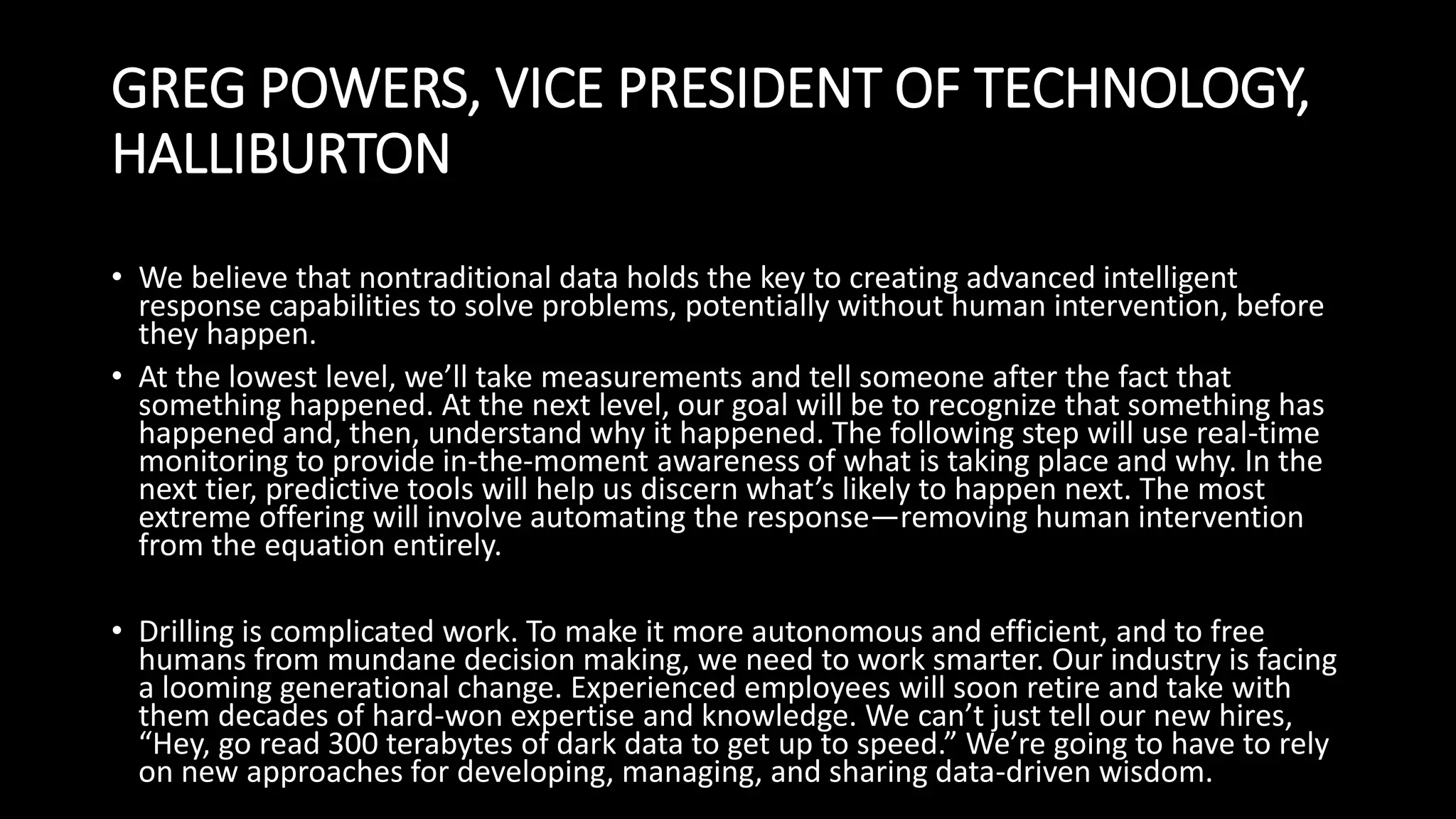
The document discusses dark data, defined as unutilized information collected by organizations that can pose legal, reputational, and financial risks if not analyzed properly. Approximately 90% of data generated is never used, leading to potential opportunities and insights being lost, particularly in sectors like healthcare and retail. Strategies for mitigating risks and turning dark data into valuable insights include ongoing inventory assessments, advanced analytical tools, and integrating data from various sources.