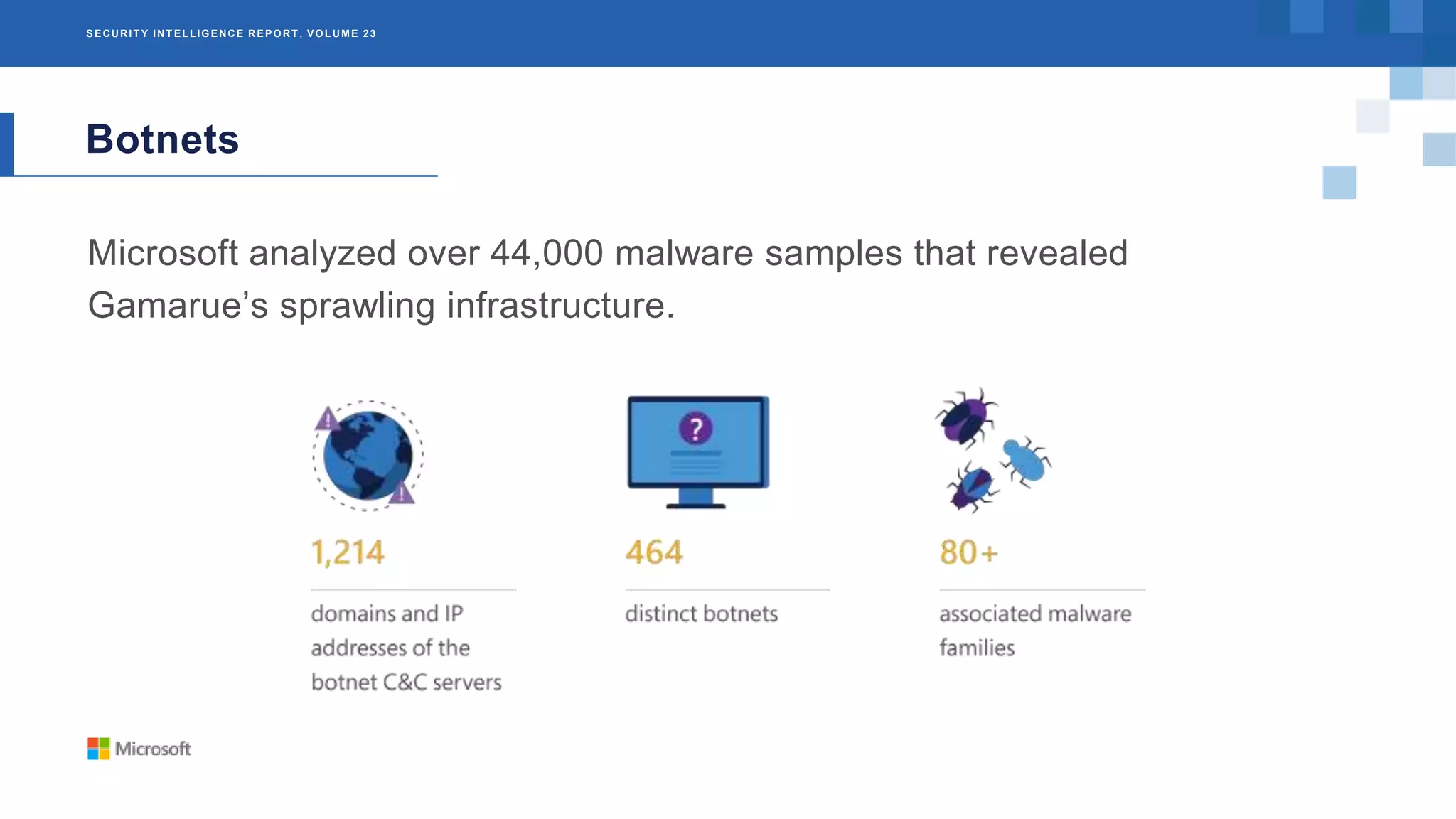
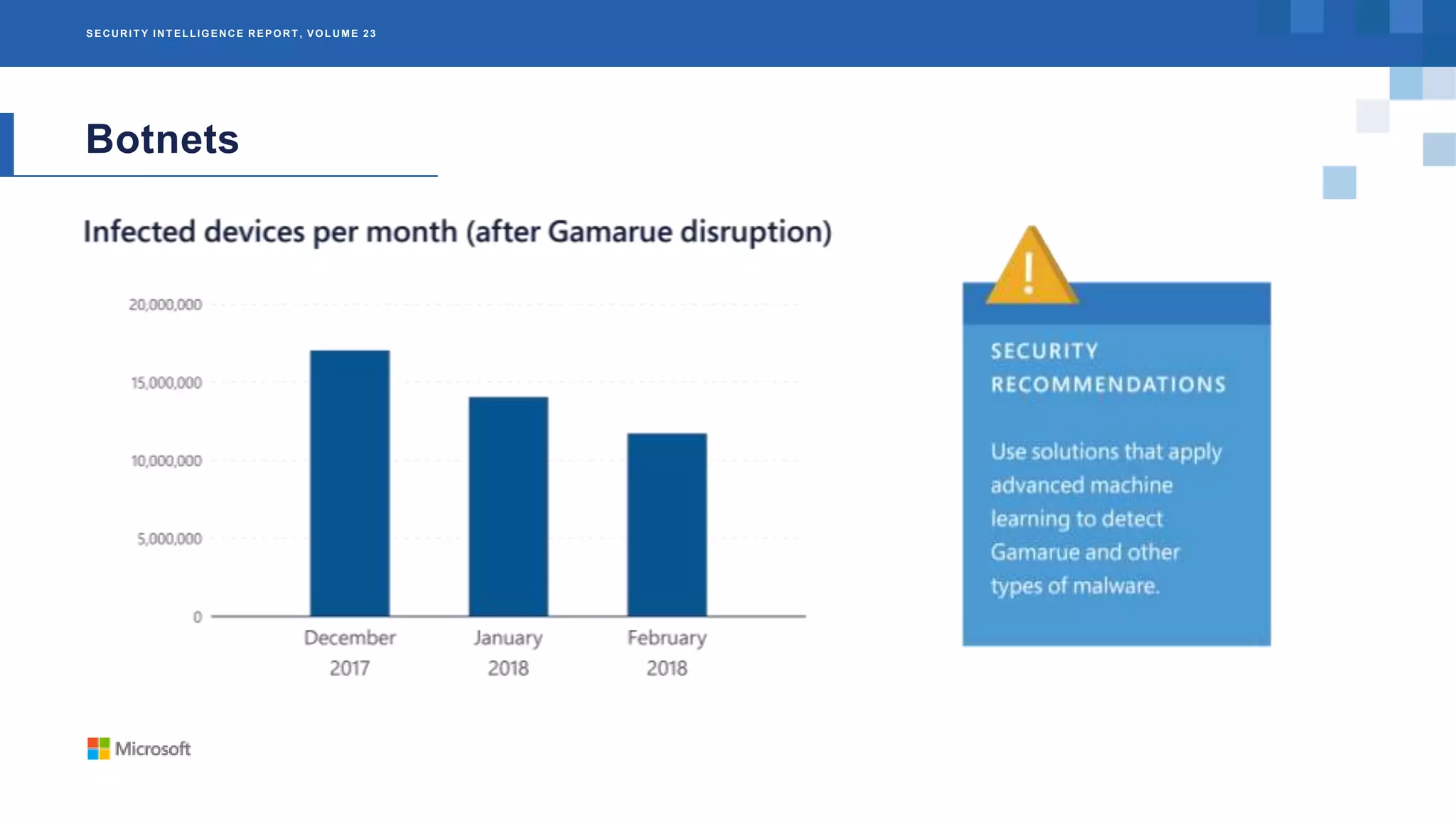
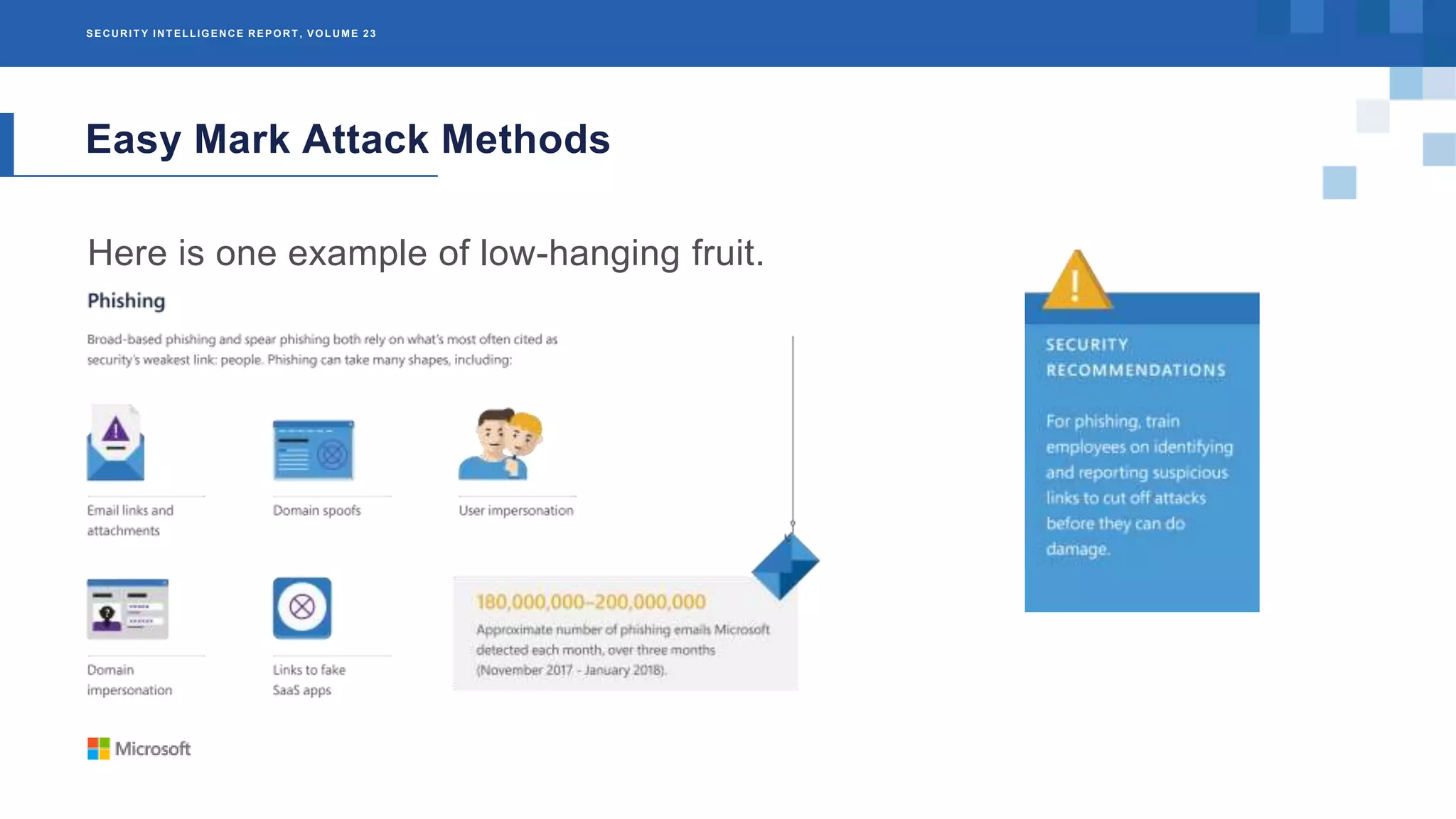
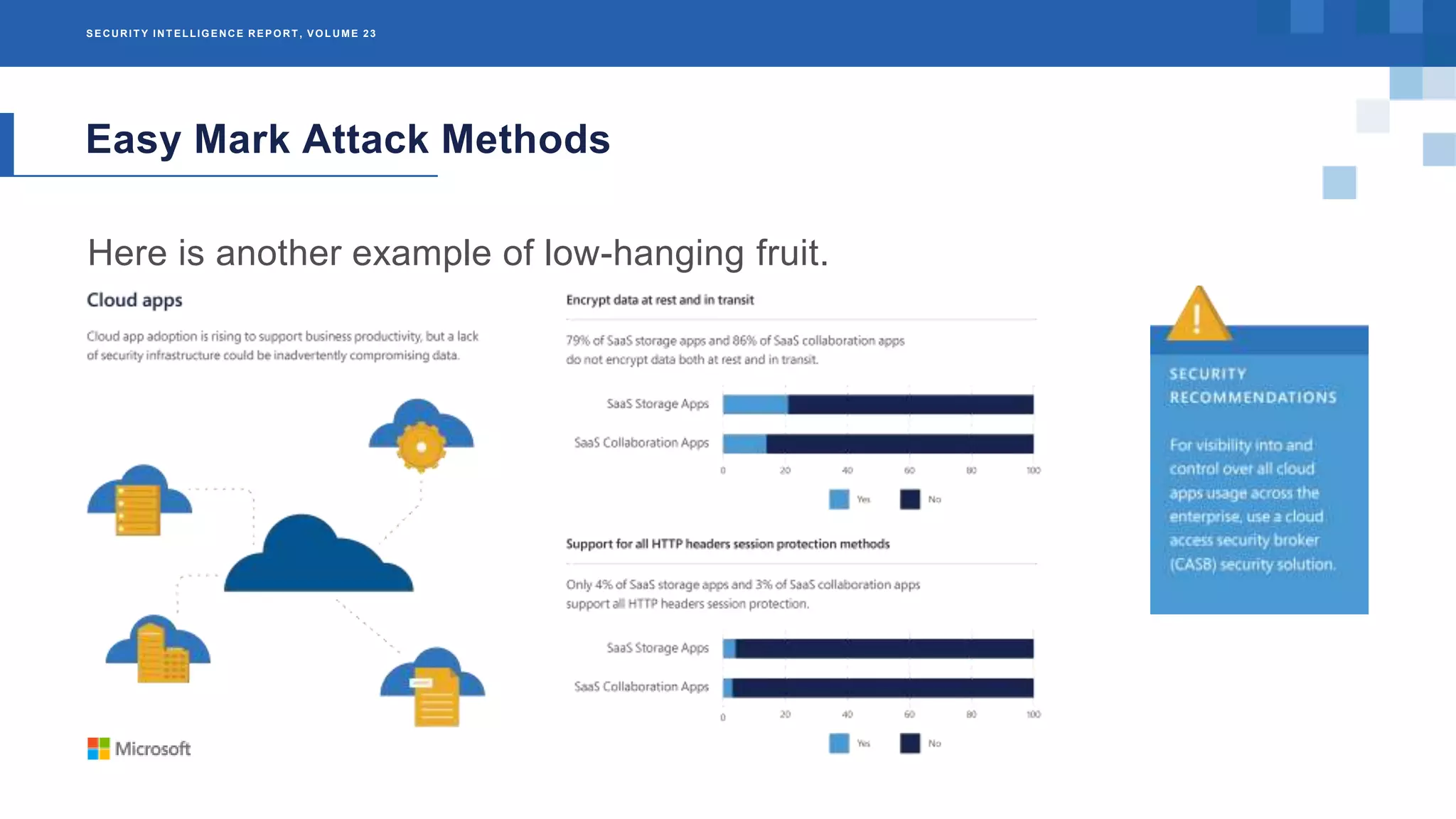
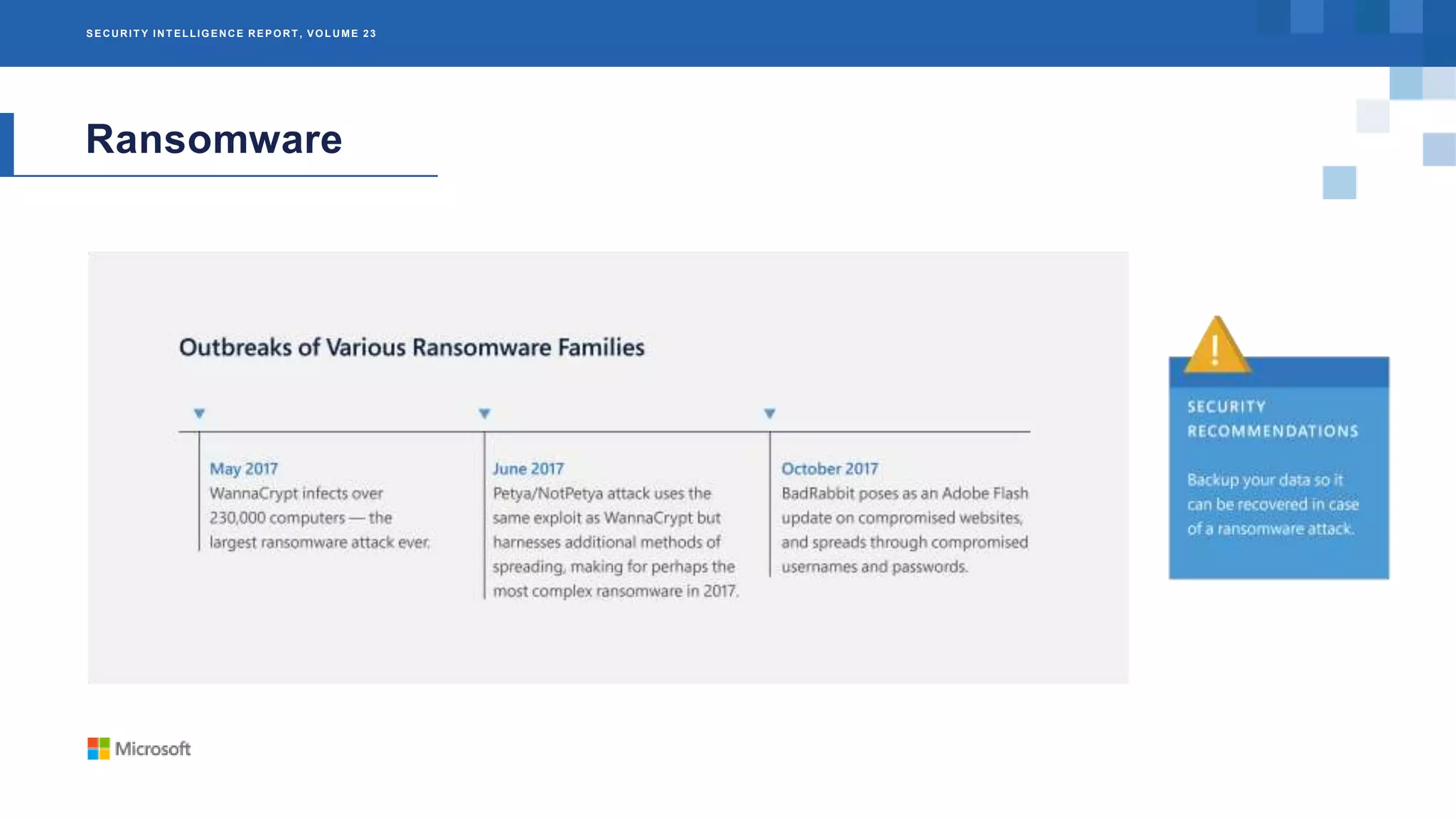
The Microsoft Security Intelligence Report, Volume 23, provides an analysis of cybersecurity threats from 2017, focusing on botnets, easy mark attack methods, and ransomware. It highlights the prevalence of botnets like Gamarue, which infected over 23 million IP addresses, and notes how attackers are adapting to security measures through social engineering. Additionally, the report details the impact of ransomware on critical services and emphasizes the importance of understanding these threats for better mitigation strategies.