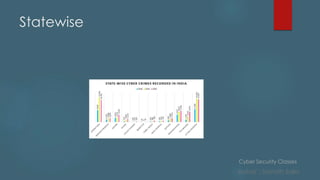
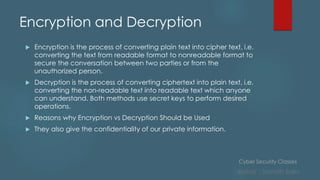
This document provides an overview of cyber security classes taught by Sainath Salla. It discusses various topics that will be covered in the classes like potential risks and vulnerabilities, definitions, privacy best practices, and types of cyber threats. It also explains key concepts such as what cybersecurity is, types of sensitive information, common threats like hacking and malware, and how to protect against threats like ransomware and phishing. Furthermore, it describes models like the OSI model and important terms like steganography and encryption/decryption.