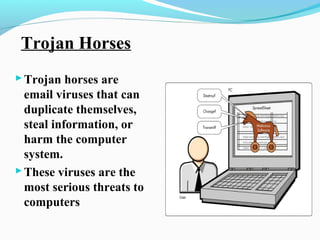
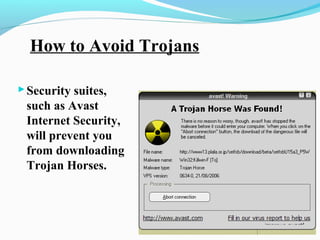
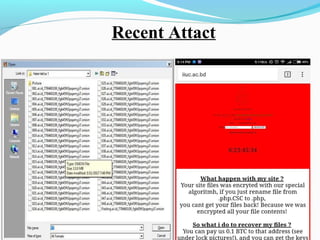
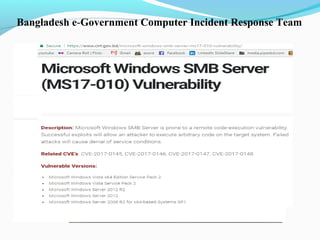
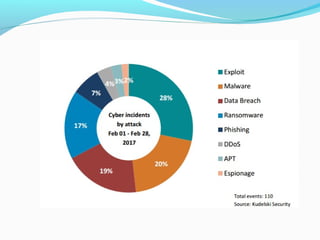
This document discusses cyber security and the present threats. It defines cyber security as protecting networks, computers, programs and data from attacks. Some major security problems are discussed like viruses, hackers, malware, Trojan horses, password cracking, and ransomware. The document provides preventive measures that can be taken against these threats like installing security suites, using strong passwords, and enabling firewalls. It also discusses advantages of cyber security like protecting data theft and disadvantages like systems running slower. In conclusion, complete security is difficult but being aware and taking smart precautions can help.