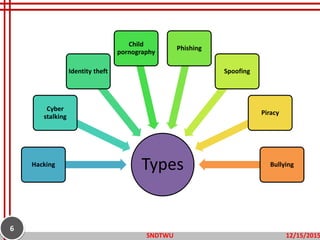
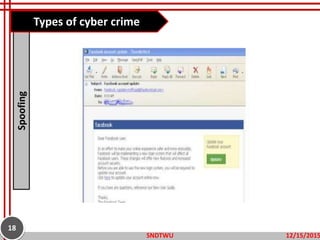
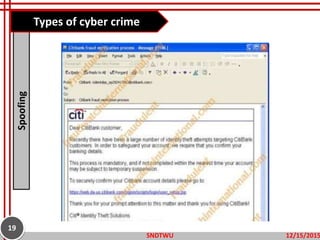
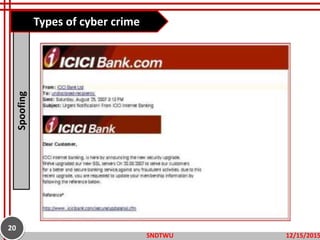
The document provides an overview of cybercrime, defining it as illegal activities conducted through electronic means and outlining its various types, including hacking, identity theft, and cyberstalking. It emphasizes the increasing prevalence of cybercrime in modern society and discusses potential prevention measures such as using strong passwords and securing networks. The objectives include understanding the definitions and types of cybercrime and learning ways to prevent them.