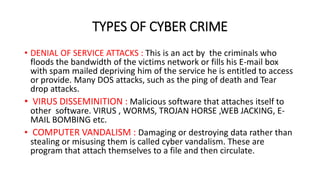
The document discusses various forms of cybercrime, categorizing them based on the role of computers as targets or tools in committing criminal activities, including hacking, denial of service attacks, and cyberbullying. It highlights the motives behind such crimes and outlines the challenges faced by law enforcement, specifically referencing the Prevention of Electronic Crimes Act, 2016 in Pakistan. Additionally, tips for individuals to protect themselves from cybercrime are provided.