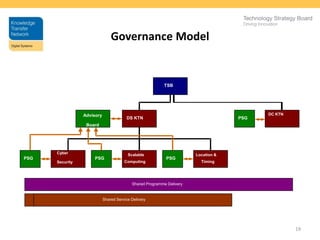
The Knowledge Transfer Networks (KTNs) were set up in the UK to facilitate knowledge sharing and collaboration between business, government, and academia. The Digital Systems KTN focuses on key digital technologies and brings together experts to address challenges like cybersecurity, cloud computing, and smart transportation. Collaboration is important for tackling issues in a digital society by sharing expertise, innovations, and understanding of problems. The KTN promotes collaboration through events, funding, special interest groups, and knowledge sharing to help overcome challenges like data security and privacy. There is potential to expand this model internationally to form a coordinated global response to cybersecurity threats.