This document provides an overview of cryptography and its history. It discusses:
- Why cryptography is studied, including its real-world applications and interest for students.
- Basic cryptography terminology like cryptographers, cryptanalysts, encryption algorithms, and secret keys.
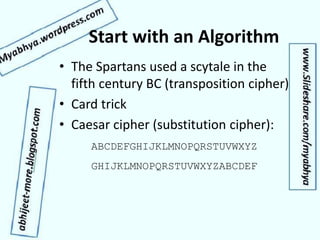
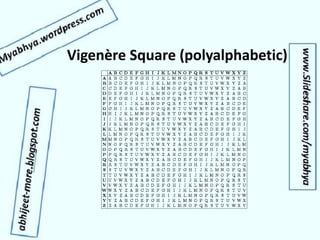
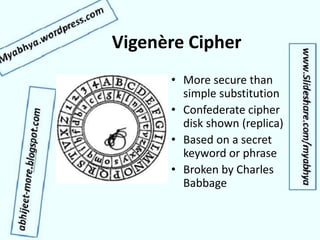
- Examples of early encryption techniques from ancient times to cipher machines in World War II.
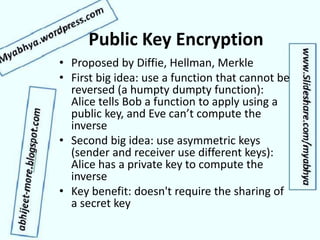
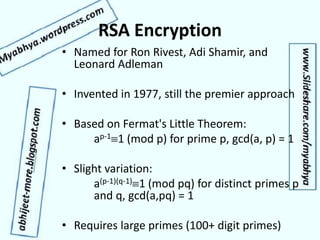
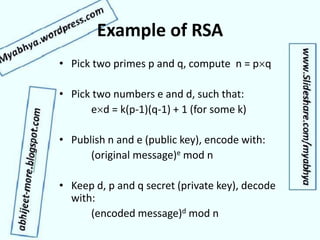
- Modern public key encryption like RSA, which was a major innovation allowing secure digital communication.
- Political issues around cryptography and efforts to develop and crack encryption methods through history.