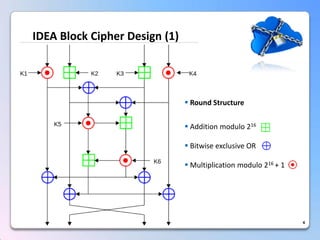
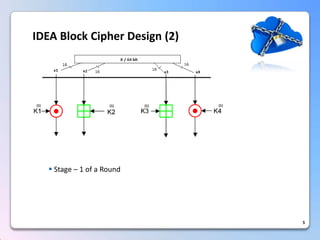
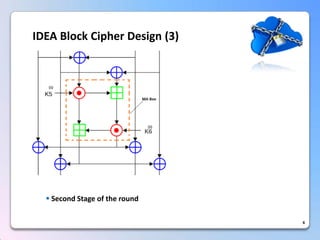
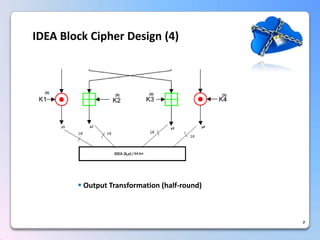
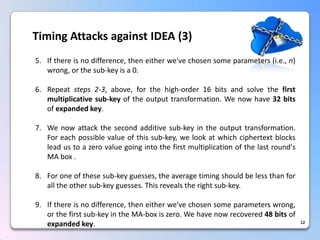
This document summarizes a timing attack against the IDEA block cipher. It describes how precise timing measurements of encryptions can reveal information about the secret key. The attack analyzes timing differences between encryptions to determine when operations like multiplication involve a zero value. This leaks key bits over multiple rounds of the analysis. The attack can recover the full 128-bit key without knowledge of the plaintext.