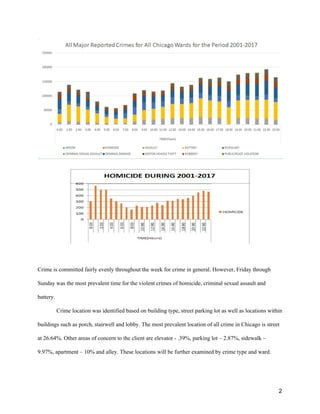
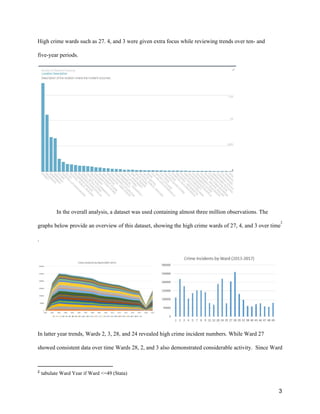
This report provides recommendations for scheduling security officers at properties owned by a client based on an analysis of crime data from 2001-2017 in Chicago. It finds that Wards 27, 3, and 4 experience the highest crime, with Ward 27 the primary focus. Crime peaks from May-September and Friday-Sunday. Theft and battery are most common. It recommends a seasonal staff that fluctuates based on time of day and week, with extra security in Wards 27 and 3 focusing on streets, apartments, and sidewalks from 1-2pm and 10pm-8am. Social media could also help prevent crime.

![27 is a focused area for security recommendations, nearby Ward 28 should be included with guard
coverage.
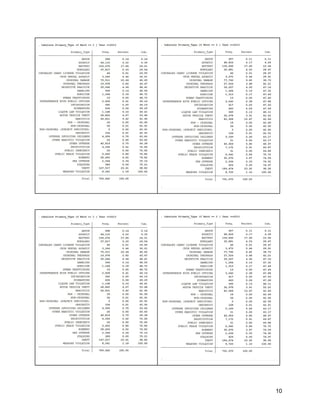
For Wards 1 through 4, the team focused on the five most recent years of data from 2013 through
2017 . The data revealed that out of
3
these four wards, Ward 2 had the highest
crime incidents across this five year
period, peaking in 2017 at 11,420
incidents. Ward 3 had the next highest
rate across the five year period, peaking
at 8,317 in 2013. Wards 1 and 4 had less
incidents across the same five-year
period and 2016 seemed to have the least amount of incidents overall as compared to the other four years.
Next, the team explored the type of crime and amount between the same five-year period.
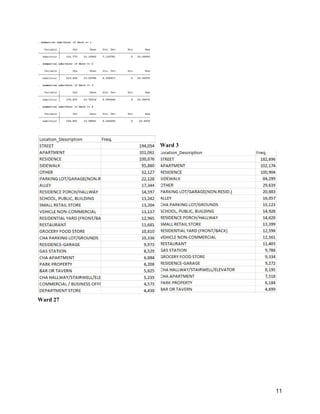
Crime trends of the same four wards also offered interesting results. Theft and battery were the
two most common crime types between 2013-2017 . Narcotics and assault crimes seem to be the two
4
additional crime types that are common in Wards 1 through 4. While theft is a serious offense, battery
involves physical safety of a person and as a result, it will be included in recommendations for security
personnel coverage, especially in Ward 3. Other crimes of substantial consideration include burglary,
criminal damage, robbery, and motor vehicle theft. Deceptive practice and motor vehicle theft also have
noticeable numbers in the analysis. In addition to battery, assault includes physical safety of a person and
will also be included in the recommendation section for security personnel coverage. Consequently, the
3
tabulate Ward Year if Ward <= 4 (Stata)
4
tabulate Primary_Type if Ward==[1,2,3,4] | Year >=2013 (Stata)
4](https://image.slidesharecdn.com/crimesprojectreportrevised-180415201817/85/Crimes-Project-Data-Mining-Analytics-5-320.jpg)
![average time these crimes took place across all four wards were between 1 p.m. - 2 p.m., which will also
be included in security coverage in the final recommendations .
5
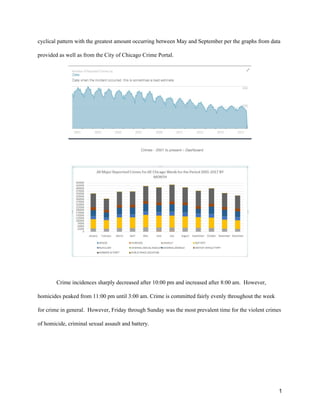
When graphing ten-year historical crime data in the city, there is a clear weather pattern
associated with crime. In January and February, crime tends to be relatively low, accelerating in April and
May to a July peak. From July through the end of the year, the graph slopes downward indicating less
crime as the temperature decreases. This proves to be a benefit to your firm as fewer security guards will
be needed in the colder months. Perhaps seasonal staff can help in the summer for a discounted “seasonal
employee” type rate. The weather relationship holds true for our biggest concern, Ward 27.
5
summarize admithour if Ward==[1,2,3,4] | Year >=2013 (Stata)
5](https://image.slidesharecdn.com/crimesprojectreportrevised-180415201817/85/Crimes-Project-Data-Mining-Analytics-6-320.jpg)