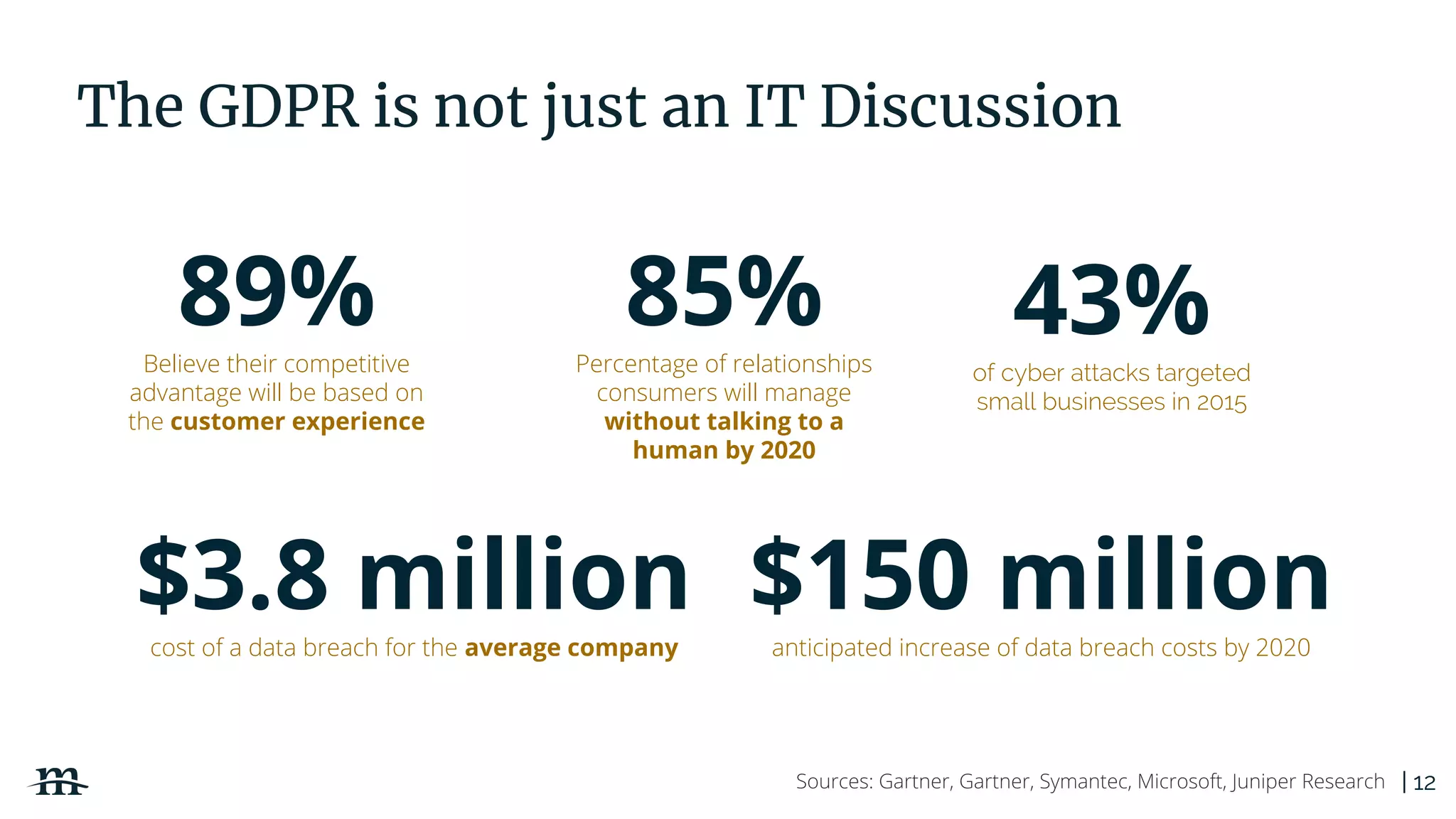
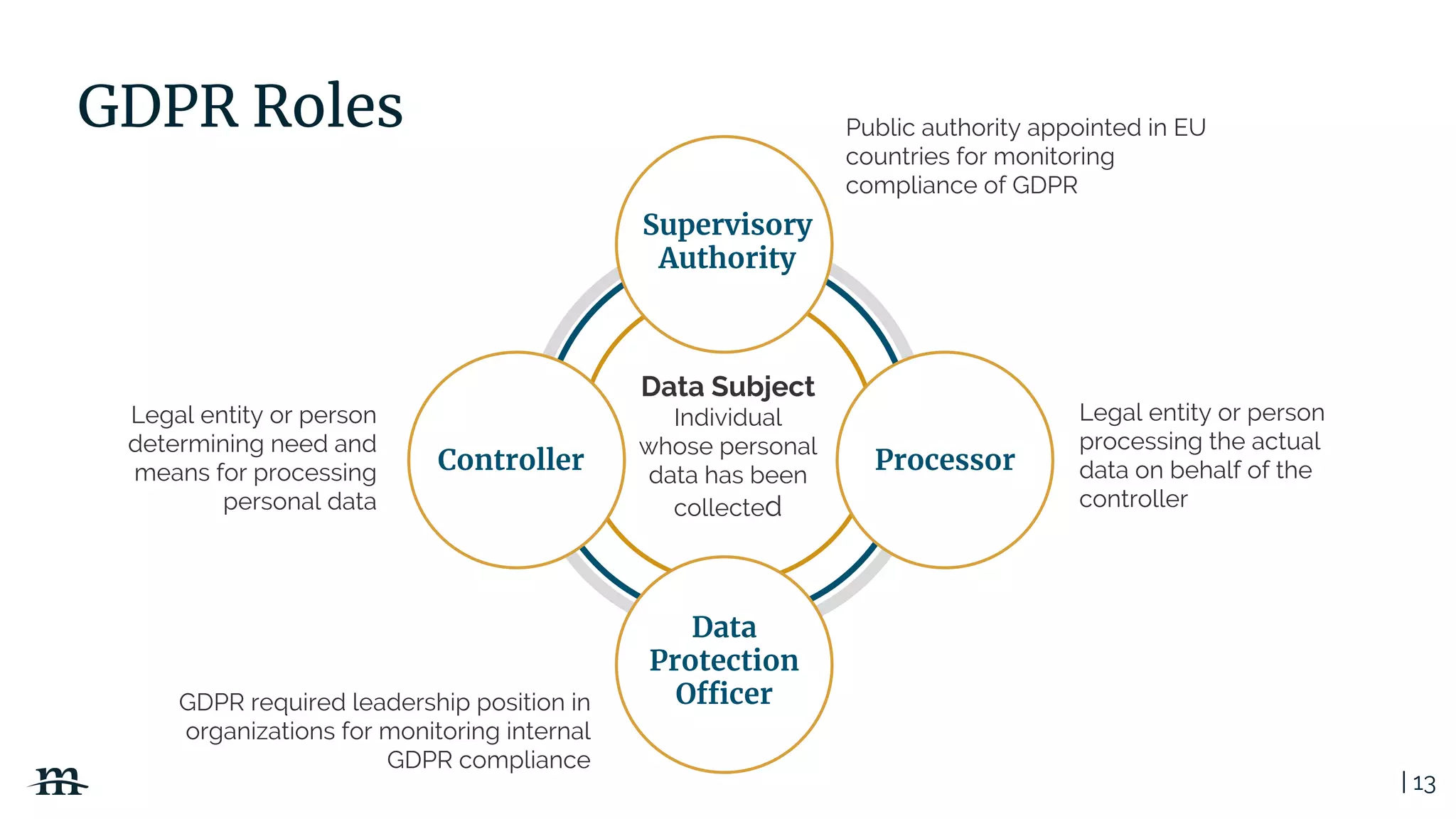
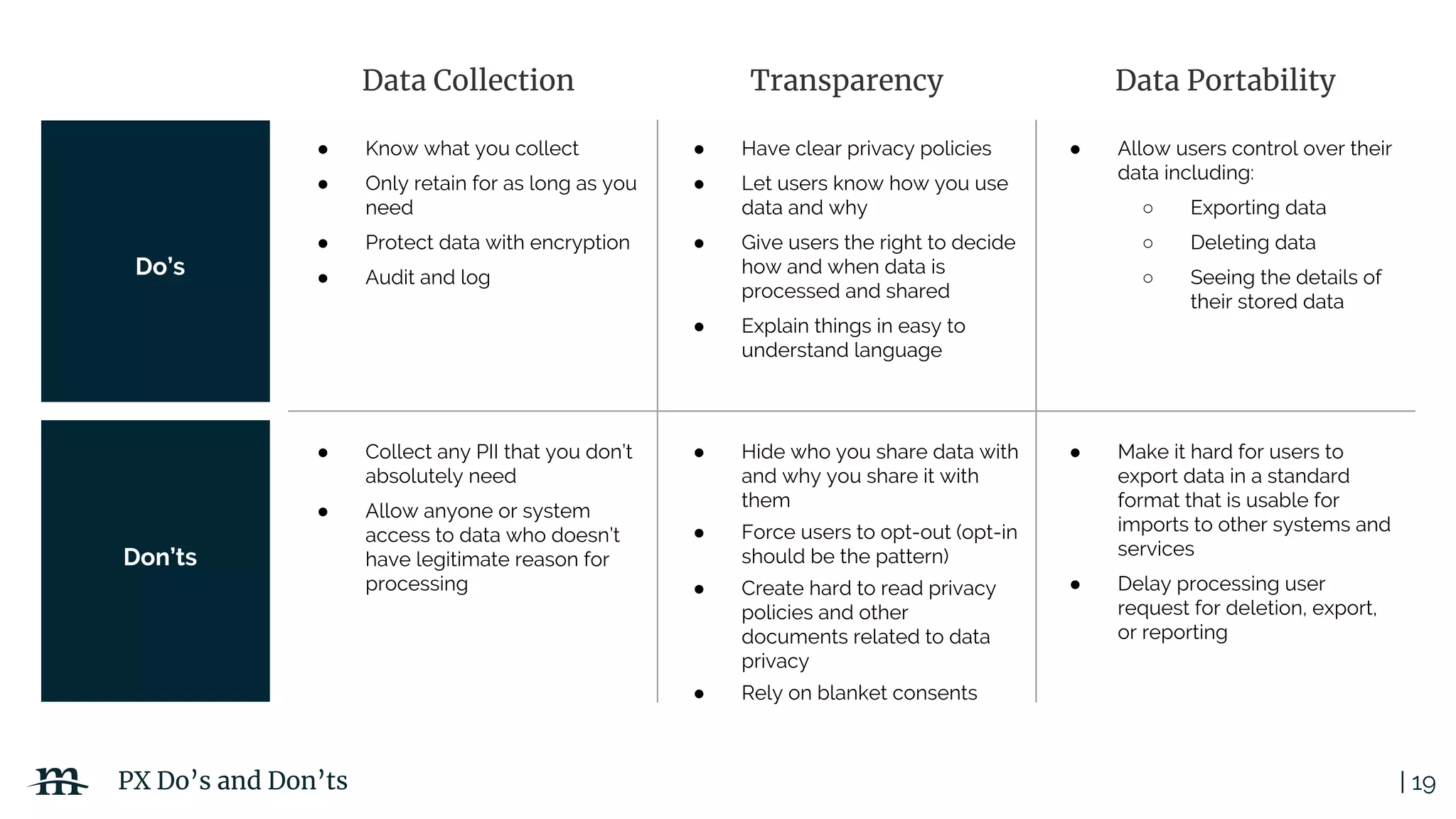
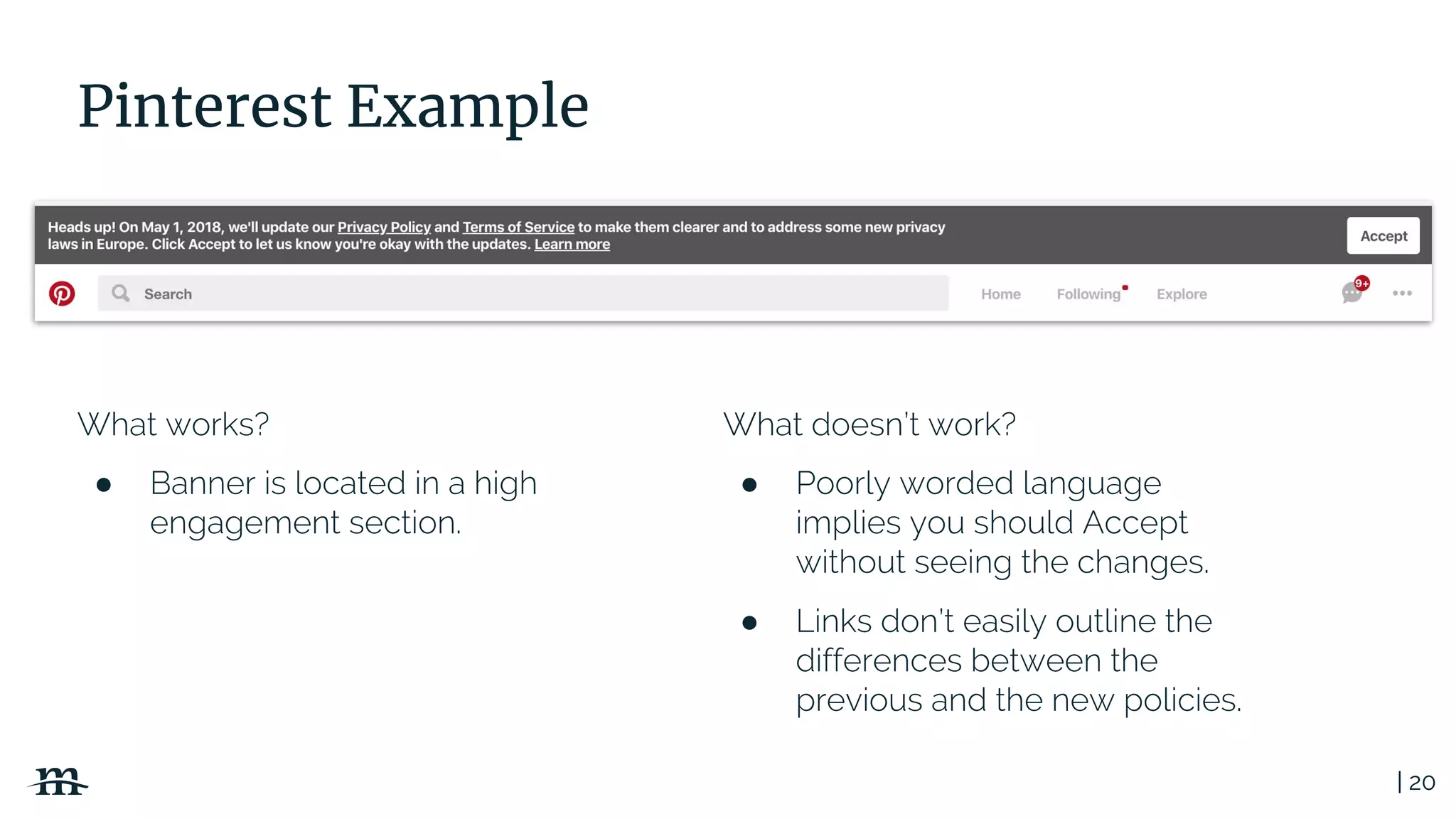
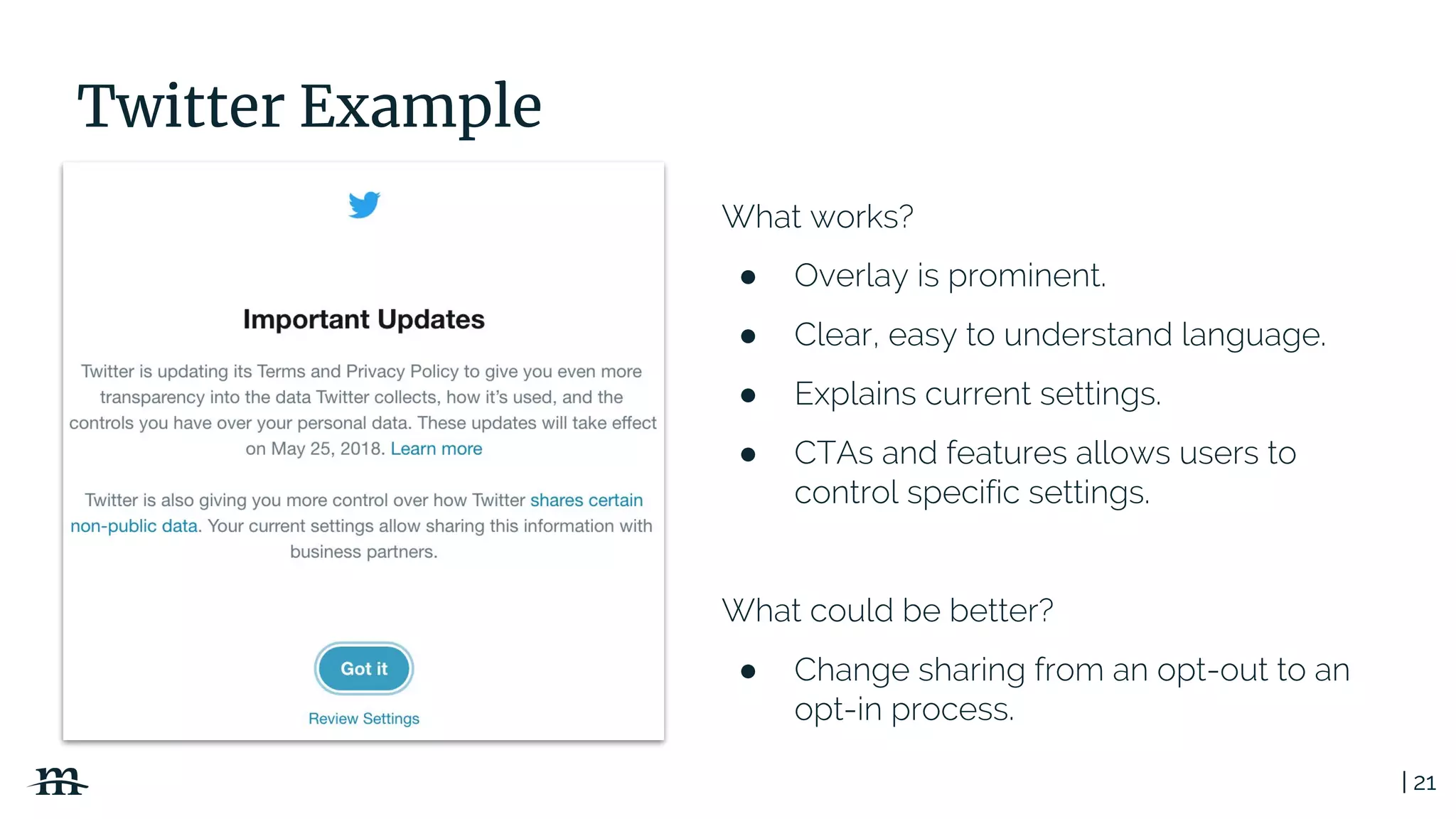
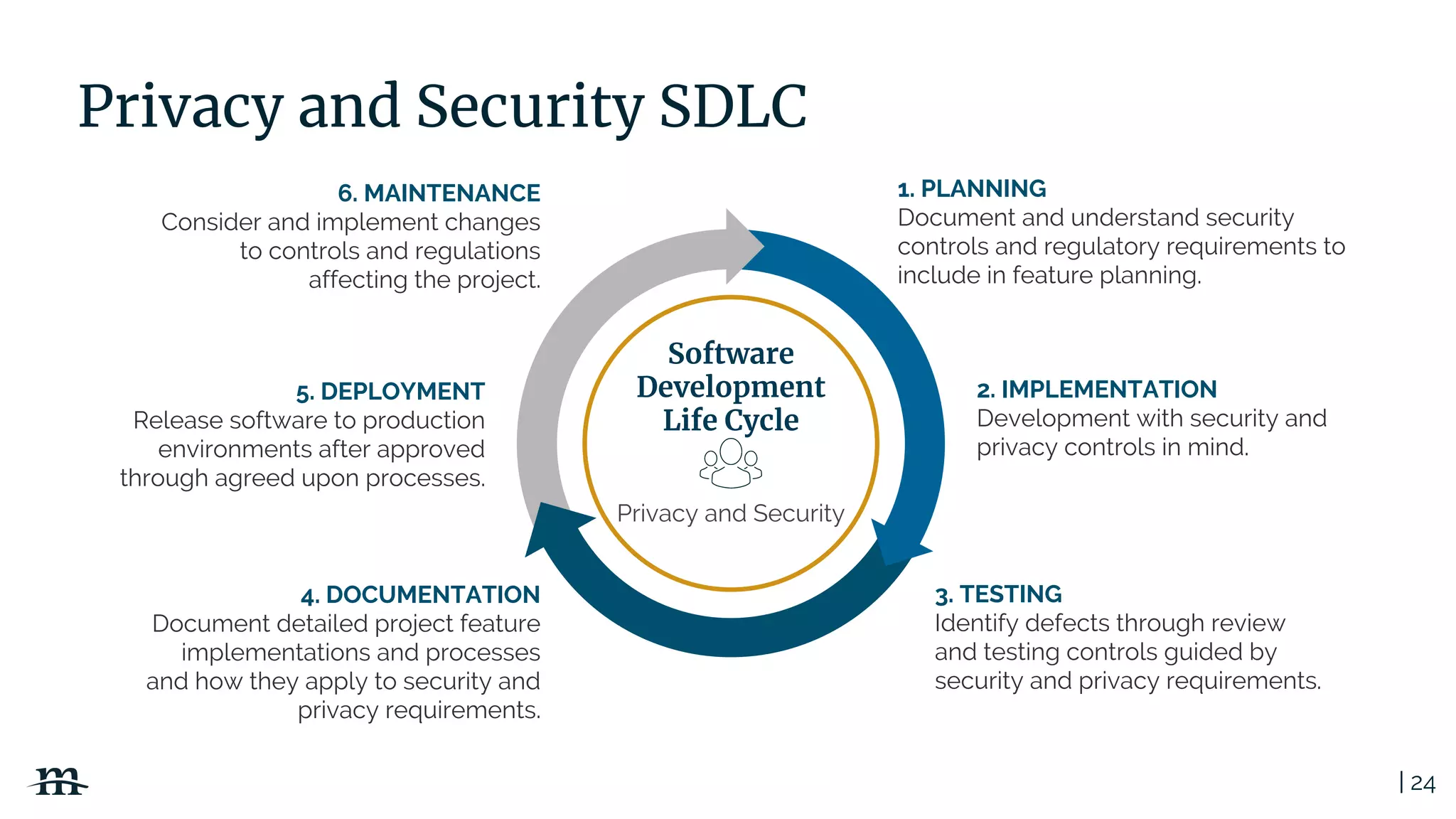
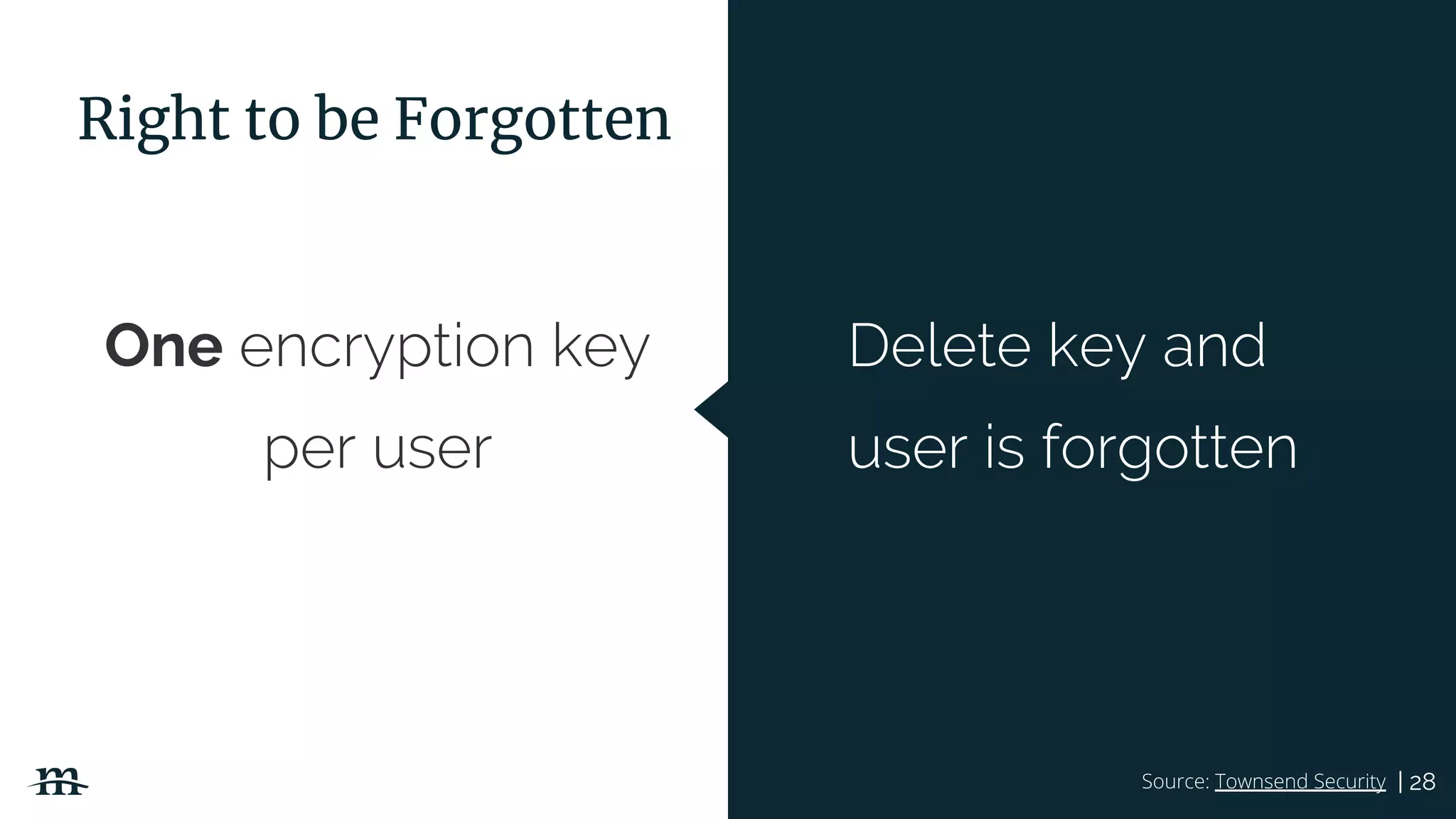
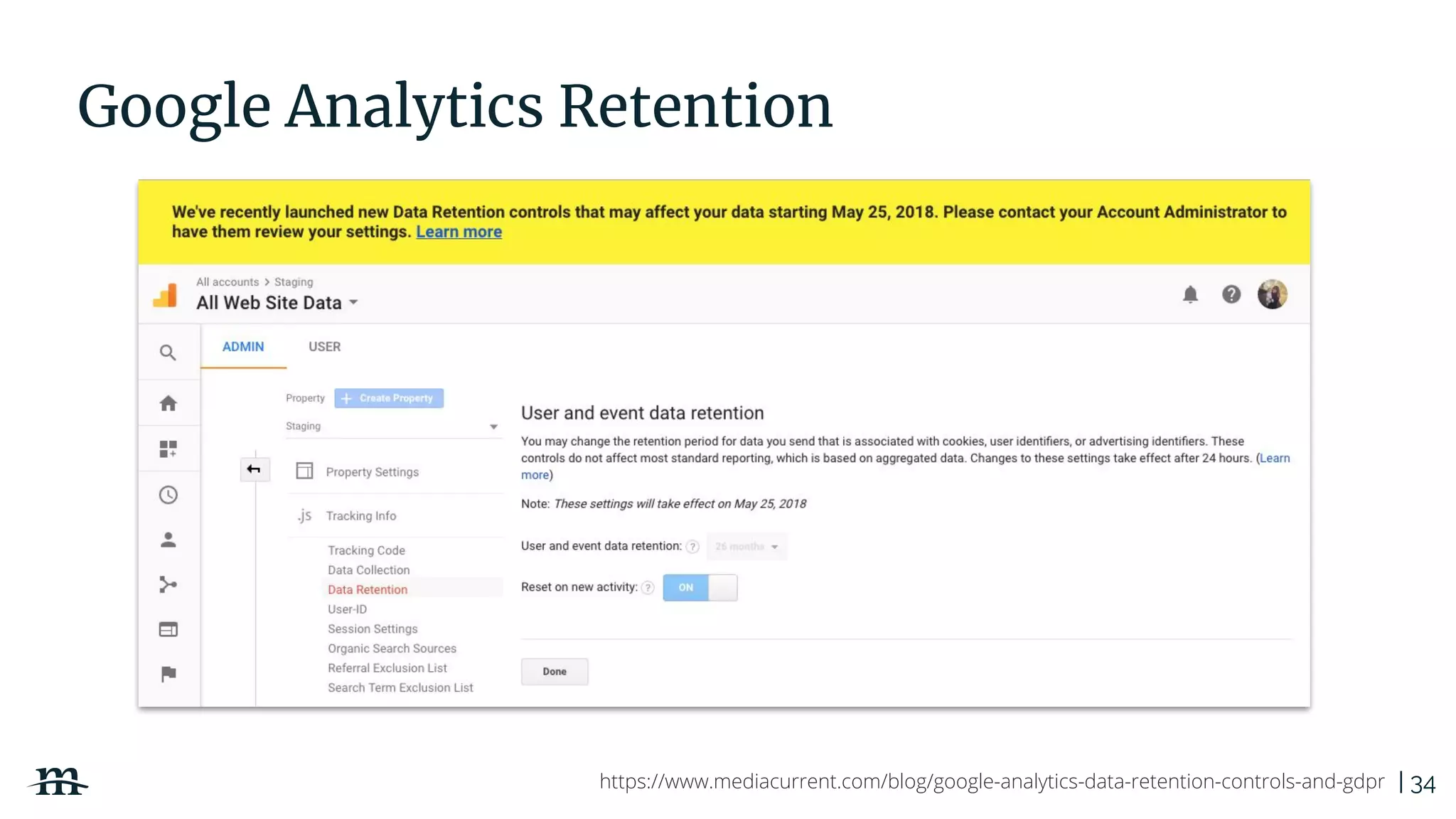
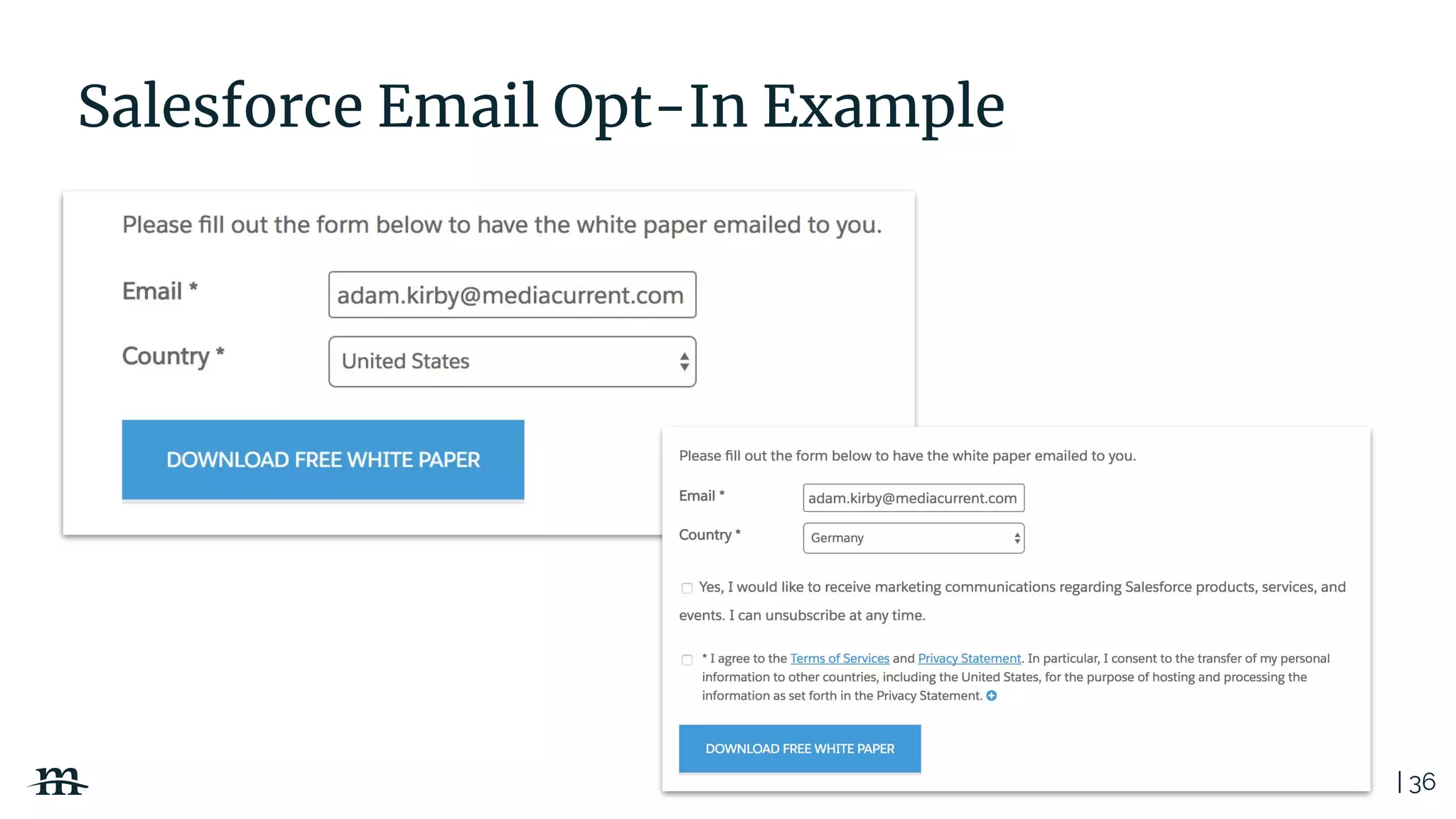
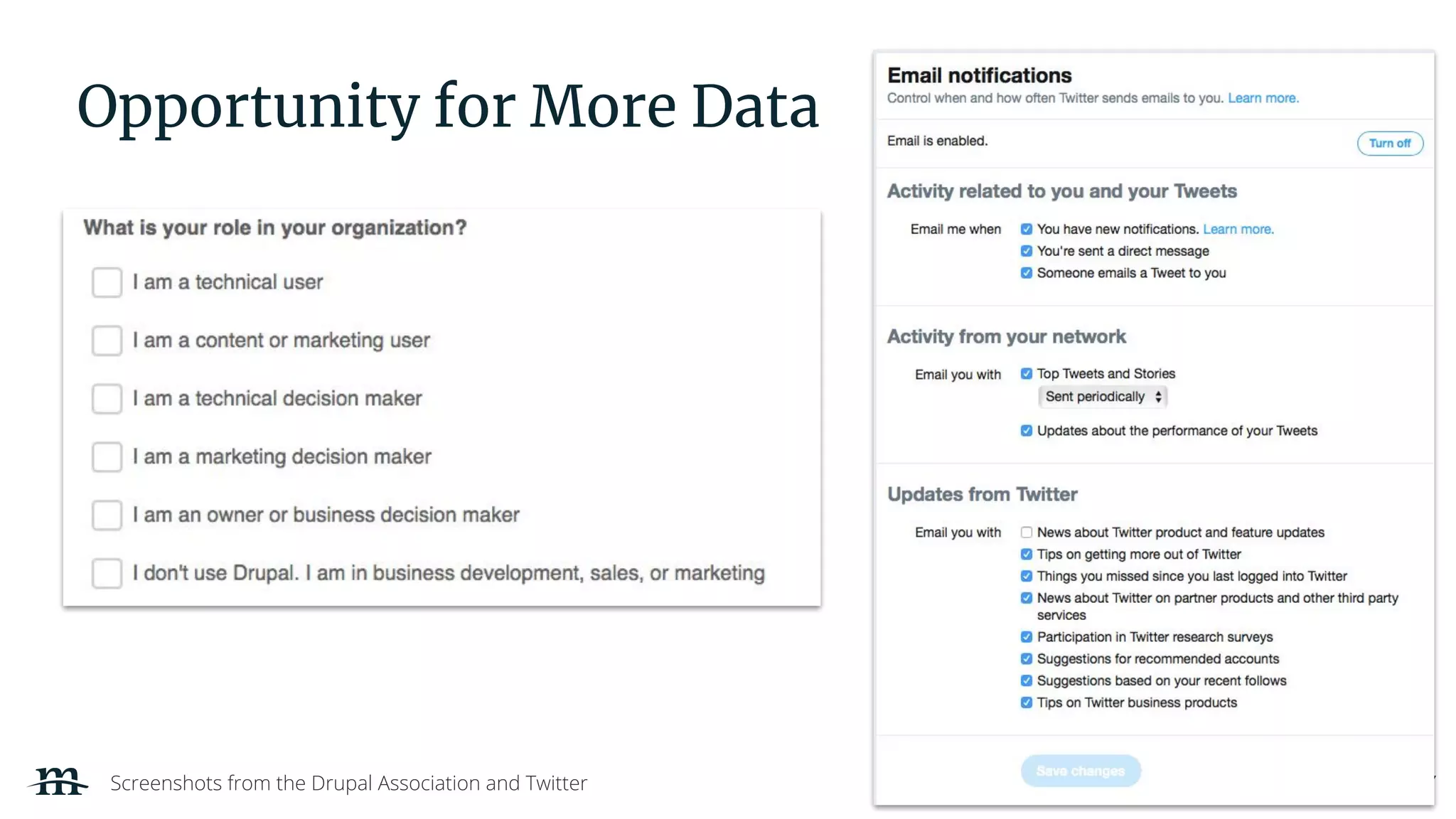
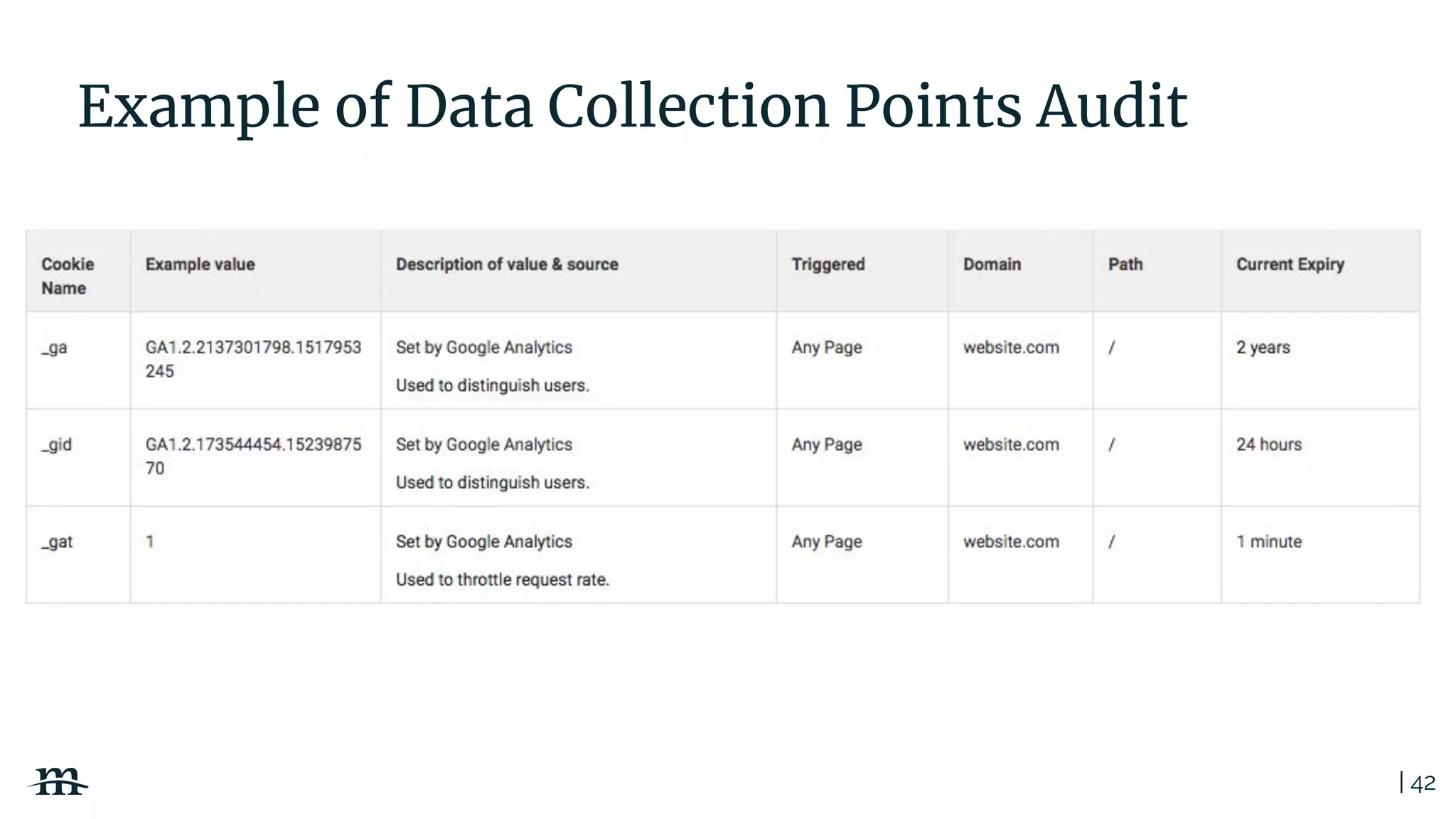
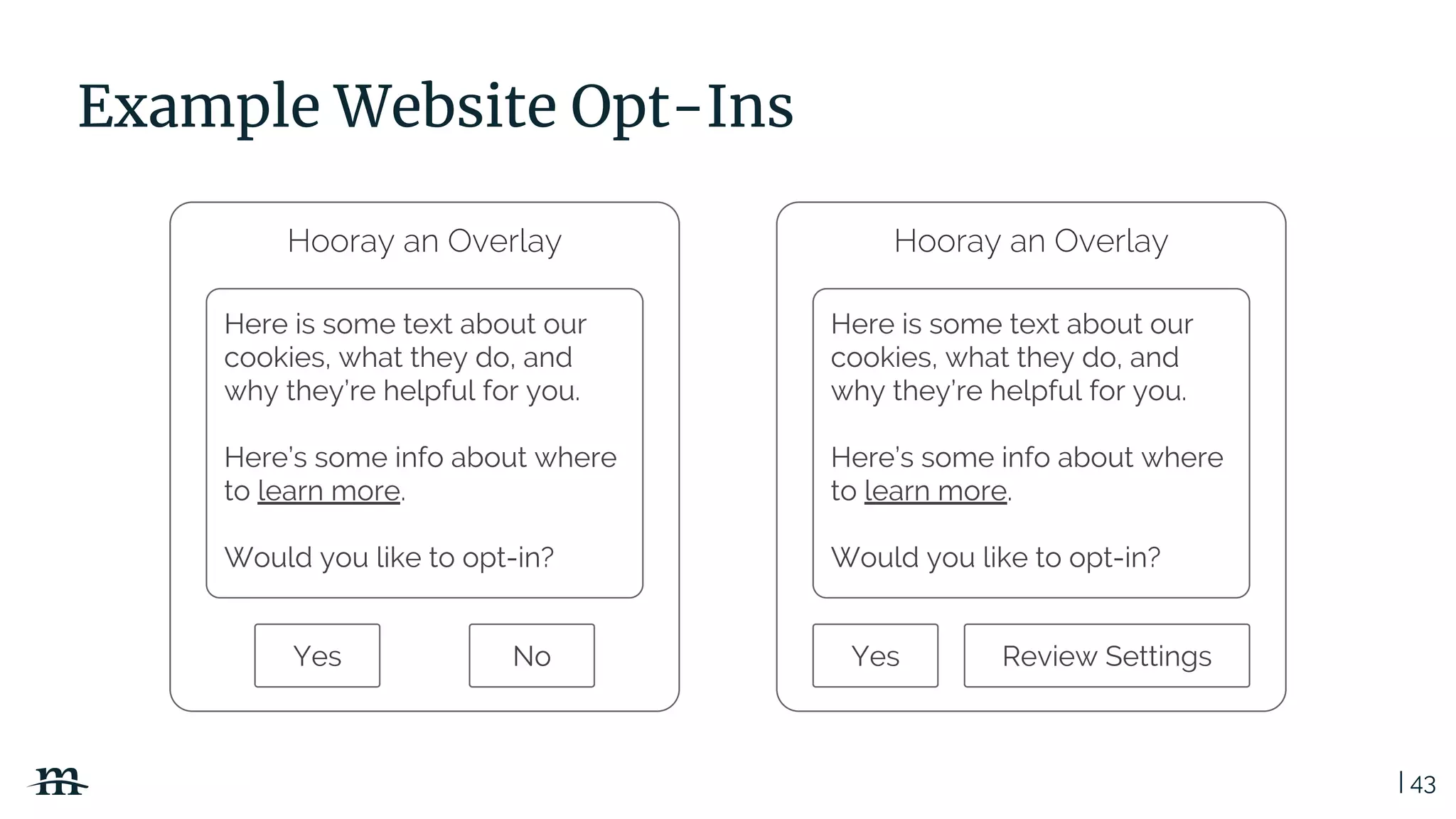
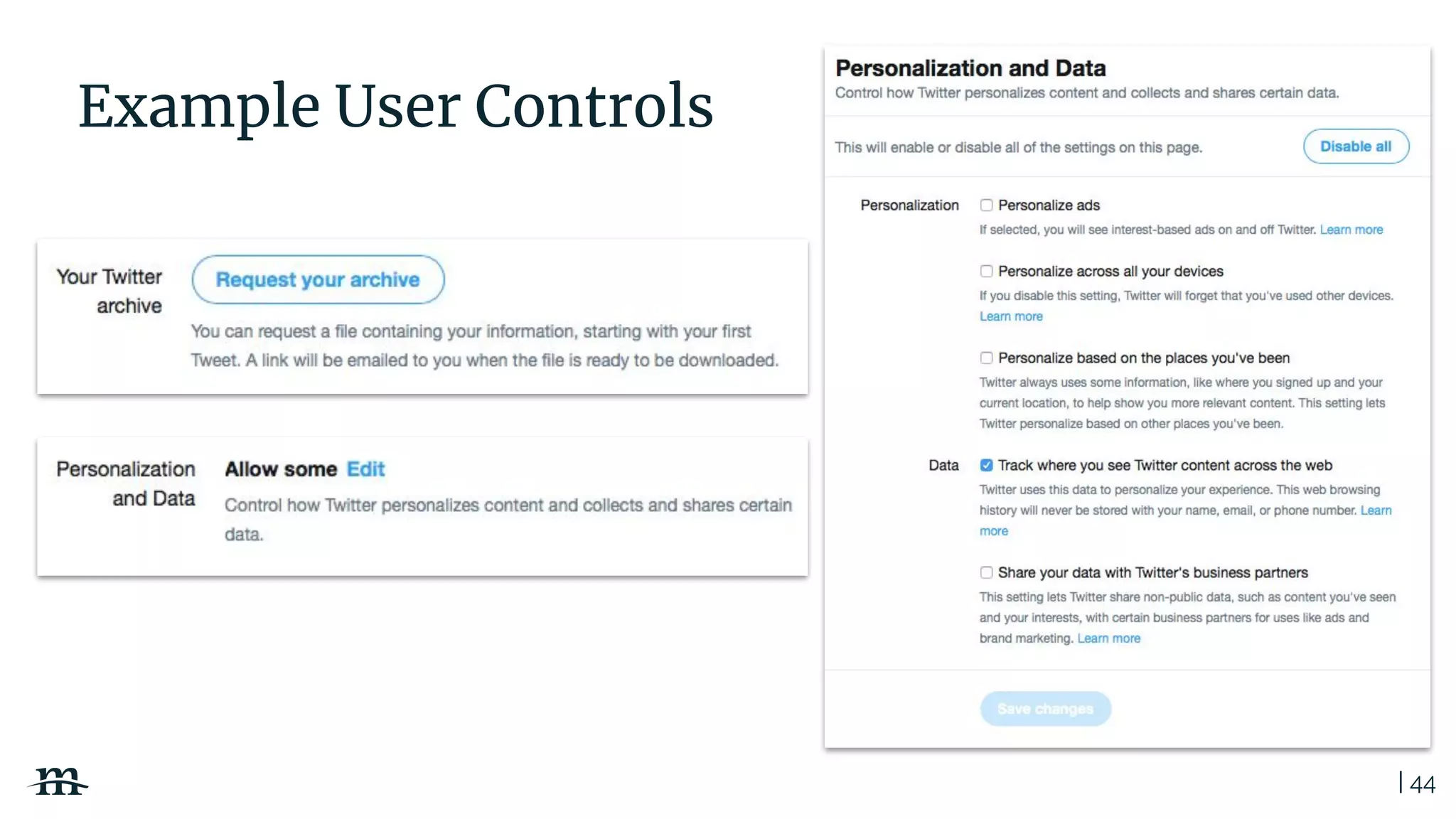
The document outlines a webinar focused on creating a GDPR action plan, emphasizing compliance needs for organizations handling personal data. It highlights the importance of understanding GDPR principles, implementing security measures, and ensuring user rights are upheld to avoid hefty penalties. Additionally, it suggests strategies for creating a positive privacy experience and establishing an actionable framework to align with GDPR regulations.