This document presents a comprehensive training agenda on Java fundamentals, focusing on its core concepts, features, and object-oriented programming principles. It covers essential topics such as Java's history, platform independence, data types, exception handling, and core programming techniques like inheritance and polymorphism. Additionally, it discusses Java's string handling classes, collections, and the Java Development Kit (JDK) components required for compiling and executing Java programs.









![Page 36Classification: Restricted
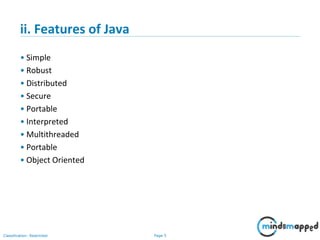
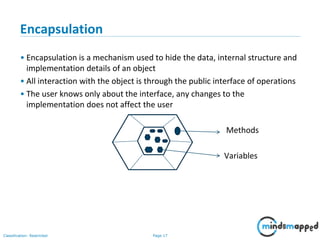
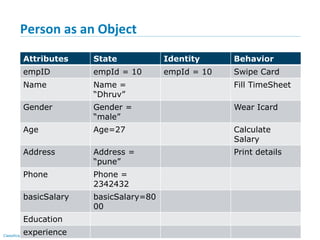
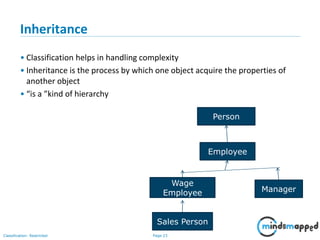
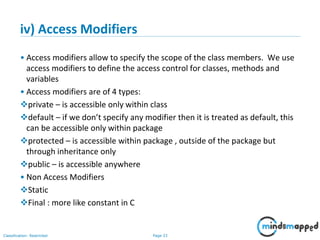
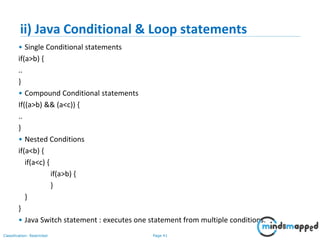
vi) Java Class Syntax
By Convention:
class Class_Name class name starts with capital case
{ e.g. class MySample
variable_Declaration;
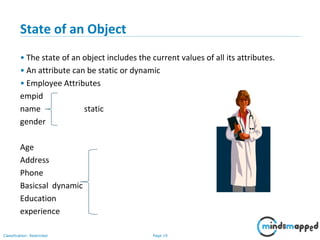
variable(attribute or property)
method_Declaration() { name starts with small case
….. e.g. int date
…..
}
public static void main(String args[]) Method(behavior) name starts with
{ first word small case then next
…. Words 1st letter capital case called
…. Camel case
} //end of class e.g. void printDate() {
}](https://image.slidesharecdn.com/day1112-corejava-180811153345/85/Core-Java-for-Selenium-36-320.jpg)
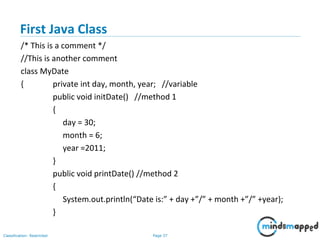
![Page 38Classification: Restricted
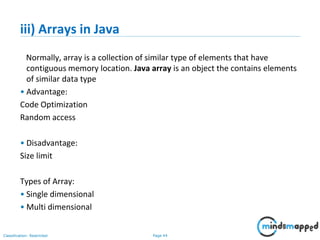
Create an Object
//continuation
public static void main(String args[])
{
MyDate d = new MyDate();
//method invocation
d.initDate();
d.printDate();
}
}](https://image.slidesharecdn.com/day1112-corejava-180811153345/85/Core-Java-for-Selenium-38-320.jpg)









![Page 51Classification: Restricted
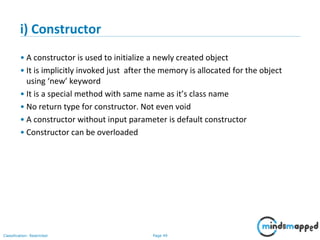
Sample Program
class MathEngine
{
public int add(int num1, int num2)
{
….
}
public int add(int num1, int num2, int num3)
{
…
}
}
class Program
{
public static void main(String args[])
{
MathEngine obj = new MathEngine();
int result = obj.add(12,13);
int output = obj.add(15,16,17);
}
}](https://image.slidesharecdn.com/day1112-corejava-180811153345/85/Core-Java-for-Selenium-51-320.jpg)






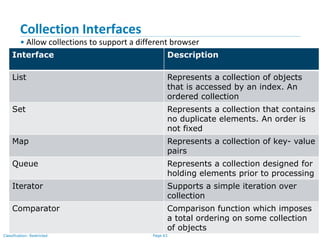
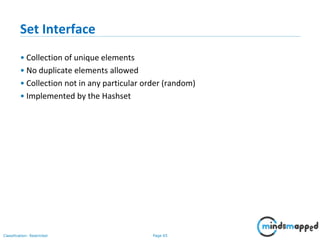
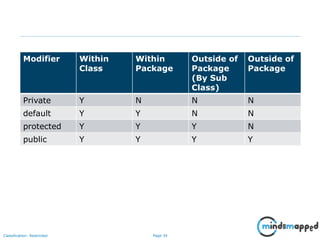
![Page 64Classification: Restricted
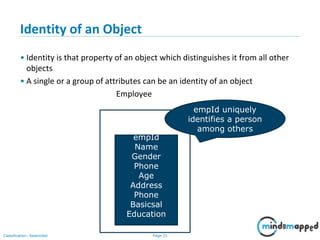
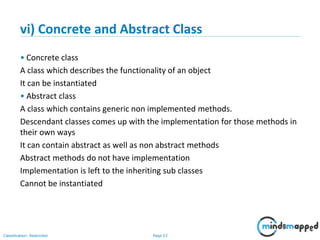
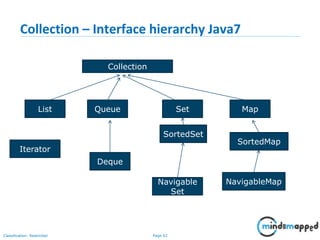
List Interface
• Ordered Collection
• May contain duplicates
• Implemented by classes
-- ArrayList [Resizable – array implementation of the List interface]
-- LinkedList [Doubly linked list implementation of the list]
--Vector [the Vector class implements a growable array of objects]](https://image.slidesharecdn.com/day1112-corejava-180811153345/85/Core-Java-for-Selenium-64-320.jpg)