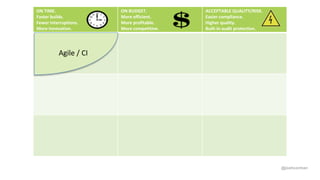
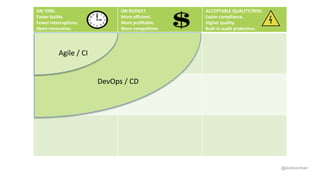
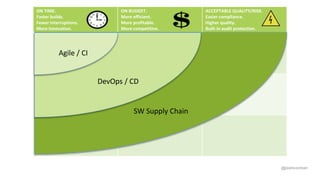
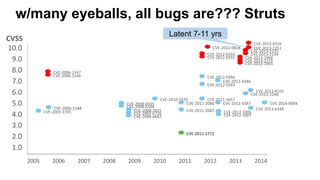
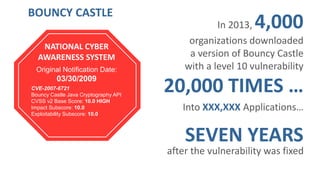
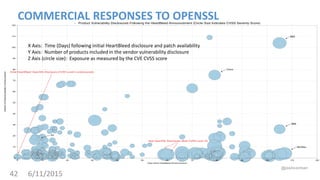
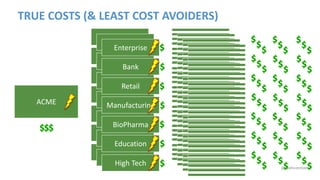
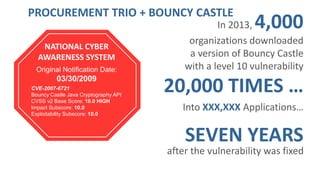
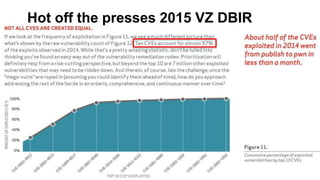
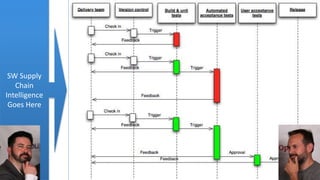
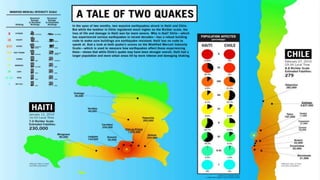
Josh Corman discusses adopting a software supply chain approach to accelerate development in a secure and efficient manner. This involves treating open source and third party components like a manufacturing supply chain by having fewer, high quality suppliers, and visibility into components used. This enables faster development by reducing interruptions and issues, and improves quality by avoiding known vulnerable components. As software and connected technologies grow critical, such rigor around software supply chains will be increasingly important for security and safety.