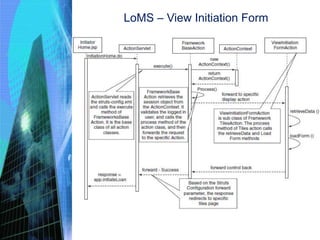
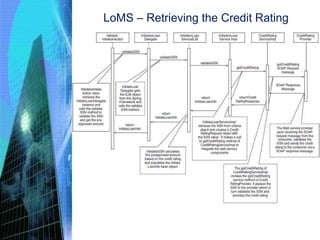
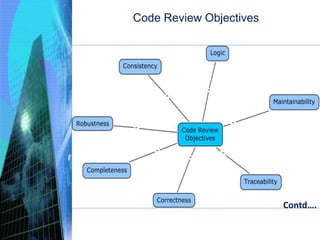
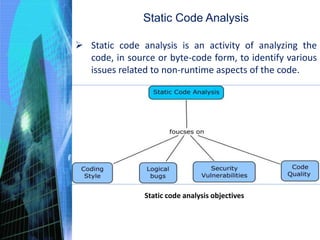
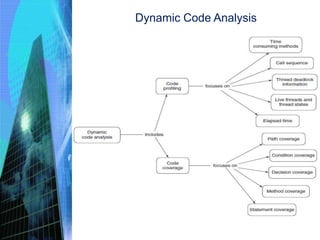
The document discusses the process of constructing enterprise applications. It involves translating the design into code components through various activities like achieving construction readiness, constructing solution layers, code review, testing, and creating deployable packages. Construction readiness includes defining a construction plan, package structure, configuration management plan, and development environment. Solution layers include infrastructure, presentation, business, data access, and integration components. Code review and static/dynamic analysis help ensure quality. The overall process aims to fulfill requirements through proper architecture, techniques, and tools.