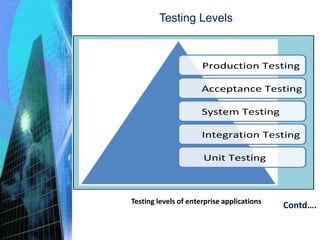
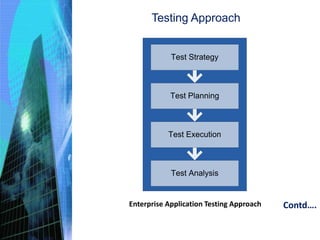
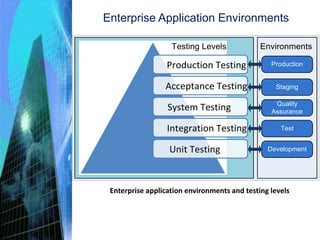
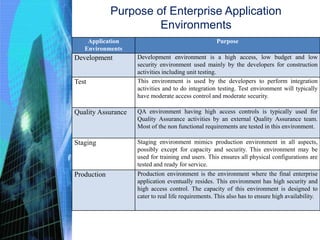
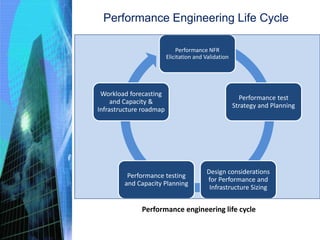
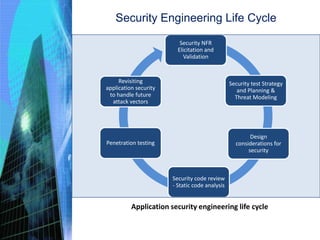
The document discusses various aspects of testing and rolling out enterprise applications. It describes different types of testing like functional testing, non-functional testing, white box testing, black box testing and gray box testing. It also discusses different testing levels from unit testing to acceptance testing and production testing. The document then covers testing approaches, environments, performance testing and security testing in detail. Finally, it provides an overview of user acceptance testing and strategies for rolling out enterprise applications.