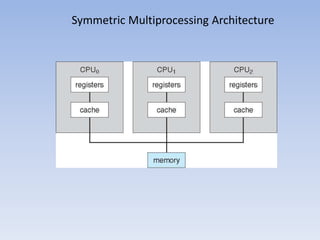
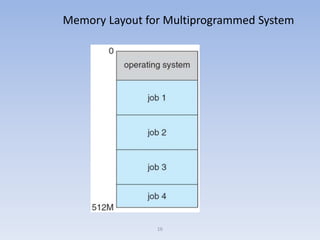
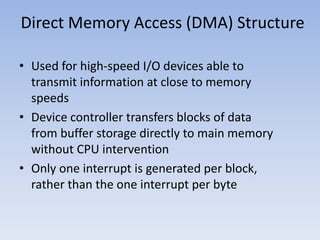
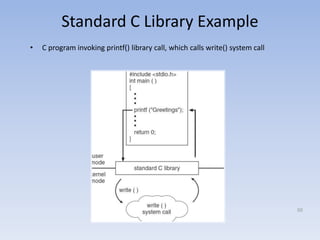
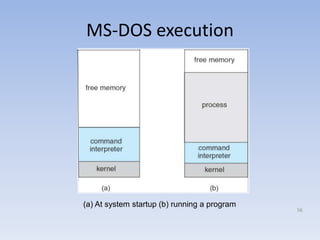
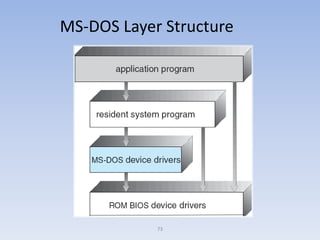
This document discusses computer system architecture and operating system structures. It covers single and multiprocessor systems, including symmetric and asymmetric multiprocessing. It also discusses clustered systems, operating system operations like interrupts and dual mode, and system calls. Finally, it discusses user interfaces like command line and graphical user interfaces, and simple operating system structures.