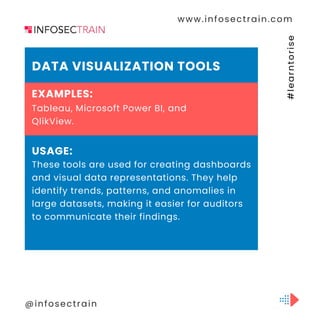
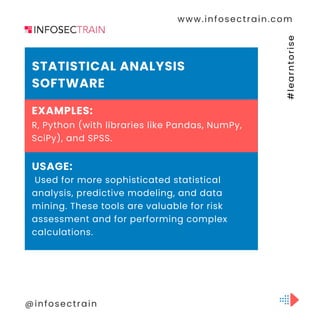
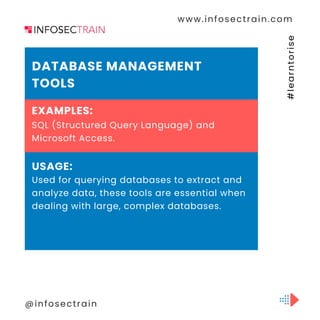
The document discusses Computer-Assisted Audit Techniques (CAATs), which are tools that help auditors analyze large datasets and assess controls in organizations. It mentions various software including Generalized Audit Software (GAS) like ACL and IDEA, data visualization tools such as Tableau and Power BI, and statistical analysis software like R and Python for sophisticated analysis. Additionally, it highlights continuous auditing tools, database management systems, ERP-specific audit tools, and the use of custom scripts in the auditing process.