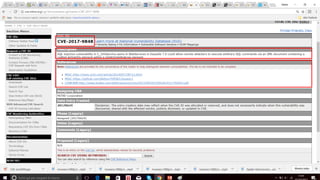
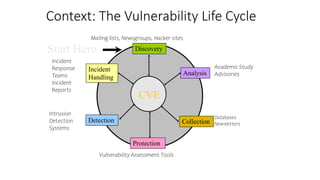
The document discusses Common Vulnerabilities and Exposures (CVE), which is a list that assigns unique identifiers (CVE IDs) to publicly known cybersecurity vulnerabilities. This ensures different parties use consistent names to discuss vulnerabilities and enables data exchange. It is maintained by a board and addresses issues like allowing disparate databases to correlate vulnerability data using a common language. CVE IDs follow the format CVE-YYYY-NNNN and include a description and references.