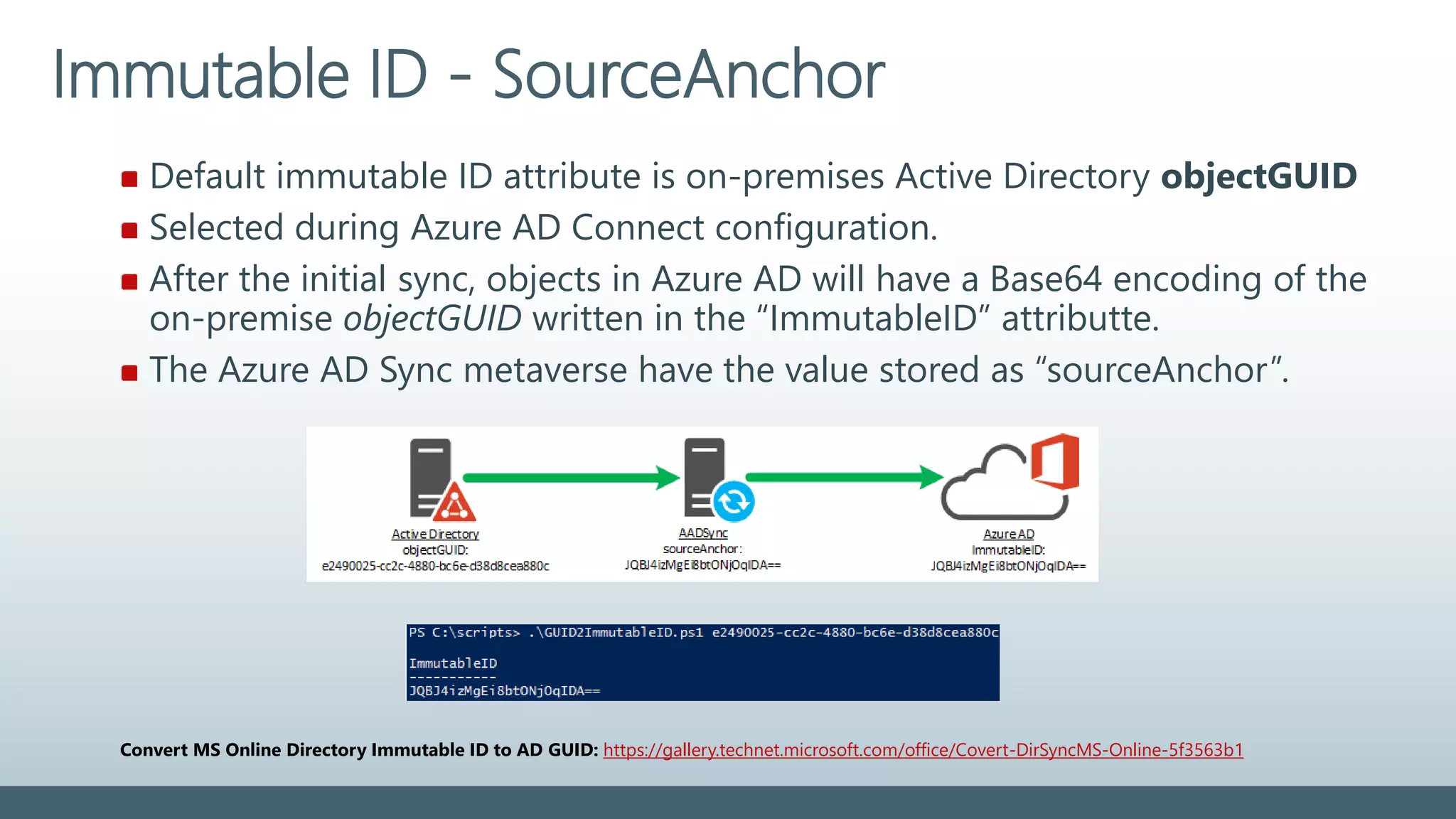
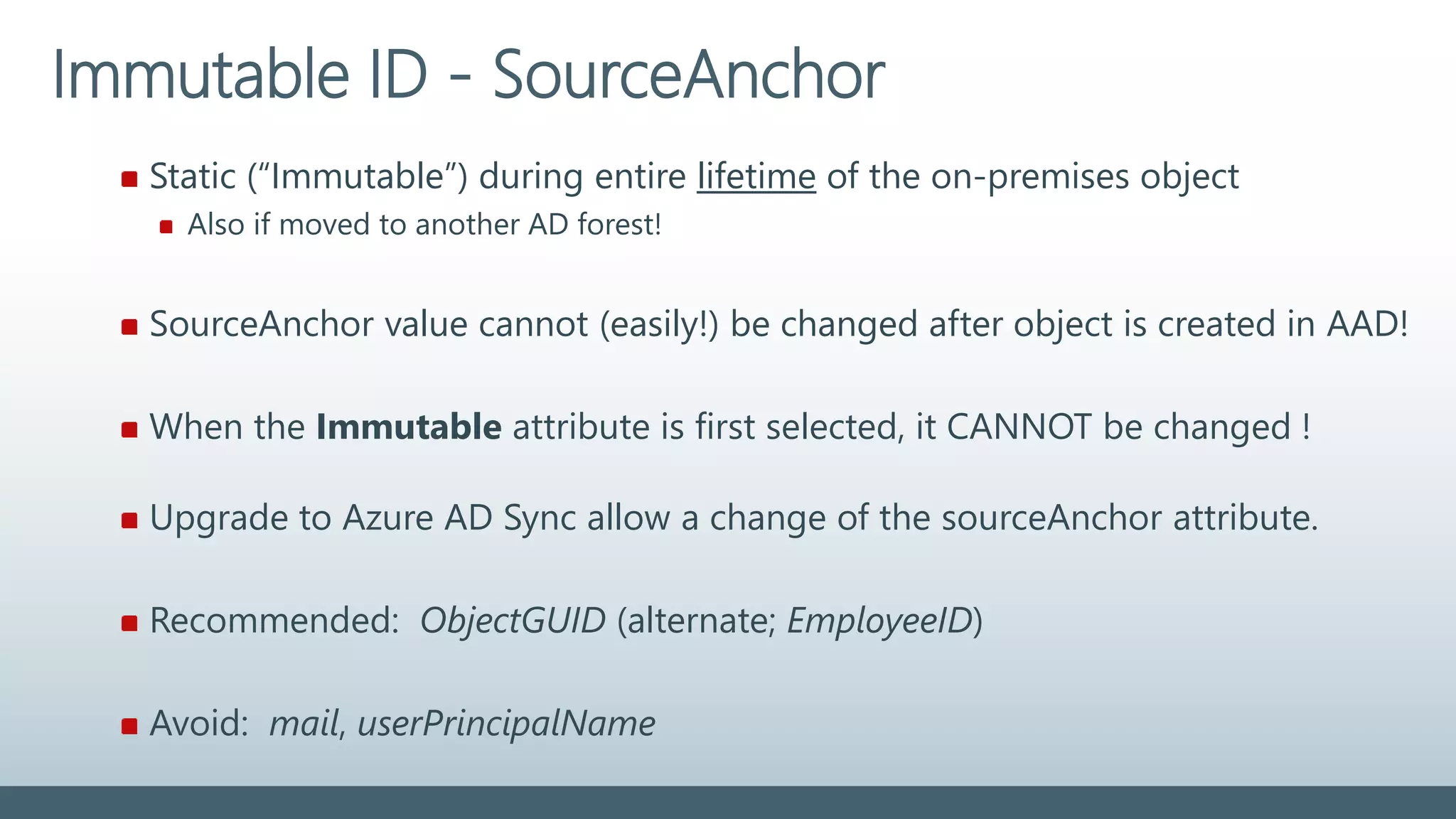
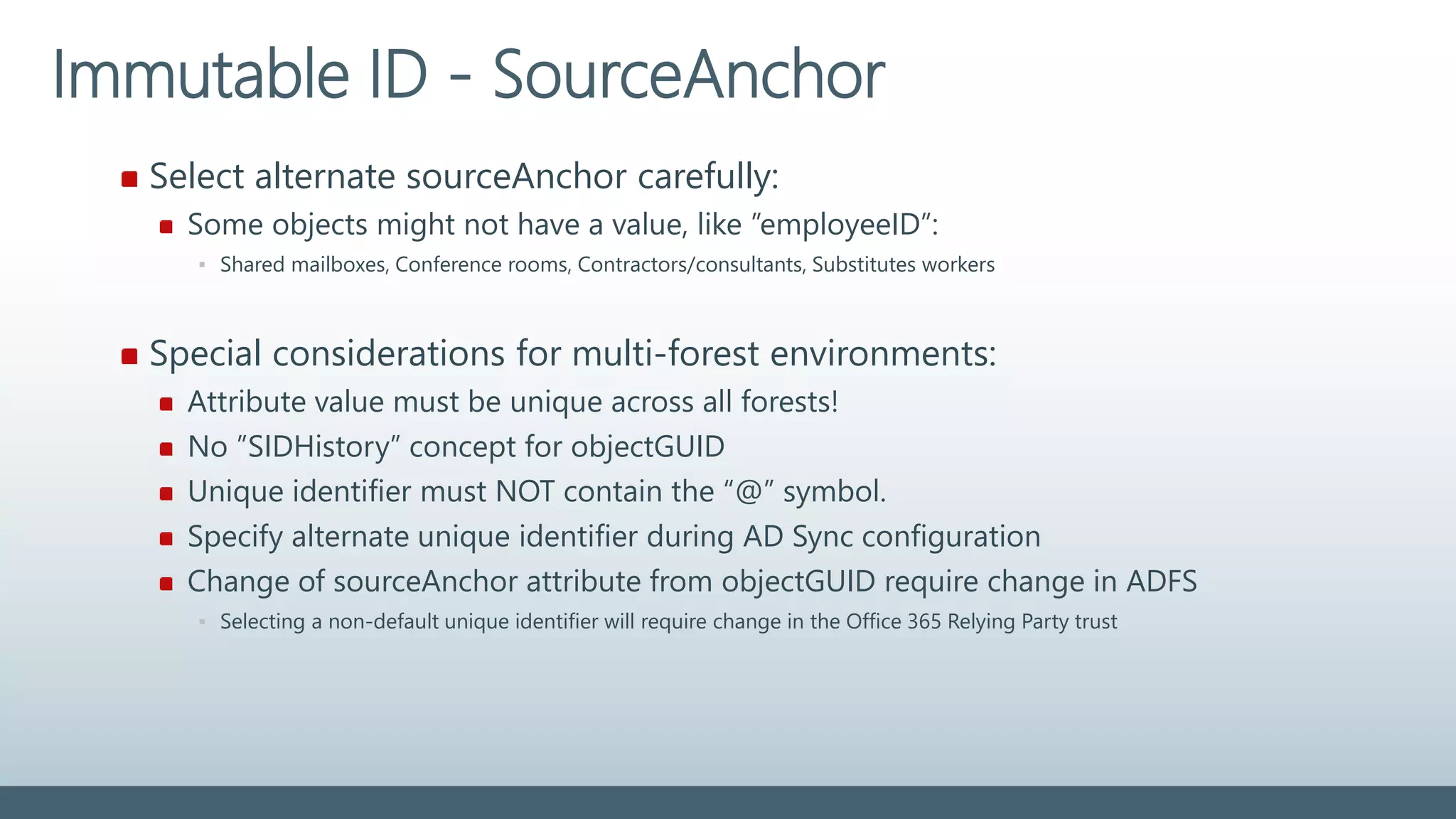
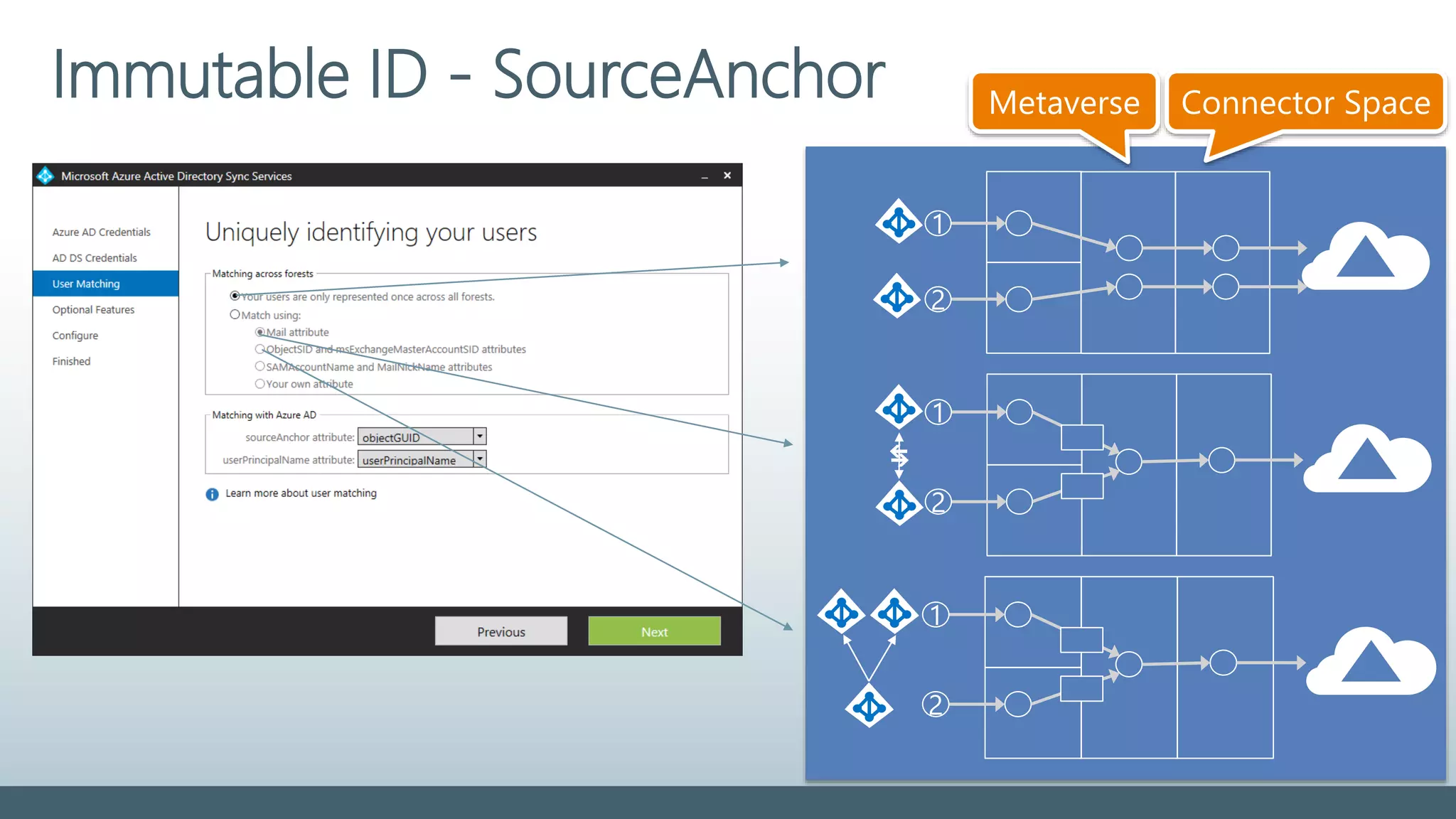
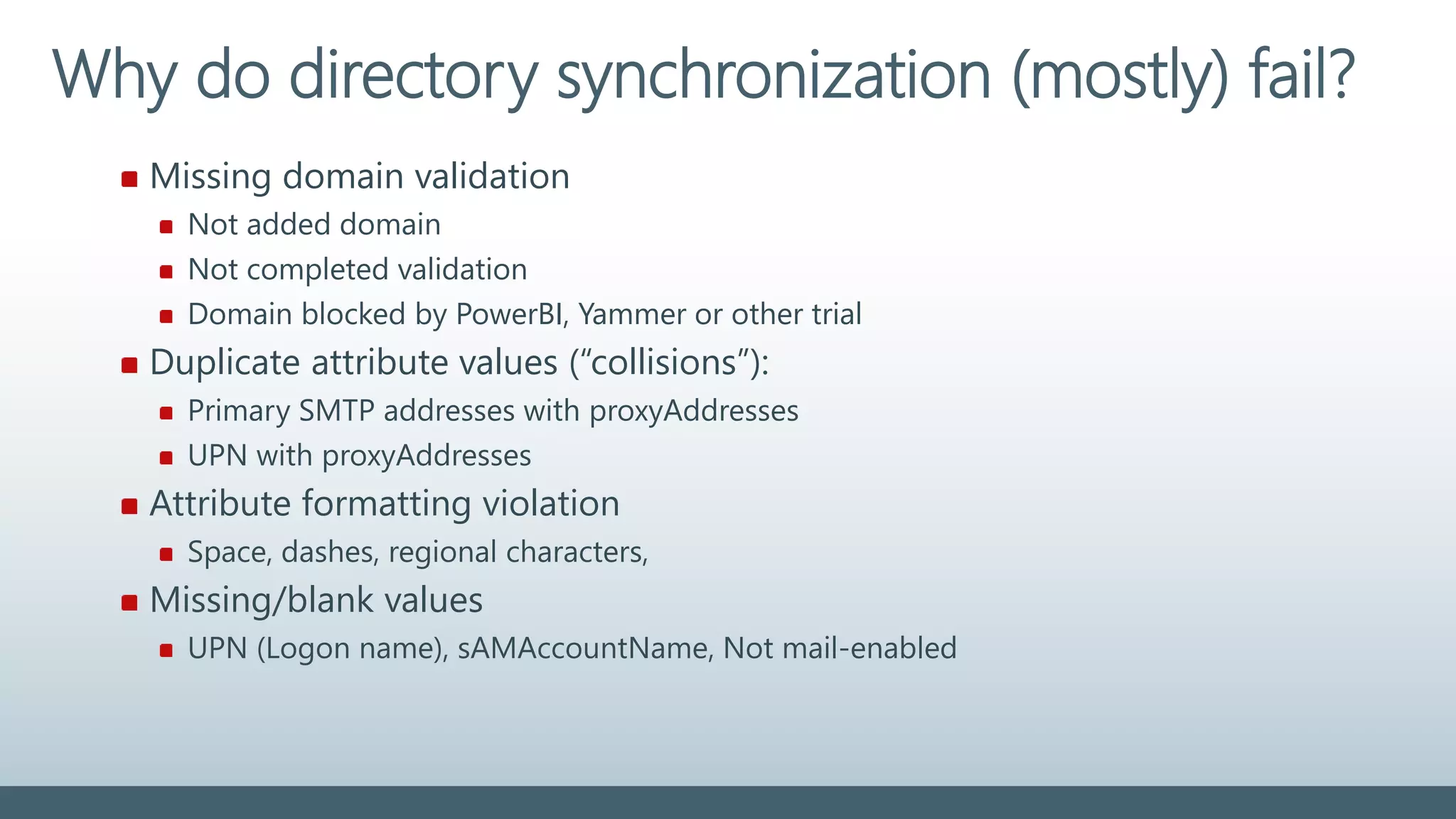
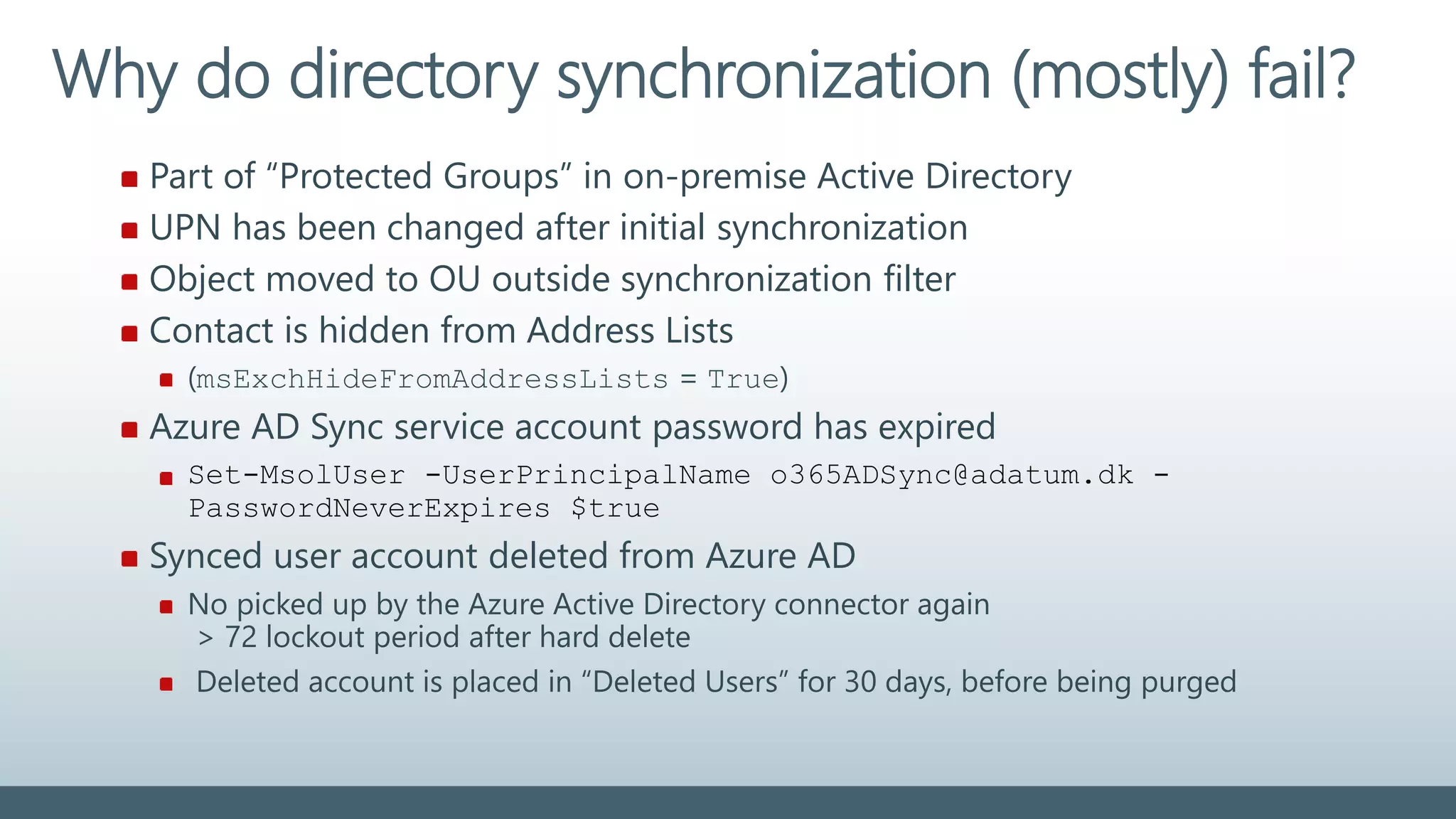
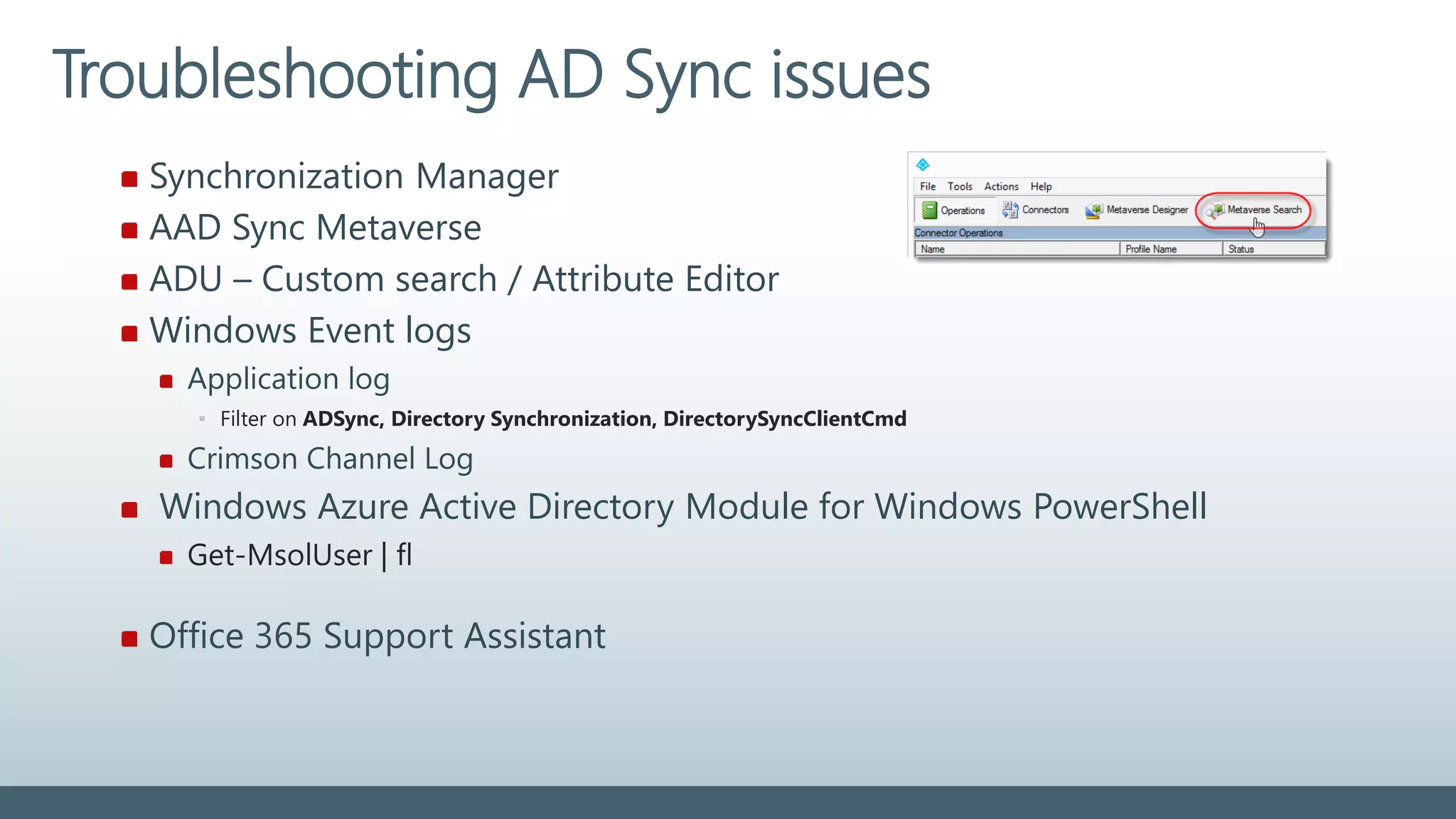
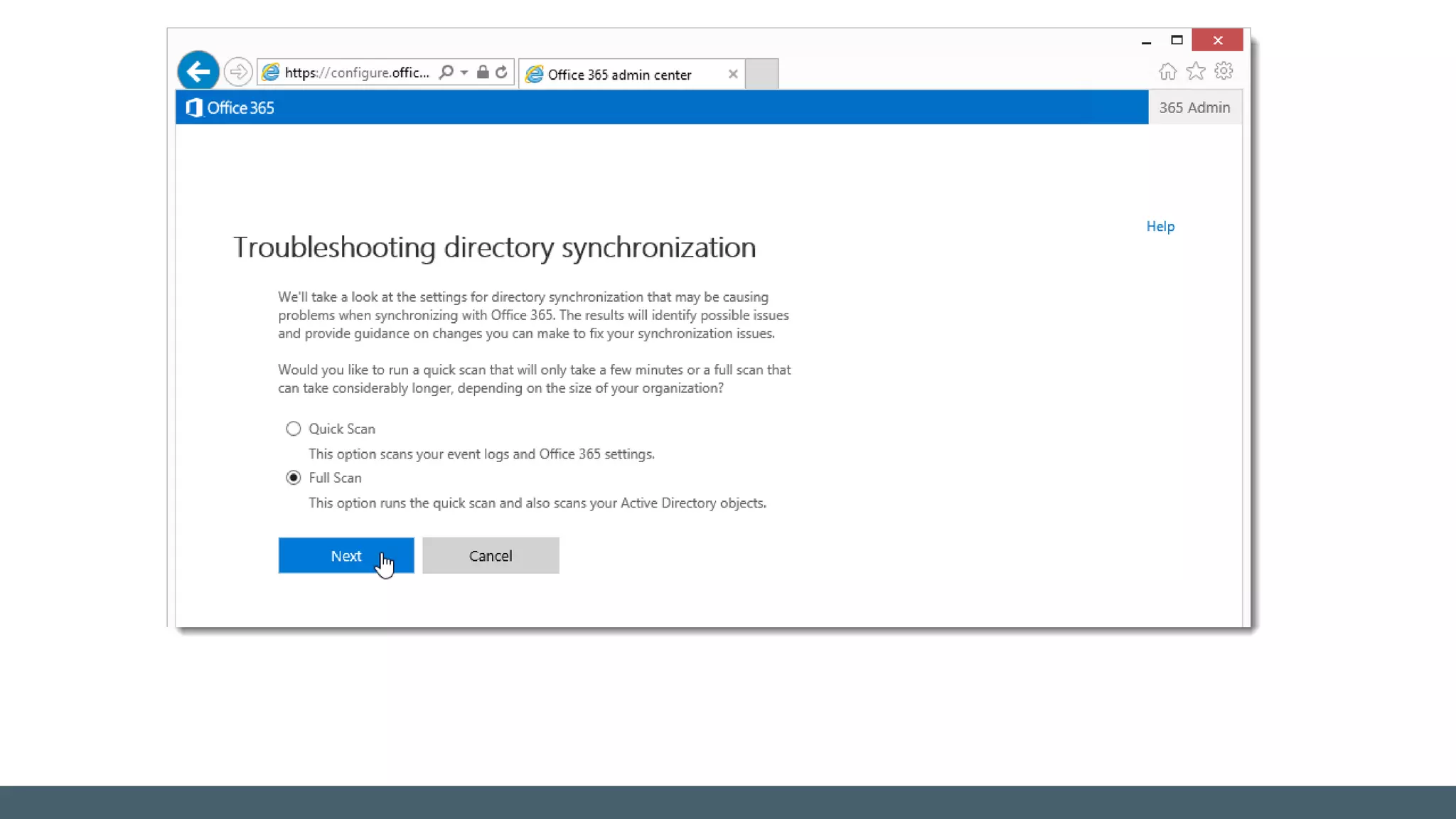
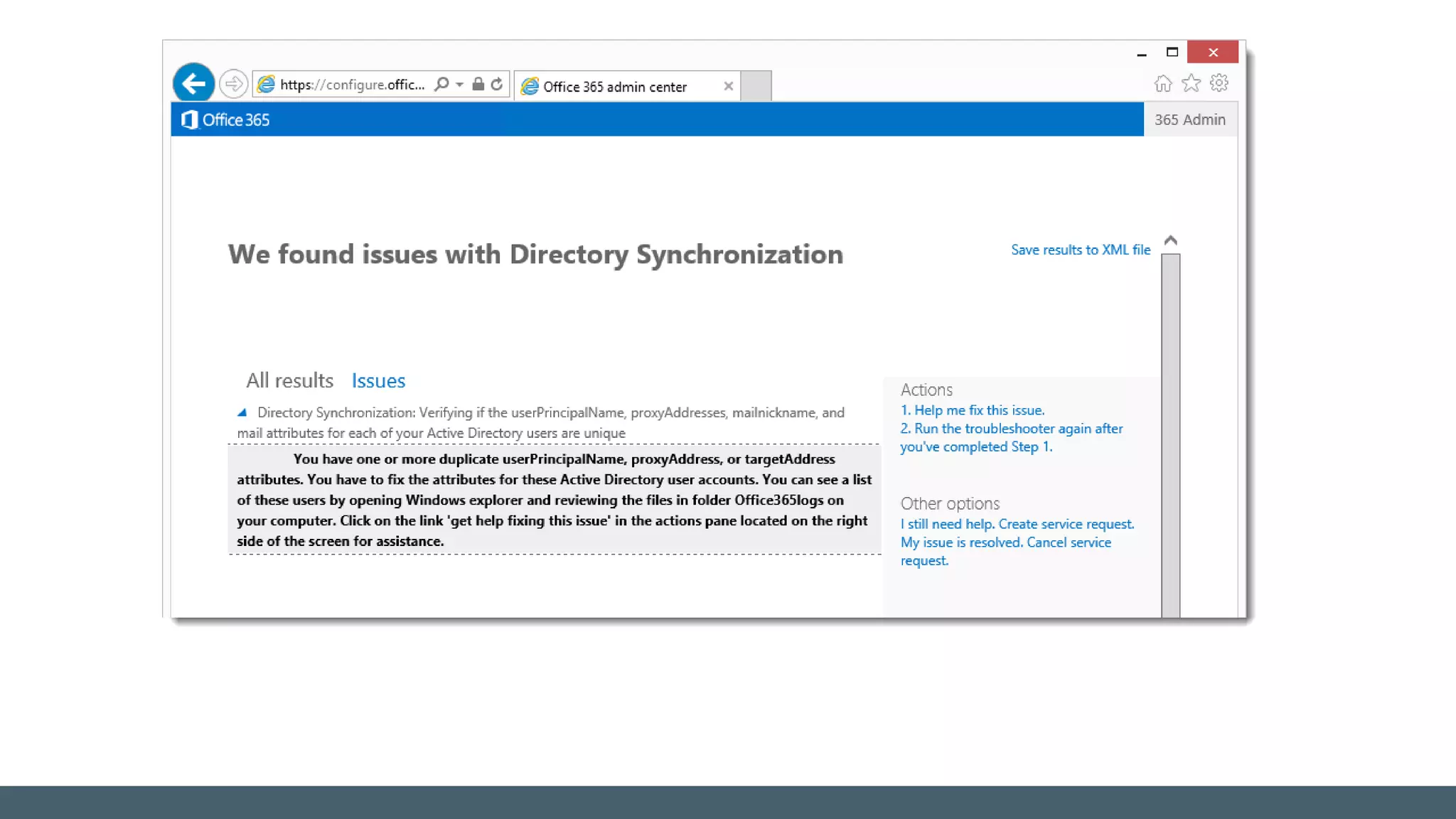
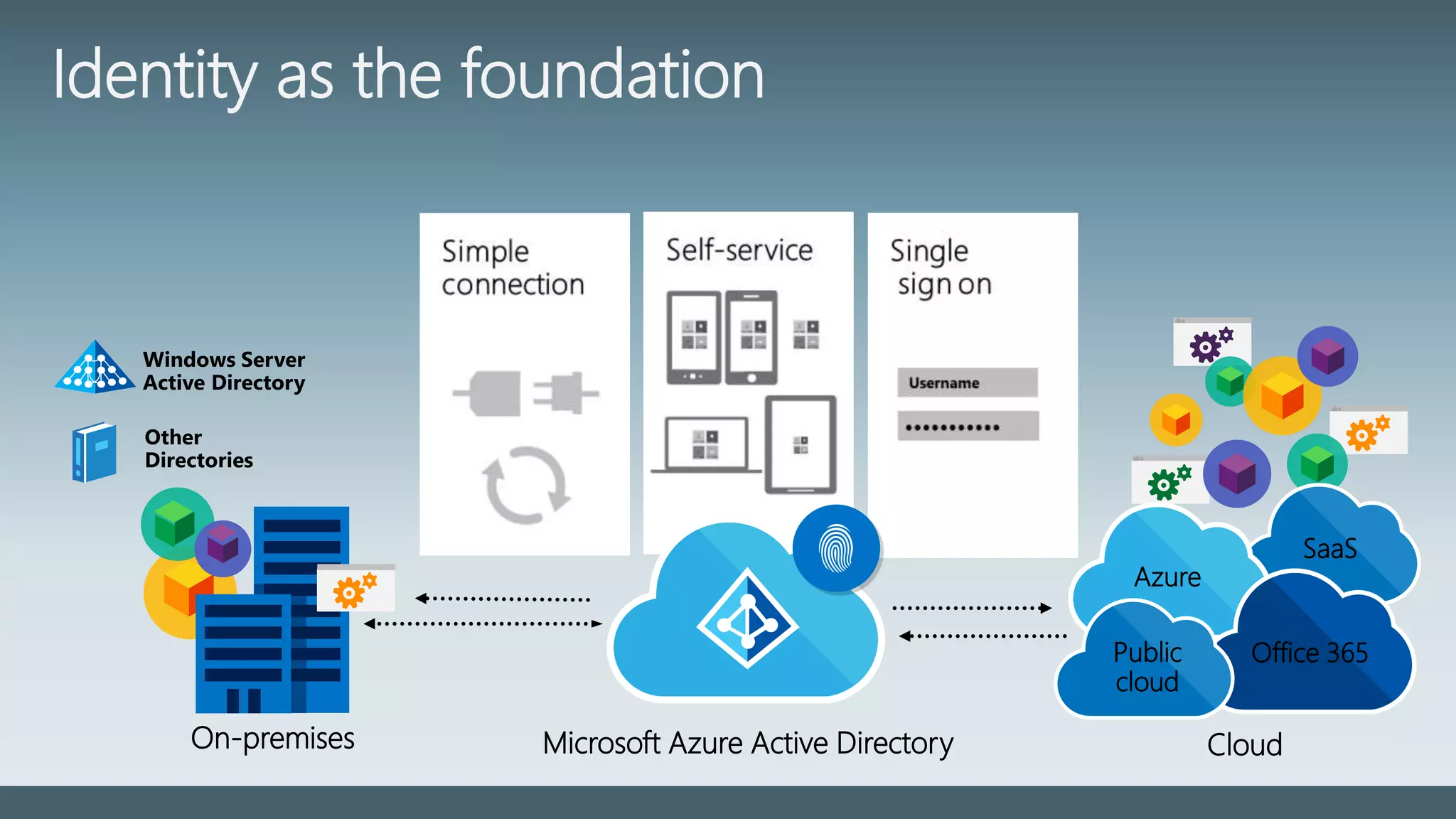
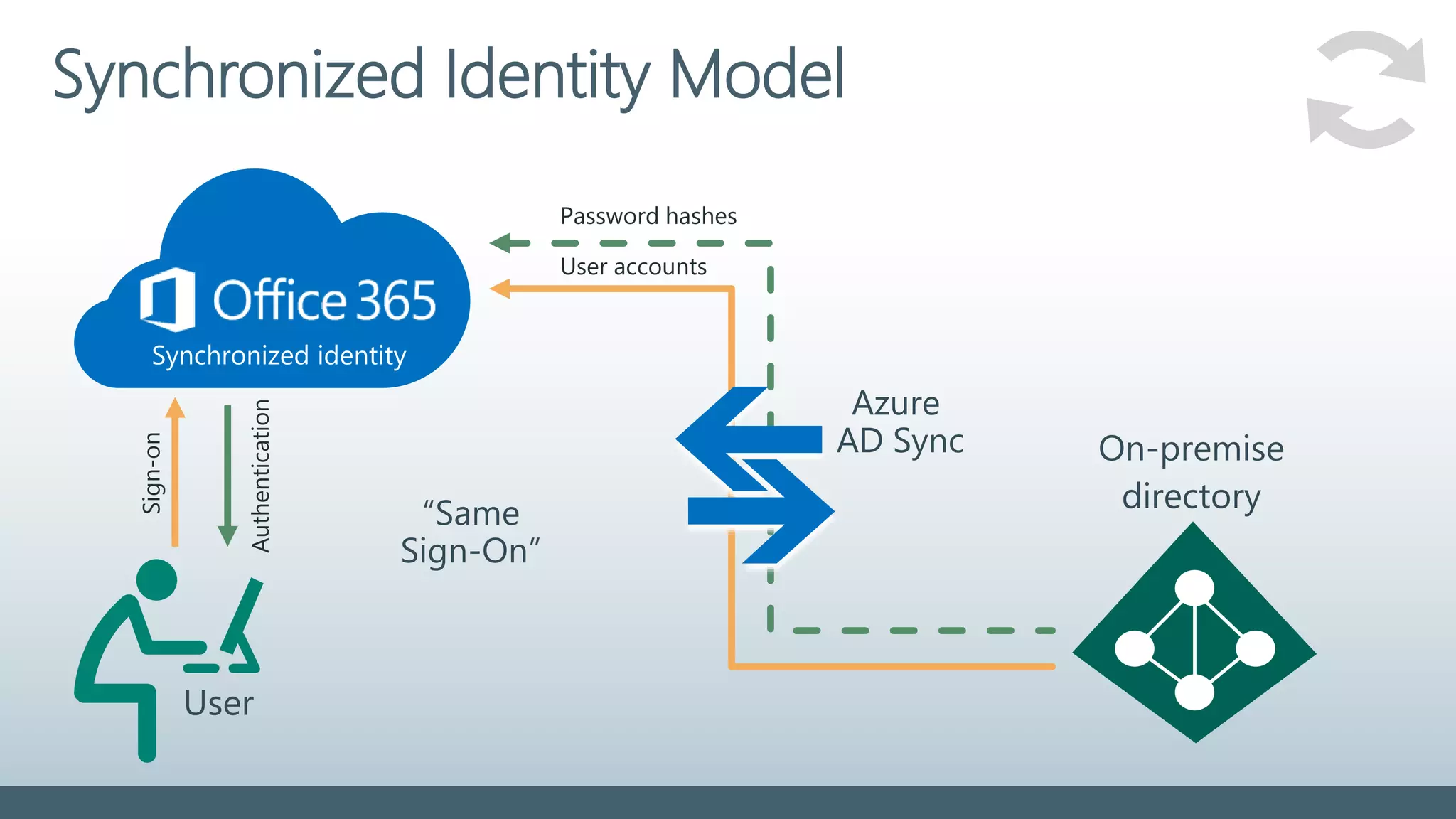
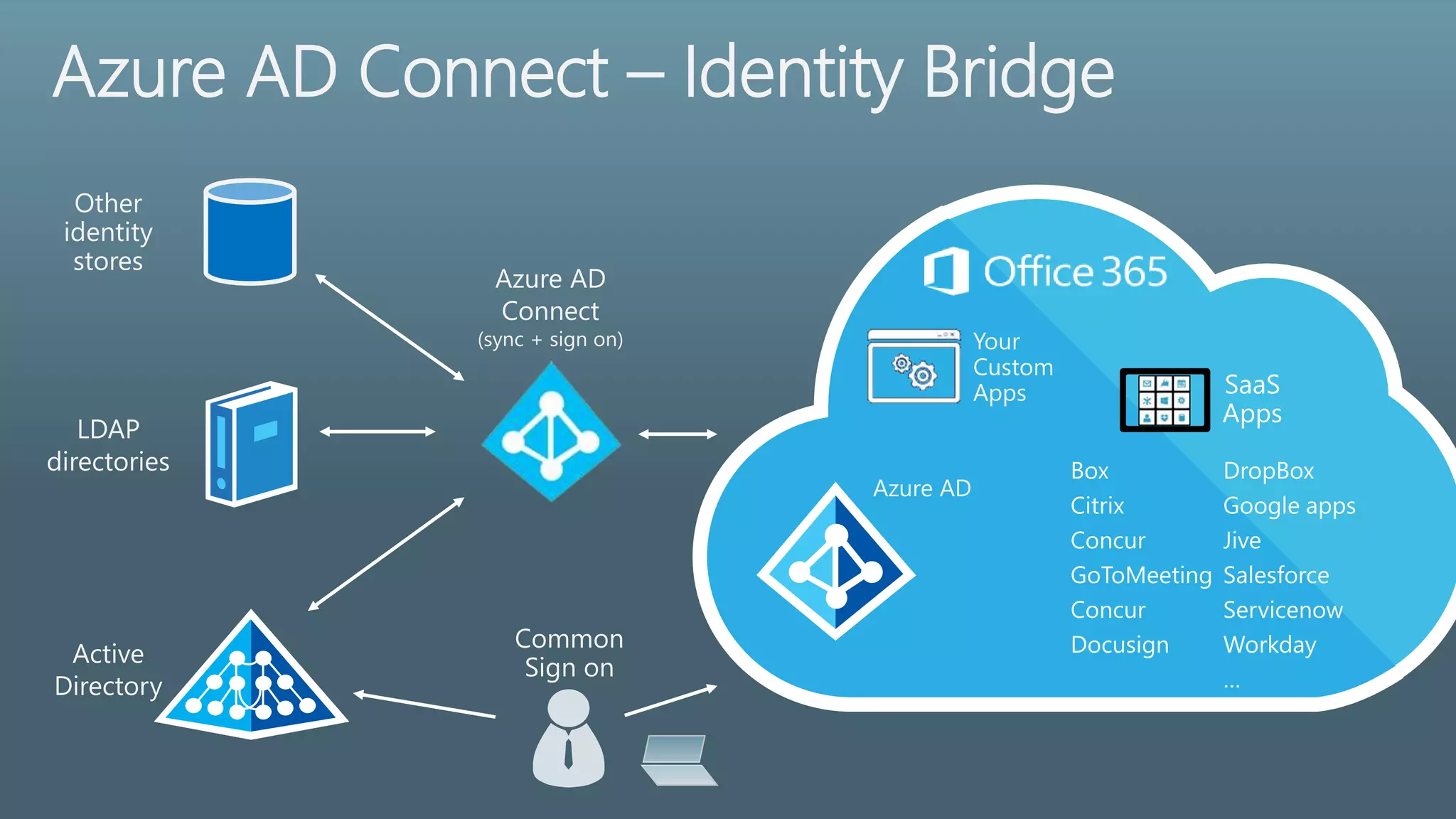
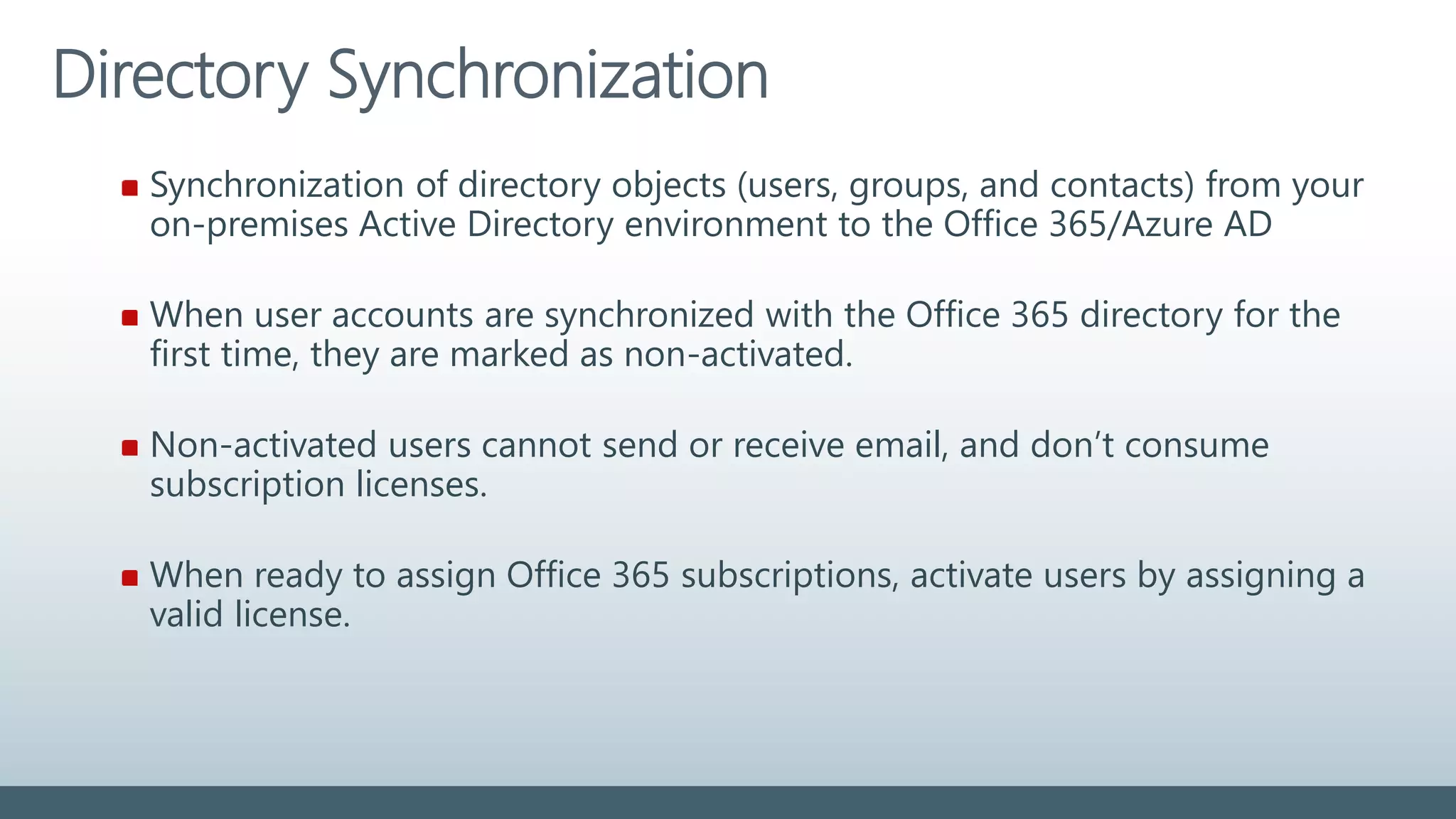
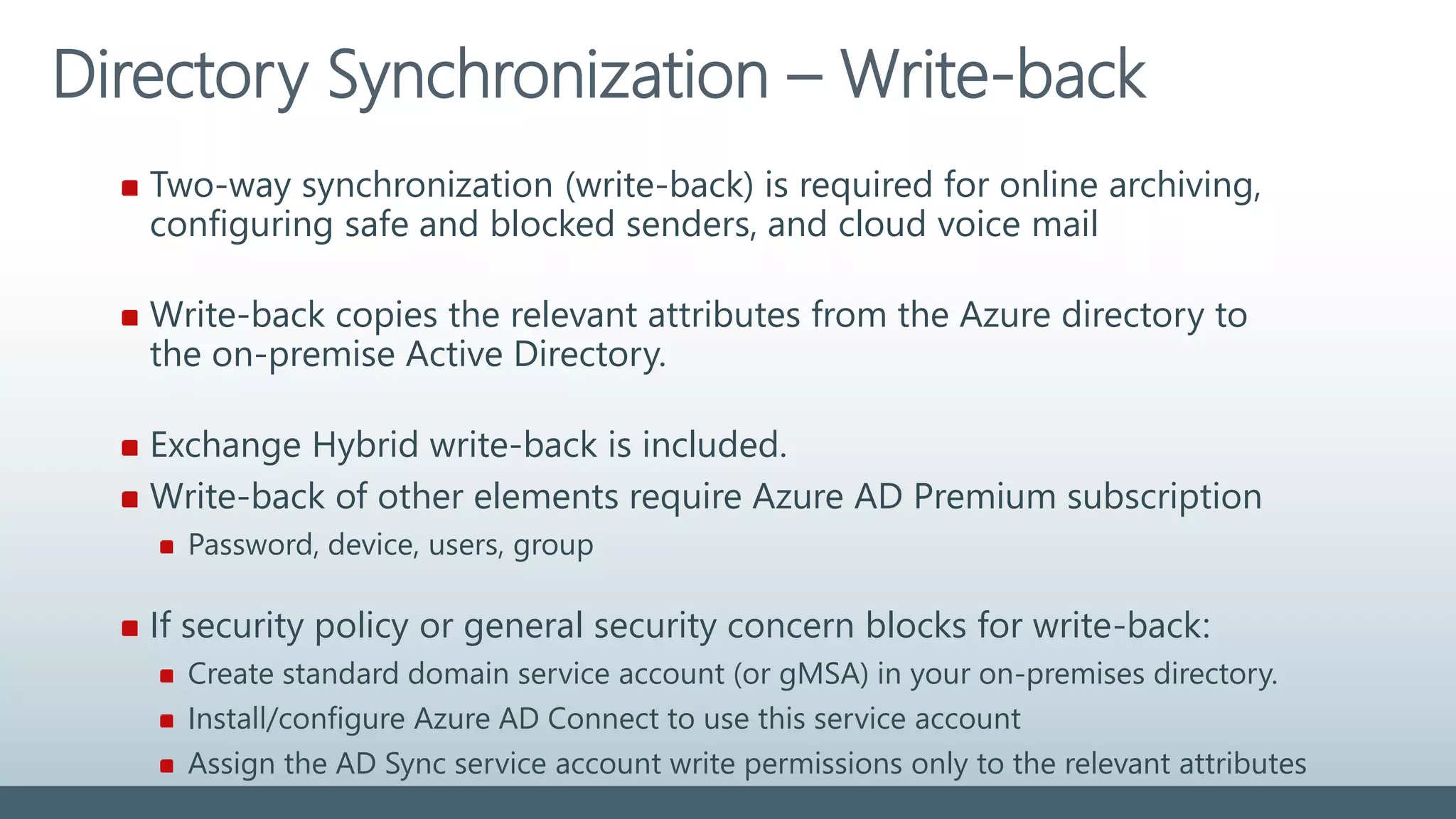
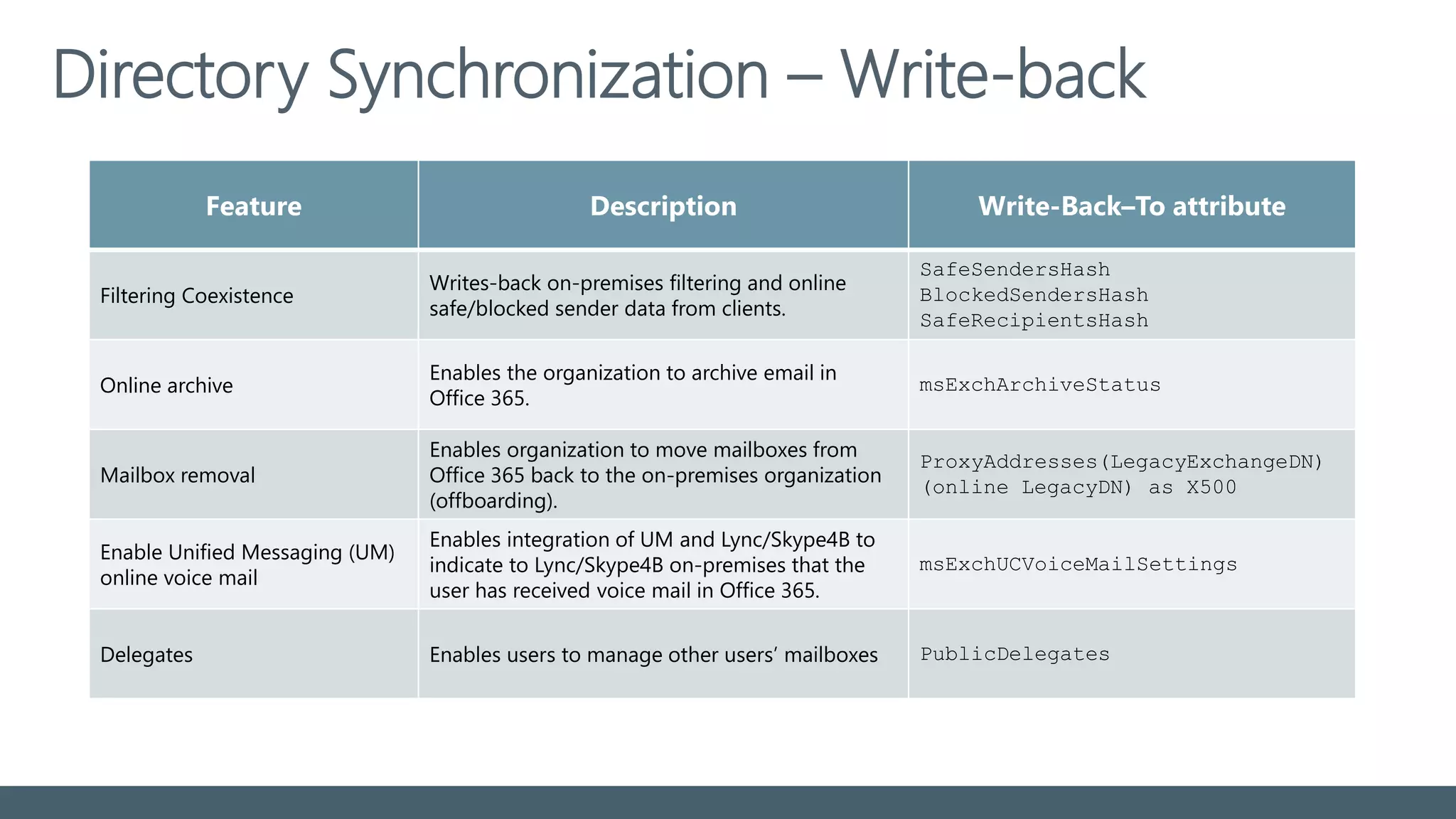
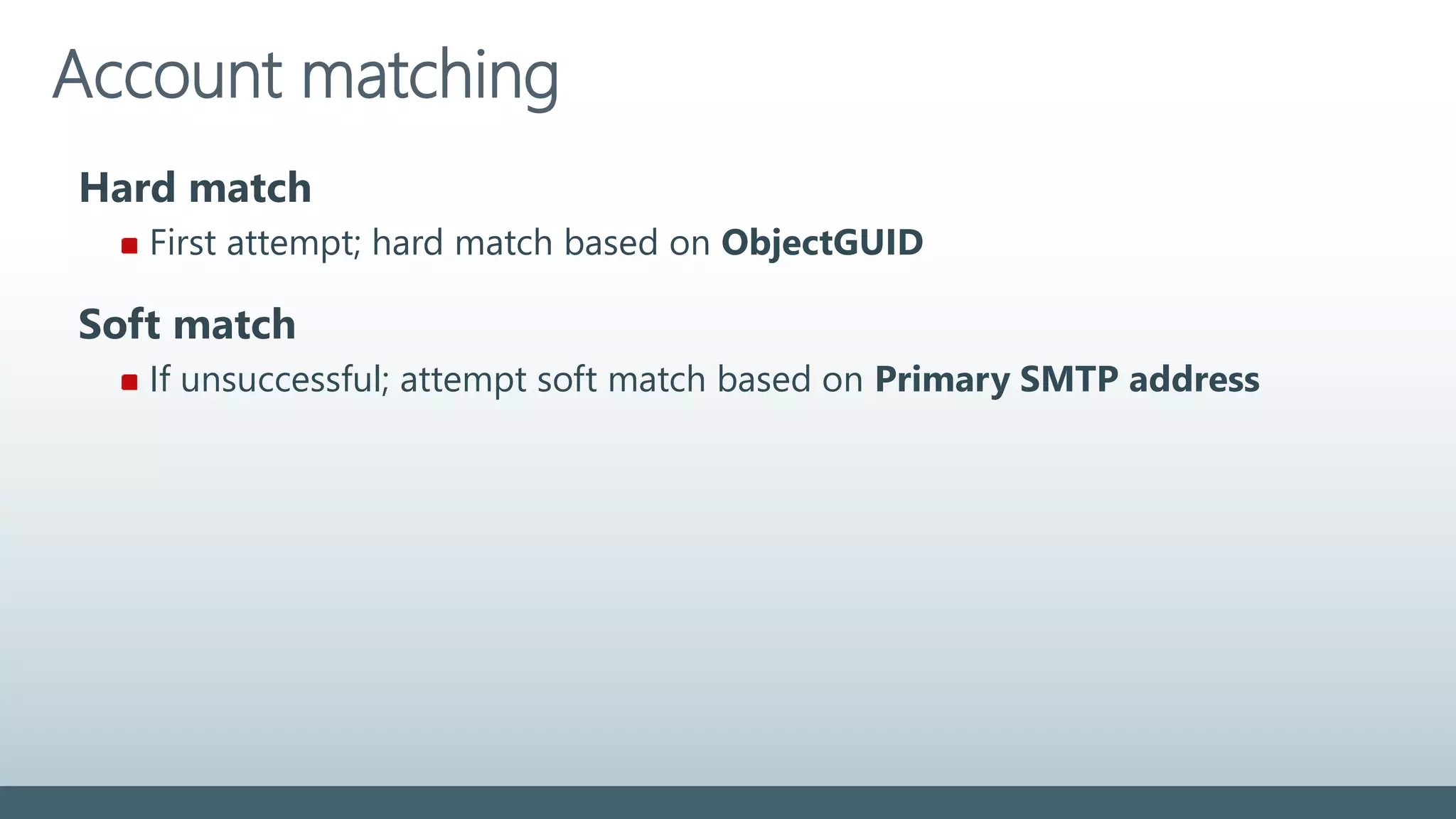
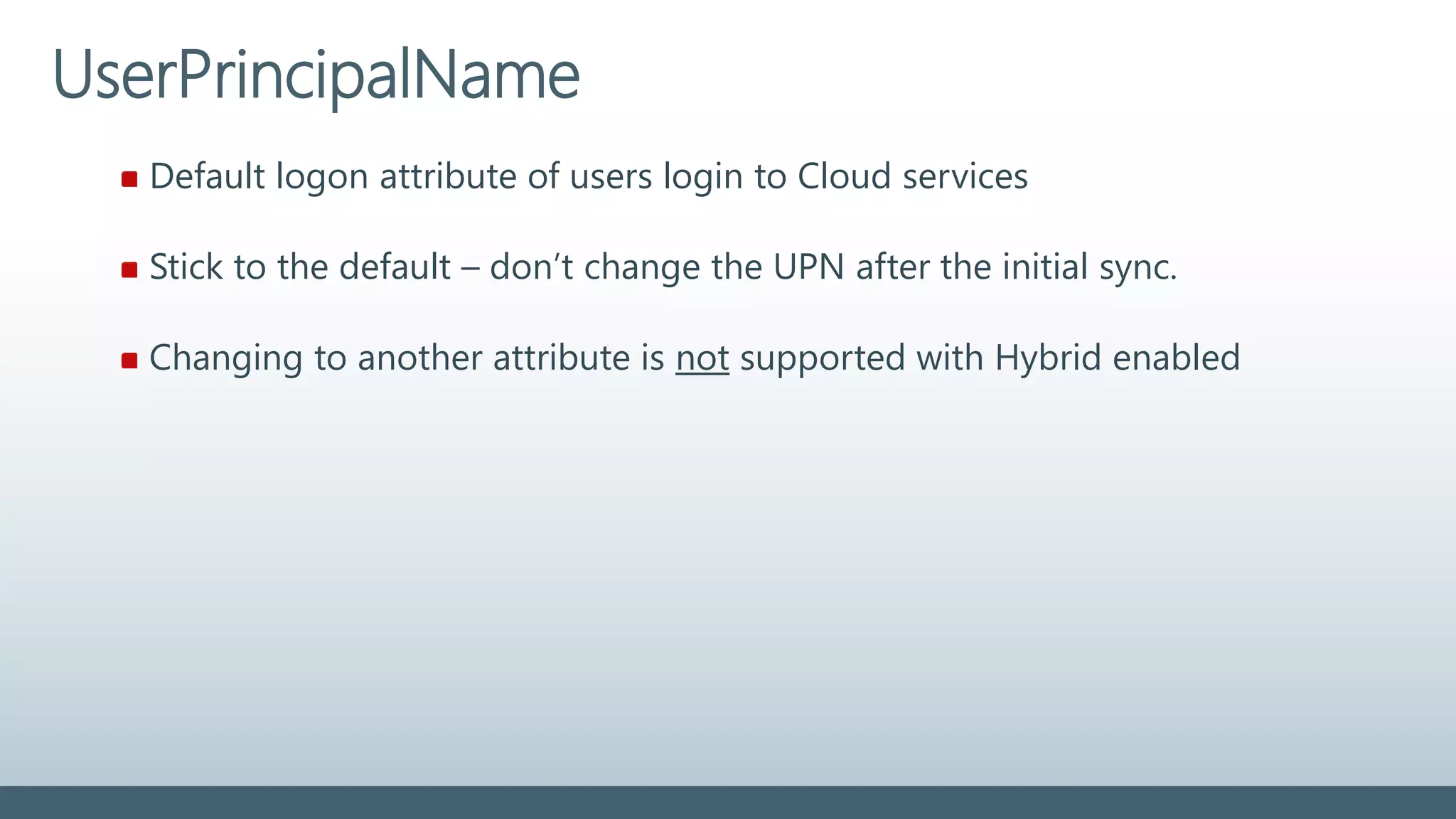
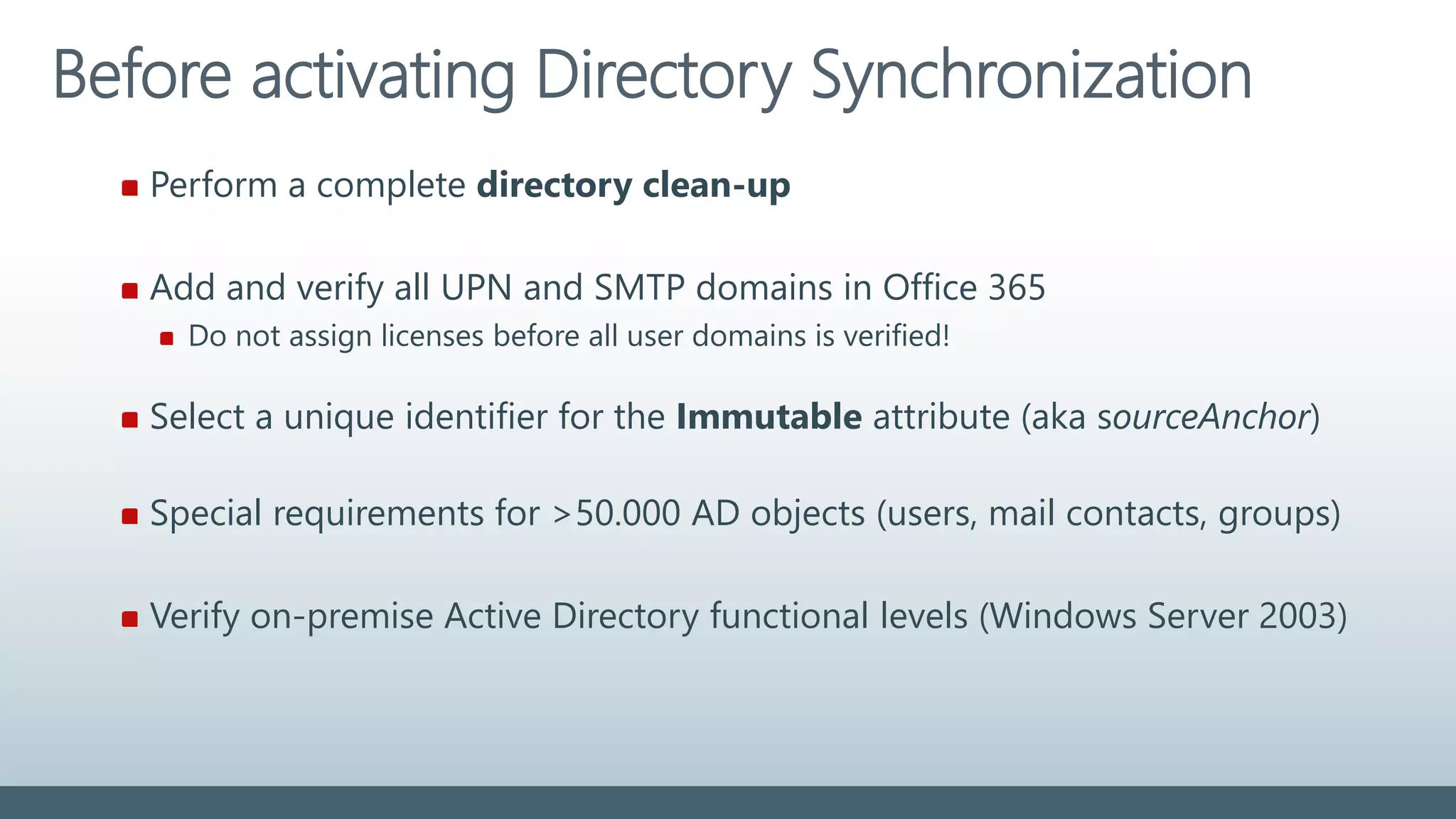
The document provides a comprehensive overview of identity management within cloud environments, focusing on Azure Active Directory and Office 365. It details the importance and process of directory synchronization, including prerequisites, account matching, and troubleshooting steps for effective integration. Key considerations for successful synchronization are emphasized, such as directory clean-up, attribute formatting, and maintaining a healthy synchronization state.





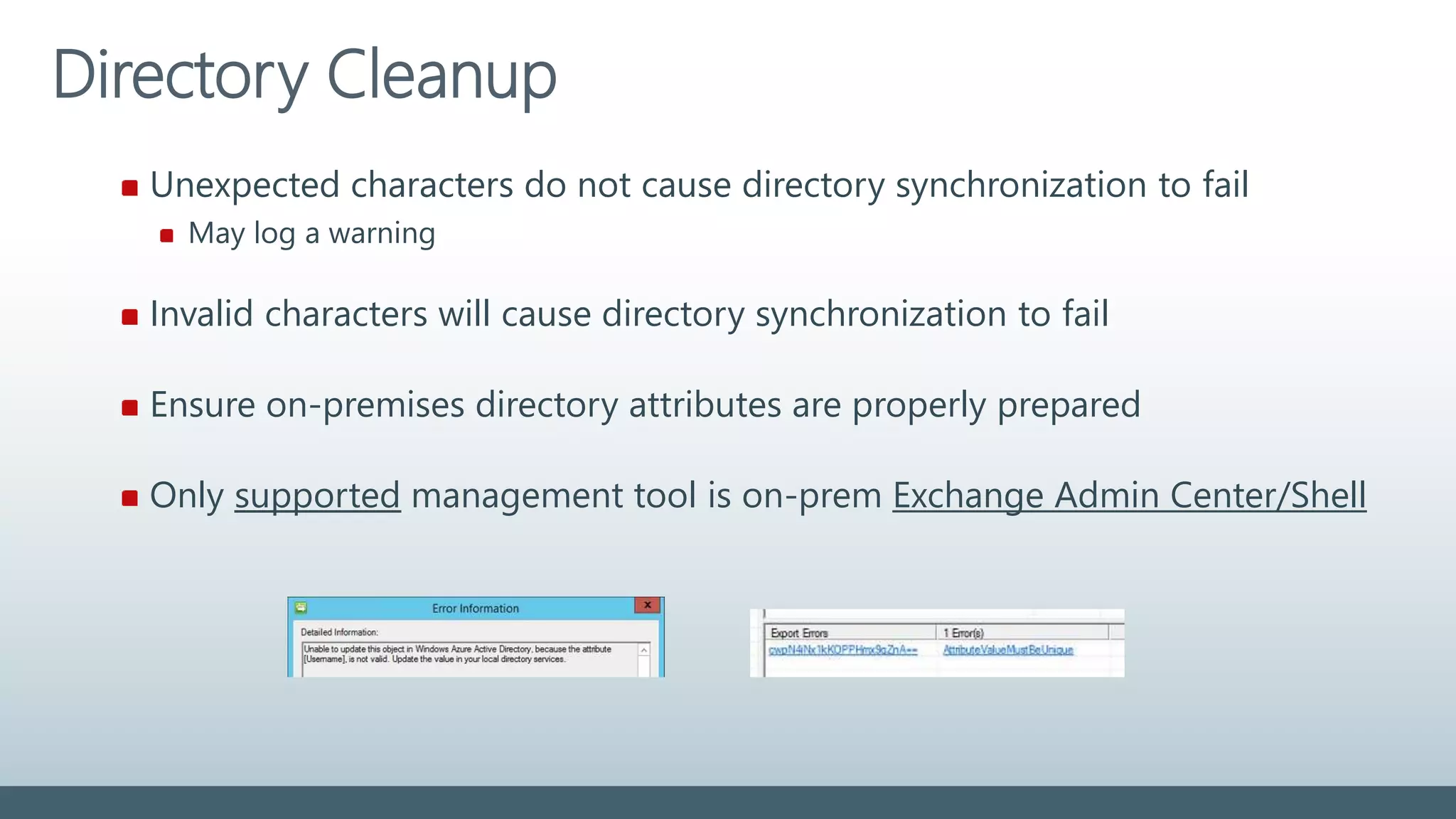
![Attributes to prepare
Attribute Values Length Invalid characters
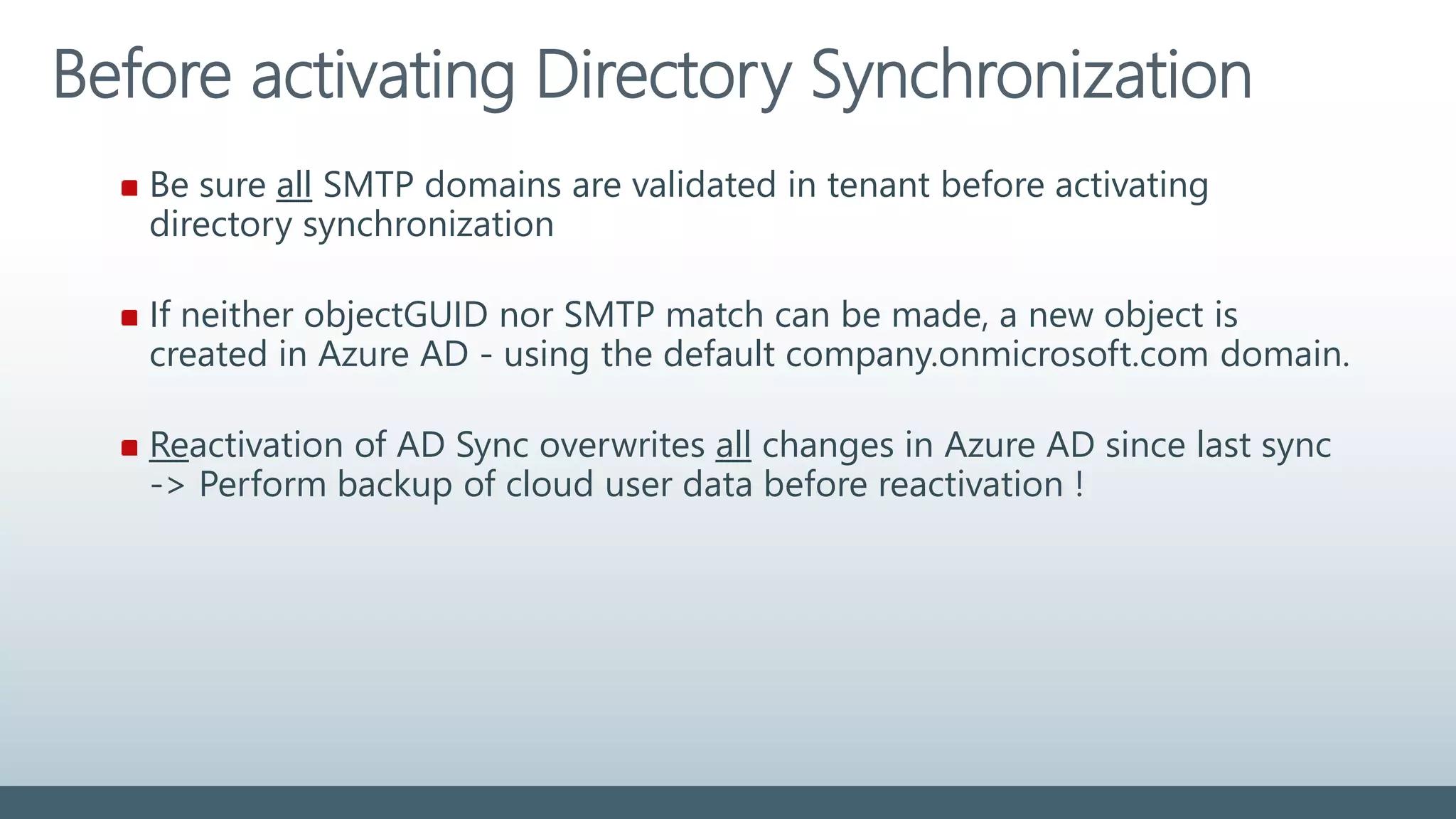
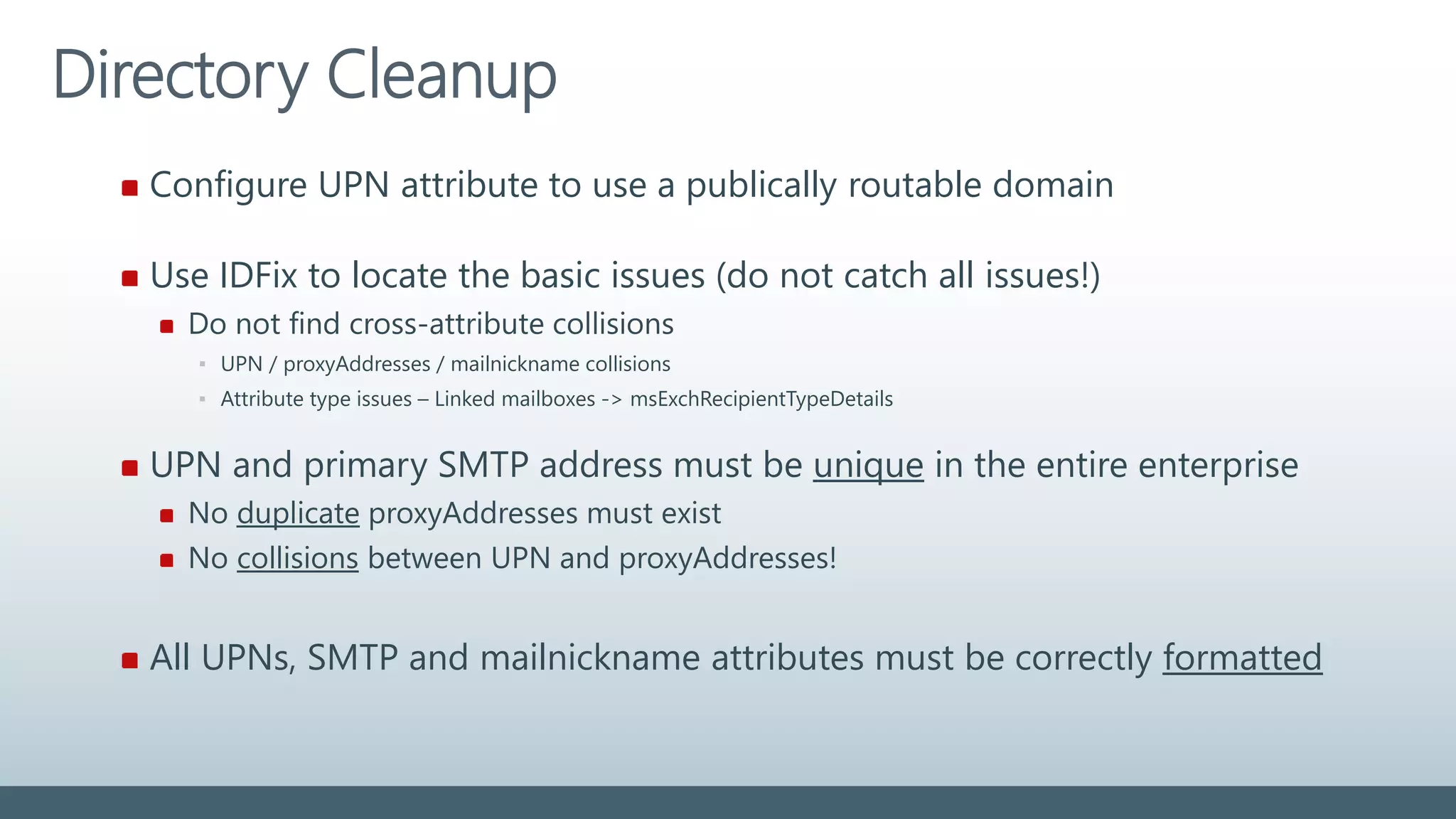
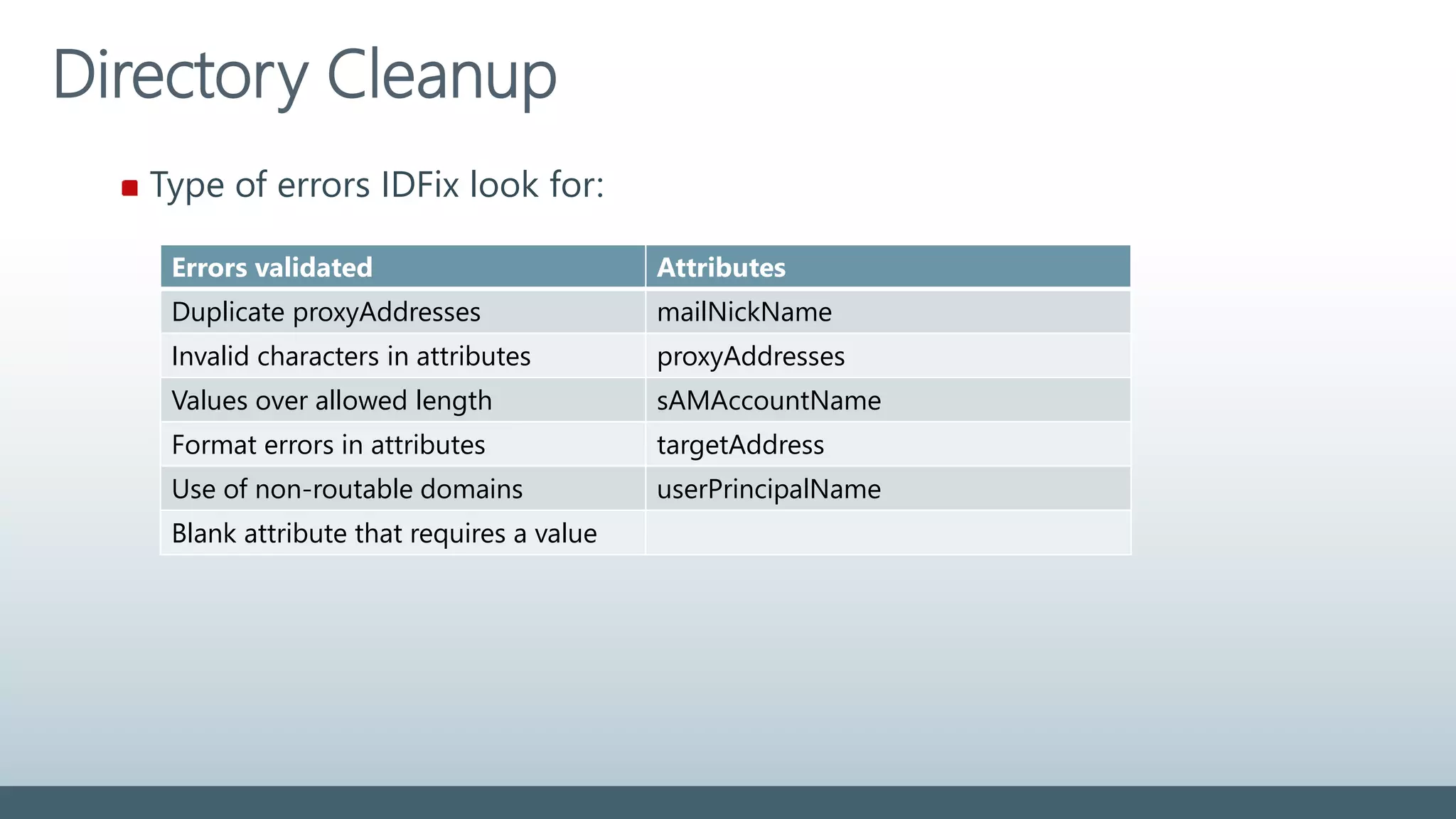
displayName Must not be blank 255 ? @ +
givenName Syncronized. Not required 63 ? @ +
Mail Must be unique in directory 255 [ ! # $ % & * + / = ? ^ ` { } ]
mailNickname
(Exchange alias)
Must be unique in directory 63 [ ! # $ % & * + / = ? ^ ` { } | ~ < > ( ) ‘ ; : ,
] “ @ (space) front/end (.)
proxyAddresses Must be unique in directory
Must comply with SMTP standards
256 % & * + / = ? ‘ { } | < > ( ) ; : , [ ] “ (space)
sAMAccountName Must be unique in directory 20 [ “ | , / : < > + = ; ? * ]
sn (surname) Syncronized. Not required 63 ? @ +
targetAddress Must be unique in directory
Must comply with SMTP standards
255 % & * + / = ? ‘ { } | < > ( ) ; : , [ ] “ (space)
userPrincipalName Must be unique in directory
Must comply with SMTP standards
Must use public routable domain
113
(64+@+48)
% & * + / = ? ‘ { } | < > ( ) ; : , [ ] “ (space)
front/end (.)/(&)/(@)
For most attributes it is not supported to use regional special characters](https://image.slidesharecdn.com/colabora-identityinaworldofcloud-november2015-151130111124-lva1-app6891/75/CoLabora-Identity-in-a-World-of-Cloud-november-2015-21-2048.jpg)