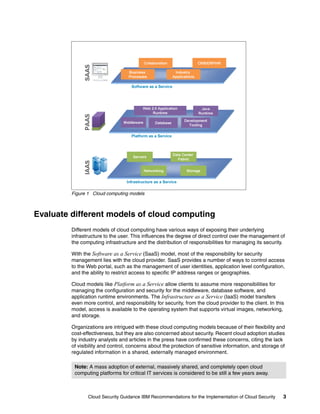
The IBM Redpaper discusses best practices and recommendations for implementing cloud security, emphasizing the need for organizations to understand the unique security challenges presented by cloud computing. It outlines a framework for enterprise security, highlighting key areas such as governance, risk management, and compliance, as well as the importance of data protection and identity management. The document provides actionable guidance for establishing secure cloud environments, including the implementation of robust security programs and infrastructure management.