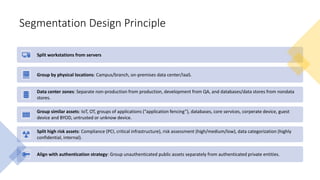
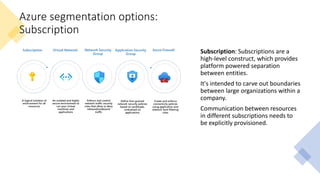
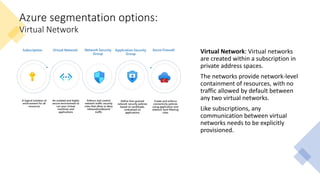
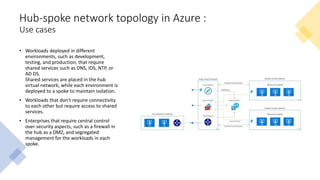
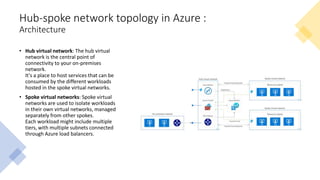
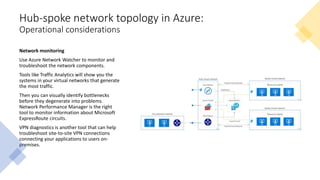
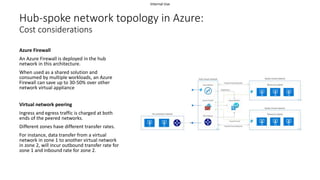
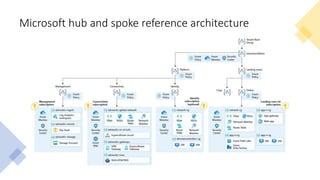
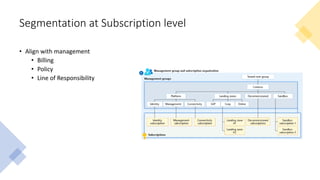
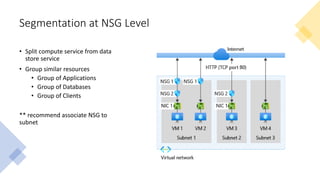
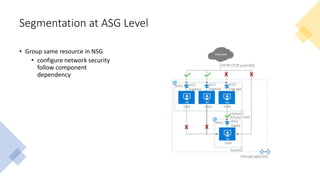
The document discusses network segmentation strategies on the Azure platform. It outlines several segmentation options on Azure including subscriptions, virtual networks, network security groups, application security groups, and Azure Firewall. It recommends segmenting based on principles such as splitting workstations from servers, grouping by physical location, separating production and non-production workloads, and isolating high risk or sensitive assets. The hub-spoke architecture is presented as a common topology for implementing segmentation on Azure with shared services in the hub and isolated workloads in spokes.